2020-12-03 15:50:31 Author: blog.elcomsoft.com(查看原文) 阅读量:333 收藏
After adding jailbreak-free extraction for iOS 13.5.1 through 13.7, we now support every Apple device running any version of iOS from 9.0 through 13.7 with no gaps or exclusions. For the first time, full file system extraction and keychain decryption are possible on all devices running these iOS versions.
Full iOS 13 support without a jailbreak
When extracting an iOS device, one needs low-level access to the device. Years ago, we developed a workflow to allow experts imaging the device’s file system and decrypting the keychain. That workflow largely relied upon publicly available jailbreaks. While decidedly not forensically sound, this process was the only chance of accessing the full content of the device including all keychain records, private chats and application data not included in backups.
We were never completely satisfied with the workflow, and so we developed a different method for accessing the data that does not require a jailbreak. This all-in-one extraction method utilizes an extraction agent of our own development. Once installed, the agent automatically escapes sandbox, escalates privileges and establishes a communication channel with the computer. Agent-based extraction provides numerous benefits over jailbreak-based acquisition, being a lot safer, a lot faster, and a lot more robust.
We are continuously working on extending the agent’s compatibility. Starting today, users of iOS Forensic Toolkit 6.60 and subsequent releases will be able to perform the complete extraction (file system and keychain) of Apple devices running all versions of iOS starting with iOS 9.0 through iOS 13.7 (up from the previously supported iOS 13.5). This covers devices ranging from the iPhone 5s through iPhone 11 Pro Max if they run one of the versions of iOS mentioned above.
Steps to extract the file system and decrypt the keychain
