Digital transformation initiatives have pushed an ever-increasing number of organizations to migrate to the cloud. Realizing the advantages of moving data and services to the cloud, the overwhelming majority of organizations have embraced a multi-cloud strategy, choosing between the available cloud delivery models of Software-as-a-Service (SaaS), Platform-as-a-Service (PaaS) and Infrastructure-as-a-Service (IaaS).
While SaaS models such as Office 365 are the most widely used and understood, IaaS and PaaS models have also seen rapid adoption in the enterprise. The objective of this article is to understand the benefits and the differences between IaaS and PaaS to form a useful guide for all businesses, especially small-medium enterprises starting their journey towards digital transformation and to the cloud.

What is IaaS?
Infrastructure as a Service (IaaS) platforms are scalable and automated computing resources providing self-service capabilities for accessing and monitoring computers, networking, storage, and other services. The platforms allow businesses to purchase resources on-demand and as-needed rather than having to shop for on-premises hardware.
IaaS delivers cloud computing infrastructure through virtualization technology. Access to these cloud services is achieved through a dashboard or an API, giving IaaS customers complete control over the whole infrastructure. In effect, IaaS provides identical technologies and capabilities as a conventional on-premises data center without having to physically manage it.
IaaS Pros and Cons
IaaS platforms benefit organizations in multiple ways. They help businesses scale their infrastructure up or down, in response to changing demand. Organizations purchase IaaS resources as needed, for as long as they need them, without lengthy procurement and deployment cycles. Additionally, hosting the hardware and the required services in the cloud reduces the labor required for hosting and maintaining those on-premises.
In comparison to the other delivery models, IaaS platforms offer the greatest level of control over software and hardware. IaaS is effective for workloads that are temporary. For example, it might be more cost-effective to host and test an application under development in an IaaS platform rather than overloading on-premises environments. Once the application is tested and validated, the business may progress to either an on-premises deployment or to a long-term IaaS deployment.
Despite its flexible, pay-as-you-go model, IaaS customers may find costs to be higher than expected. Businesses should actively monitor their IaaS environments to understand how they are being used, and to avoid being charged for idle, orphaned, or otherwise unused services.
Closely related with the continuous monitoring of IaaS services is the lack of policy-based governance of configuration settings. The velocity and scale of change which the cloud enables presents a challenge to many organizations, as they wrestle with the lack of automation in bringing rogue configurations back into compliance.
Finally, visibility is often a concern for IT security teams, as developers strive to innovate ever faster, deploying more VMs, storage, and so on. Impaired visibility of IaaS resources increases risk; stated simply, security teams cannot secure or provide governance oversight of resources they do not know exist. IaaS security is a major concern for businesses of all sizes, which we will discuss further below.
What is PaaS?
Platform as a service (PaaS) provides developers with a complete environment for the development and deployment of apps in the cloud. With PaaS, developers can create anything from simple apps to complex cloud-based business software. Like SaaS, PaaS environments allow businesses to access up-to-date, powerful tools that they may not be able to afford.
In contrast to SaaS platforms, PaaS is not delivering software. Instead, it is an online platform accessible to developers to create software. PaaS environments give developers the ability to concentrate on developing software and apps without worrying about operating systems, software updates, storage, or infrastructure.
PaaS Pros and Cons
No matter the size of the company, PaaS platforms present numerous advantages. These scalable platforms allow for simple, cost-effective development and deployment of cloud-native apps. Developers can customize apps without the pain of maintaining the software, while a reduced amount of coding is required. Further, PaaS enables the automation of business policies and can streamline workflows when multiple developers are working on the same project. Finally, PaaS can reduce costs associated with app development and deployment, while also simplifying the challenges of agile and speedy DevOps cycles.
Despite the obvious benefits, vendor lock-in is an area of concern. Selection of a PaaS provider should be based on their relative strengths, languages and the frameworks they support for application development. Since migrating services and data from one platform to another is an arduous process, no one wants to find himself in a position where a PaaS platform fails to support the organization’s technology stack. As a result, selecting a PaaS provider should involve the evaluation of business risks due to service downtime and vendor lock-in.
Security in IaaS and PaaS platforms
With traditional on-premises data centers, the security of data and infrastructure was the sole responsibility of internal security teams. Clearly defined perimeters made the application of security controls a relatively straightforward process. Migrating to the cloud, those boundaries are blurred, and security teams must deal with infrastructure and services beyond traditional perimeter security, which complicates the establishment of a robust security strategy.
In the cloud, the cloud service provider (CSP) assumes some responsibility, especially to secure the underlying infrastructure, but it is the customer’s absolute responsibility to secure their own data and applications. Failure to do so will leave companies vulnerable to data breaches. In short, the CSP is responsible for security of the cloud, but the customer is responsible for securing their data in the cloud.
Security is the biggest concern of organizations using public cloud. Enforcing a robust security posture in the cloud is a challenge aggravated by many factors such as:
- Complexity of cloud-based deployments
- Impaired visibility across services, applications, and data in the cloud
- Lack of automated, real-time configuration security posture assessments against recommended best practices, such as those published by the Center for Internet Security (CIS Benchmarks).
