2020-11-18 20:46:53 Author: blog.elcomsoft.com(查看原文) 阅读量:257 收藏
Hashcat is a great, free tool competing head to head with the tools we make. We charge several hundred dollars for what, in the end, can be done with a free tool. What are the reasons for our customers to choose ElcomSoft products instead of Hashcat, and is the expense justified? We did our best to compare the two tools to help you make the informed decision.
Both Hashcat and Elcomsoft Distributed Password Recovery are tools for breaking passwords. Both tools can perform hardware-accelerated brute-force attacks using conventional video cards, and both tools can do dictionary and smart attacks. Both tools can use distributed networks to speed up the attacks, yet Hashcat needs a third-party tool for that. Both are thoroughly optimized to offer the highest performance on hundreds of file formats. On paper, the two tools have so many similarities they may look alike. The usage experience in typical use cases, however, could not be more different.
System requirements
Elcomsoft Distributed Password Recovery is a Windows only product. You need Windows 7, 8, 8.1 or Windows 10 to run both the server and each of the clients. If you are using distributed attacks, each of the computers comprising the distributed network must run Windows.
In addition to Windows, you need proper drivers. Elcomsoft Distributed Password Recovery is comfortable with officially released versions of NVIDIA drivers; we’ve seen no nasty surprises with either Studio or Gaming drivers as long as they come with CUDA. AMD drivers are a bit sketchier, so we have to test major releases for compatibility. If you’re using a different GPU, the correct OpenCL driver must be installed in order for the hardware acceleration to work.
Hashcat is a cross-platform tool supporting all major versions of Windows, macOS, and many Linux distributions. However, you’ll be hard-pressed to find one single platform on which all of the Hashcat features work. From time to time, you’ll need Hashcat to use several host operating systems to perform its duties. As an example, you’ll need a Mac to extract encryption metadata from FileVault disks.
In addition to the host OS, you’ll also need the following to utilize some or all Hashcat features.
- git (optional but recommended)
- Perl
- Python
- C/C++ compiler, correctly configured and equipped with the required libraries. Some hash extraction utilities are available exclusively in source code with no precompiled binaries.
Hardware acceleration
Both tools advertise hardware acceleration to speed up brute-force attacks. The devil is in the detail.
Elcomsoft Distributed Password Recovery offers GPU acceleration on NVIDIA video cards, while some formats can utilize AMD hardware. Our tool can also utilize OpenCL, the open standard for parallel programming of heterogeneous systems. Thanks to OpenCL support, Distributed Password Recovery can utilize the GPU units found in many Intel processors, which can deliver several times the typical performance of CPU cores. Should GPU acceleration be unavailable on a given system or for a given format, the tool transparently falls back to CPU-only implementation.
Hashcat is decidedly GPU only. The tool requires an AMD or NVIDIA video card to work, and you’ll need a compatible version of the graphic driver. Where Hashcat requires the use of the OpenCL runtime to interface with compatible CPUs (which we struggled to enable), Distributed Password Recovery addresses the CPU cores directly, utilizes the native CUDA for interfacing with NVIDIA boards, and uses OpenCL for everything else.
Supported formats
Even the best password recovery tool is worth nothing if it does not support that one encrypted data format you urgently need to break. On paper, Hashcat supports a larger number of formats compared to our tool. While both Hashcat and Elcomsoft Distributed Password Recovery advertise hundreds of supported formats and generally tick all the basics, our tool covers a few things that Hashcat does not. These include:
- Office 97/2003 (key search)
- PDF with 40 bit encryption (key search)
- Apple iWork (Pages, Numbers, Keynote)
- Hangul/Hancom Office (HanWord, HanCell)
- PGP ZIP archives (.PGP) (password recovery)
- PGP secret key rings (.SKR) (passphrase recovery) (GPU accelerated)
- PGP disks with conventional encryption (.PGD) (password recovery) (GPU accelerated)
- PGP self-decrypting archives (.EXE) (password recovery)
- PGP whole disk encryption (password recovery) (GPU accelerated)
- Intuit Quicken
- macOS keychain password (GPU accelerated)
- BlackBerry backups (.IPD, .BBB) (password recovery) (GPU accelerated)
- FileMaker
- Apple Disk Image (.DMG) passwords
- DashLane password manager
- Tally ERP 9 Vault passwords
Setting up and initial configuration
The greater differences are experienced when setting up and configuring the tools for the first time. When installed on a single computer, Elcomsoft Distributed Password Recovery is essentially a plug-and-play endeavor: you download the installation file, double-click to install, then launch the product from the Windows Start menu. That’s pretty much it; the tool automatically launches the required components (the client, server, and interactive management console) and detects the available acceleration resources. By the time you see the main window, the tool is ready to run your first attack.