To extract the file system and decrypt the keychain from an iOS device without a jailbreak, follow these steps.
Install iOS Forensic Toolkit 6.60 or newer. On macOS, the Toolkit is now distributed as password-protected DMG file (in older versions, the DMG was not protected with a password, but packed into RAR archive with a password). Do not forget to clear the ‘quarantine’ flag from DMG file on Catalina and Big Sur before mounting it (see Installing and using iOS Forensic Toolkit on macOS 10.15 Catalina).
Connect the device in the powered-on state with a Lightning cable and establish trust relationship if needed. If requested, you will have to unlock the device and enter the passcode for pairing.
Launch the Toolkit (Toolkit.cmd on Windows or Toolkit.command on macOS). On macOS, do not run the script directly from the mounted image, but copy the Toolkit files onto a local disk into a folder such as “EIFT” first. All the features your need are grouped under the Acquisition agent. We recommend keeping the device in Airplane mode.
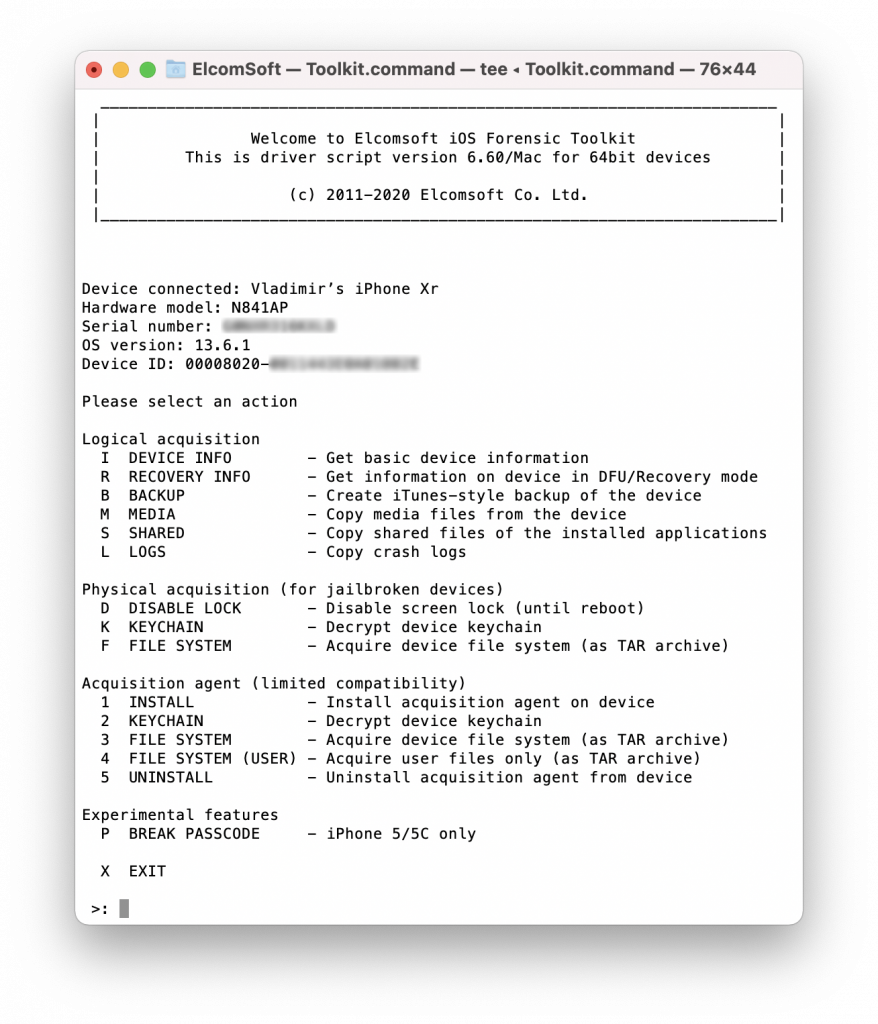 Install the Agent. Press [1] to sideload the agent module to the device. The device should be unlocked and paired; the local antivirus software should should be temporarily disabled. You will be prompted for an Apple ID first. In Windows, you can only use an Apple ID registered in the Apple Developer Program; on macOS, you can use any Apple ID including throwaway accounts. This Apple ID is not related to the Apple ID used on the device you are investigating.
Install the Agent. Press [1] to sideload the agent module to the device. The device should be unlocked and paired; the local antivirus software should should be temporarily disabled. You will be prompted for an Apple ID first. In Windows, you can only use an Apple ID registered in the Apple Developer Program; on macOS, you can use any Apple ID including throwaway accounts. This Apple ID is not related to the Apple ID used on the device you are investigating.
