
2020-04-30 02:19:15 Author: www.offensiveosint.io(查看原文) 阅读量:226 收藏
This is the second part of my investigation into critical infrastructure around the world. This article should have been a presentation on ICS Conference in Singapore, however due to Coronavirus it will be a virtual event. I'm not interested in participating and I have left with quite good material so decided to make a summary blog post about it.
You can still read my first ICS research "Intelligence Gathering on U.S. Critical Infrastructure" on conference website.
Intelligence Gathering on U.S. Critical Infrastructure
In case you missed last episode about how to look for disinformation in social media, you can still find it here
Offensive OSINT s01e03 - Looking for election related disinformation on Polish service wykop.pl
In this episode, we will take a look on disinformation campaign in polish social media platform - wykop.pl. It’s very similar to widely known Reddit, without subreddits, but with tags and micro blog instead. I will present techniques to gather information about users, upvotes/downvotes and content. …
Offensive OSINT

OSINT & INDUSTRIAL CONTROL SYSTEMS
I have learned a lot about Industrial Control Systems devices, since last research, their types or vendors and also about general approach for this kind of investigations. Right now, the last article would look completely different because of changes in Kamerka. The update makes everything simpler, it includes a lot of new features like GUI, Google Maps, WHOIS XML and BinaryEdge or more than 100 devices to choose. It's just a ultimate reconnaissance ICS/IoT tool nicely presented and is meant to be used by intelligence analysts.
For most of the people, who used Kamerka, it's just another tool that can find fancy devices in Shodan, but for researchers specialized in monitoring exposed devices it's trove of information. When critical infrastructure comes to game, then things start to be interesting, no device in critical infrastructure sector should be facing the Internet under any circumstances. The main point of this research is to find any device or management panel exposed directly to the Internet counted as a critical infrastructure.
US Department of Homeland Security made a special guidance regarding critical infrastructure during coronavirus outbreak.
Coronavirus | CISA
The Cybersecurity and Infrastructure Security Agency (CISA) continues to monitor the evolving COVID-19 situation, taking part in interagency and industry coordination calls, and working with critical infrastructure partners.

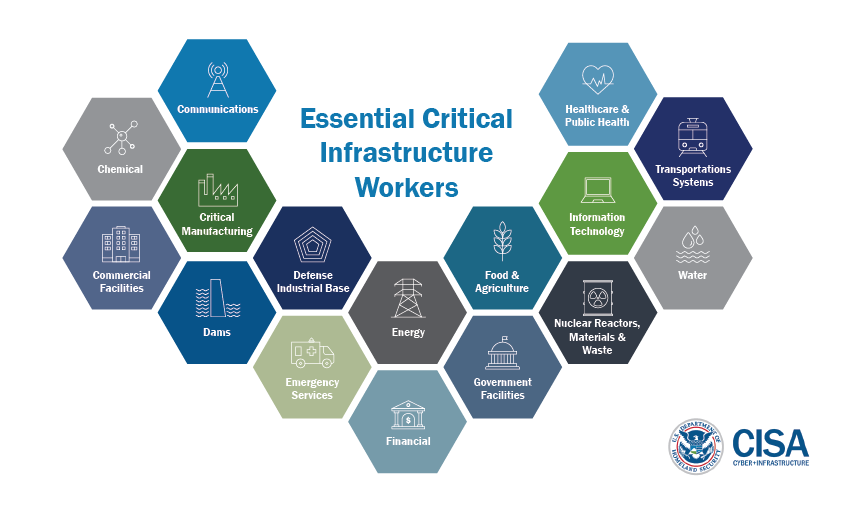
There are plenty of sectors that have to run continuously and require additional security measures. I wrote more about each sector in the first part and you should get acquainted with it.
Nowadays, the most important sector is Healthcare & Public Health. To examine this, one needs more precise approach than just scan ICS/SCADA devices. You can read my research - how to find exposed medical devices/services and gain knowledge about healthcare industry.
When ꓘamerka meets healthcare — Research on exposed medical devices
ꓘamerka is going after hospitals and health clinics. I’m publishing tons of queries related to healthcare industry and medical sciences including variety of devices, EMR (Electronic Medical Records) or PACS (Picture Archiving and Communication System). As always, I will also show how to geolocate ce…
WojciechOffensive OSINT

Currently, you can come across hundreds of thousands publicly accessible SCADA devices from different vendors and variety of models. So how can you find only ones operating in on of the mentioned 16 sectors of critical infrastructure?
OSINT & CRITICAL INFRASTRUCTURE
First, lets answer a question why and who attacks the critical services that are necessary for operating a municipally or even country. Still the most dangerous one are APTs and theirs weapons - most famous Stuxnet or Triton. I put insiders also in threat group because of their knowledge. If they don't have direct access or know password they might be helpful when comes to mapping the network or components.
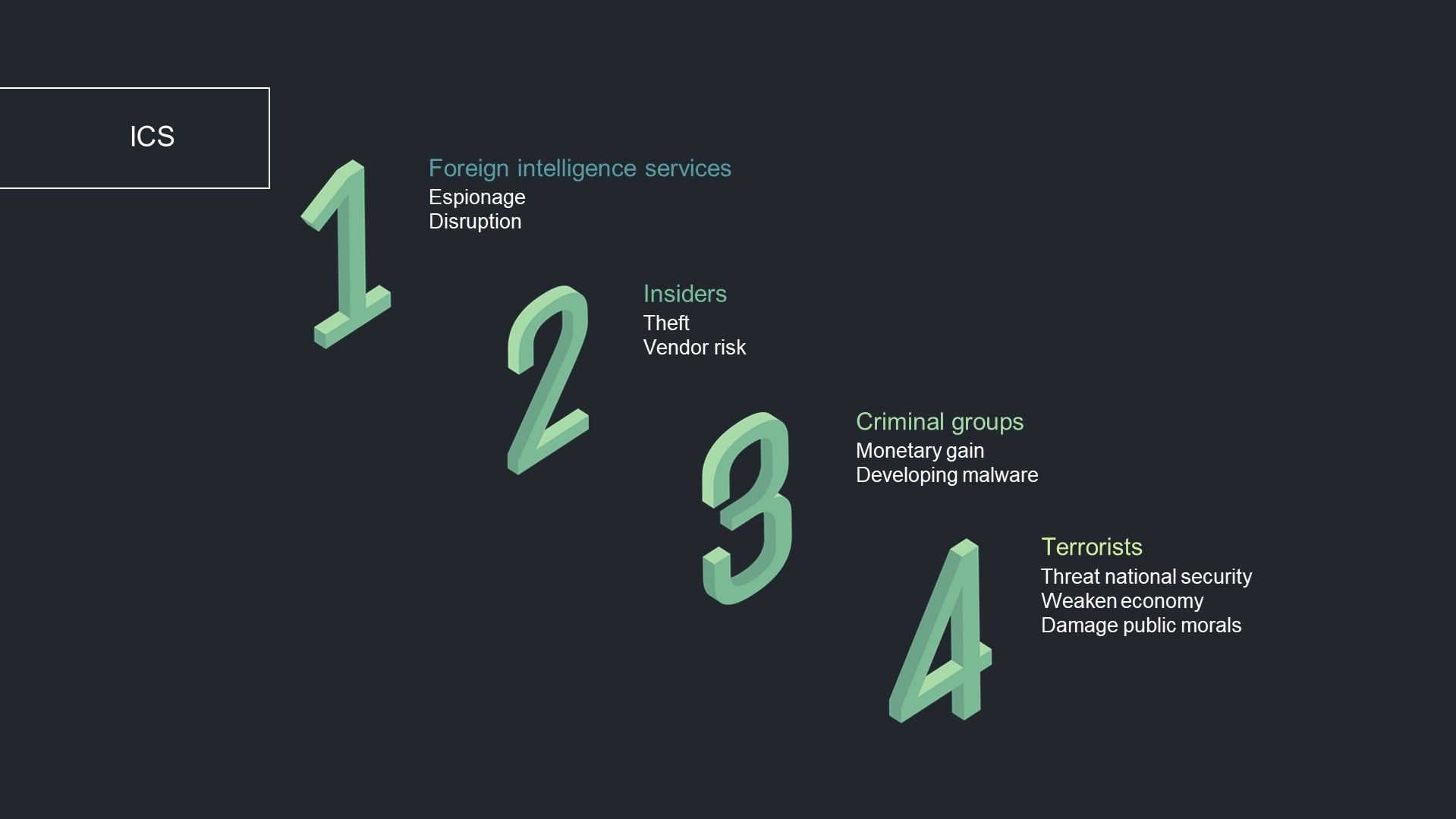
Criminals groups does not often attack industrial devices, however it slowly start to become a real thing. The ransomware dubbed "Ekans", described by Dragos, showed some signs that may indicate interests in targeting ICS devices.
EKANS Ransomware and ICS Operations
The last group that might be threat are terrorists, it also includes different forms of hacktivism. I haven't heard about any such case yet, but it can be a big thing in the future. Due to many exposed devices and simplicity of getting access someone may cause disruption, which then is a threat for national security. It also shows strength of adversary, might weaken economy and damage public morals.
We know already who can target ICS, so now we should think what kind of information threat actor can gather during reconnaissance. It's perfect moment to remind about MITRE ATTACK for ICS, it describes every step of attack on SCADA/ICS devices.
https://collaborate.mitre.org/attackics/index.php/Initial_Access
My presentation focuses on first step - "Initial Access", and consists of different way and techniques to obtain intelligence that supports the whole chain of cyber attack.
- Exploit Public-Facing Application https://collaborate.mitre.org/attackics/index.php/Technique/T819
- External Remote Services https://collaborate.mitre.org/attackics/index.php/Technique/T822
- Spearphishing Attachment https://collaborate.mitre.org/attackics/index.php/Technique/T865
- Internet Accessible Device https://collaborate.mitre.org/attackics/index.php/Technique/T883
It's worth to highlight, one of the group associated with Industroyer successfully gained access via exploiting exposed device.
Sandworm actors exploited vulnerabilities in GE's Cimplicity HMI and Advantech/Broadwin WebAccess HMI software which had been directly exposed to the internet
To defend from any of the group, I prefer offensive approach and find as many weak and entry points as possible. It's really tough task since our battlefield is a whole country and each exposed device that belong to it.
I distinguish three most important categories for ICS devices from OSINT perspective.
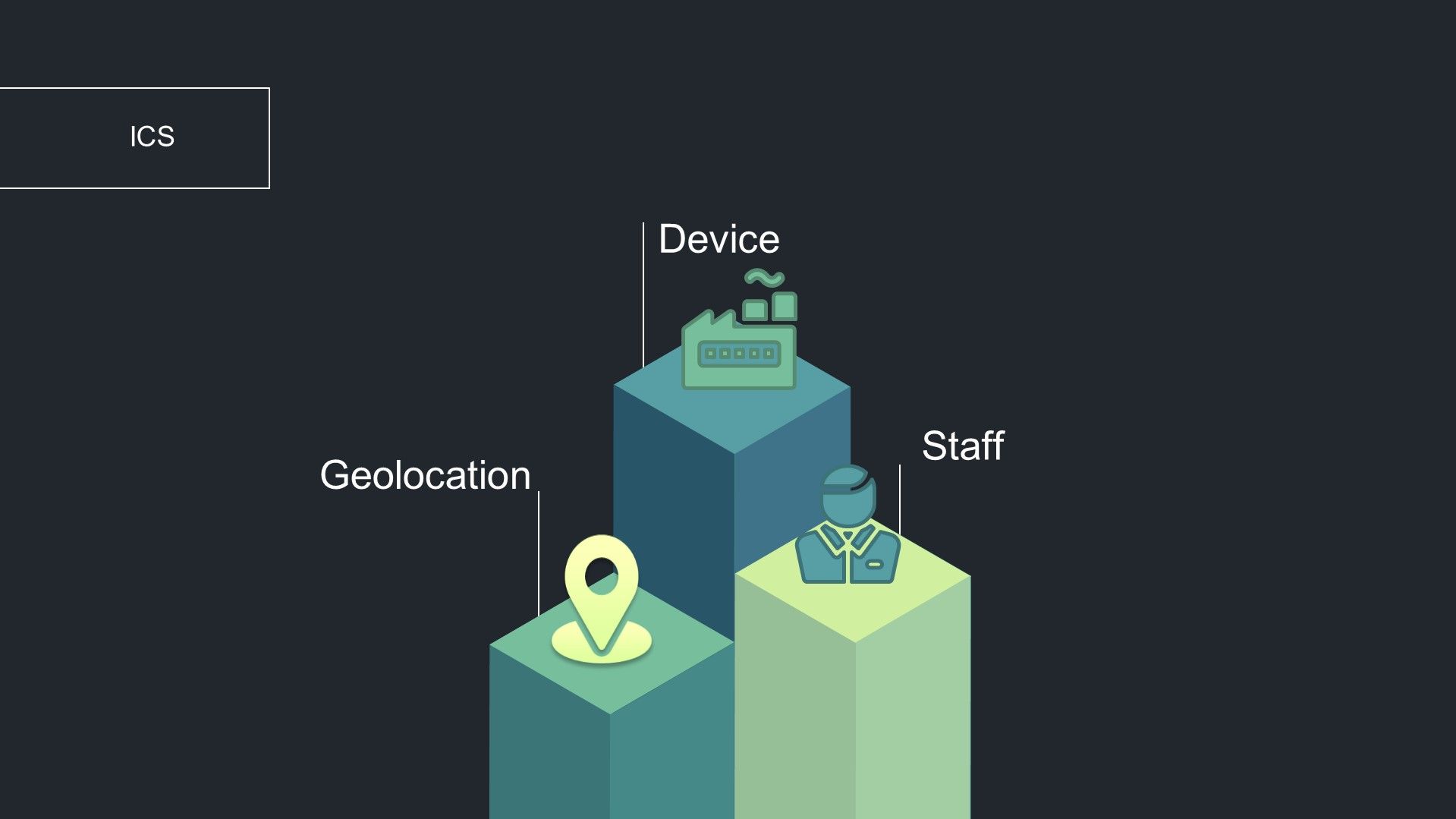
From device itself, attacker can gain enormous amount of information like vendor, model, vulnerabilities and also about whole machine - different ports or weaknesses. The login panel or WHOIS might reveal information about actual location of device or building that it exists in. From then we can move to exploring the physical security based on google maps, social media photos or history satellite views from @planetlabs. I also made a specific example of spear phishing attempt exclusively for ICS conference.
KAMERKA & SOUTHEAST ASIA
All of you may already know tool "Kamerka", in short words it's a platform to gather intelligence on ICS, IIoT and IoT devices based on coordinates or for a whole country. The conference research was also based on the Kamerka, I used it to collect all necessary data, draw charts and visualize it on the map. If you don't know the tool, you can read about it below.
Hack the planet with ꓘamerka GUI — Ultimate Internet of Things/Industrial Control Systems reconnaissance tool.
From now on ꓘamerka is not only simple script for mapping devices, it has evolved to fully equipped reconnaissance web application. It allows to visualize any country with Industrial Control Systems devices or particular territory with Internet of Things devices. Moreover, it supports Google Maps fo…
WojciechOffensive OSINT

Before going into specific critical infrastructure findings, let's take a look on a bigger view, i.e. statistics about exposed devices in Southeast Asia region. In Kamerka we have general dashboard, and it's presented below.
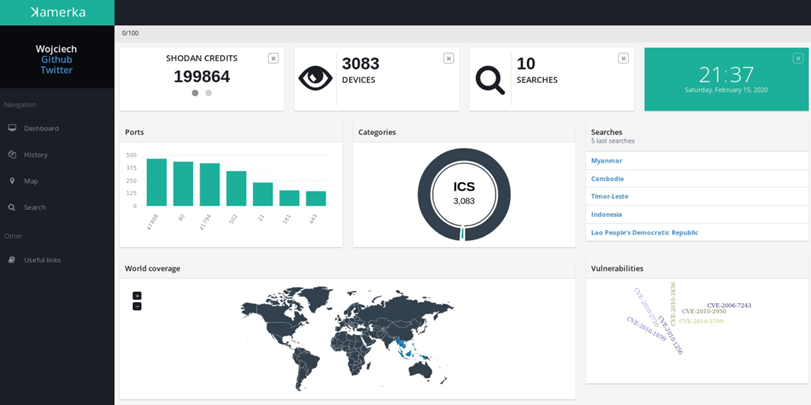
It also supports map for each search as well as for all devices. Map presents devices in Southeast Asia.
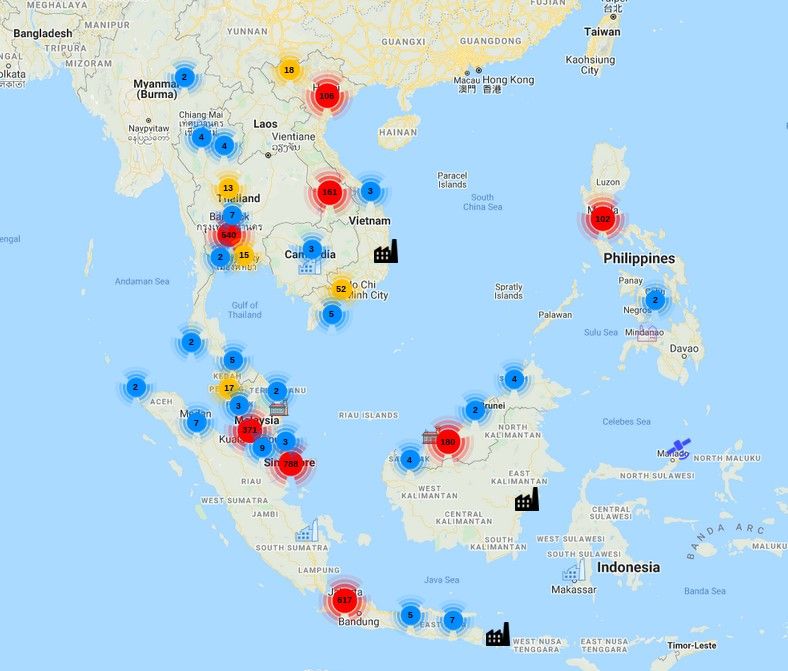
In addition, at the time of the research, 3 SAILOR 900 VSAT System were exposed and ships were located in Persian Gulf, Gulf of Oman and one parked in port in Sharjah, United Arab Emirates. To locate VSAT systems, Kamerka does not take an IP geolocation but scrapes precise coordinates from exposed VSAT panel management and put it in map.
I took 10 biggest countries in Southeast Asia and found 3083 exposed Industrial Control System devices. Chart below presents relationship between countries and amount of devices.
I omitted Timor Leste and Laos, due to completely lack of devices. Singapore is located on the first place however I came across many honeypots.
Next chart shows percentage of types and vendors used in ICS in Southeast Asia.
BACnet is the most popular and operate almost on 1/4 of all devices. Windweb (third place) is used by lot of embedded systems same as VxWorks. In this region, there are 82 Bosch security systems exposed which are vulnerable to RCE. Whole list of queries and devices in Kamerka is accessible below.
woj-ciech/Kamerka-GUI
Ultimate Internet of Things/Industrial Control Systems reconnaissance tool. - woj-ciech/Kamerka-GUI
woj-ciechGitHub
The most used ICS ports
On port 161, different Lantronix devices listen but also it's on the chart due to Singapore's honeypots. One of the example of such trap (below) impersonates Simatic device on port 161.
68.183.228.248
Ports open: 23, 37, 84, 102, 104, 161, 175, 311, 389, 1433, 1599, 1741, 2222, 2404, 3310, 4664, 4786, 4848, 5560, 5601, 5672, 5938, 5986, 7071, 7171, 7657, 8087, 8139, 8334, 8800, 8880, 9000, 9009, 9042, 9530, 9600, 9869, 9944, 9981, 10001, 21379, 27015, 32400, 52317, 54138, 55442, 60001

Statistics are needed if someone thinks about developing exploits for mass exploitation specific country. If one country targets Indonesia where Crestron is most common device, it's reasonable to put most effort and money to look for vulnerabilities in this particular device/vendor.
Armored with the map, statistics and information about each host we can start digging. Actually a lot of interesting data can be retrieved from such a broad perspective.
Some of the devices might actually operate in the critical infrastructure but nothing from OSINT perspective points to this conclusion, no precise WHOIS information, no hostname or lack of any indicator in login panel.
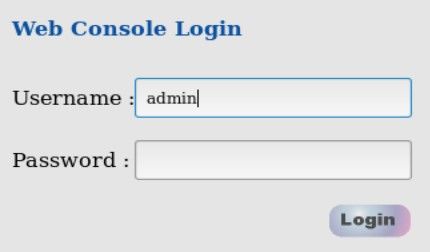
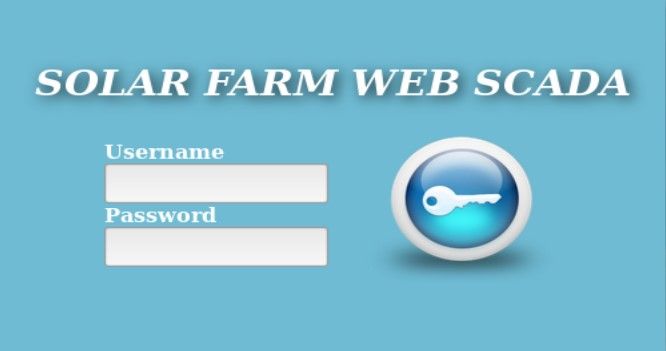
From the other hand, many panels contain information useful to geolocate device, in many cases it's name of the facility or physical address.