Manual methods of discovery, assessment, and remediation are doomed to failure because the speed and scale of agility which the cloud provides far outstrips the capacity of mere mortals to keep pace.
The key to a successful cloud security strategy is understanding the Shared Responsibility Model.
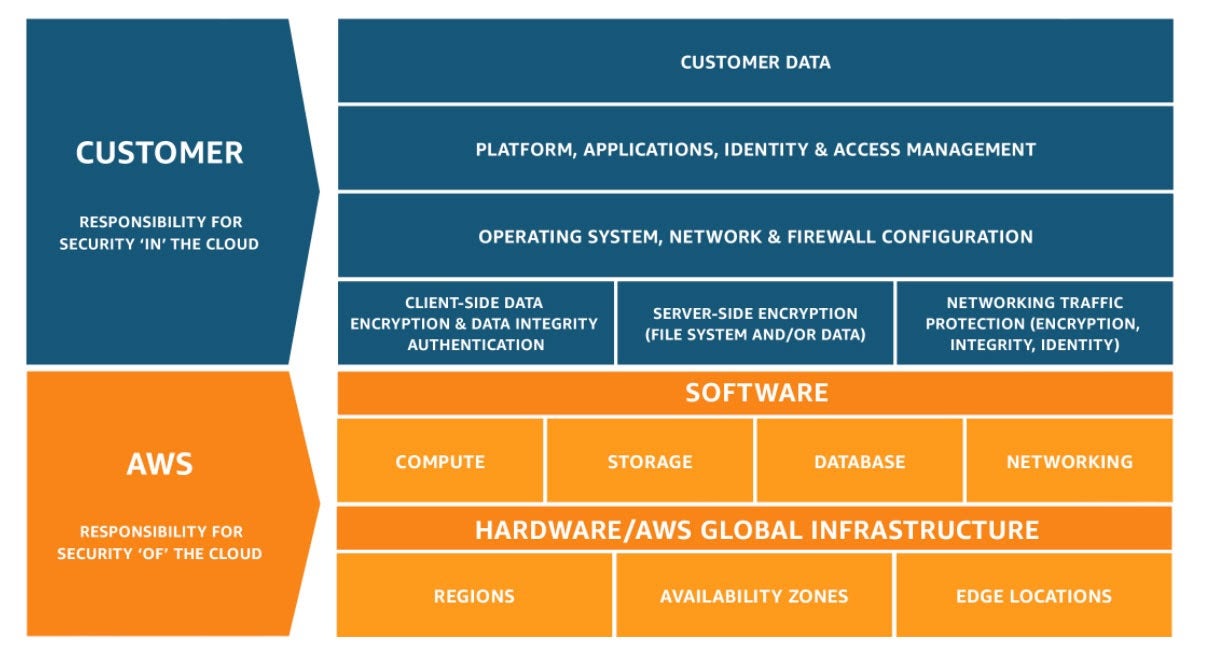
In IaaS platforms, the CSP is responsible for securing the data centers and other hardware that support the infrastructure, including networks, storage disks, and VMs. IaaS customers must secure their own data, operating systems, and software stacks that run their applications. The PaaS model places more responsibility in the hands of the platform vendors, but it is the customer’s responsibility to secure their applications and associated data.
Automated Application Control for Cloud Workloads
Protect cloud-native workloads with advanced lockdown capabilities that guarantee the immutable state of containerized workloads.
How SentinelOne Can Help
A robust and effective cloud security strategy requires a different approach. Security teams must protect both the on-prem infrastructure and those in the cloud. While these servers physically reside beyond the corporate boundaries, it is solely the customer’s responsibility to ensure cloud host security by constantly monitoring all processes to autonomously identify malicious events and thwart them before they spread their evil.
A prime example of malware in the public cloud is cryptojacking malware. If malicious actors can gain access to your VMs or containers and elevate privileges, they can inject cryptomining malware – and you get to pay for that compute load. To mitigate threats like this, consider investing in runtime EPP and EDR solutions which cover both VMs and containers.
While cloud providers do take their own security responsibilities seriously, the core of cloud security is for businesses to secure their own data and applications. To ensure the security of your cloud workloads, deploy a capable workload protection solution. For more information about how SentinelOne Cloud Workload Security can work for you, contact us or request a free demo.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
- Hiding in Plain Sight | The IoT Security Headache and How to Fix It
- Healthcare and Cybersecurity in the Times of Covid-19
- How to Catch a Spy | Detecting FinFisher Spyware on macOS
- APTs and Defending the Enterprise in an Age of Cyber Uncertainty
- Unifying Endpoint Security for Enterprise | An Interview With Migo Kedem
- Revisiting the Pyramid of Pain | Leveraging EDR Data to Improve Cyber Threat Intelligence
- How Ransomware Attacks Are Threatening Our Critical Infrastructure
- The C-suite Guide to Cyber Safety | 7 Steps to Securing Your Organization
- What Is Cloud Security (and How Do You Secure the Cloud Today)?