You will be prompted for a password for that Apple ID. In Windows, use an app-specific password generated in advance in My Apple ID; in macOS, use the regular password, but you will have to pass two-factor authentication by entering the code delivered to a trusted device.
If the given account is connected to more the one developer program (Windows) or at least one (macOS), you will be prompted to choose one.
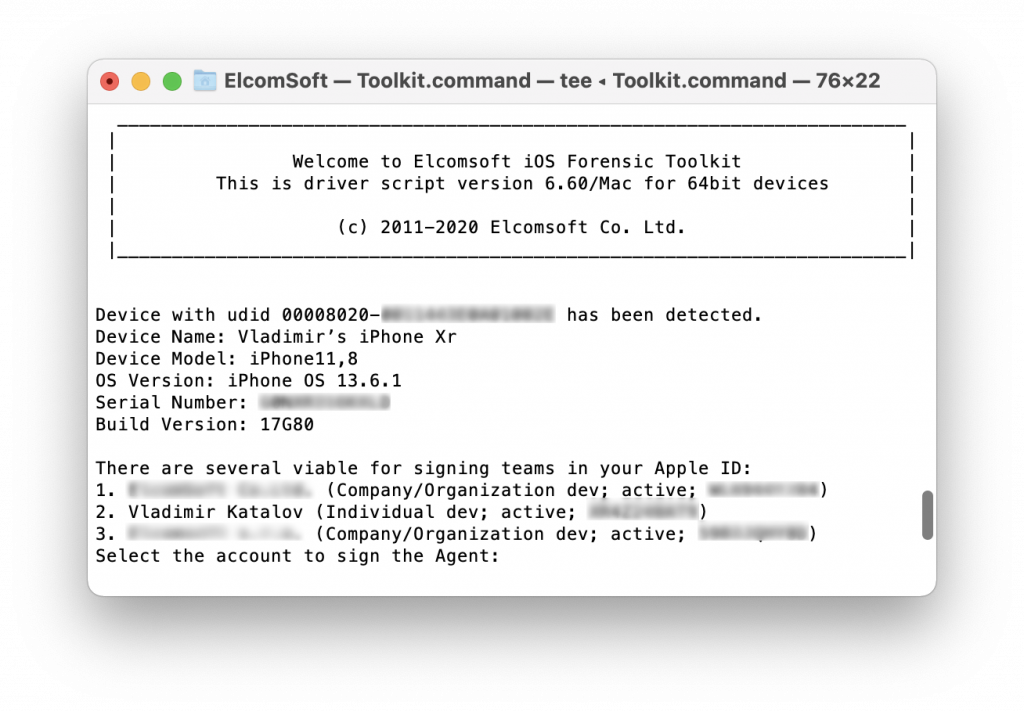 The Toolkit signs the main agent module for the connected device and sideloads it there:
The Toolkit signs the main agent module for the connected device and sideloads it there: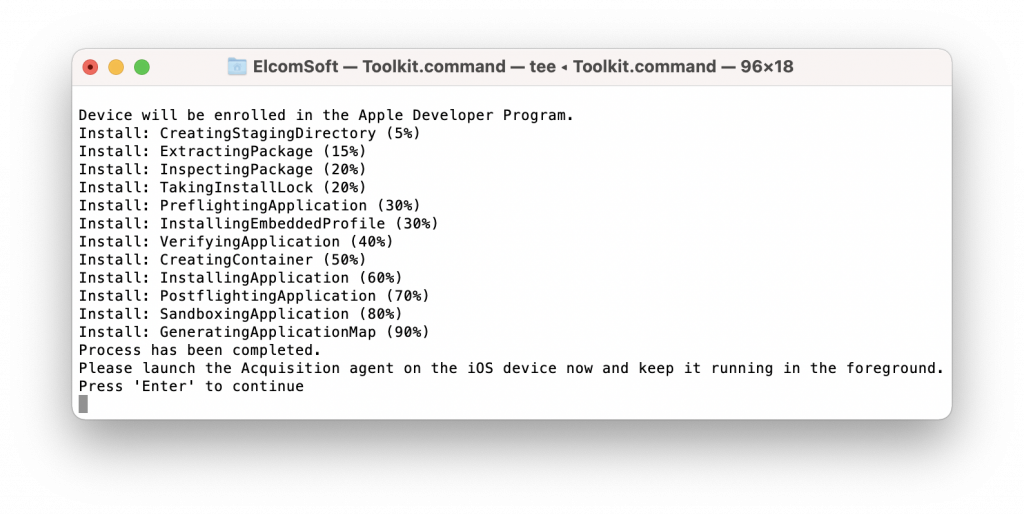 The Agent icon (the app name is Acquisition) now appears on the iPhone screen:
The Agent icon (the app name is Acquisition) now appears on the iPhone screen:
Tap on the app icon to launch, and keep it running in the foreground. If you used a non-developer account to sign the app, an extra step is required: you’ll need to approve the certificate; see Extracting iPhone File System and Keychain Without an Apple Developer Account for more details.
Now you can extract the keychain, capture the file system image or extract user files.
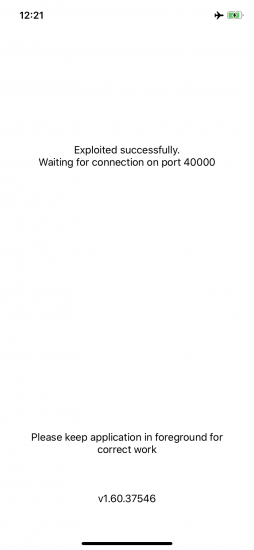
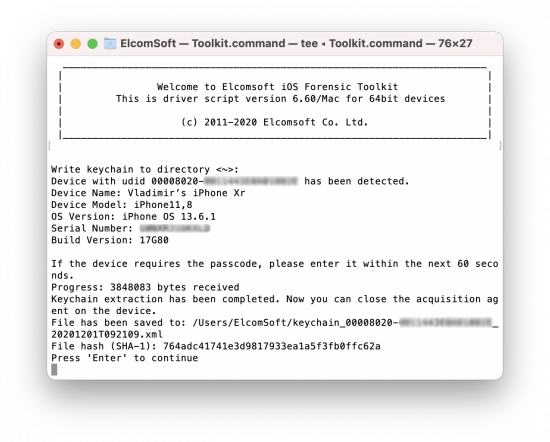
Extract the keychain. Press [2] to start keychain extraction. The Agent obtains root privileges, which is safe for the device and the data, but may cause a reboot of the device. If that happens, reconnect the device (pairing might be required again), close the Agent, launch it again, and try again. In the worst case it may take up to 3 or 4 attempts until the exploit works. On success, you should see the Exploited successfully message first. Exploiting may take up to 30 seconds, depending on the device model and iOS version.