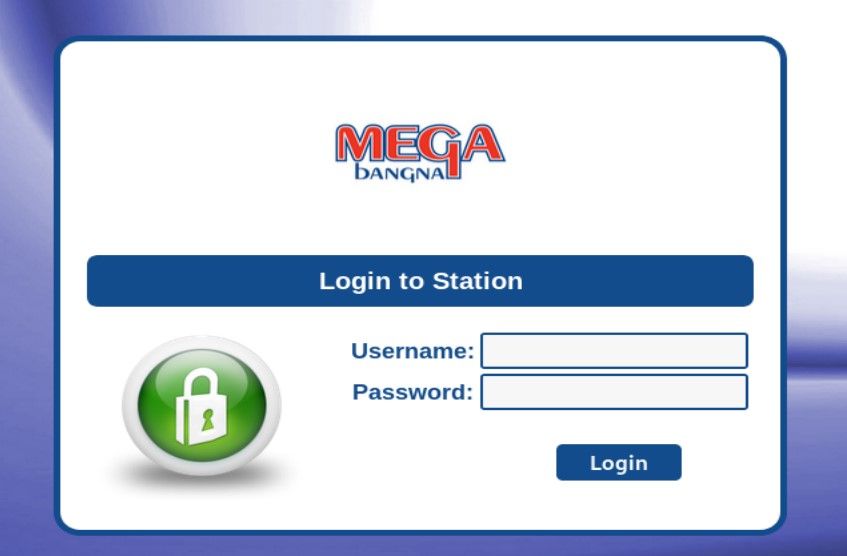
First station belongs to University Sains Islan in Malaysia and second one to Mega Bagna - shopping centre in Thailand.
And there is a third type of exposed device, which gives access to the information that should't be disclosed. Majority devices are behind authentication and allow only to read the data but it's a trove of information in terms of getting inside knowledge about potential target - organization or physical building. To get a full access nothing will stop bad actors from exploiting existing vulnerability or try bruteforcing password.
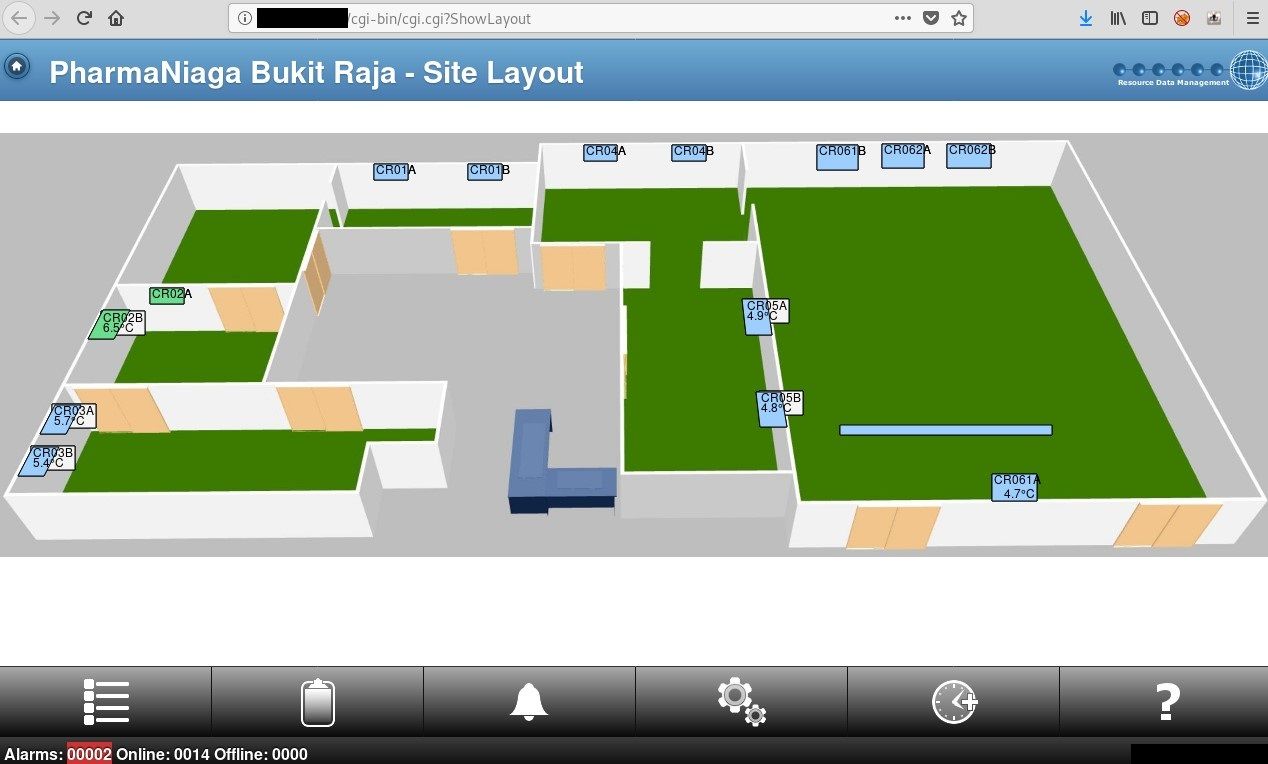
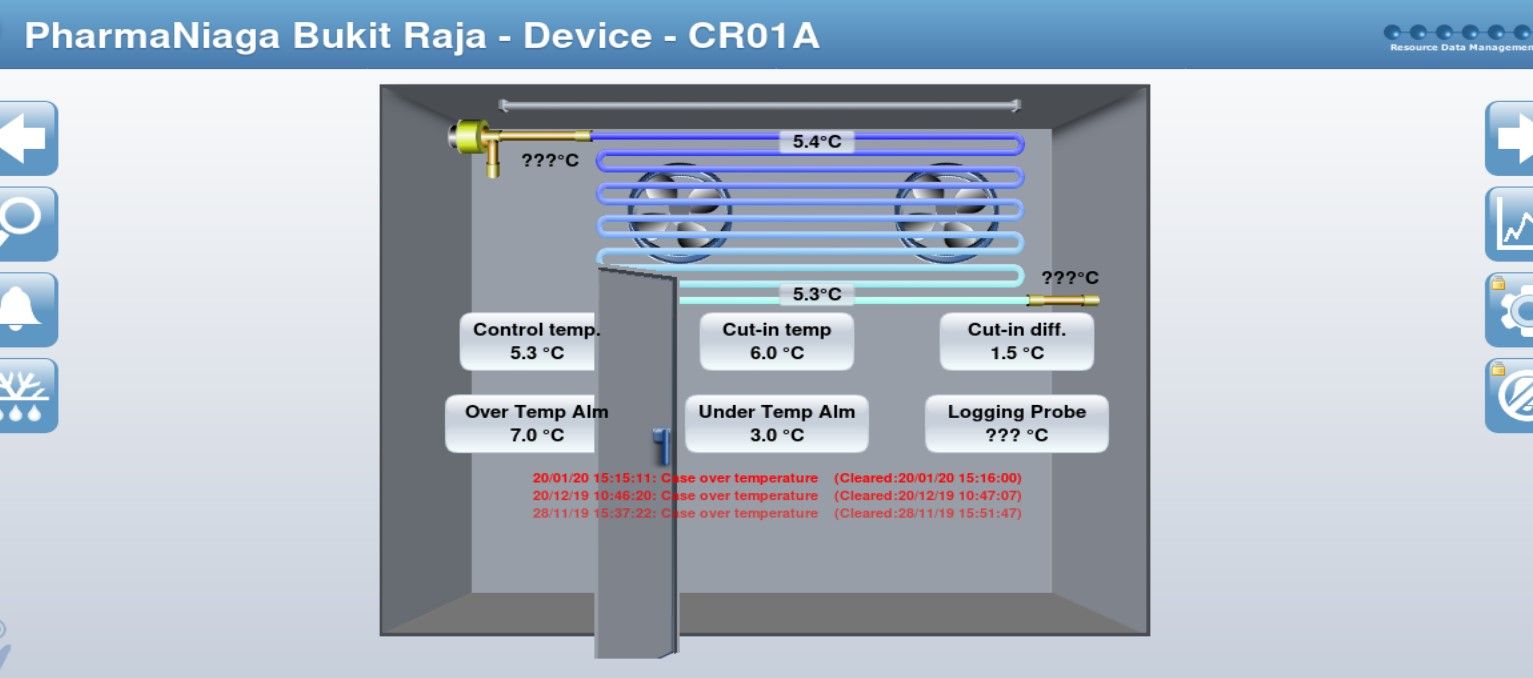
Above panel management is responsible for operating in pharmacy in Malaysia and discloses information about heating, ventilation, air conditioning, refrigeration (HVACR) and Building Management System (BMS) in general.
Another example may be Wiser for KNX (homeLYnk) which is a personalized home automation solution, offering a complete system based on open protocols like KNX, Modbus, BACnet and IP. It's registered to pharmaceutical company in Indonesia - Novo Nordisk.
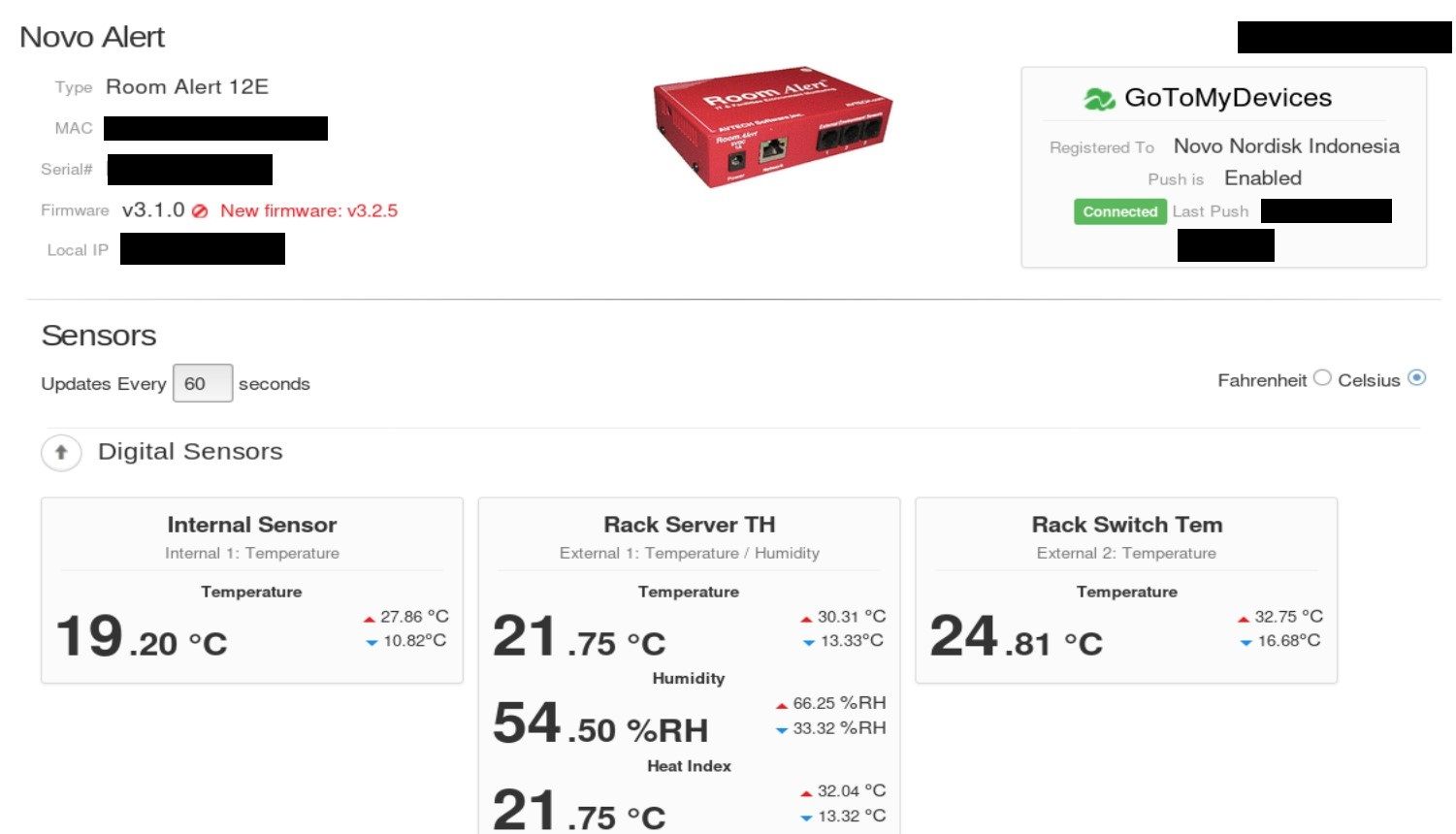
I could give plenty of this kind of examples but we are here to catch the big fish and find device in critical infrastructure that disrupting might cause inevitable damage to the society.
KAMERKA & CRITICAL INFRASTRUCTURE IN SOUTHEAST ASIA
No device has been compromised.
No damage has been caused.
Findings have been reported.
So right now we are looking for anything that might be operating in one of the 16 sectors mentioned earlier. It can be a device in power plant, waste water plant, hospital, laboratory or research facility. It's a huge battlefield with many creative possibilities to obtain information and find potential entry point or target personnel.
Indicator in login panels, seen above, it's only one example of possible geolocation device and building itself. Kamerka extracts these indicators from:
- Niagara Fox - Station Name,
- NMEA - exact coordinates,
- Ships - exact coordinates,
- Tanks - physical address,
- BACnet - projects name
You can find additional indicators in hostname, certificates, users, email addresses, WHOIS information or in device itself.
Choa Chu Kang Waterworks
Part one of the research "Gathering Intelligence on Critical Infrastructure in U.S." was mostly based on exposed Niagara Fox stations. First finding shows what FBI warns about - port 1911, and it's information disclosure.
FBI warns industry that hackers could probe vulnerable connections in building systems
Kamerka found 3 IP addresses in Singapore with exposed port 1911 and "CCKWWSolar" in theirs station name.
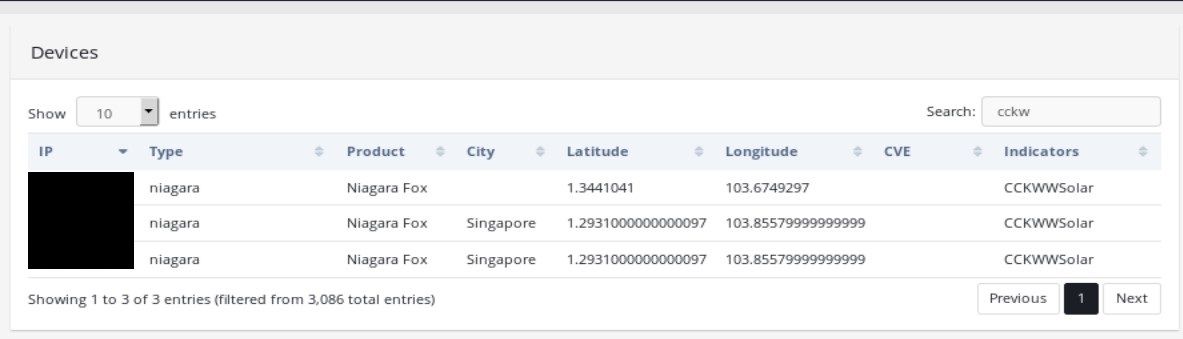
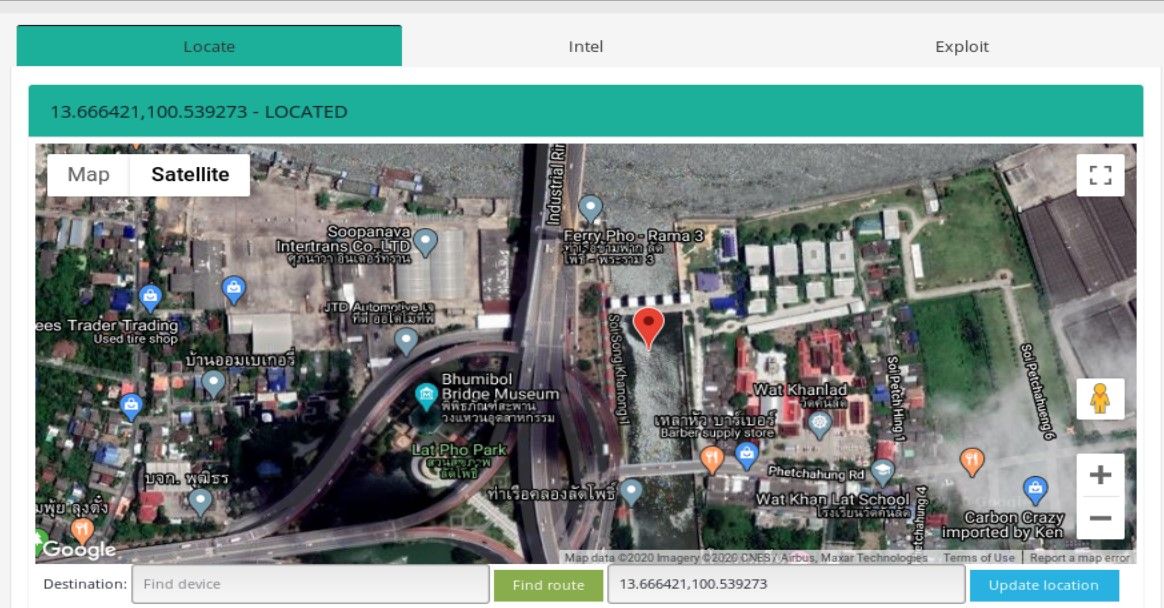
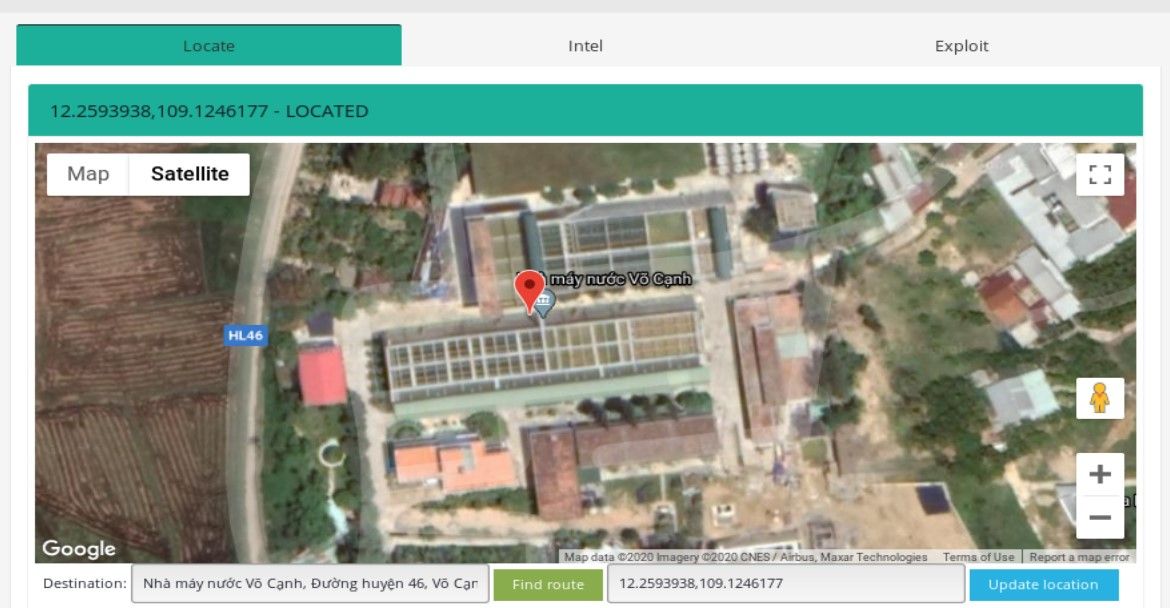
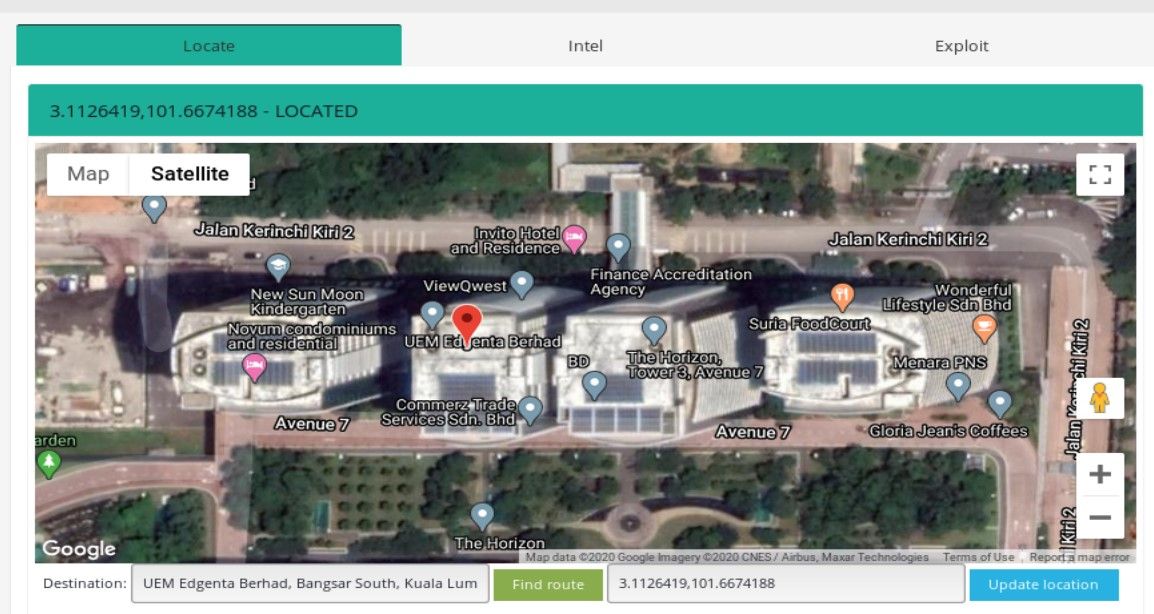
I learned a lot about different infrastructure in Asia thanks to decoding many abbreviations and googling their meaning that were completely unknown for me. It turned out that CCKWW means Choa Chu Kang WaterWorks, sounds interesting enough so I decided to investigate it deeper. First thing is to geolocate actual facility. Kamerka makes it very easy, switch to Locate tab and write facility in google maps search form, click green button to draw the route, get coordinates and type them into "update location" field.
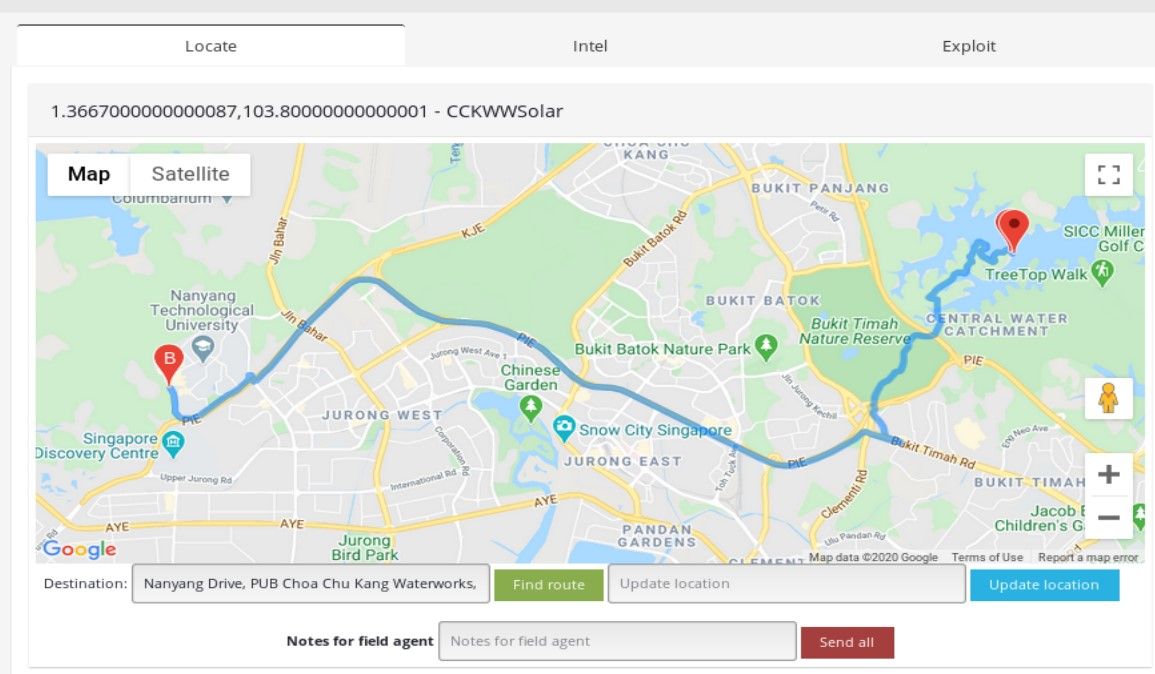
Then click blue button. After that, some tabs will turn green meaning device has been located. You can take a closer look by zooming and switching to satellite view.
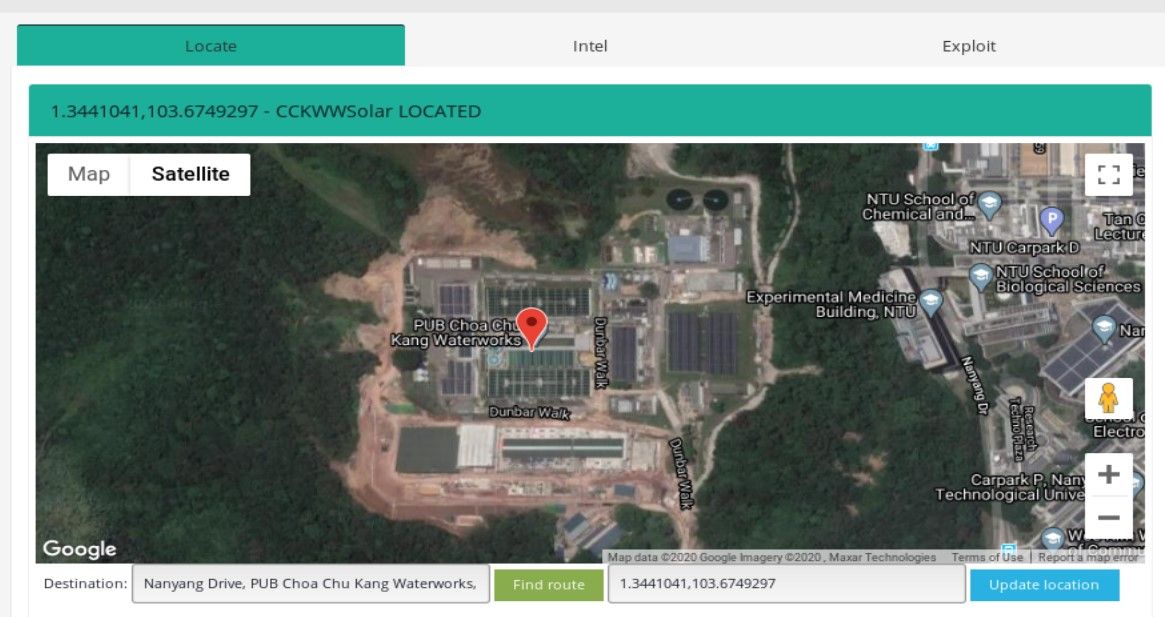
You should always rely also on manual research by finding any possible information and photo about facility. It might be related to financing, board members, building plans or photos that shows internal infrastructure like rooms or servers.
Satellite photos shows many solar panels and three IPs related to the solar infrastructure are directly accessible via the Internet.
Article from straitstimes.com indicates installation of more than 3,300 solar panels in the Choa Chu Kang Waterworks on 25th of June, 2015.
Choa Chu Kang Waterworks now powered in part by solar energy
National water agency PUB’s Choa Chu Kang Waterworks is now run partially by solar energy, after the installation of more than 3,300 solar panels.. Read more at straitstimes.com.
 SAMANTHA BOHThe Straits Times
SAMANTHA BOHThe Straits Times

