Producing and consuming actionable Cyber Threat Intelligence is a large part of a security analyst’s daily work, but threat intelligence comes in many forms. As most experienced analysts’ know, some forms of threat intel are more useful than others, but that usefulness tends to be inversely proportional to availability. File hashes and IP addresses for the latest campaigns are usually the first to be shared among security researchers, but they are also rapidly changed by attackers, limiting their utility. This relationship between availability and usefulness was nicely illustrated by David J Bianco’s Pyramid of Pain. The general points of the Pyramid still hold true, but security solutions have not stood still in the intervening years, and with the right technology to hand, producing and consuming high-value indicators like TTPs can be a whole lot easier than it once was. Let’s see how.

Revisiting the Pyramid of Pain
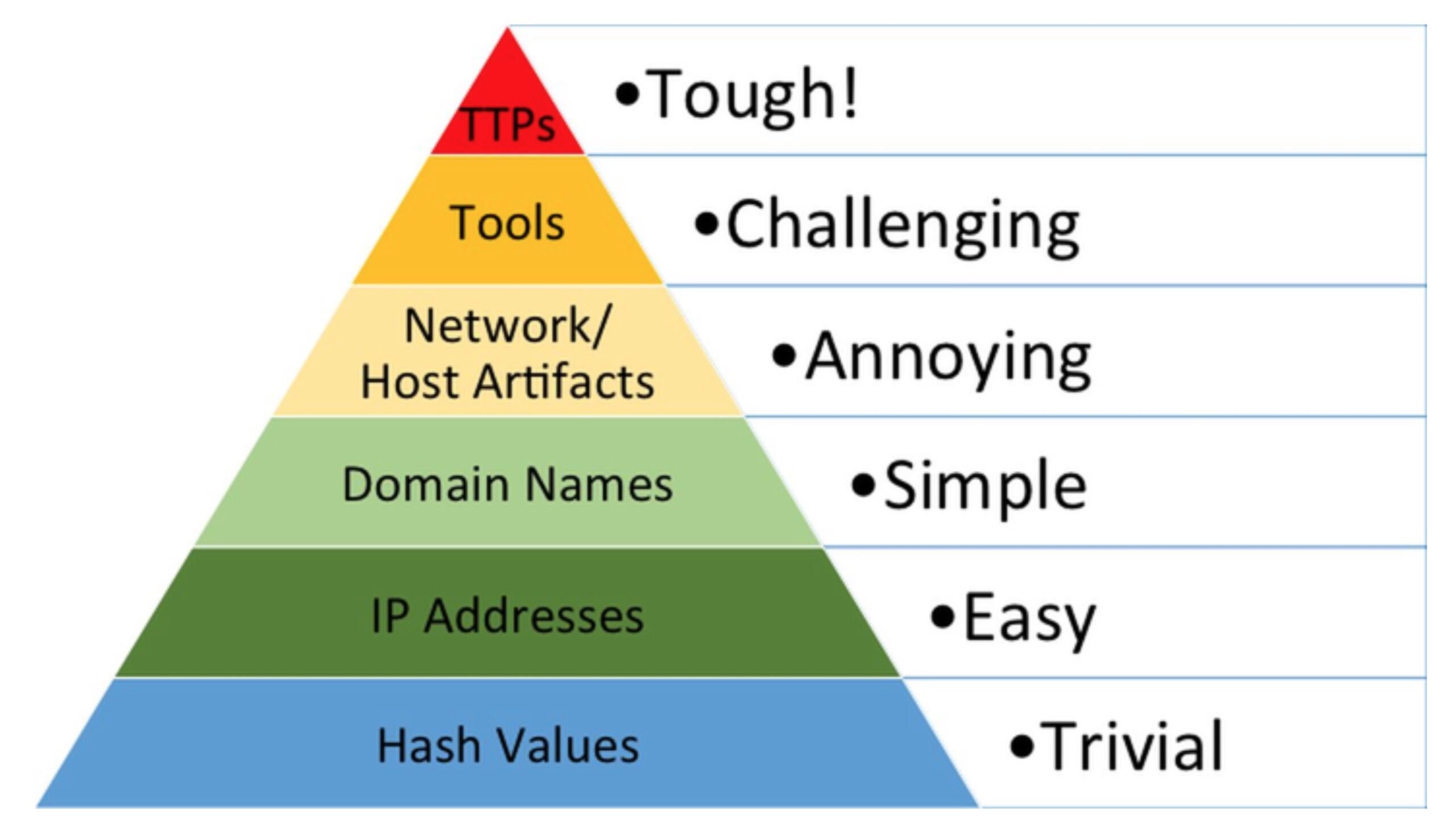
Let’s recall how Bianco’s Pyramid of Pain works. The ‘pain’ here is supposed to be the pain felt by attackers once a particular kind of indicator for their attack becomes known. However, as we’ll see, the pyramid also describes parallel difficulties for defenders in terms of availability of each class of indicator.