Note that extracting the keychain requires you to give the permission to use Face ID or Touch ID, and then using biometrics or entering the device passcode (note the Acquisition app name); this is mandatory for the correct operation of the Agent app in order to get the full keychain contents, including records with the highest protection class:
 Extract the file system. Press [3] to extract the full file system image, or [4] to save the user’s files excluding the system partition:
Extract the file system. Press [3] to extract the full file system image, or [4] to save the user’s files excluding the system partition:
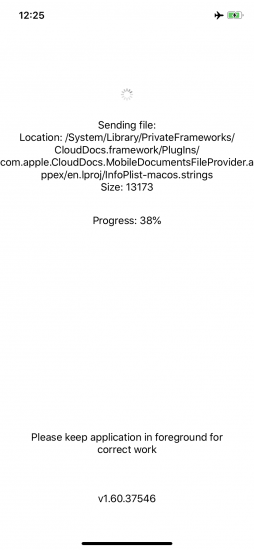
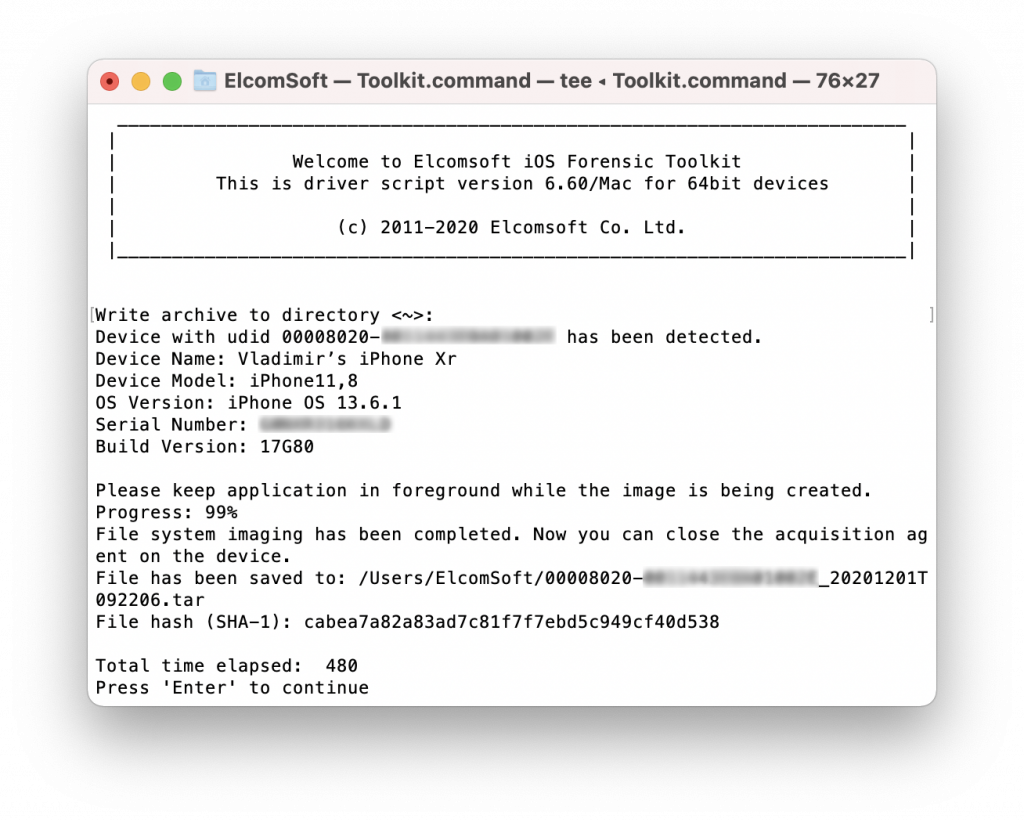 Once the imaging is complete (the speed is usually 30 to 35 MB/s), the Toolkit outputs the hash sum (SHA-1) of the extracted image/archive. Please note that the progress reporting may differ between the Agent and in Toolkit user interface.