To see where solar panels have been added and how facility has been rebuilt we can use planetlabs history satellite views. Below is a comparison showing physical changes since 2015.
We can clearly see where solar panels have been mounted and what attacker can potentially compromise.

Royal Irrigation Department - Lat Pho Canal
mySCADA offers the smart visualizations which help to control and optimize the production. mySCADA gives the possibility to control from anywhere, anytime.
Niagara Fox discloses a lot of information by default but it's mostly related to the device, i.e. model, vendor, operation system or version of virtual machine. Panels of mySCADA product display more than it should if not properly configured. Non-authenticated users can take a inside look into information about whole infrastructure used by the application. One of the example can be Lat Pho Canal managed by Royal Irrigation Department in Thailand.
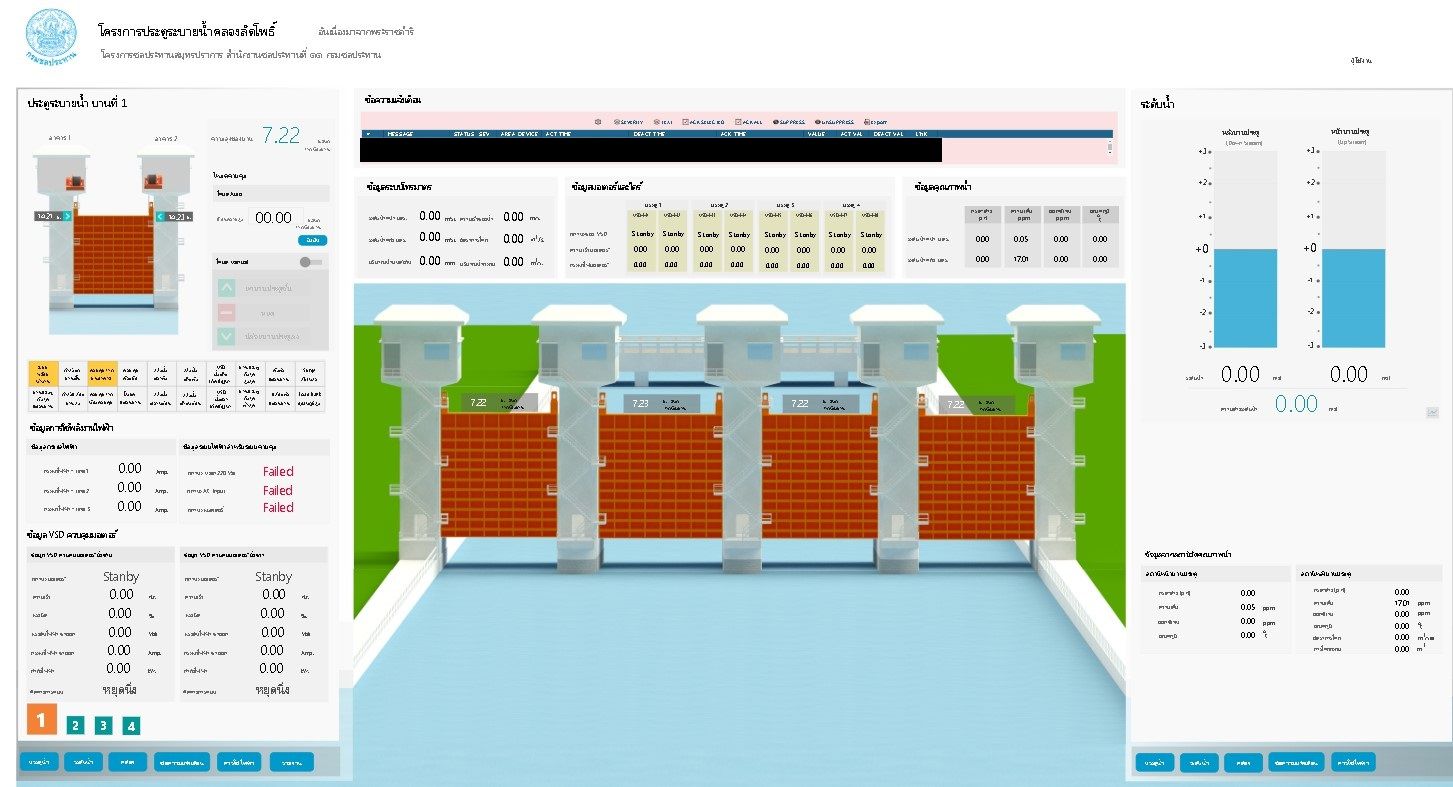
As you can see, mySCADA application supports dams on one of the rivers in Thailand, disclosing many interesting information at this same time. First we have a (polyphonic music!) graphical interface including image of dams, data and charts.
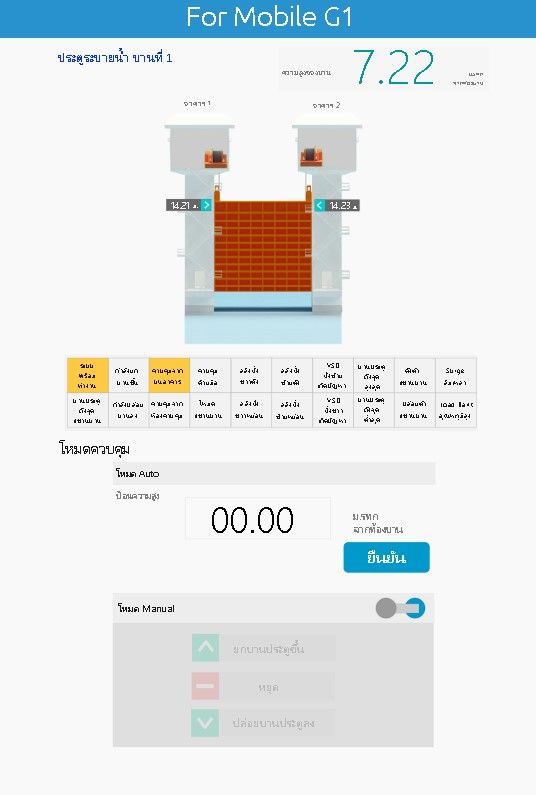
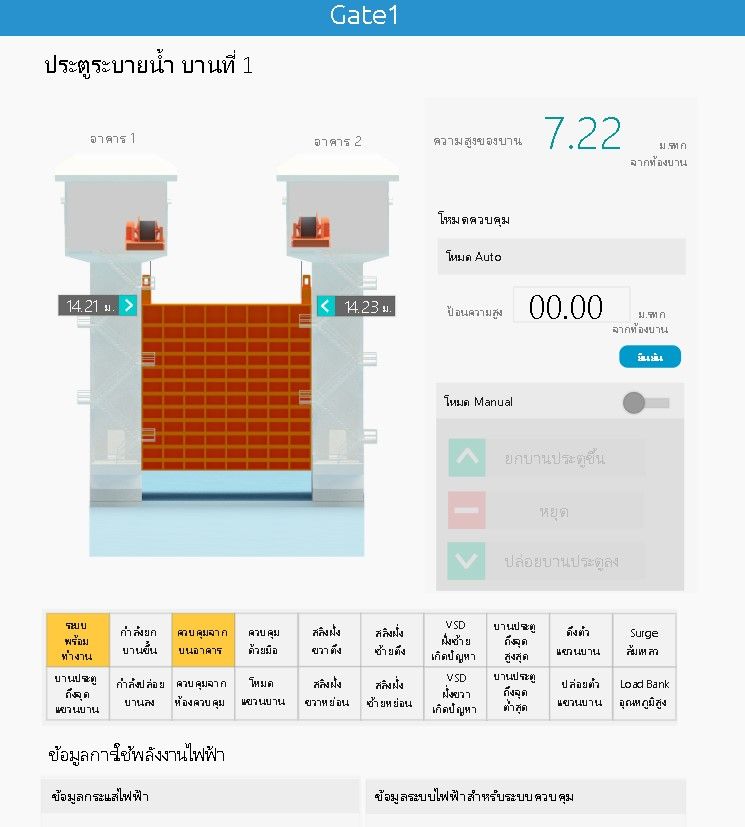
It also gives access to each dam and possibility to manage for authenticated users. For people knowing architecture of specific infrastructure and operating software, it's easy to fully take the management over and cause damage or gather espionage information like device condition or alarms.
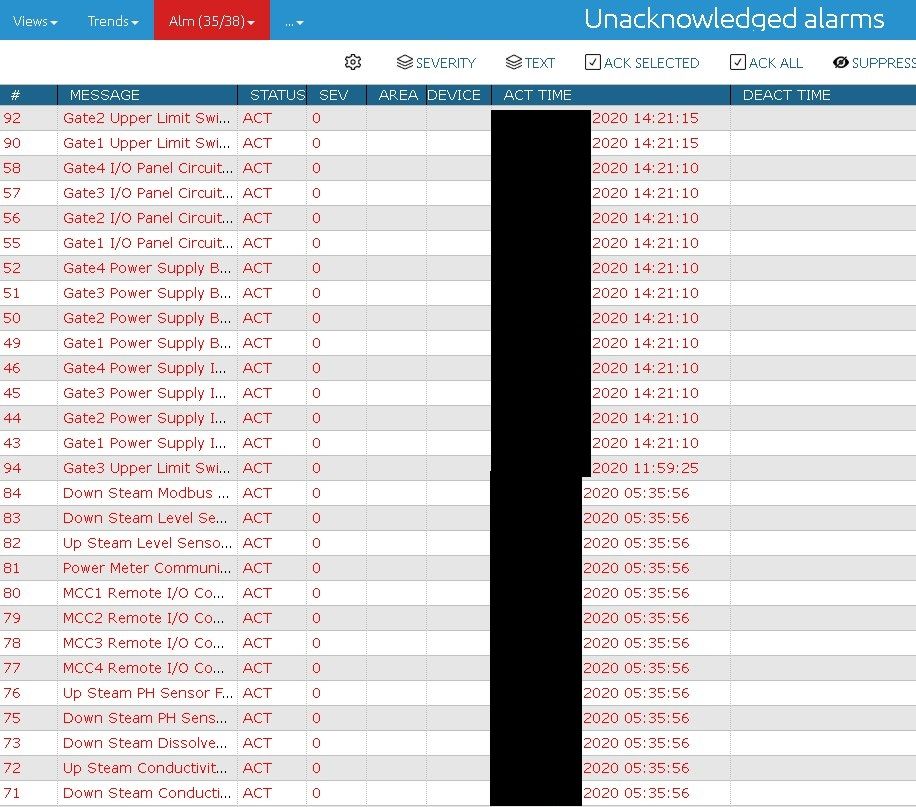
As always, manual research is needed to confirm location of the place, gather more details and estimate potential damage that might be caused for the society.

