
2020-11-23 09:30:29 Author: medium.com(查看原文) 阅读量:292 收藏
Hi everyone,
This blog is about how I found the Facebook Messenger iOS App Leaking Access Token Of Million Users to Third Party Site(GIF search engine)

I was testing an iOS application by intercepting the API requests through Burp. After a few hours of testing, I have ended up with nothing. I just closed that app in iPhone and swiping at the notifications.
There I saw one of my college mates had texted me in Messenger. After tapping on it I was moved to Messenger app and I have searched for a GIF to make a reply to her message. At the moment I came to remember that I‘m using burp proxy and I have looked into the burp history. Many Tenor GIF requests are sent. I was simply looking at all the requests and responses. After noticing that “access_token” leaking in all Tenor GIF requests I was like

What is Access Token?
An access token is some kind of a temporary token or a key which is used to perform certain actions on behalf of the user
What we can do with that?
Using token we can access the user’s account without password
Immediately I have reported the issue to Facebook. They took one day to investigate and the next day they sent to the Product Team. Within 5 hours they pushed an update with a temporary fix
POC Video:
Timeline:
26-Sep-2020: Report Sent
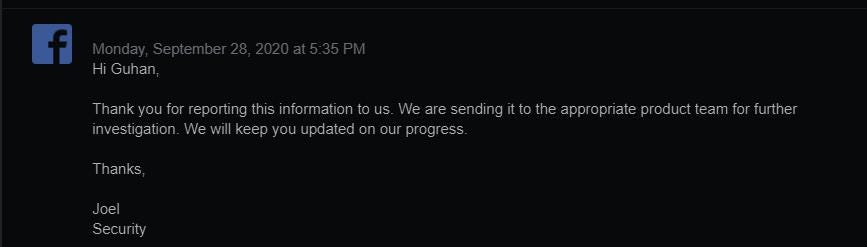
28-Sep-2020: Further investigation by Facebook
28-Sep-2020: Temporary Fix
06-Oct-2020: Fixed
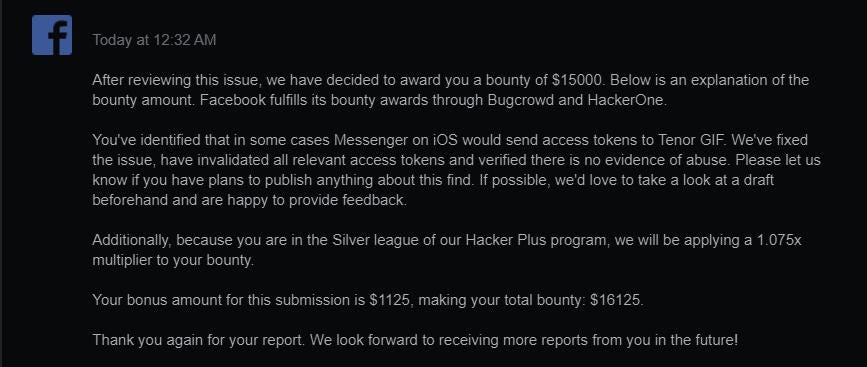
10-Nov-2020: Rewarded 15k$
Conclusion:
Facebook has confirmed that there is no evidence of abuse and has invalidated all relevant access tokens
Thanks to Priya Sarvesan(my classmate who texted me :p) and Facebook Security Team
如有侵权请联系:admin#unsafe.sh