Once the imaging is complete (the speed is usually 30 to 35 MB/s), the Toolkit outputs the hash sum (SHA-1) of the extracted image/archive. Please note that the progress reporting may differ between the Agent and in Toolkit user interface.
For the test device we used an iPhone Xr running iOS 13.6.1. The file system image was 15.6 GB, copied in 8 minutes. The user partition was 7.4 GB only, copied in 3.5 minutes. Imaging a 512 GB model full of data may take about 4 hours.
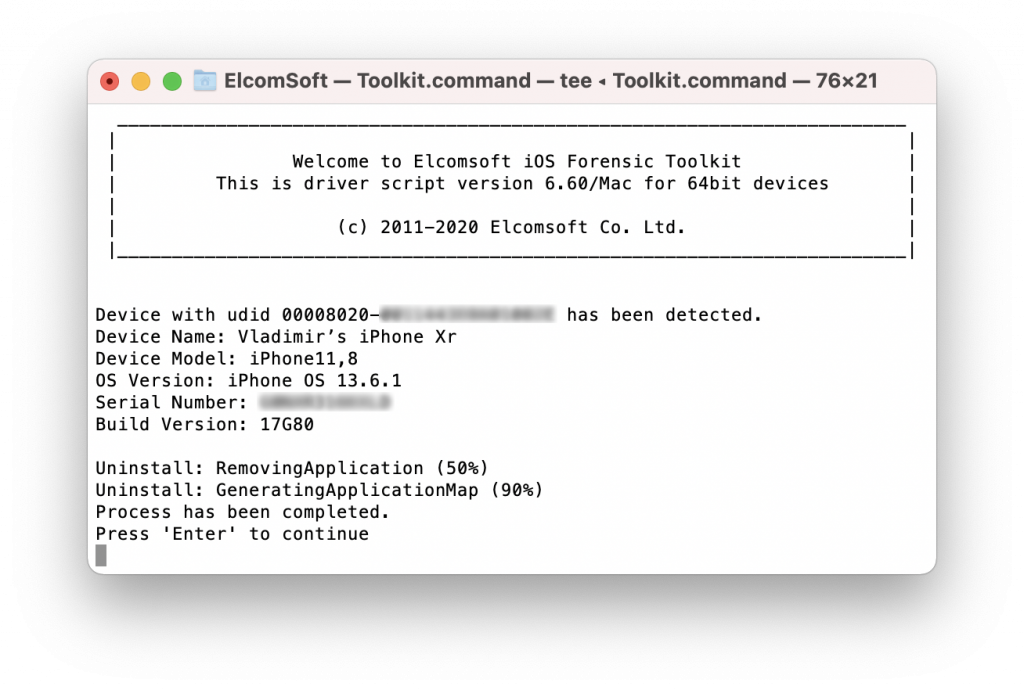
Remove the agent. Press [5] to uninstall the agent from the device. Note that some traces of using the Agent are left on the device (e.g. in the log files).