Description suits to the image of dams from mySCADA application and now we also know more about use of the infrastructure. For sure it counts as a critical infrastructure and additionally can be used to generate electricity. Next step in cyber attack would be to collect as much information about staff as possible. In the top-left corner of mySCADA application, logo of Royal Irrigation Department is present.
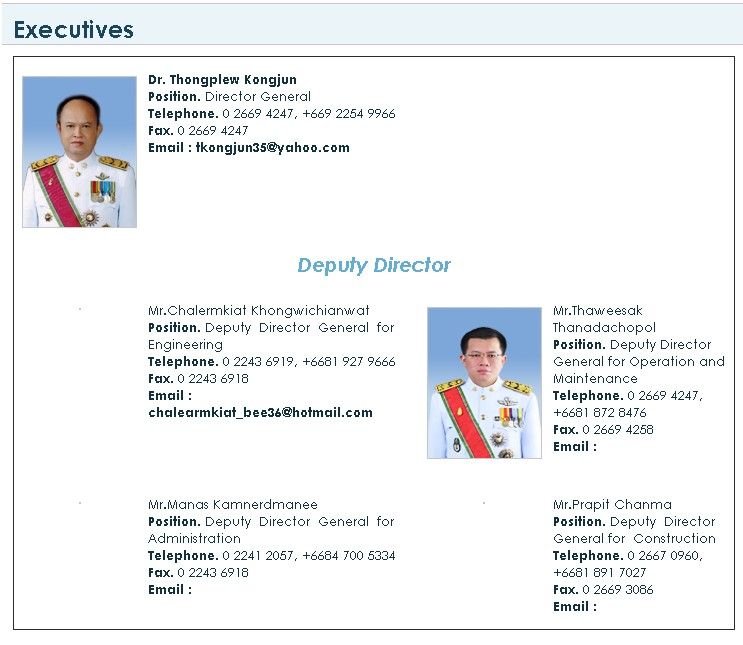
From official government website we can learn that executives still use yahoo and hotmail domains for related management things. Checking password dumps for these particular emails and used it for 'privilege escalation' sounds like a first thing that attacker would think of.
We can't forget to update location in Kamerka and check how it looks like in Google Images/Maps.

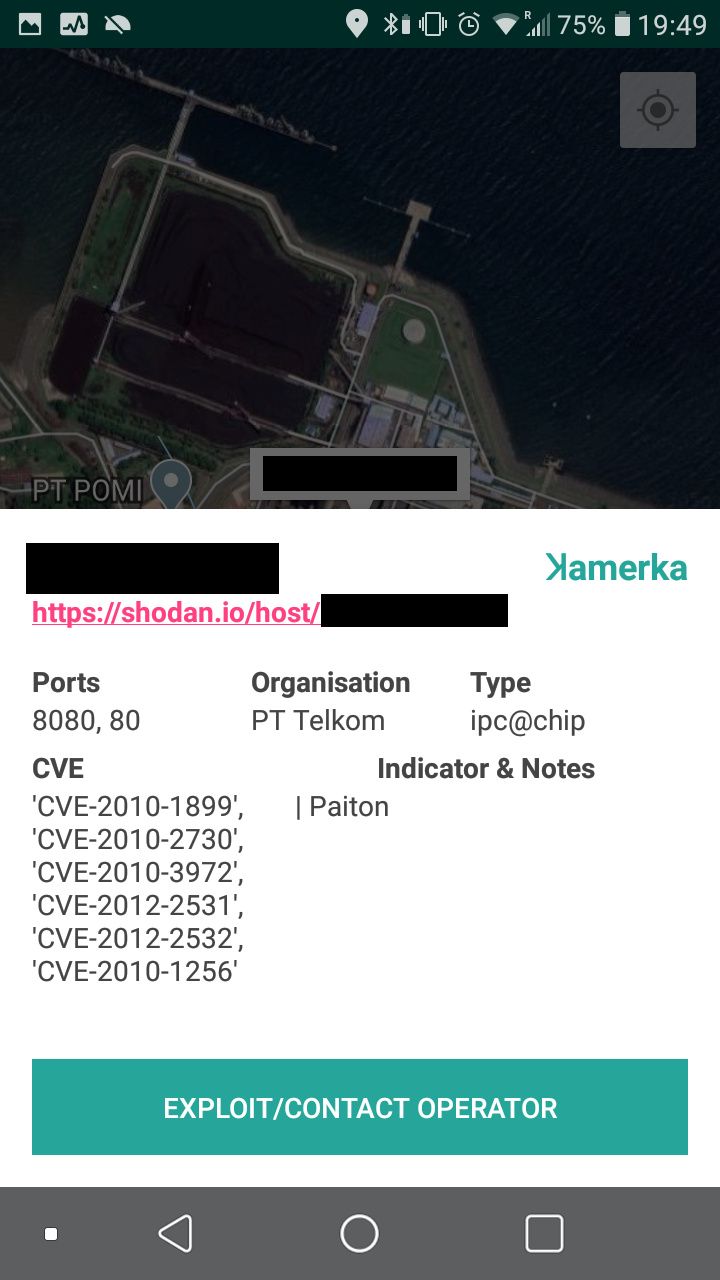
Paiton Power Station - PT. Jawa Power
This findings is not sophisticated but I put it here because it's the largest energy power plant with exposed devices I found.
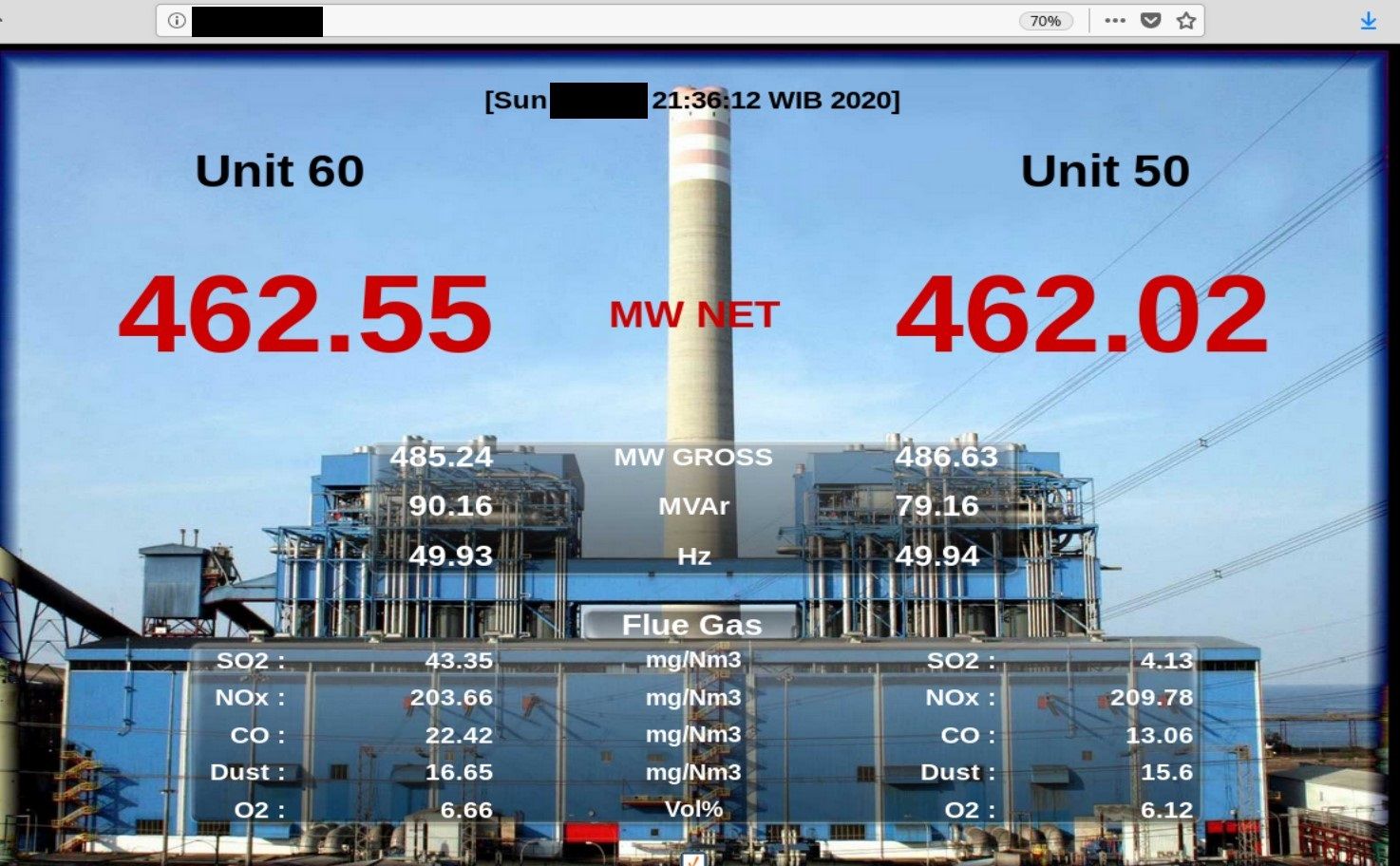
The extensive complex has a maximum generating capacity of 4,710 megawatts. It is the largest power station in Indonesia and the 10th largest coal-fired power station in the world.
It is a HTML website with embedeed JAR file, probably for remote connection however it was not accessible during time of the research.
In addition, another exposed port on this same machine reveals Solar-Log 1200 device.
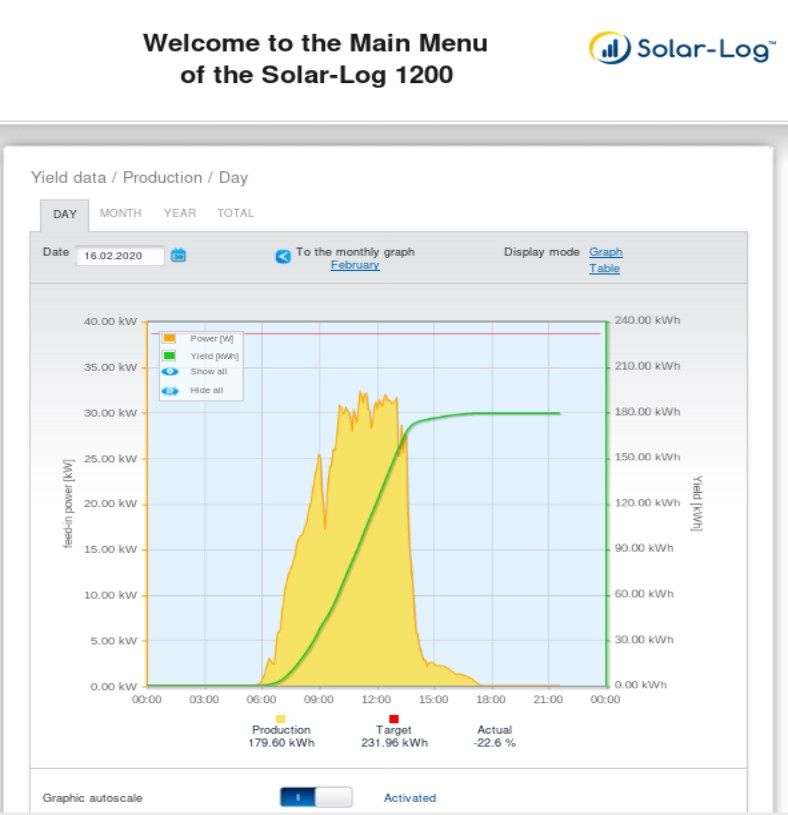
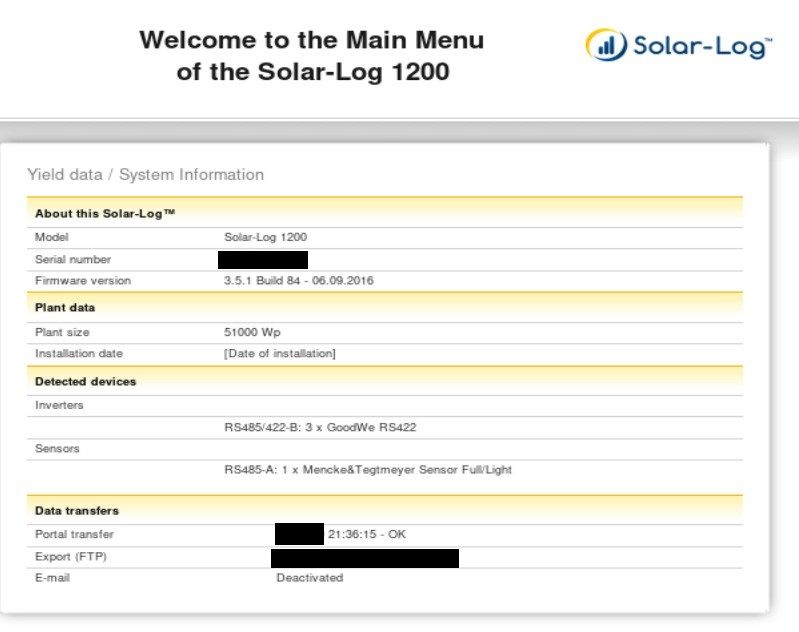
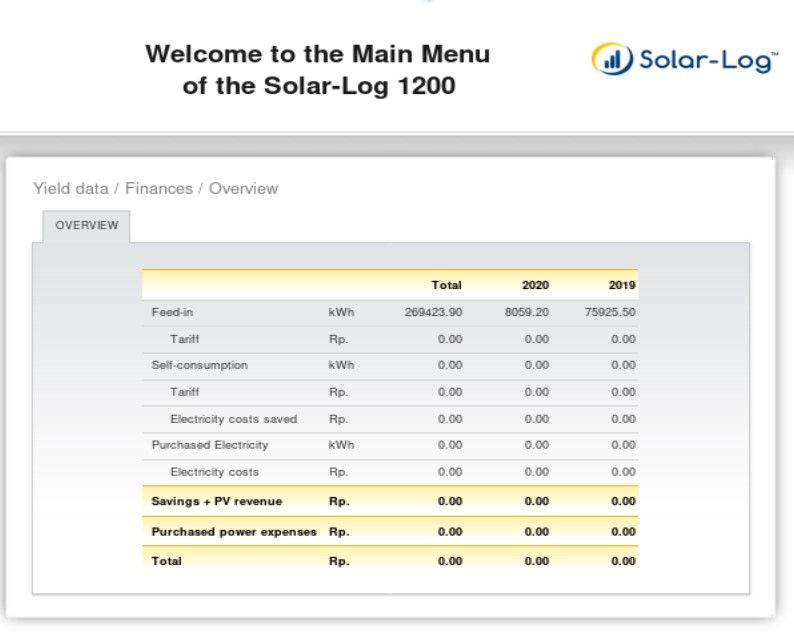
It gives inside view into statistics, finances, used firmware or inverter details.
We need to update location in Kamerka.
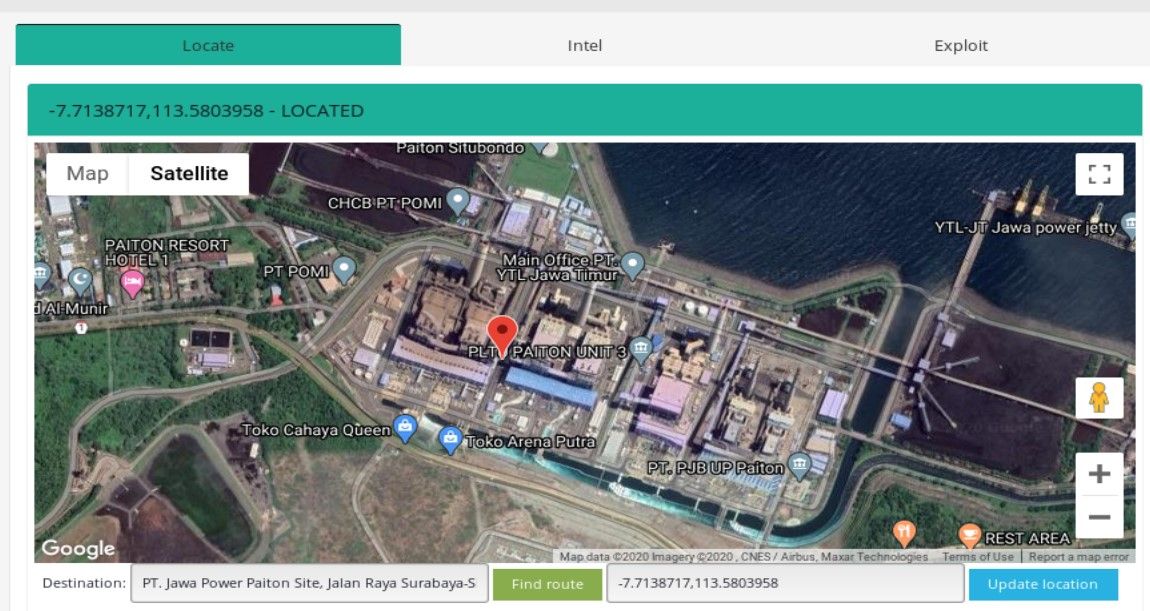
Below photo presents perfectly exact spot where photo from website was taken. It was in front of the first blue building, in the background there are two smaller units and one big chimney.

