
The clearer you see, the better you win!

So, I was trying Google this time to see if I get something interseting in it. I spent like 20 days on an acquisition and finally I found some interesting stuffs over there. This is the tell about one of them:)
While I was testing almost everything, I saw a URI in burp which was providing some user data including thier user IDs and usernames. It was looking something like this:- redected.com/c/ask/20/l/latest.json. It got my attention so I started searching for some info where I could try other users’ user IDs or username as well.
Finally I found an endpoint where it was showing the data of my account. The Endpoint looked like this:- redected.com/u/yourusername.json. Well this was the endpoint which I was trying to find since a while and that’s all we need as a hacker! I changed the usernames to the ones which I found from another endpoint and BOOM! I was able to see the PII of other users as well. I have put some POCs of them below:-
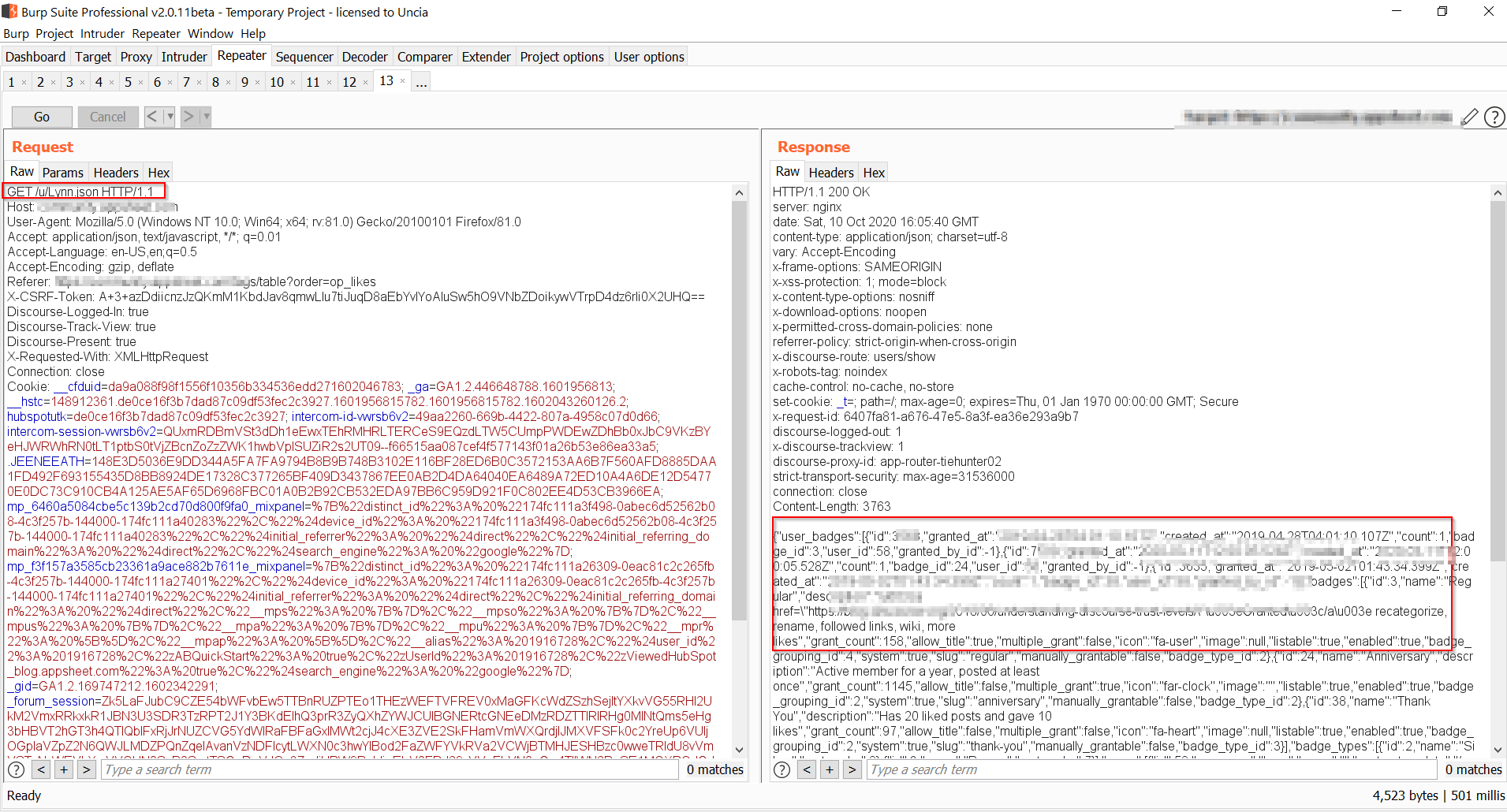
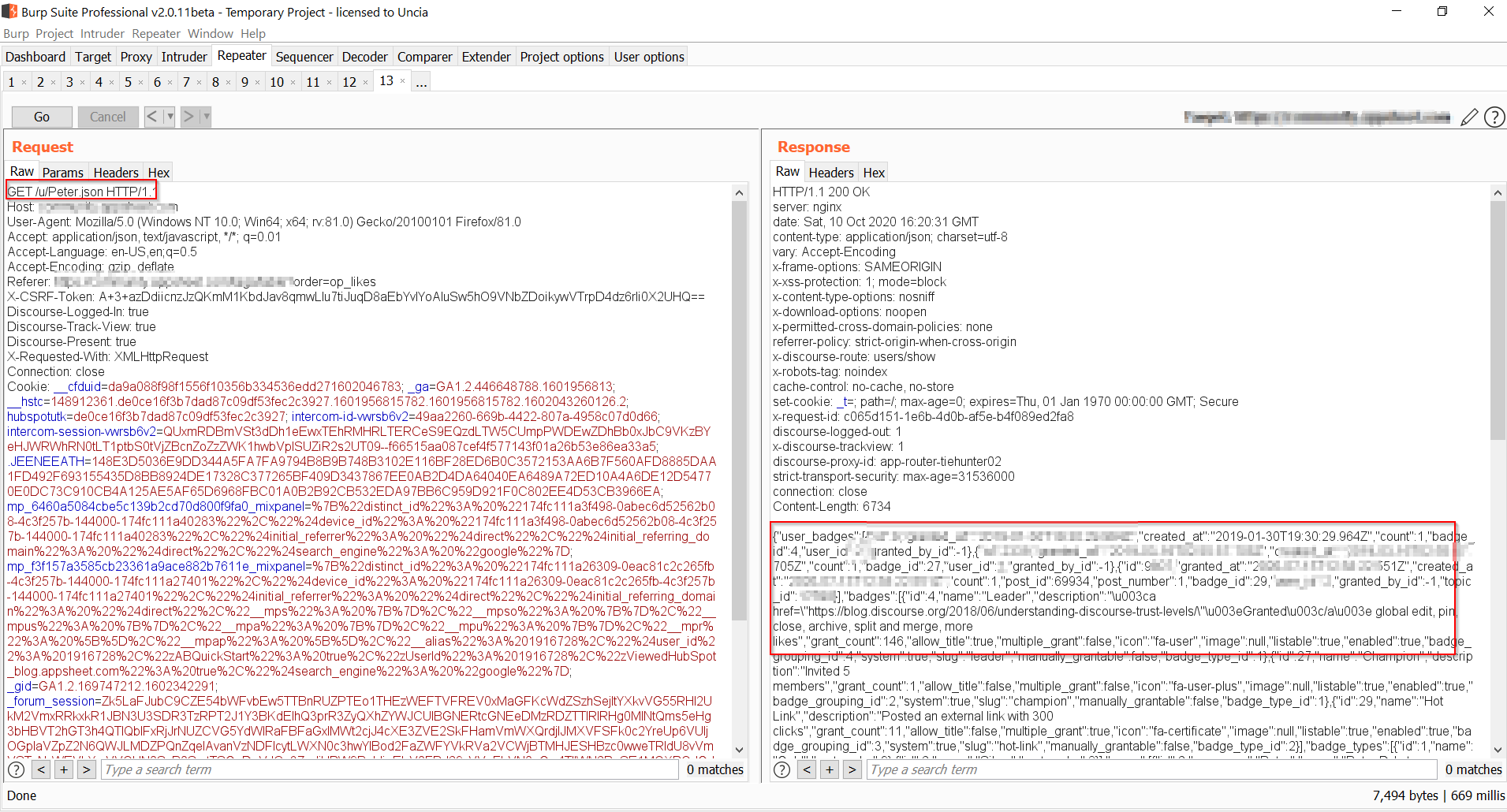
That was an easy find once you get that endpoint. I took the time and it paid off. I would like to mention “no target is safe”. What you need to create is this mindset. Once you have it, go ahead and hack’em all! Also, it really matters how much time you are putting into your efforts. Big targets, actually huge targets need time to get exploited. Stick with it and you will find something eventually:)
I hope this helps people out there to observe targets better. With this, I will wrap up this write-up here. If you like this, follow me on twitter. Also, a clap will be highly appreciated:)
Keep your head high and your hacks higher!
Happy hacking! adios ❤
LinkedIn:- https://www.linkedin.com/in/manas-harsh-05636a154/
如有侵权请联系:admin#unsafe.sh