The Good
What could be better than a new security feature? Why, one that users are asked for their input as it’s developed and rolled out, of course! In a welcome move for browser security and user participation, Mozilla this week announced that it is opening a public “comment period” regarding its recent DNS-over-HTTPS (DoH) feature.
Quick refresher: DNS is the means by which browsers “lookup” the actual IP address of domain names, like sentinelone.com, for example. However, these lookups travel across the network – through various gateways and servers – entirely unencrypted. That means each of those points can both potentially “sniff” and interfere with the lookup. With DoH (pronounced “dough”, apparently), DNS lookups are encrypted between the requesting browser and the DNS resolver via HTTPS.

Source: Mozilla
What’s not to like? Well, ISPs for one aren’t over-the-moon about it because it can disrupt their ability to inject ads into users’ browsing requests. However, there are other, more legitimate, concerns such as making it more difficult for security tools to monitor and filter malicious web traffic. In the UK, authorities use DNS as a tool to fight child exploitation by filtering out domains serving up illegal content.
Given these concerns and the many different use cases for DNS filtering, Mozilla have taken the welcome step of eliciting public comment, open until January 4th 2021, on how the feature should be deployed. The company say they want to “crowdsource ideas, recommendations, and insights that can help us maximise the security and privacy-enhancing benefits of our implementation of DoH”. They go on to say that they “We welcome contributions for anyone who cares about the growth of a healthy, rights-protective and secure Internet”. Apple, take note?
The Bad
While we’re on the topic of web security, this week’s bad news concerns a suspected REvil ransomware attack on managed web hosting solution provider Managed.com. While the attack at first seemed to be limited in scale, the company soon had to take down its entire web hosting infrastructure, which affected blogging platform giants WordPress, among others.
The company says that it is both working to resolve the incident and cooperating with law enforcement agencies in an attempt to identify the entities involved in the attack. That’s not just out of a sense of public duty; it is pretty much a requirement these days as companies need to ensure that if they consider paying the attackers, they will not risk legal sanctions for dealing with certain proscribed entities.
BleepingComputer report that the perpertrators were likely REvil and that they are demanding a $500,000 ransom for a decryptor.
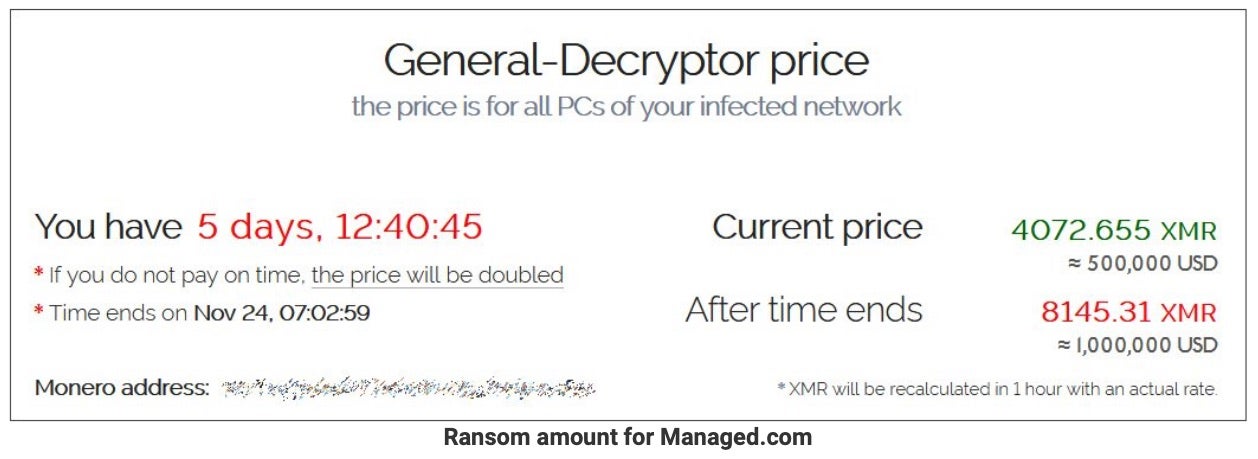
Source: BleepingComputer
There’s no suggestion at this point that Managed.com have had any contact with the perpetrators. Per their official statement, the company say their “Technology and Information Security teams are working diligently to eliminate the threat and restore our customers to full capacity.”
The Ugly
Since the start of the pandemic in early 2020, video conferencing software has come under a lot of scrutiny with regard to security, with Zoom, for example, taking a lot of the early heat. But the problems they faced were perhaps nowhere near as serious as three recently disclosed vulnerabilities in Cisco Webex.
Researchers from IBM discovered that Webex meetings could be “haunted” by invisible participants. These uninvited “ghost” guests could join meetings without showing up in the participants list and could remain in the meeting even if the host tried to expel them. To top it all, a third vulnerability made it possible to gather information about other attendees without joining the meeting at all.
According to the researchers, the vulnerabilities reside in the way Cisco Webex handles the “handshake” process between the client app and the Webex server and affect both scheduled meetings and Webex Personal Rooms. The vulnerabilities were also demonstrated on multiple platforms, including Windows, macOS and iOS.