Water Treatment System - Võ Cạnh
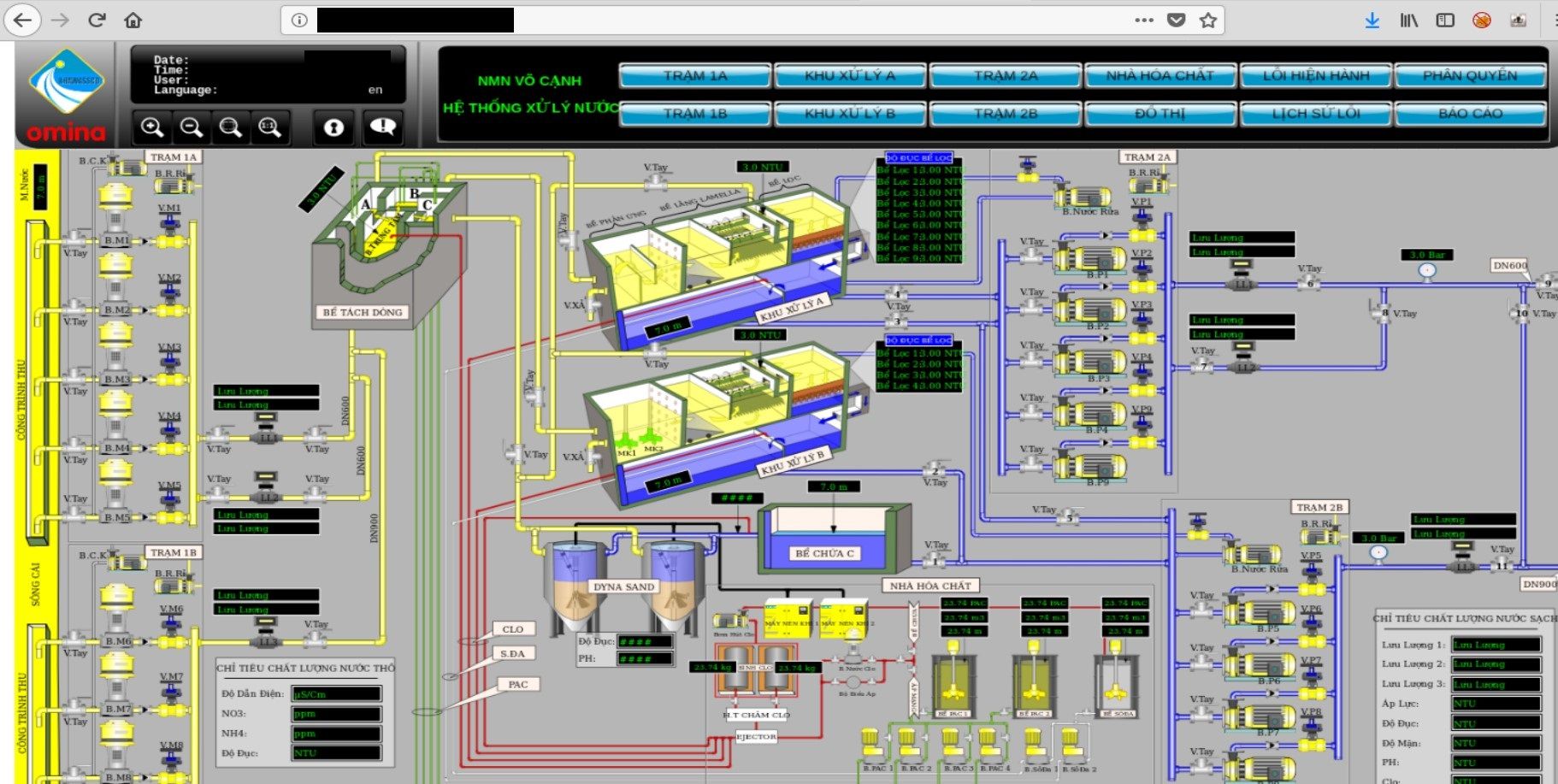
The Atvise® portal provides secure access on decentralized distributed plants and processes over the Internet (private cloud).
Water sector is another one in critical infrastructure and is responsible for filtration and improving water. In next step it is distributed for drinking, irrigation or industrial water supply. No doubt that disrupting process of such facility would cause suspension in operating and supplying.
In this case, Atvise portal was not properly secured and gives access to each pump station, handling areas, blocks or chemicals storage.
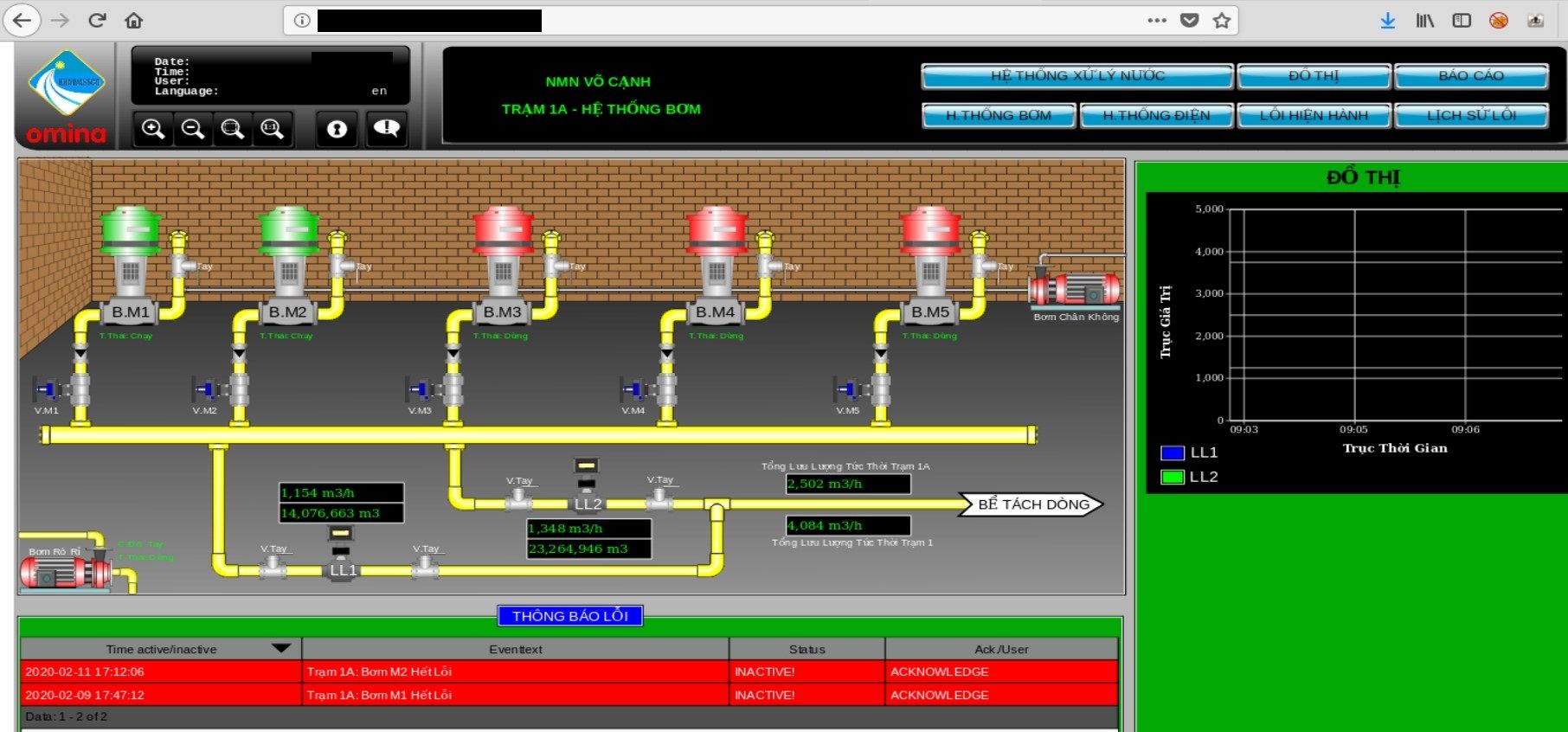
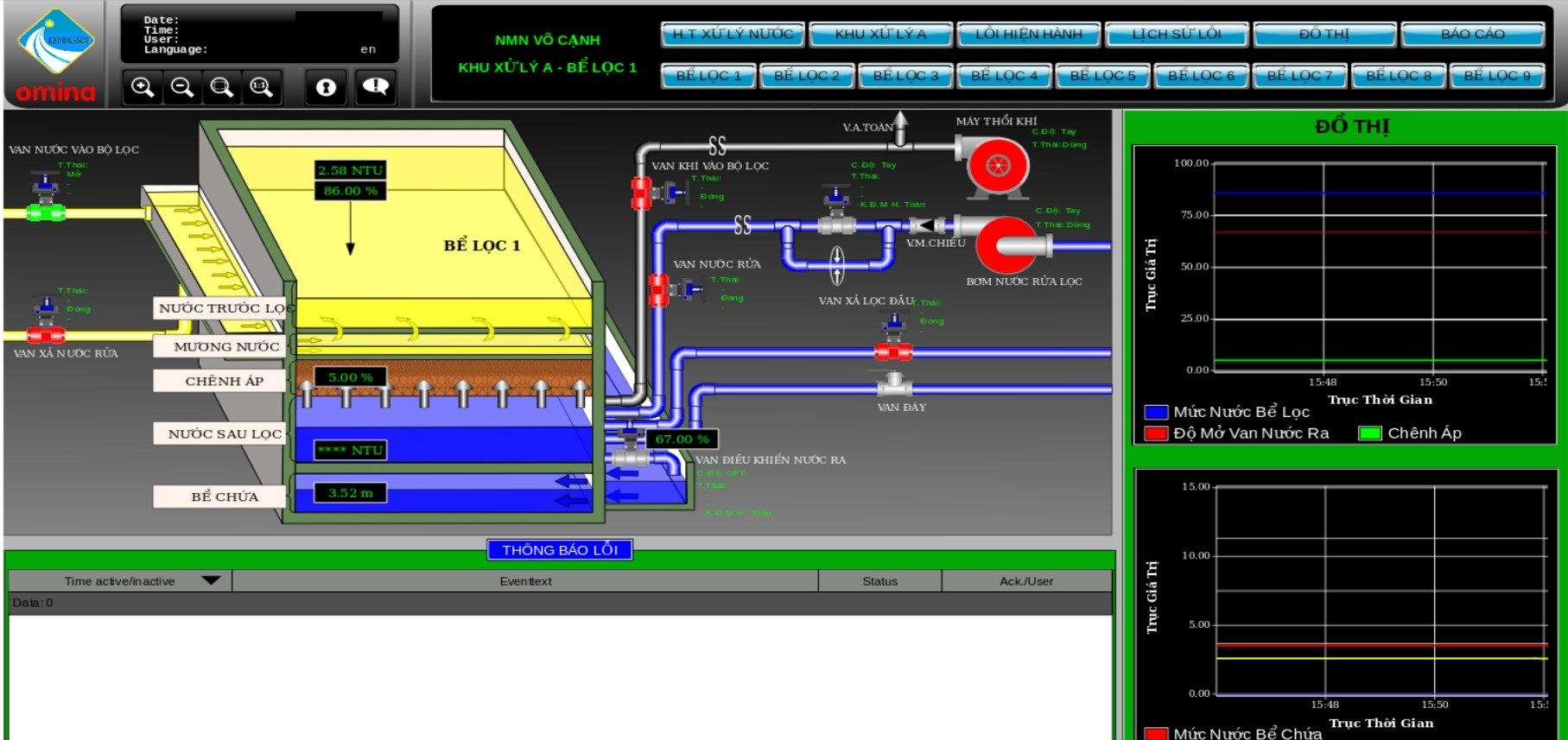
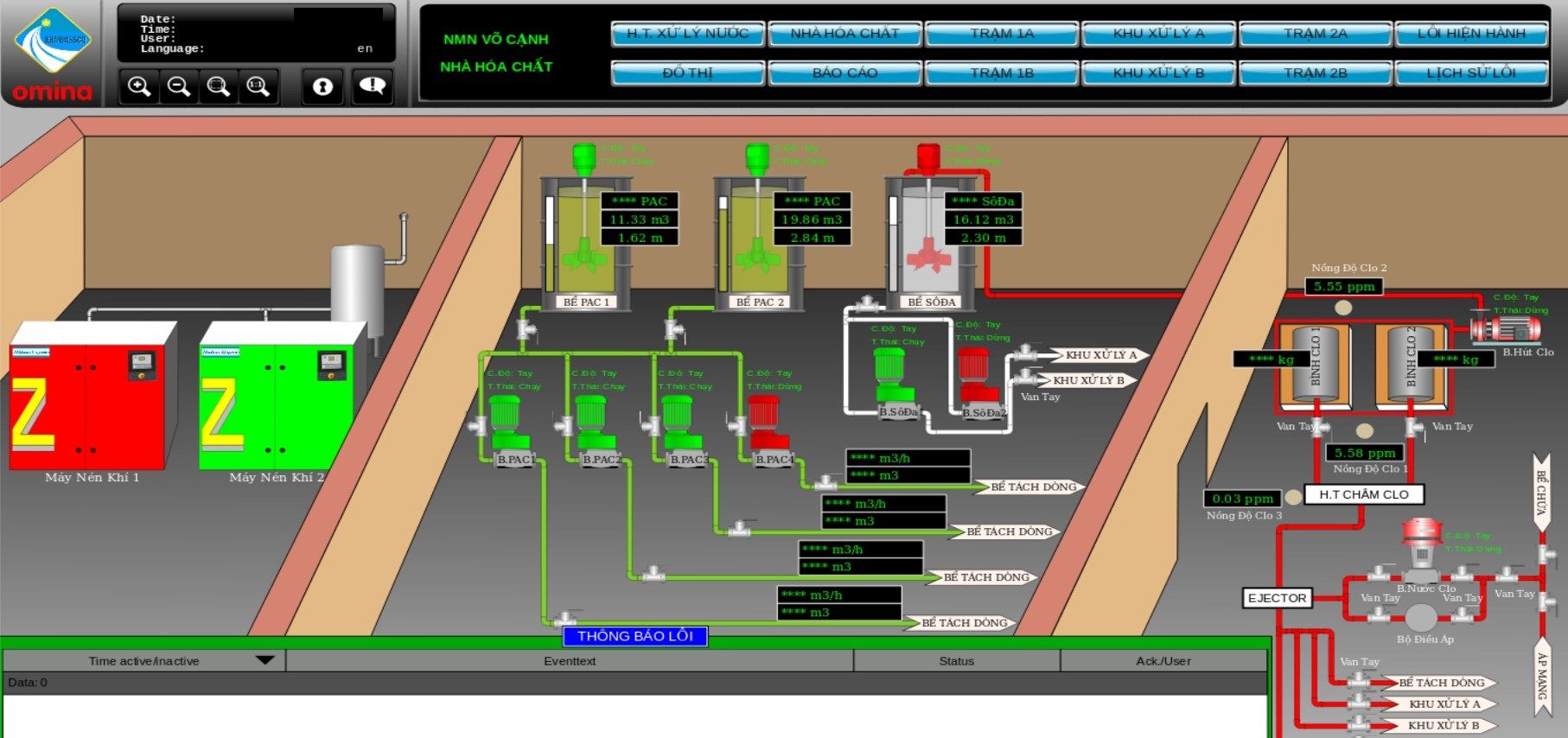
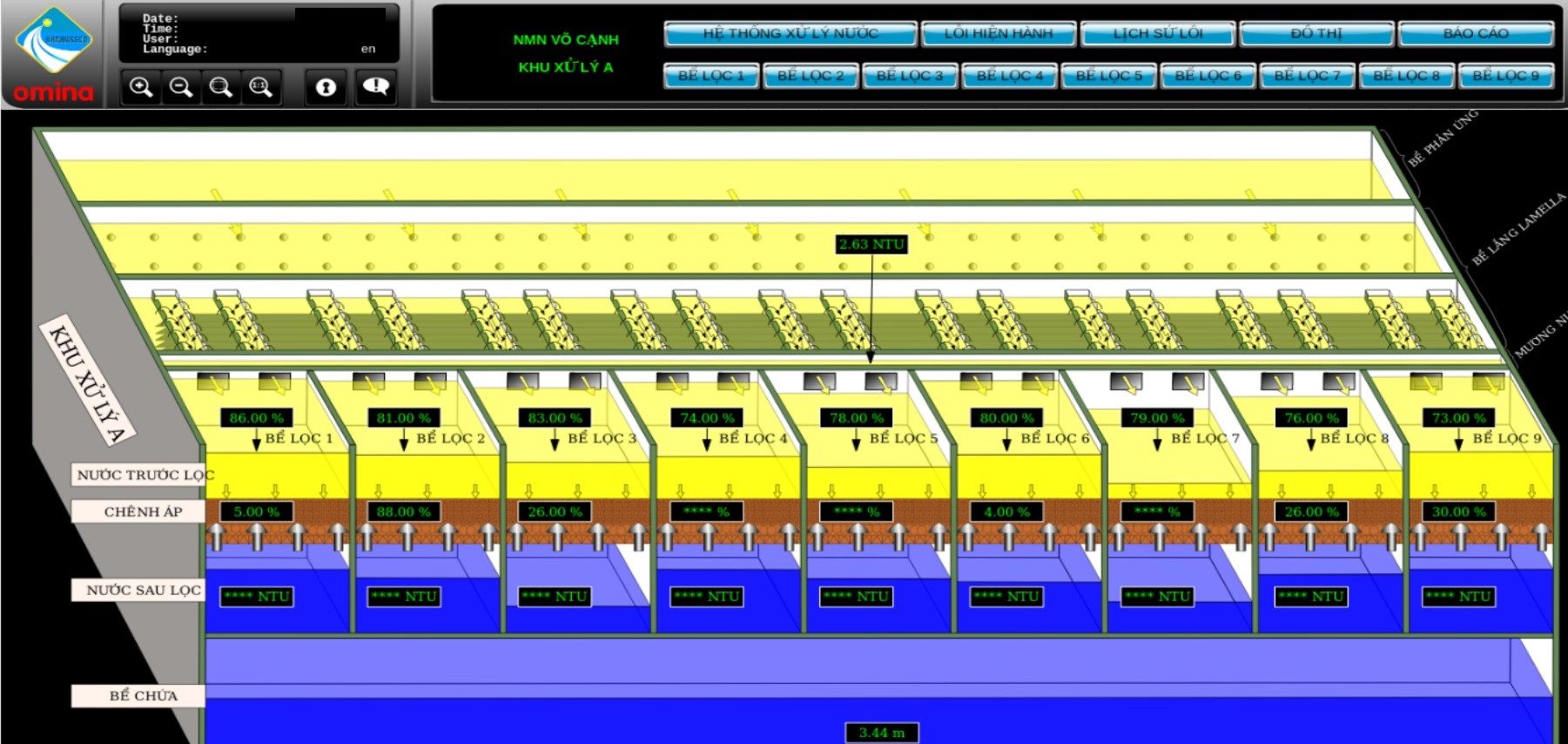
It's definitely too much information exposed, attacker can get insight about processes, systems or devices used in the plant.
The owner of infrastructure is Khawassco which operates in Vietnam and provides following services
http://ctnkh.com.vn/view.aspx?id_mn=18&id_p=24&parent=7
- Produce and supply clean water.
- Survey, design of focal works and water supply and drainage network system.
- Construction and installation of focal works and drainage network system.
- Consulting, verifying design of network and works of water supply and drainage pumping station
- Management and development of Nha Trang city drainage system.
- Set up investment projects of water supply and drainage works.
- Collecting tanks (septic tanks) to households.
- Supervision of construction of water supply and drainage works of class 2.
- Testing water meters from 15mm - 50mm.
From their official website we can confirm that water treatment system in Võ Cạnh belongs to them.
Not much online information is available about this plant, I found one picture from 2016 and corresponding article
Lãnh đạo tỉnh kiểm tra tình trạng thiếu nước trên sông Cái
Chiều 22-4, ông Trần Sơn Hải, Phó Chủ tịch Thường trực UBND tỉnh Khánh Hòa cùng đoàn công tác đến kiểm tra mực nước sông Cái và đập ngăn mặn tại chân cầu Vĩnh Phương (TP. Nha Trang).