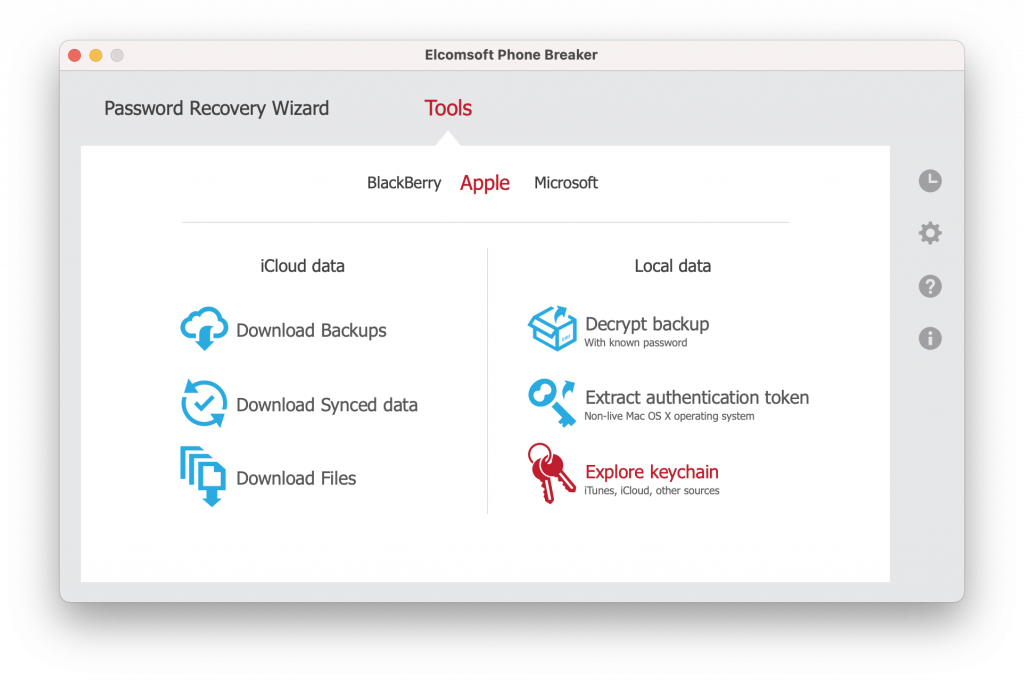
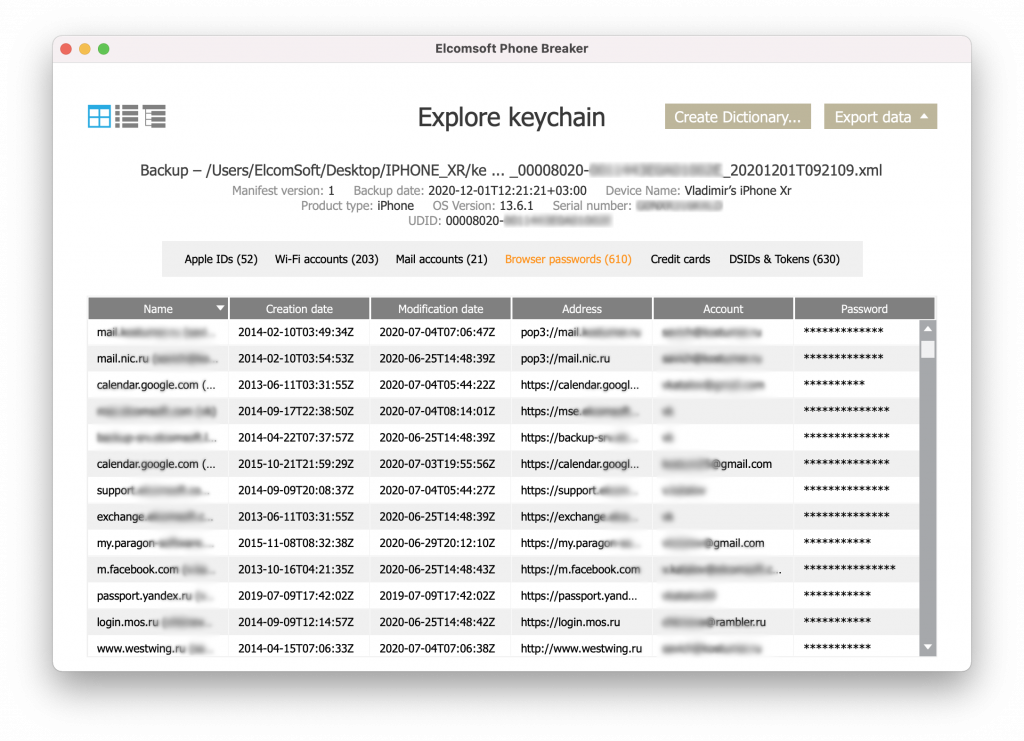
 Further analysis. The keychain can be analyzed using Elcomsoft Phone Breaker:
Further analysis. The keychain can be analyzed using Elcomsoft Phone Breaker:
 To browse and analyze the content of the extracted file system image, use the quick and lightweight Elcomsoft Phone Viewer or a fully-featured forensic package such as Oxygen Forensic Detective.
To browse and analyze the content of the extracted file system image, use the quick and lightweight Elcomsoft Phone Viewer or a fully-featured forensic package such as Oxygen Forensic Detective.
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh