The Good
The last couple of weeks have been somewhat ‘quiet’ with regards to Maze ransomware. It turns out that there may very well be a good reason for that. This week the actors behind Maze ransomware indicated that they are essentially ‘closing up shop’.
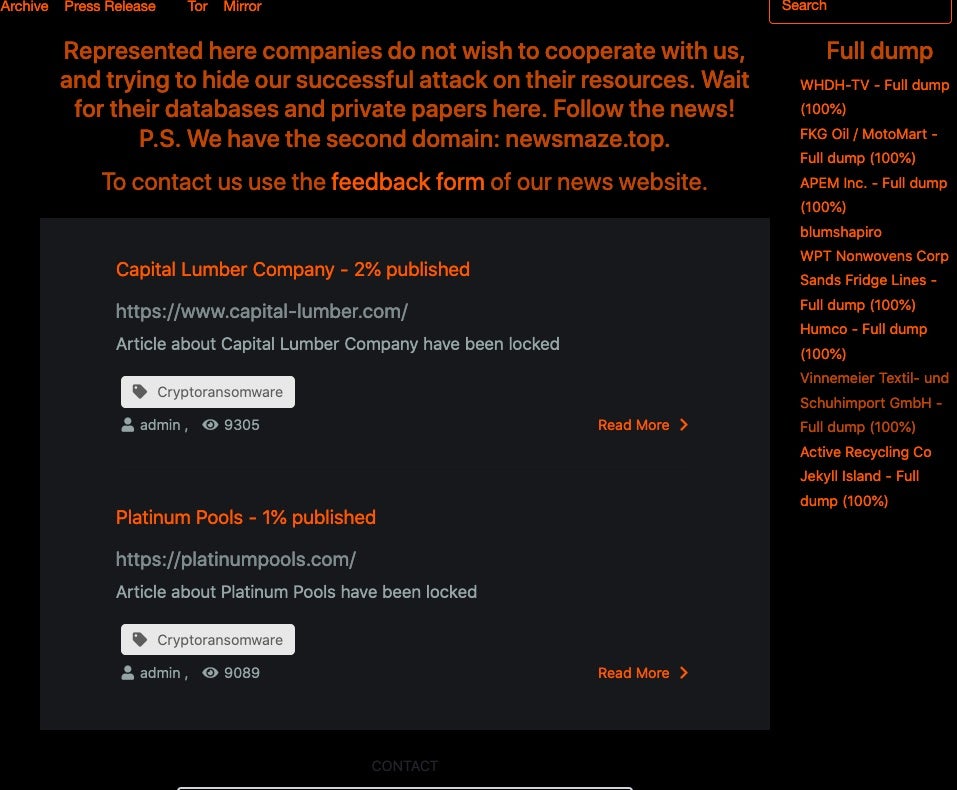
Since Maze debuted in 2019, Maze has proven to be one of the most prolific and aggressive ransomware families. They were one of the first to embrace the ‘double-whammy’ of both encryption and public release of victim data. Similar to other ransomware gangs nowadays, the Maze crew are maintaining a blog. As of today (October 30th), the Maze Crew has listed over 330 companies on their shaming site. Many of those listings are accompanied by full data leaks of all the loot stolen by Maze. The most common industries amongst the listed victims are Financial Services, Consumer Products/Wholesale, Construction, and Financial Services. That said, victims are representing basically all imaginable industries.
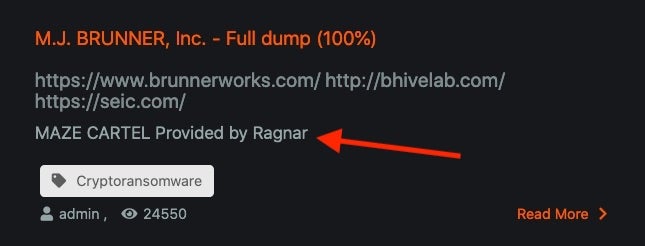
While their blog does not reflect any announcement at this time, they appear to have reduced the amount of information present on their site.
It is yet unknown what will come of other ransomware families that claim to be members of the “Maze Cartel” (ex: Ragnar, SunCrypt). Only time will tell if this ‘shutdown’ is permanent; it is nice to know that we may all experience a break (even if temporary) from these attackers.
The Bad
This week, CISA (Cybersecurity & Infrastructure Security Agency) release Alert (AA20-302A) The joint advisory speaks to an increased focus by Trickbot, Ryuk, and related malware families on targeting high-value healthcare entities.

The alert is explicitly stating, “As part of the new Anchor toolset, Trickbot developers created Anchor_DNS, a tool for sending and receiving data from victim machines using Domain Name System (DNS) tunneling.”
According to the FBI, CISA, and HHS alert, the actors involved have been aggressively deploying Trickbot / Anchor into targeted medical entities to amplify the attack with later-stage Ryuk infections.
Our own SentinelLabs team already identified the team behind Trickbot has been aggressively updating and deploying various modules, including Anchor and Bazar Loader. These evolutionary changes to Trickbot are furthering their reach into high-value targets, including healthcare entities. We have shared research highlighting that the development continues on TrickBot’s Anchor project, using ICMP for command and control communication.
Over the last few years, Trickbot has continued to prove its resiliency. Even recent attempts to disrupt Trickbot have proven only slightly effective, and for a limited time at that. The actors behind these campaigns are well resourced, very well staffed, and focus on dangerous abandon targets. The CISA alert provides detailed guidelines and steps with regards to Mitigations, Ransomware Best Practices, User Awareness Best Practices, Ransomware prevention, along with ample situational contacts. We encourage all to review the thorough alert and swiftly take any action to reduce exposure and improve their defensive posture.
The Ugly
NetWalker, in addition to Ryuk, has been quite active lately. This week Enel Group, a multinational energy company, was highlighted as a victim of NetWalker ransomware. They were promptly listed on the actor’s ‘shaming blog’; Some reports indicate that the attackers demanded a 14 million dollar ransom. Also, Steelcase, a large office furniture company, was hit with Ryuk ransomware. It is reported that the Steelcase campaign, as per standard procedure w/ this actor, initiated the ransomware delivery by way of Trickbot and/or Bazar Loader. Now, breaking away from ransomware and malware in general, we have perhaps the most ‘ugly’ attack of the week….that being an extortion attack on Vastaamo. The Finland-based company runs multiple psychotherapy centers across the country. Attackers allegedly breached the company and made off with hundreds of patient records. It is reported that the attackers gained access to personal and health information, session notes, dates of visits, and billing statements. Some of the affected patients were contacted directly (via email) with individual blackmail requests one step further. The attackers have demanded 40 BTC (~$540k) to halt the pilfered data posting to a site they maintain on the dark web. All these attacks are highly unfortunate and illustrate the depths that the modern adversary will sink to. If anything, this serves as an excellent reminder to continually review your security posture and keep those defenses up!
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
- Cloud Security | Understanding the Difference Between IaaS and PaaS
- Hiding in Plain Sight | The IoT Security Headache and How to Fix It
- Healthcare and Cybersecurity in the Times of Covid-19
- How to Catch a Spy | Detecting FinFisher Spyware on macOS
- APTs and Defending the Enterprise in an Age of Cyber Uncertainty
- Unifying Endpoint Security for Enterprise | An Interview With Migo Kedem
- Revisiting the Pyramid of Pain | Leveraging EDR Data to Improve Cyber Threat Intelligence
- How Ransomware Attacks Are Threatening Our Critical Infrastructure
- The C-suite Guide to Cyber Safety | 7 Steps to Securing Your Organization