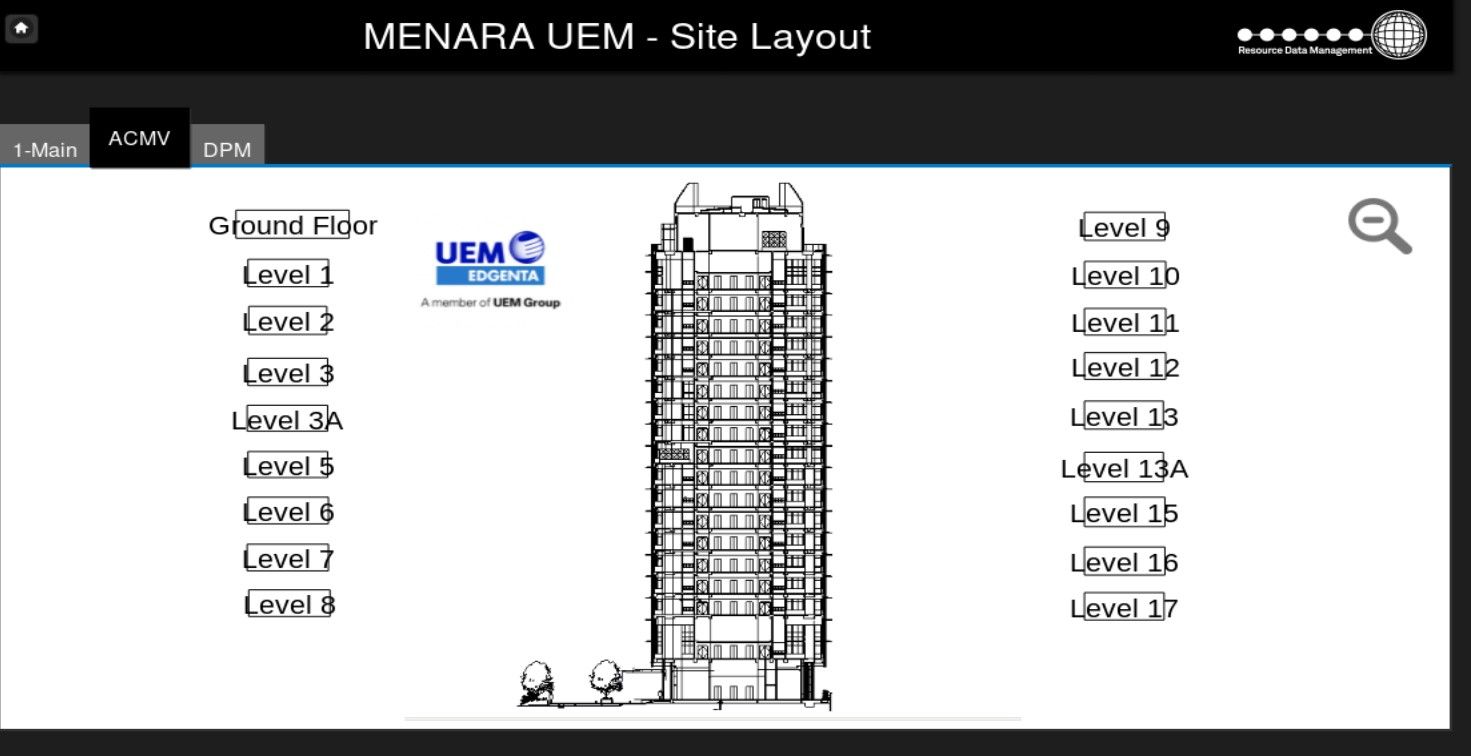
UEM Edgenta Berhad - Menara UEM Tower
The Intuitive TDB controller can be used in a variety of applications, for example HVAC, BMS, Refrigeration, Lighting and Energy, to enable monitoring and/or control.
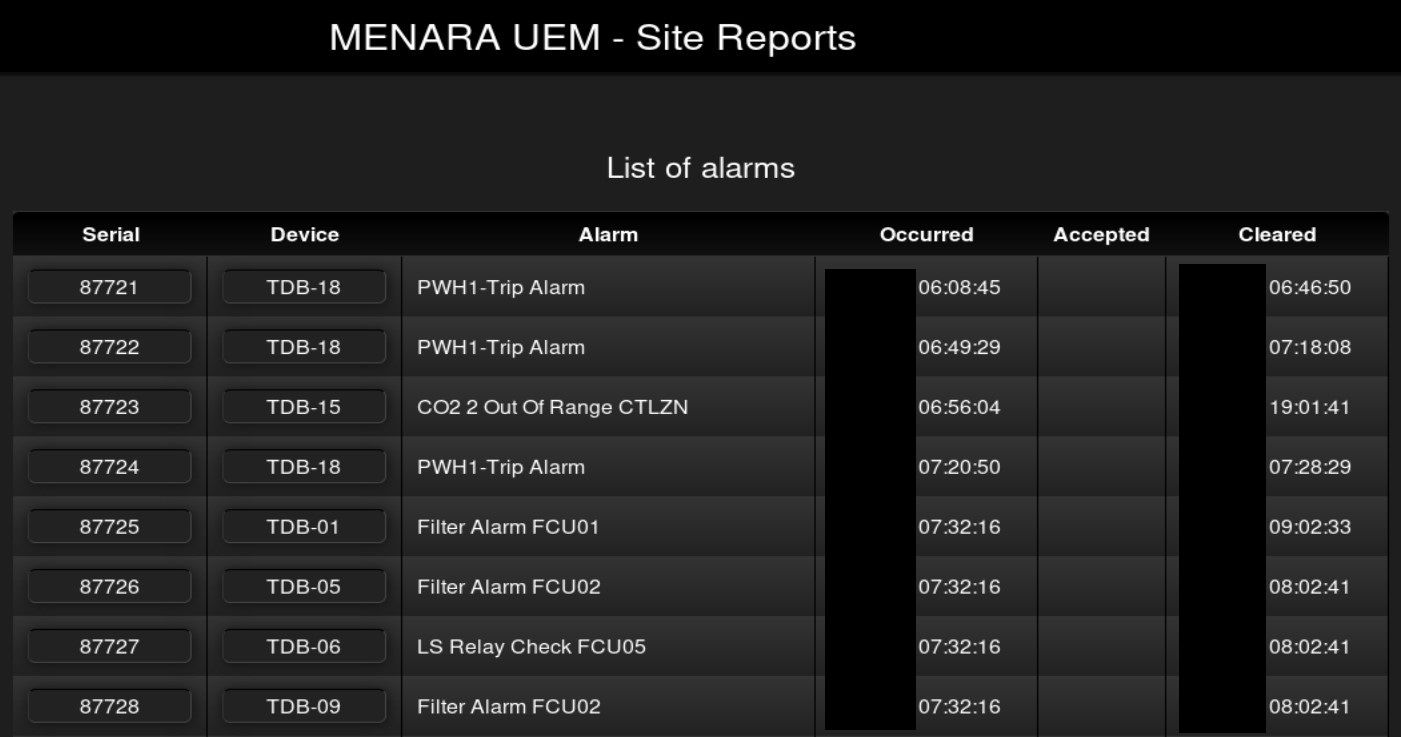
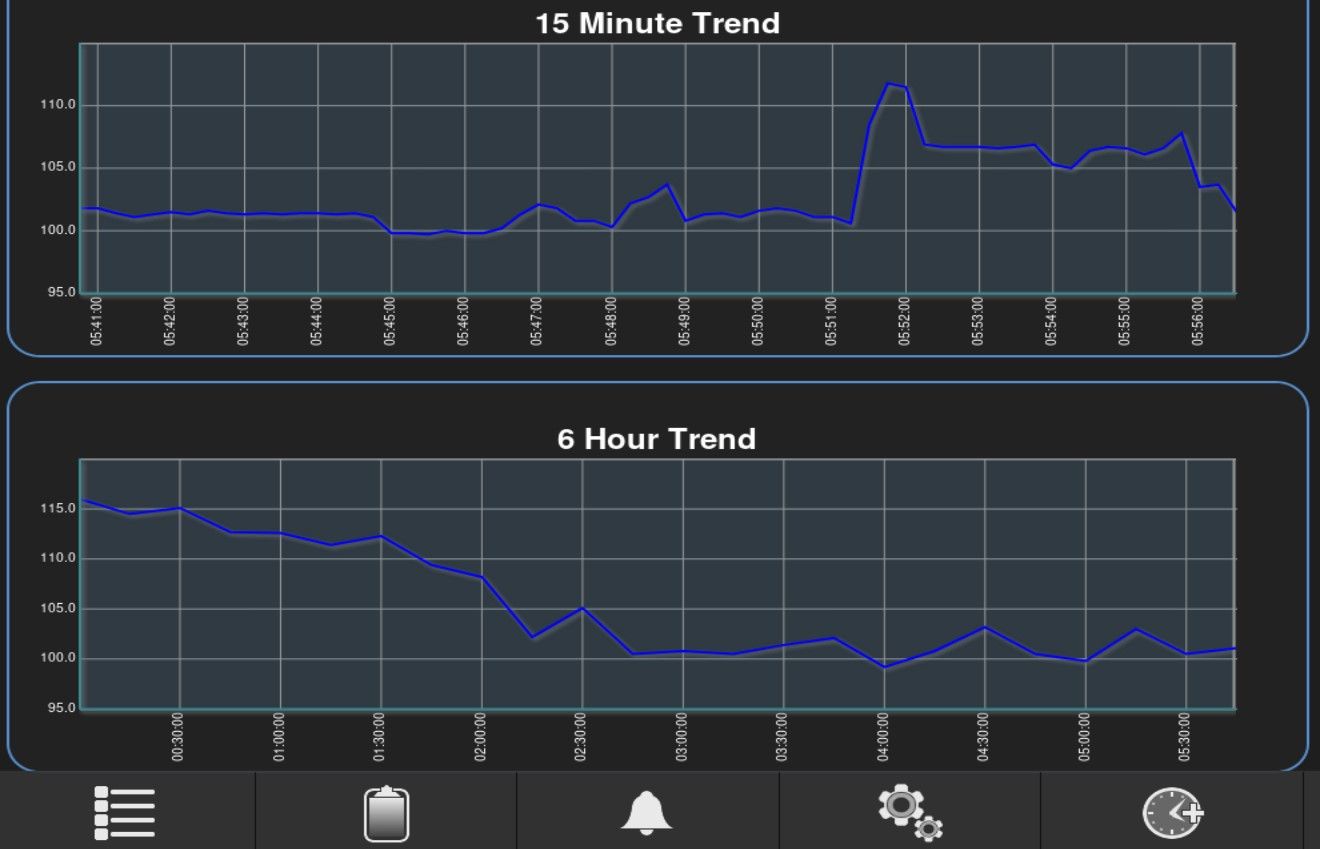
It's common to find exposed smart home or building operation workstations but it's the first time when I found building this size. Anyone can access variety of information about building - energy, heating, ventilators or lighting. In includes live data consumption, statistics, graphs or most interesting finances and budget.
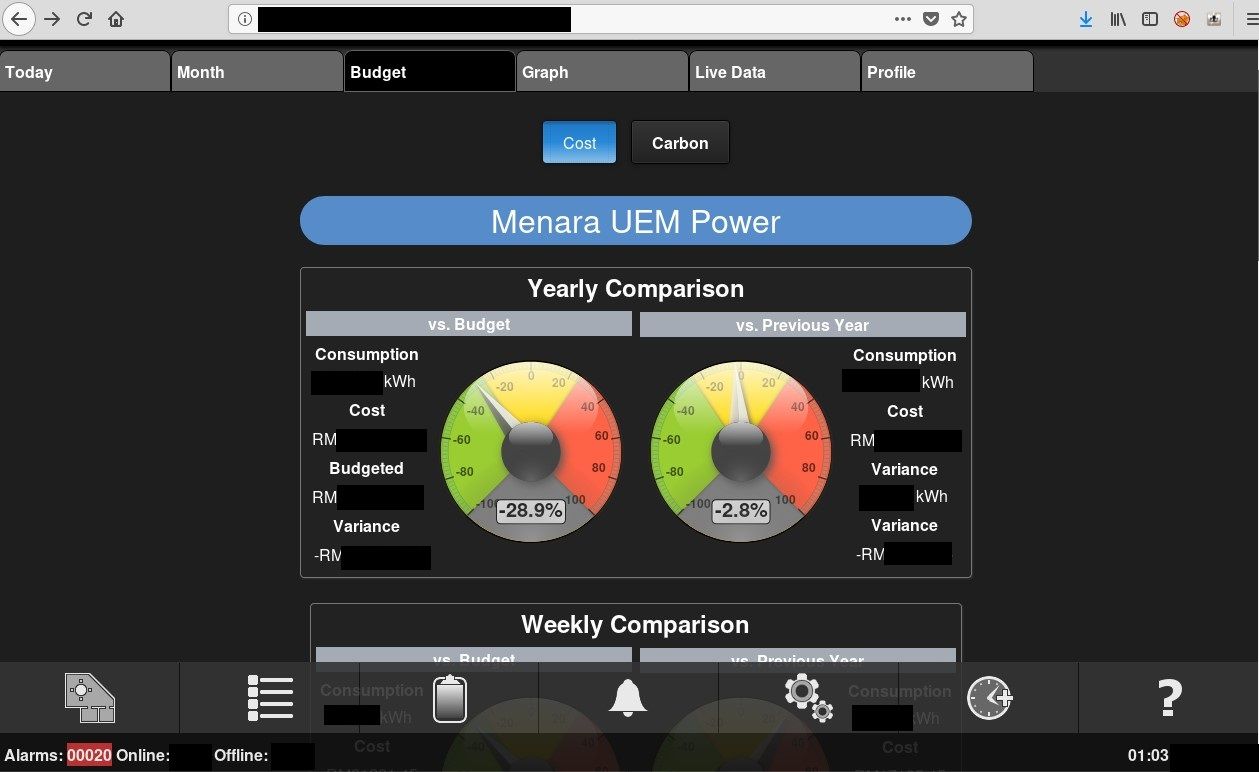
Application also reveals details of each device and plan of each floor. It is super helpful in case of physical intrusion.
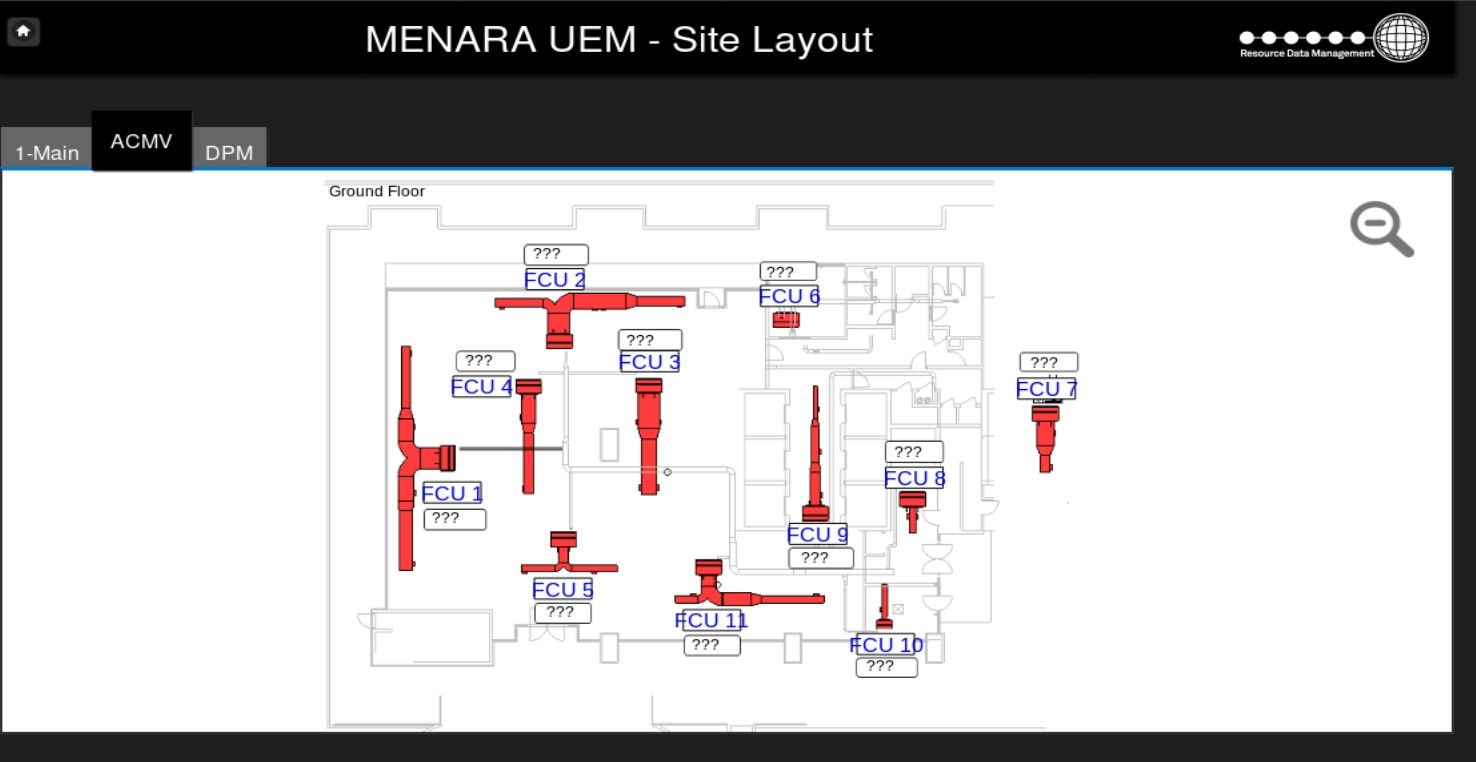
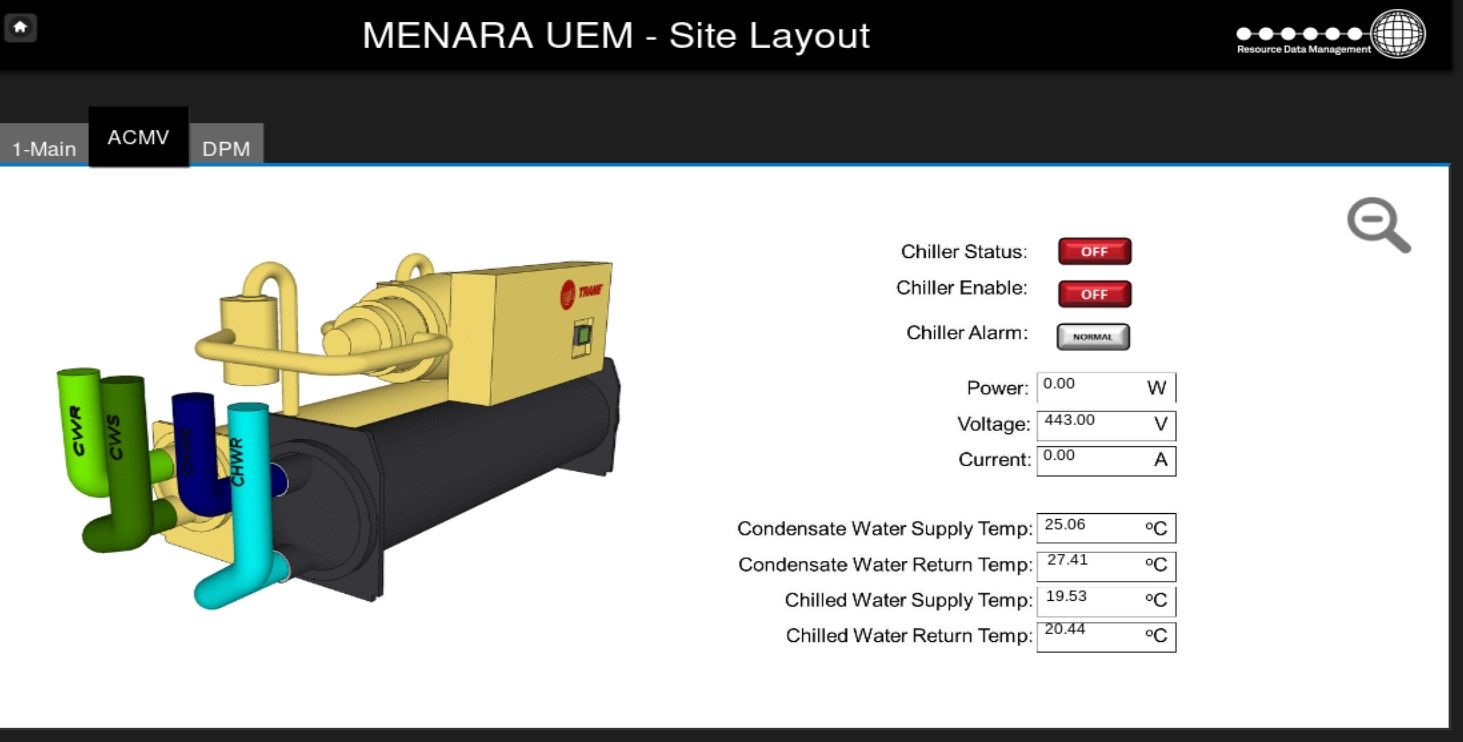
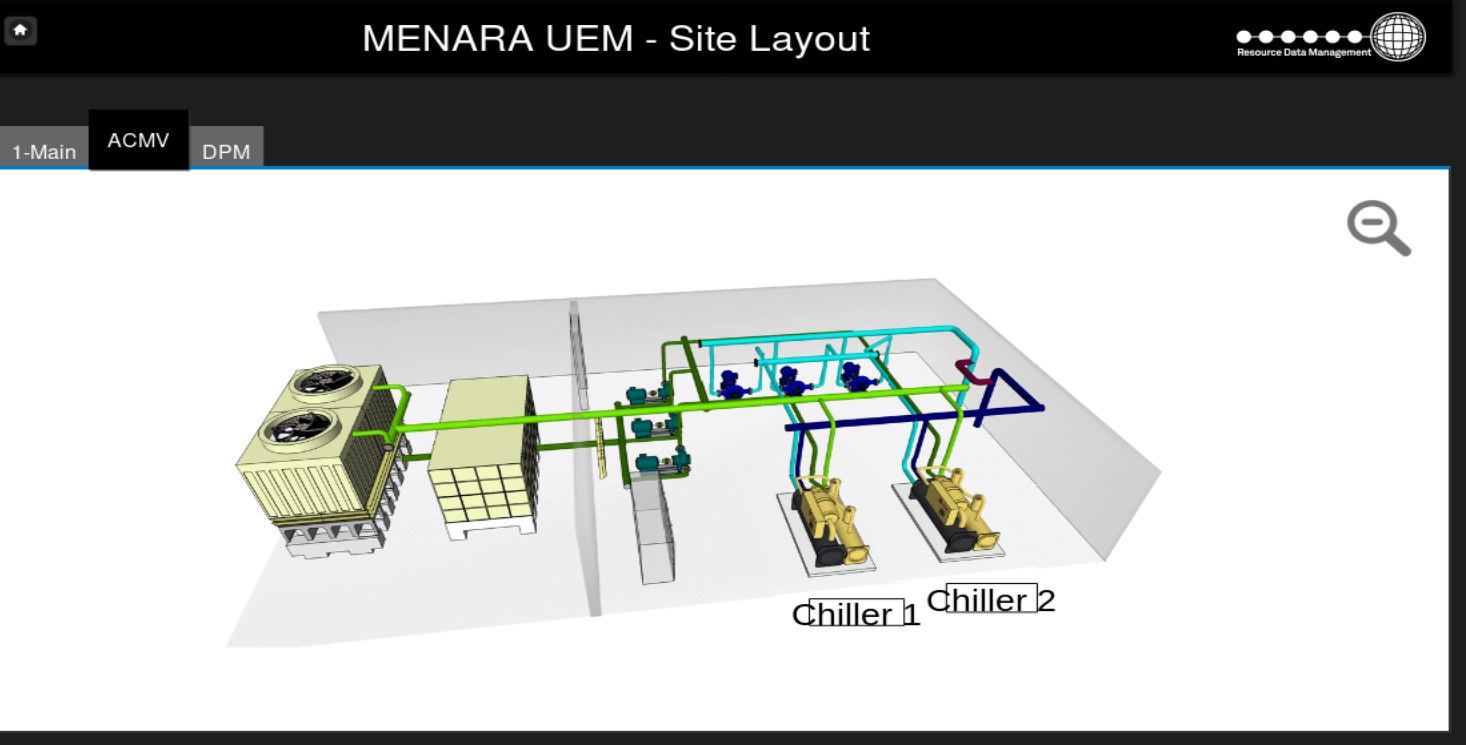
Building belongs to UEM group and is located in Kuala Lumpur, Malaysia.
The first screenshot presents that building has 17 floors. We can get a photo and compare it with real view.

This is the same building that was shown before, it is also 17 floor height and belongs to UEM.
National Laboratory for Energy Conversion Technology
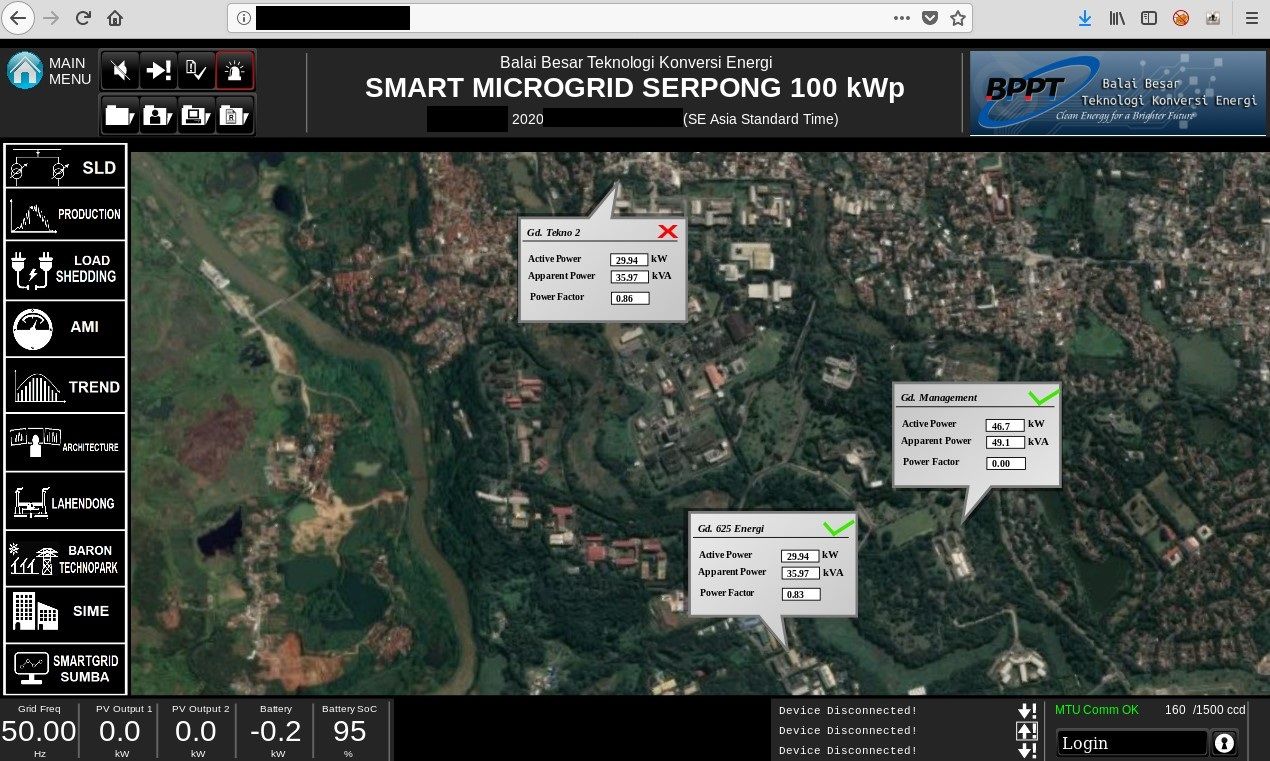
B2TKE-BPPT (Balai Besar Teknologi Konversi Energi) strives to play an important role in promoting the growth of energy industry and the implementation of efficient, reliable and clean energy technology to provide solutions for national energy issues
B2TKE - BPPT
b2tke adalah
BPPT