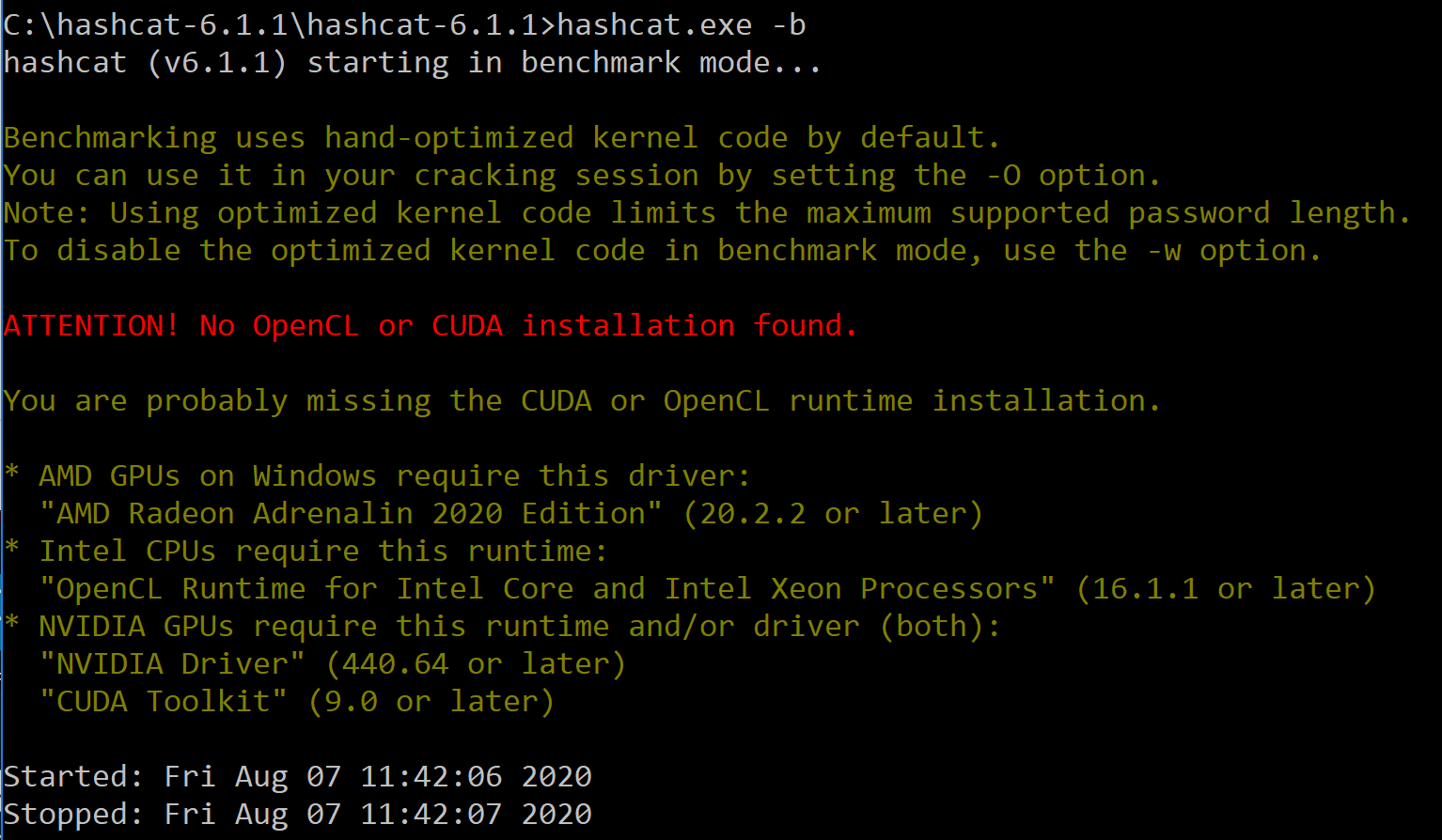
Hashcat offers a typical Linux experience even if you are using it in Windows. All goes well if you already have the compatible GPU with compatible drivers. Should something go wrong, and you may need to spend extra time troubleshooting. This, for example, is what we’ve seen when trying to benchmark Hashcat on an Intel CPU in a Windows VM:
Apparently, an OpenCL runtime is required to run attacks on Intel CPUs. Obtaining OpenCL runtime for Intel Core was borderline amazing. The runtime is only available to developers with Intel developer accounts. Registering the account and waiting for its approval took a day; however, we were still unable to run Hashcat on that computer even with the OpenCL runtime installed.
To its credit, Hashcat would run normally in Windows once we installed a compatible NVIDIA board. We could also launch Hashcat in Linux using the same video card. This time the quest was less puzzling; all that we needed to do was using the particular version of Ubuntu, carefully uninstalling the pre-installed NVIDIA drivers (a wrong move bricks the system), adding the recommended drivers repository and installing the recommended driver from that repository. Piece of cake if you use NVIDIA. We failed the quest when we tried using an AMD card though.
To sum it up, you need a supported OpenCL device to use Hashcat. NVIDIA boards are supported; you’ll need some luck for AMD or Intel. If you use Ubuntu, you’ll require an NVIDIA board. Elcomsoft Distributed Password Recovery, on the other hand, just… works.
To be continued
In the next part of the series, we’ll talk about the general workflow of the two products, distributed and cloud attacks.
REFERENCES:
![]()
Elcomsoft Distributed Password Recovery
Build high-performance clusters for breaking passwords faster. Elcomsoft Distributed Password Recovery offers zero-overhead scalability and supports GPU acceleration for faster recovery. Serving forensic experts and government agencies, data recovery services and corporations, Elcomsoft Distributed Password Recovery is here to break the most complex passwords and strong encryption keys within realistic timeframes.
Elcomsoft Distributed Password Recovery official web page & downloads »
如有侵权请联系:admin#unsafe.sh