At the base, or widest part, of the pyramid, we have file hashes – the kind of IoCs that we are all used to dealing with on a daily basis. These are easy to acquire and widely shared, so availability of these is typically good. The problem, though, is that it is also relatively painless for attackers to change a file’s hash; indeed, much modern malware even does this “autonomously” – so-called polymorphic malware – and it’s comparatively easy to write malicious software that creates copies of itself with a different file hash each time. Thus, as the pyramid graphic suggests, discovery of particular malicious file hashes causes the attacker virtually no pain at all in terms of adapting to and evading solutions that rely on detecting file hashes.
Much the same can be said of IP addresses and even domain names, which nowadays can be changed even more easily and rapidly than back in 2013 when Bianco first developed the Pyramid of Pain concept.
Network and Host artifacts – distinguishing characteristics of network traffic or host activity – increase the pain for attackers somewhat once these become known. Defenders can use technologies such as Suricata rules and Snort to identify known malicious network traffic, and tools like Yara rules and ProcFilter can similarly match malicious patterns in files and processes executing on a device.
For attackers, getting around these kinds of “signatures” involves some work (aka ‘pain’). First, they have to determine what pattern matching rule or rules are being used; since different security solutions may employ different or multiple rules, that in itself can be a difficult process. Second, once the attackers have determined how they’re being detected, they need to refactor their code in order to avoid the patterns used in the signatures.
Despite that, the pain isn’t that great if you’re a full-time threat actor outfit – it’s just part of the job. A good example of malware that continuously iterates in this way is the script-based Shlayer and ZShlayer malware that targets macOS. Part of the attraction of using scripts, from the malware authors’ point of view, is it’s much easier and much faster to iterate with shell scripts than compiled binaries. Scripting allows far more flexibility in achieving malware objectives than a lot of compiled programming languages, and many binary scanning engines don’t know how to handle scripts anyway, which can also be executed in memory with relative ease.
Things get tougher for threat actors when defenders have a good handle on what particular tools are being used to attack them – these can range from custom-made frameworks to publicly available and open-source toolkits. Switching out one tool – or more likely, set of tools – for another increases the burden on cyber threat actors because it is not always easy to find or introduce tools into a victim’s environment that have the desired capabilities.
For example, if the threat actor is making heavy use of LOLBins like PowerShell and CertUtil, or relying on publicly-available tools like Cobalt Strike or Mimikatz, it may be very a tough challenge to obtain the same functionality with different tools.
Finally, TTPs, which we’ll discuss in more detail in the next section, cause the greatest pain for threat actors because they hone in on the attacker’s actual objectives and seek to block behaviour that attempts to execute those objectives.
Intelligent Tools That Produce Actionable Intelligence
From the above discussion, it should be clear that, from a defender’s point of view, developing awareness of attackers’ tools and TTPs (Tactics, Techniques, and Procedures) – those which cause the threat actor the most pain – is where we should focus our efforts for the most gain. The problem is that Bianco’s Pyramid of Pain also paints a picture of just how easy-to-come by each of those threat intelligence indicators typically are for most enterprises: easy at the bottom, tough at the top.
File hashes are widely available in most threat intel reports but are time-consuming to digest and have a short shelf life. At the other end of the scale, TTPs return the most value, but they are not so widely known or distributed.
However, initiatives like MITRE ATT&CK have added a new dimension to cyber threat intelligence, and security tools with features like SentinelOne’s Rapid Threat Hunting put new-found power into the analyst’s hands.
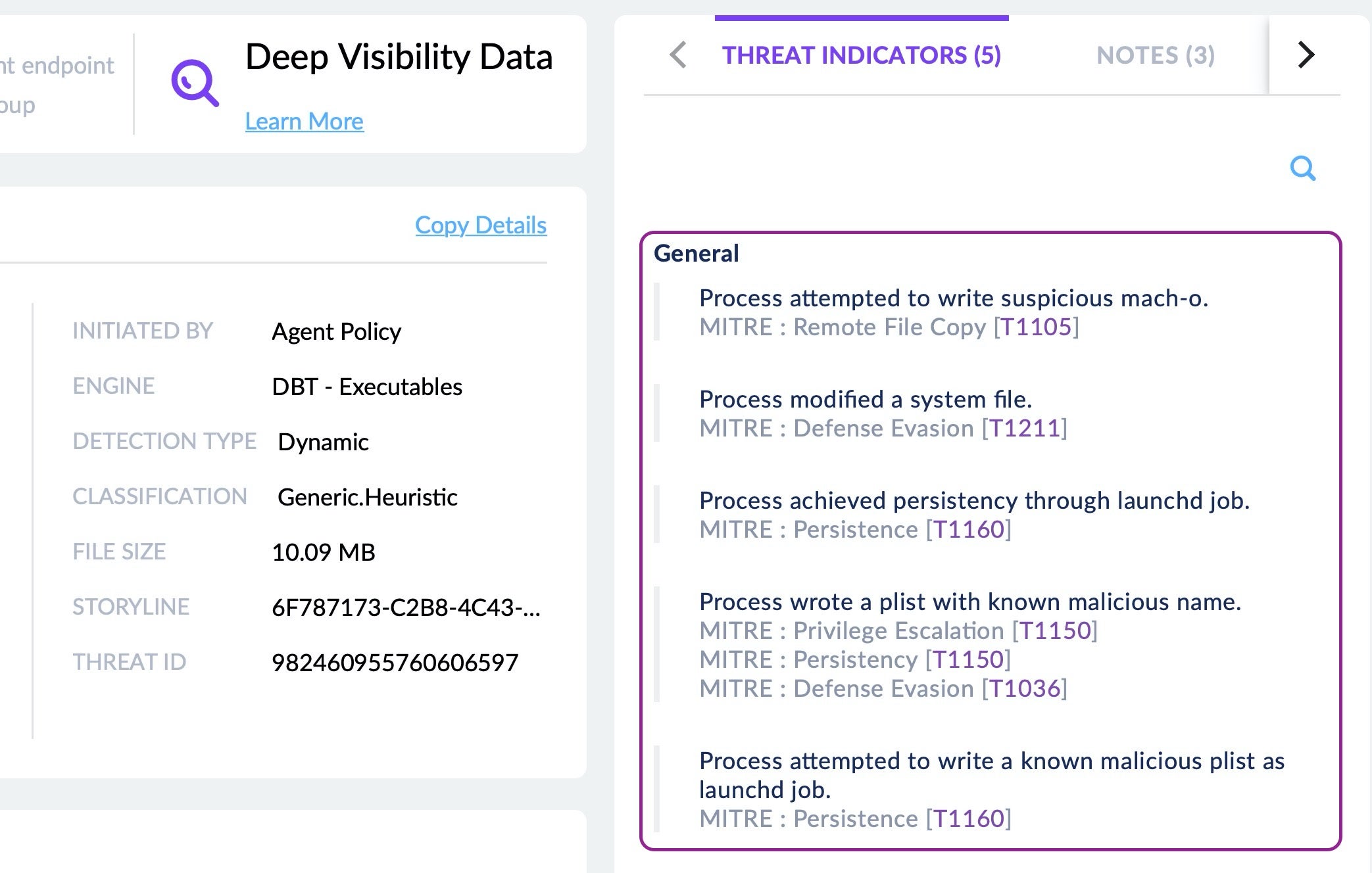
In the image above, we can see how the SentinelOne Threat Center displays all the behavioral indicators associated with a particular detection, with links to MITRE ATT&CK TTPs, for the analyst’s convenience.
Similarly, suppose you have seen a new threat intelligence report indicating a particular TTP. You could immediately search your entire fleet for any process or event with behavioral characteristics that match that TTP simply by entering the MITRE ID in the SentinelOne console’s Deep Visibility query box.
