Contribution from Brad Gorka, Vice President, Information Security, CommScope

The next-generation antivirus and endpoint detection & response (EDR) capabilities in SentinelOne are extremely powerful tools for cybersecurity defense, allowing analysts to find a needle in a haystack and then take immediate action – with minimal effort.
While these tools have exceptional potential, they can be even better when coupled with the wisdom of the infosec community and security analysts making high-quality decisions. Most experts will consider there to be a significant risk when true malware is classified as a false positive, but I realized there is also great concern with benign objects being classified as malware.
In the latter case, the result is that the object is blacklisted on all endpoints in scope. If the analyst gets it wrong, they could potentially blacklist something that could cause business interruption – such as a home-grown application needed for a critical process. But if the object is pervasive throughout most of your endpoints, this error can be catastrophic on a large scale.
Recognition of this led me to come up with a concept I named Guard Rails, which was submitted to our SentinelOne account management team and ended up on their roadmap. And now, a few months later, the feature is in the product and being used!
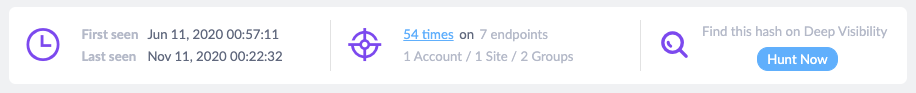
Guard Rails uses data that is already resident in the SentinelOne platform. We can query Network history to see how many other endpoints across the scopes have seen a similar alert. In addition, SentinelOne now has a ‘hunt now’ pivot button that allows you to see the potential impact of adding something to an exclusion list (aka “blacklist”).
This is quite simple, but crucial, data. For example, if an object hash is found 15 times on three devices, we can infer that a mitigation action will have a lower operational risk than another hash which is found 1,563 times on 1,560 endpoints. In the latter scenario, the analyst will immediately know that if he excludes that object it is going to impact a large number of systems. If the object is indeed malicious then that is what we need to do, but the impact assessment offered by Guard Rails gives the analyst pause to better understand and research the object and associated events. By providing this simple calculation using existing data we can guide the analyst to make better quality decisions.
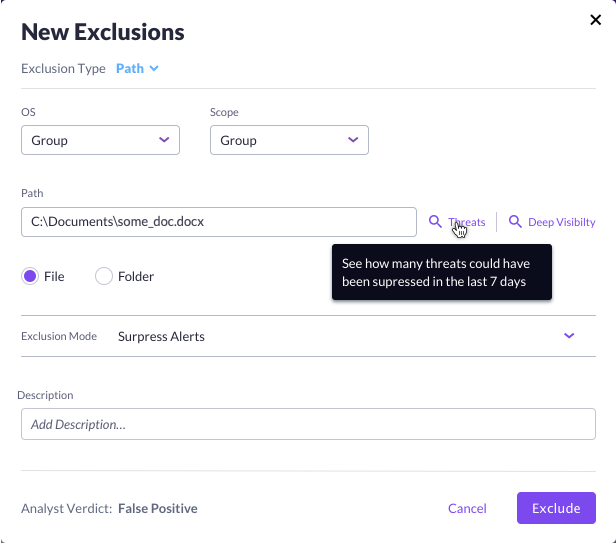
SentinelOne is also integrating another Guard Rail directly in the analyst workflow when adding a hash to the blacklist, and even on counter cases when the analyst excludes an application. Right there when the analyst is about to take action, they can pivot to either the threat list associated with that hash or to Deep Visibility to query the hash or path. This way the analyst can understand the potential impact of the action, before applying it.
I truly believe that Information Security is a team sport. Because of that mantra, an additional road mapped feature includes a crowdsourcing element to further enrich information for the analyst. And it does not end there; by using already-available data, SentinelOne can provide aggregate (non-identified) information from the larger SentinelOne customer base to provide information like:
- Are other SentinelOne customers also seeing this threat?
- How many have taken mitigation actions on the object?
This will definitely help analysts increase the confidence level in actions they take.
We are fighting a war…every day. We need good tools to help cybersecurity operators make better and faster decisions, augmented and enhanced by the artificial intelligence capabilities like you’ll find in SentinelOne. As an industry, we also need to help one another out and be allies in this war so that together we can be successful. Over the past 6-12 months, I have witnessed an increase in this type of collaboration between companies, trade groups, and law enforcement. I believe that is the right path, and it is working. I’d like to thank SentinelOne for listening to my idea, building upon it, and quickly deploying it to the product.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
- Cloud Security | Understanding the Difference Between IaaS and PaaS
- Hiding in Plain Sight | The IoT Security Headache and How to Fix It
- Healthcare and Cybersecurity in the Times of Covid-19
- How to Catch a Spy | Detecting FinFisher Spyware on macOS
- APTs and Defending the Enterprise in an Age of Cyber Uncertainty
- Unifying Endpoint Security for Enterprise | An Interview With Migo Kedem
- Revisiting the Pyramid of Pain | Leveraging EDR Data to Improve Cyber Threat Intelligence
- How Ransomware Attacks Are Threatening Our Critical Infrastructure
- The C-suite Guide to Cyber Safety | 7 Steps to Securing Your Organization