One of the server that belongs to B2TKE, exposes panel management for Smart Microgrid that supports large region - 15 buildings, charging stations and more. Default view shows map and details about energy consumption or active power. There are plenty of different saved views that are helpful to gather intelligence about the company and physical devices - their location and use. Moreover, it discloses live production details about energy usage as well as details about many devices associated with the infrastructure.
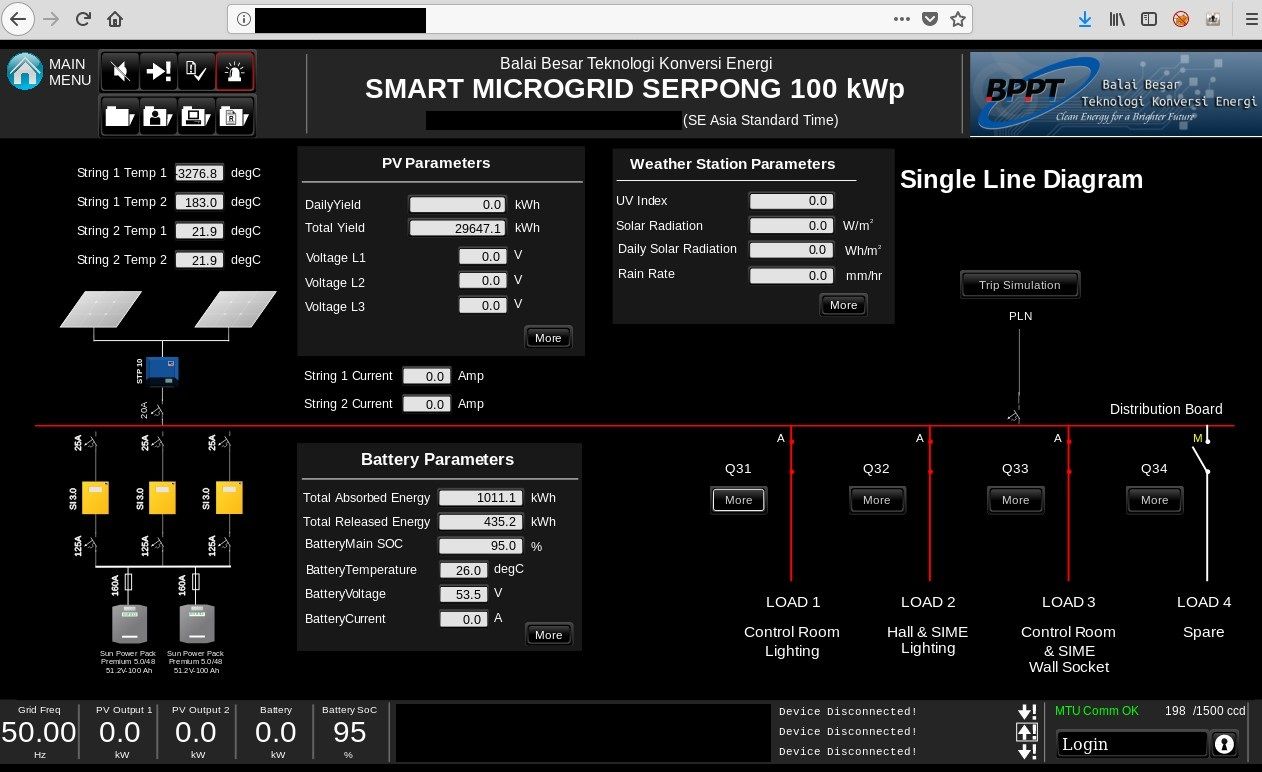
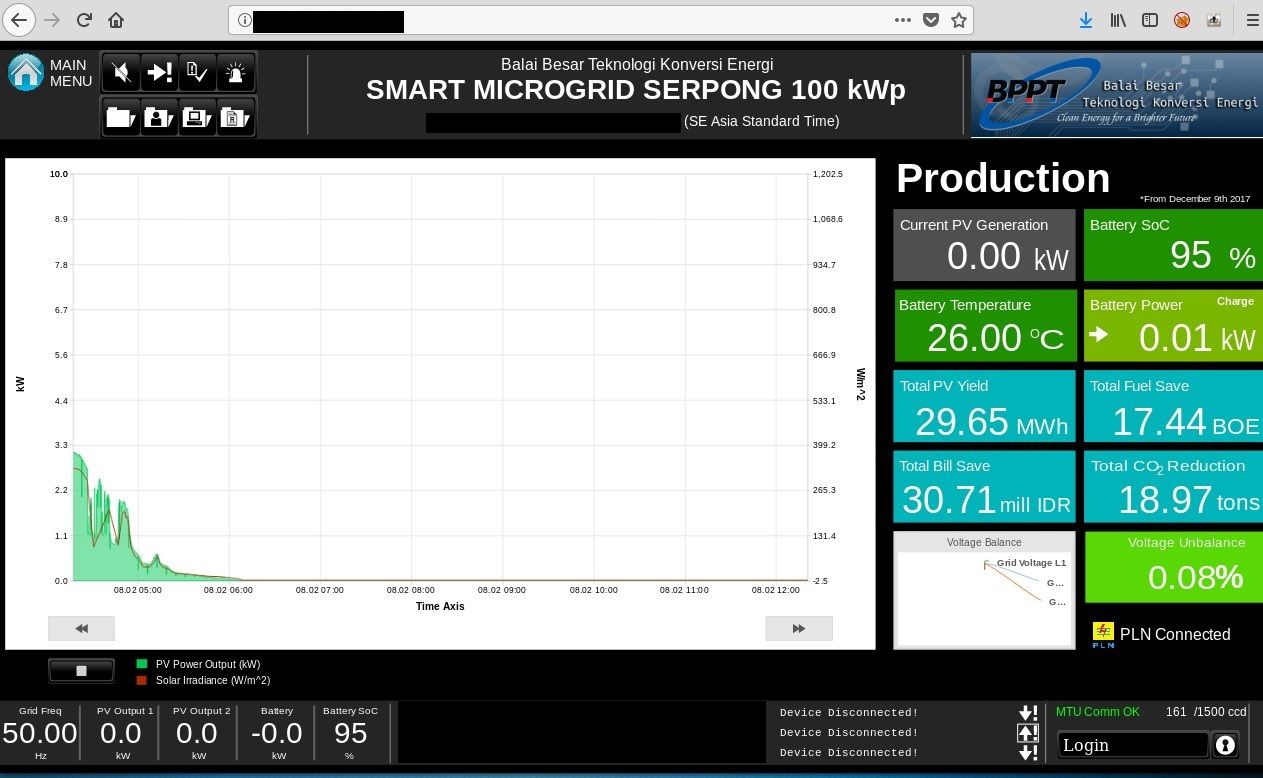
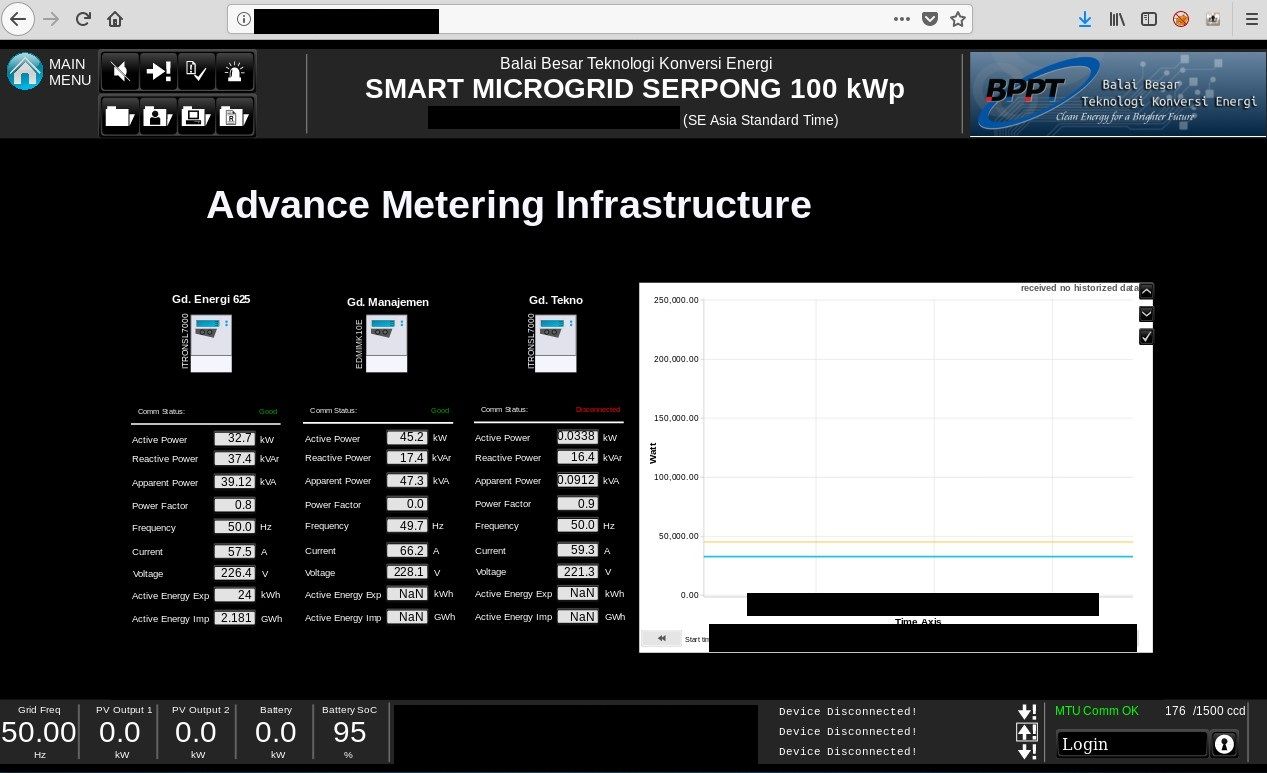
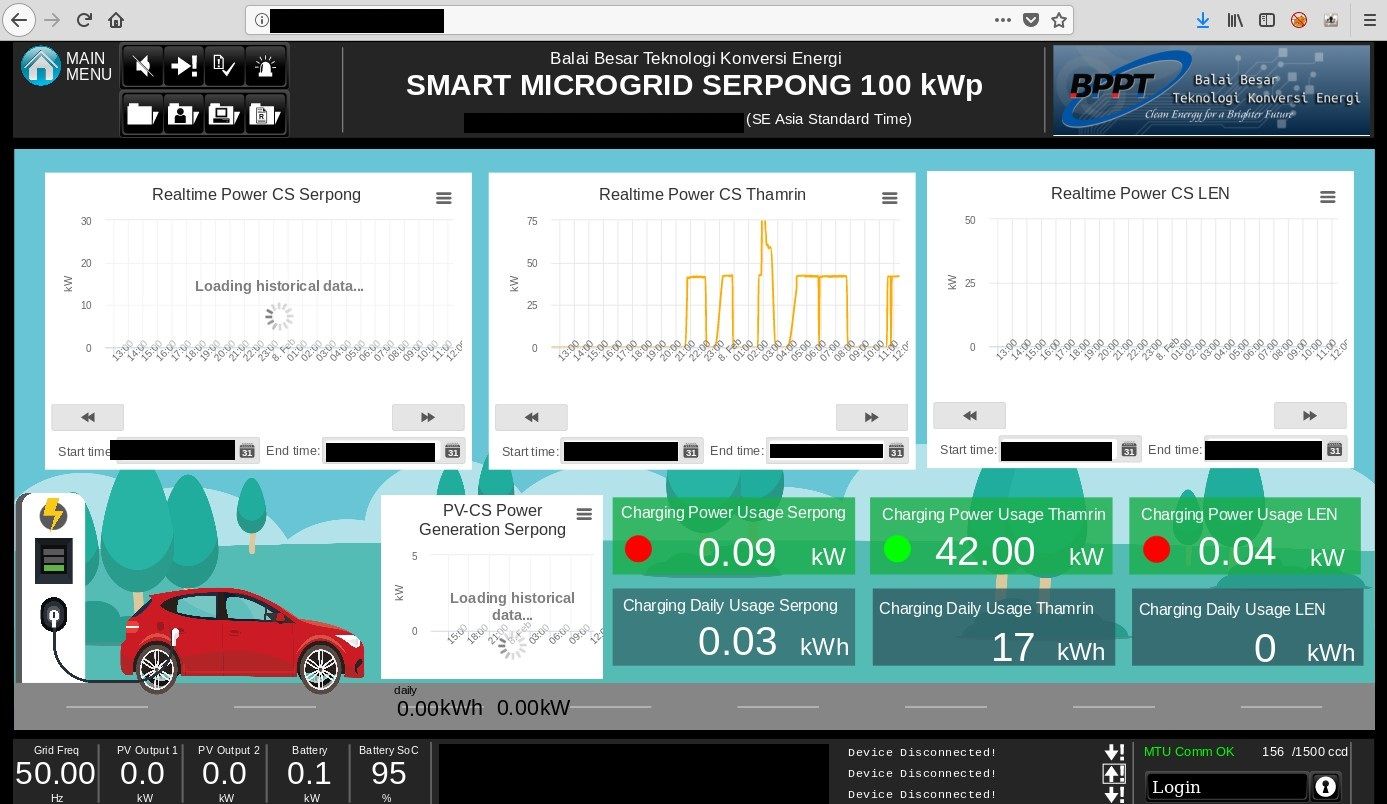
If it's not enough, it exposes internal network infrastructure, which is like a holy grail in the world of reconnaissance.
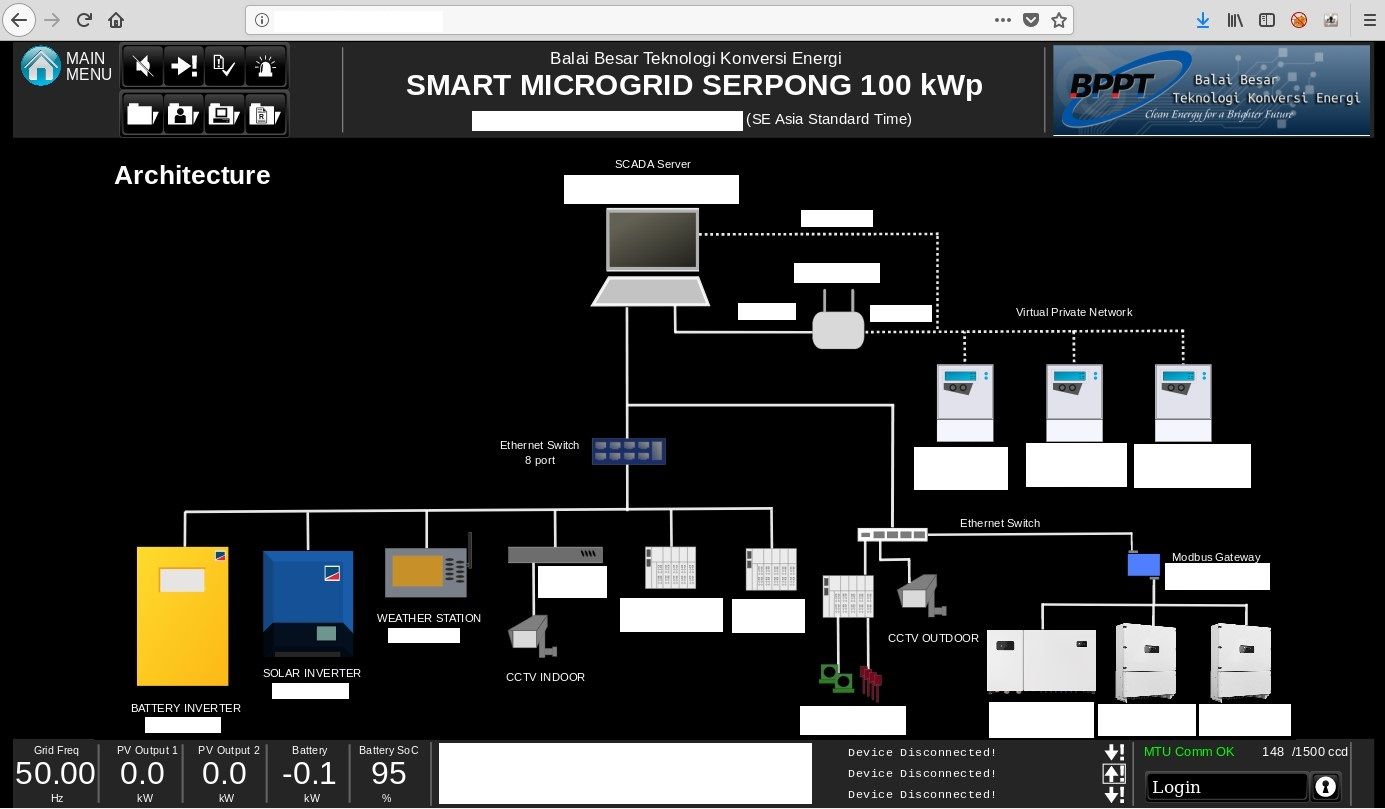
It contains diagram, types of devices and internal IP addresses. Having this information, one can freely move around the network of BPTT. There are couple devices that are clearly used in solar technology but diagram reveals also addresses of Virtual Private Networks or CCTV cameras.
I started digging deeper and translated map from exposed panel
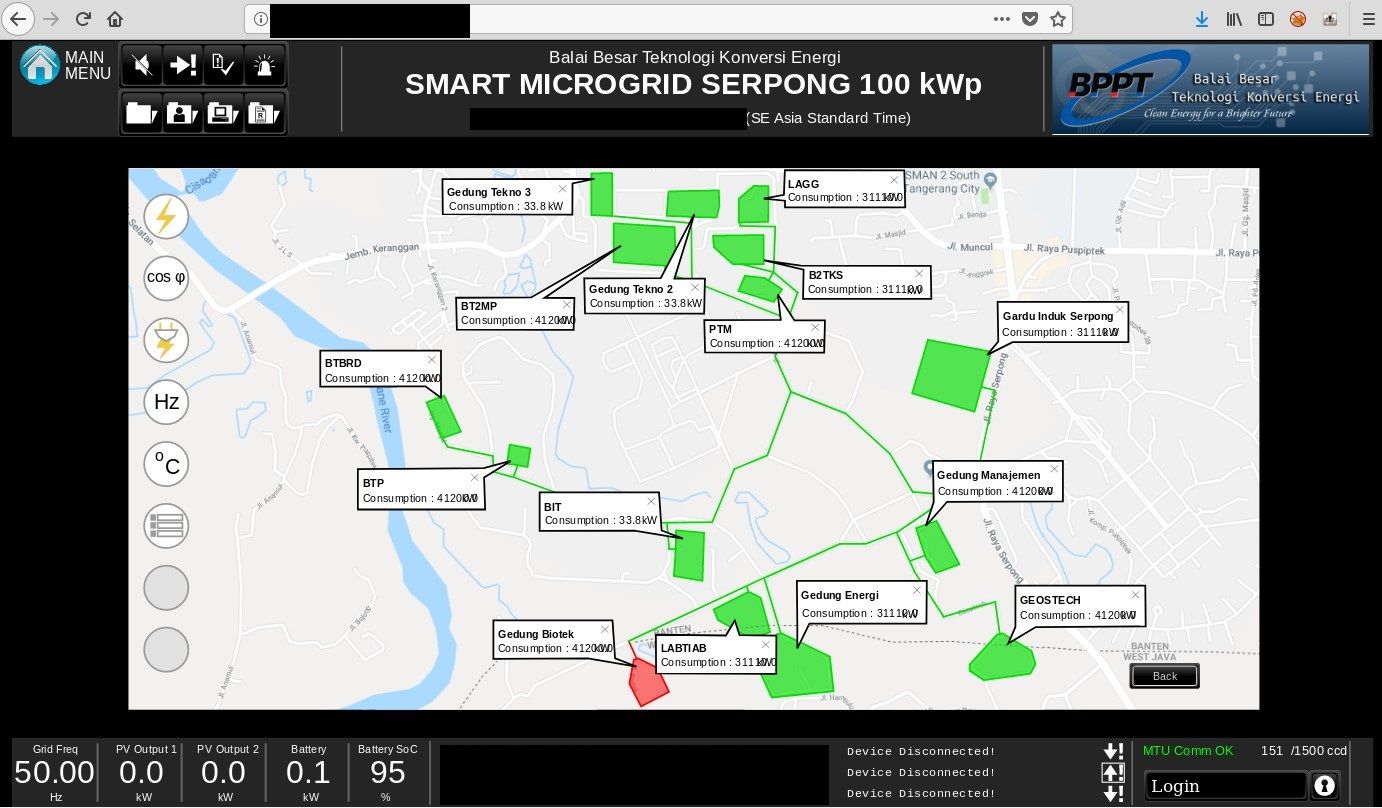
into google maps
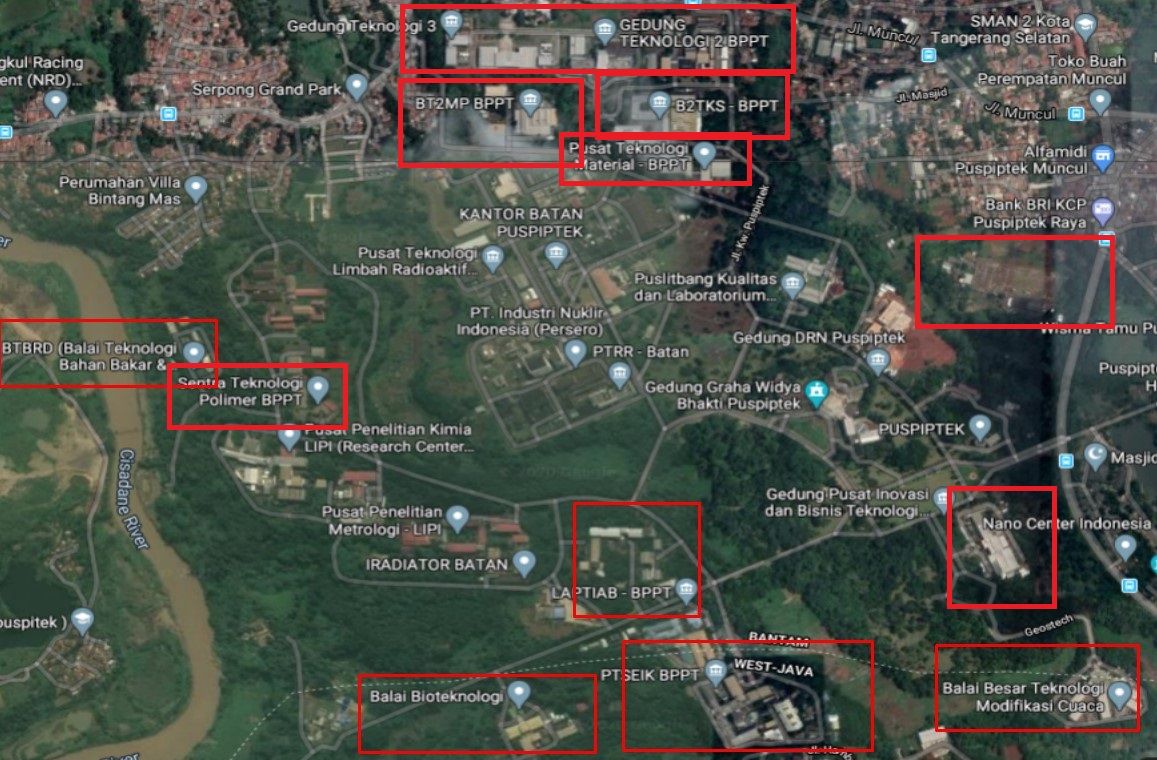
The buildings that are part of the infrastructure and exposed in the microgrid are related to
- Biotechnology
- Research institutes
- Government offices
- Charging stations
- Electrical substation
In my opinion, the most fragile facility is electrical substation located at the right hand side of the google maps screenshot.



Going to the field
A lot of factors must be meet to achieve total cyber and physical security. To test the first one we don't have to go out, everything can be done in front of the computer like scanning, reconnaissance or phishing attempts. Red teams use different tactics to examine physical security of buildings, I've never heard about any possible physical red teaming for critical infrastructure, however my point is that you must go out to check the actual building.
For this purpose, I've created Kamerka Mobile that works on Android and uses Pastebin as a data storage. You can send coordinates and additional details from web version of Kamerka and access it on your mobile.
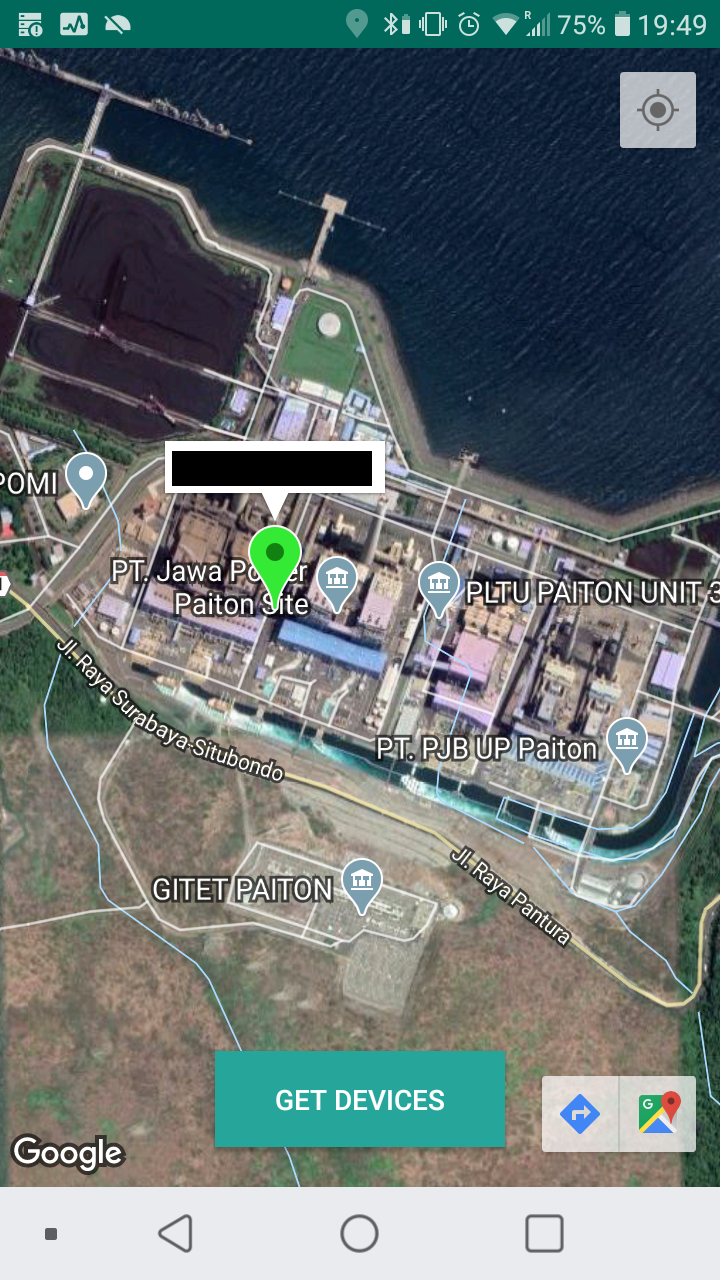
If you like the idea of mobile application, you can read more about it below
Hack like it’s 2077 — Presenting ꓘamerka mobile
From now on ꓘamerka has a mobile version. You can geolocate specific buildings or facilities in web interface and all the results will be available on your phone. It allows you to go to particular place and examine it’s physical security. Cameras, building operation systems, parking spots, UPS units…
WojciechOffensive OSINT

By providing tutorials and sharing knowledge I hope to partially cover my medical bills. If you like my work and use my tools, please donate.

I presented only 5 findings from Singapore, Thailand, Vietnam, Malaysia and Indonesia as an example that any kind of infrastructure can face the Internet and reveals many information that attacker looks for. Any disclosed detail brings attacker closer to compromise the system or abuse obtained information. So what organizations can do to protect themselves?
Conclusion
I strongly believe that this kind of offensive approach should be used by each country and authorized cyber entity to inform owners about potential dangerous exposed device in their own cyber space as well as providing offensive capabilities on enemy territory. Kamerka gives you the possibility to obtain intelligence in fast way about Industrial Control System and going deeper with your own manual research to support whole chain of cyber attack.
The critical infrastructure related research is the best what security/military analyst can do. It includes almost any OSINT field that you can imagine - technical investigation, human intelligence, GEOINT and lot more depends of your creativity and intelligence collecting skills.
Please subscribe for early access, new awesome things and more.
如有侵权请联系:admin#unsafe.sh