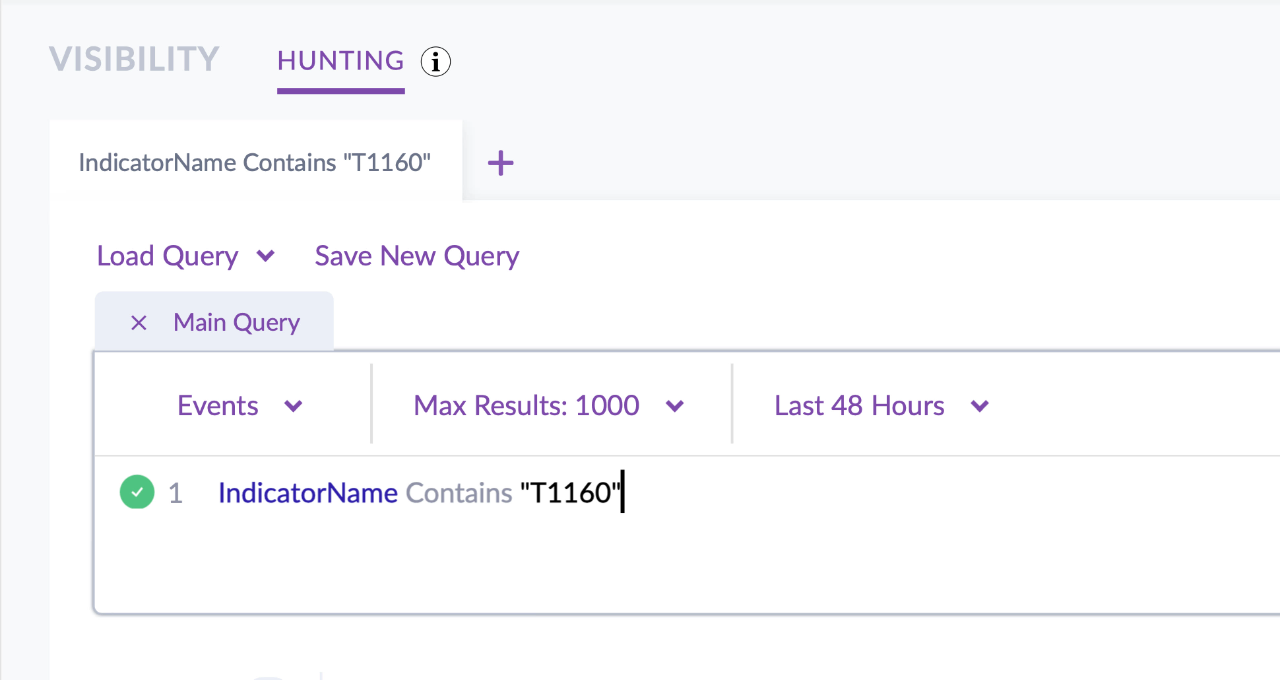
Focusing on TTPs in particular gives you a great advantage when defining rulesets or watchlists for added protection. For example, you can automate hunts using particular behavioral indicators that belong to known attacks seen in your own environment or in the environment of others. Since Bianco published the influential Pyramid of Pain concept, many threat intelligence researchers, including SentinelOne’s own SentinelLabs, include MITRE ATT&CK TTPs at the end of their reports along with other IoCs. With the right tools to hand, you can easily consume this kind of threat intel directly into your solution for both automated detection and rapid threat hunting.
Rapid Threat Hunting with Storylines
Time always seems to be on the attacker's side, but security analysts can get ahead by hunting threats faster than ever before.
Conclusion
Utilizing detailed, actionable and effective intelligence is key to thwarting cyber attacks. File hashes, IP addresses and domain names have increasingly limited use as both attackers and malware have evolved to produce campaigns in which these traditional IoCs are rapidly disposed. However, by focusing on indicators that are difficult for attackers to change with technology that can both consume and produce these much sought after indicators, we can increase the cost of business for attackers while improving our ability to detect and defeat the cyber menace.
If you would like to learn more about how SentinelOne’s Singularity platform can help improve your threat intelligence and protect your business, contact us today or request a free demo.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
- How Ransomware Attacks Are Threatening Our Critical Infrastructure
- The C-suite Guide to Cyber Safety | 7 Steps to Securing Your Organization
- What Is Cloud Security (and How Do You Secure the Cloud Today)?
- Feature Spotlight: Automated Application Control for Cloud Workloads
- Top Ways to Shorten Cybersecurity Remediation Cycles
- Coming Out of Your Shell: From Shlayer to ZShlayer
- Feature Spotlight: Introducing Cloud Funnel, the EDR Data Lake
- The BLINDINGCAN RAT and Malicious North Korean Activity
- Defeating “Doki” Malware and Container Escapes with Advanced Linux Behavioral Detection