IBM claim that employees now spend over 5 billion minutes per month in virtual meetings, which makes these kind of flaws extremely inviting targets for threat actors.
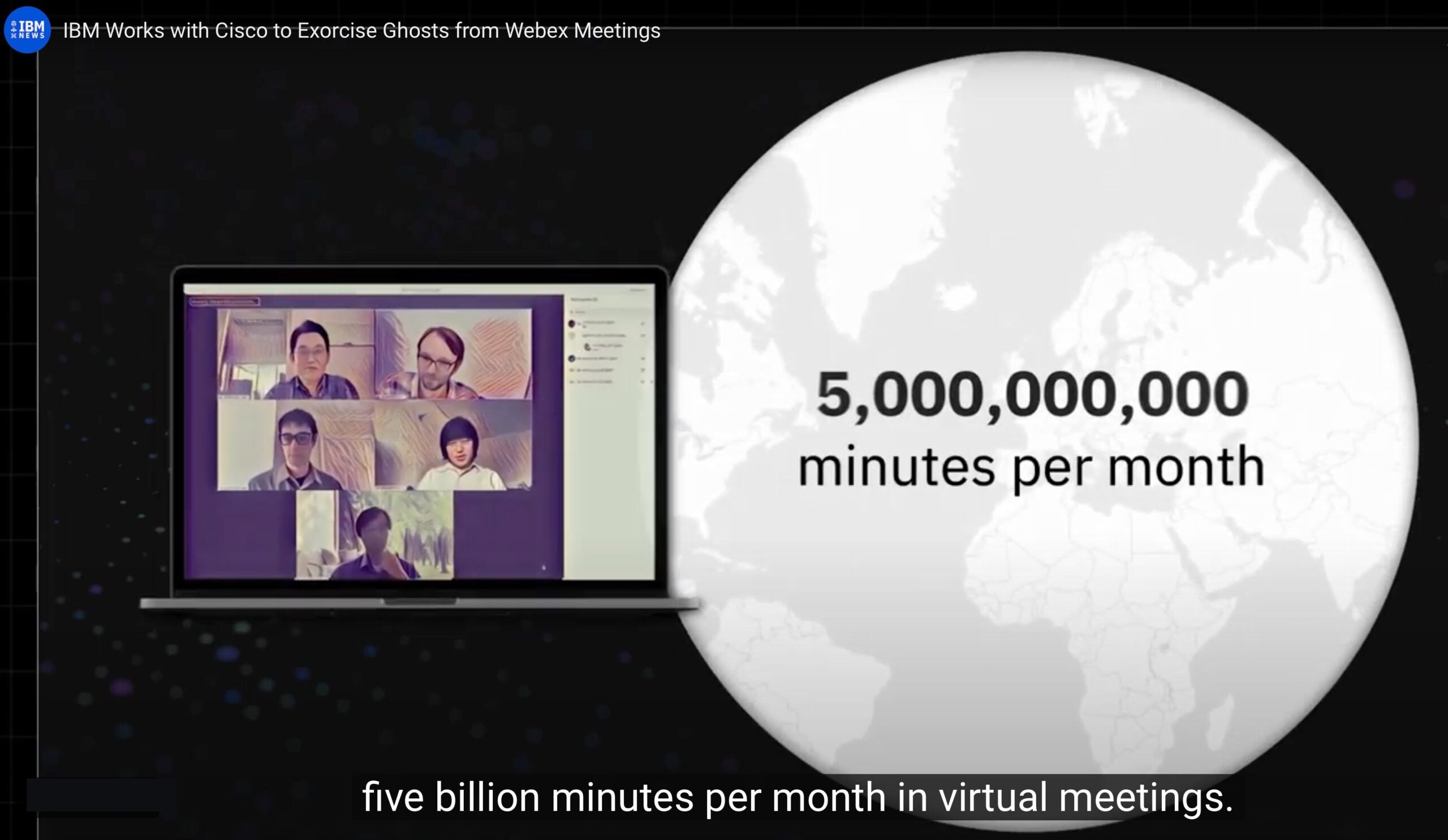
Source: IBM Research
However, there’s no evidence at the moment to suggest that malicious actors have been abusing the bugs, and Cisco have released security patches for both the Cisco Webex server and all affected client applications. Users of Cisco Webex client and server software are advised to patch without delay.
Meanwhile, the researchers filed three CVEs against the vulnerabilities, namely CVE-2020-3441, CVE-2020-3471, and CVE-2020-3419.
Like this article? Follow us on LinkedIn, Twitter, YouTube or Facebook to see the content we post.
Read more about Cyber Security
- What Happened to My Mac? Apple’s OCSP Apocalypse
- macOS Big Sur Has Landed | 10 Essential Security Tips You Should Know
- SentinelOne Guard Rails | Working Together to Secure Better
- Cloud Security | Understanding the Difference Between IaaS and PaaS
- Hiding in Plain Sight | The IoT Security Headache and How to Fix It
- Healthcare and Cybersecurity in the Times of Covid-19
- How to Catch a Spy | Detecting FinFisher Spyware on macOS
- APTs and Defending the Enterprise in an Age of Cyber Uncertainty
