Introduction
The Digital Footprint Intelligence Service announces the results of research on the digital footprints of governmental, financial and industrial organizations for countries in the Middle East region: Bahrain, Egypt, Iran, Iraq, Jordan, Kuwait, Lebanon, Oman, Qatar, Saudi Arabia, Sudan, Syria, Turkey, UAE, Yemen. The data presented in this report was collected through Kaspersky’s own threat research and analysis mechanism and various other open sources during Q3 2020. The exceptions are Iran, Iraq, Sudan, Syria and Yemen for which only open source data was used. Official entities can request the more detailed results of subsequent research and analysis via [email protected].
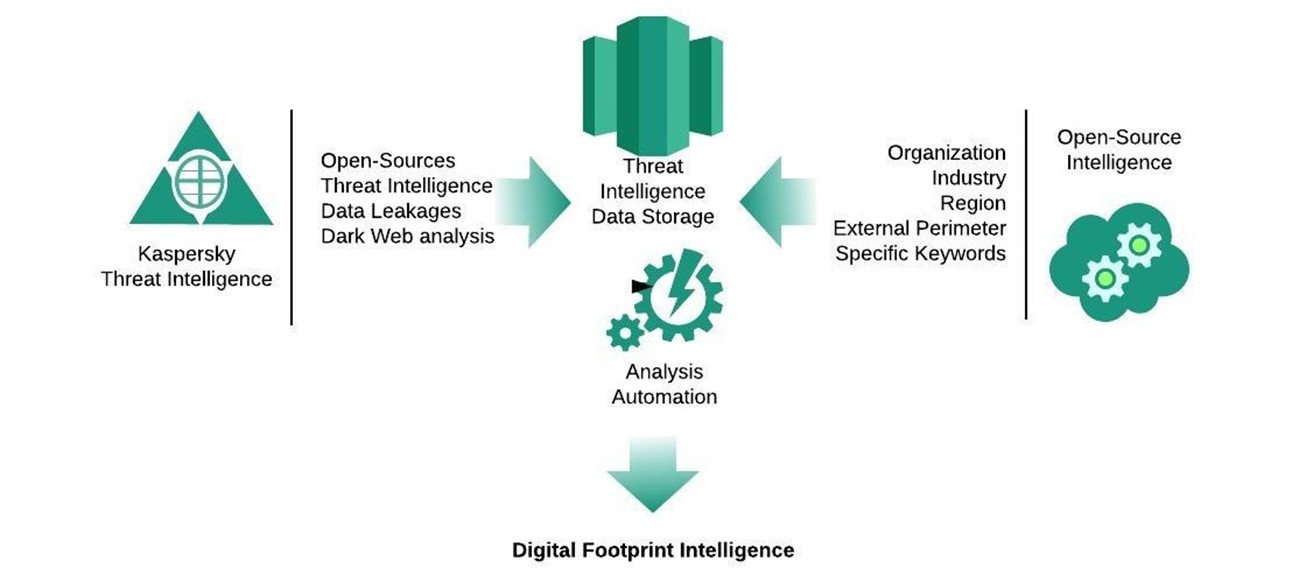
The service is designed to provide customers with an analysis of their footprint in open networks and an overview of the opportunities presented to adversaries. Assessing a company’s assets from the perspective of an attacker and their possible intentions and potential opportunities were among the key considerations for cyberthreat intelligence analysts when compiling this report.
Sources of intelligence
Scope of report
There are many organizations that belong to the three key verticals – governmental, financial and industrial – across the Middle East region, but this report focuses on critical organizations with vulnerabilities.
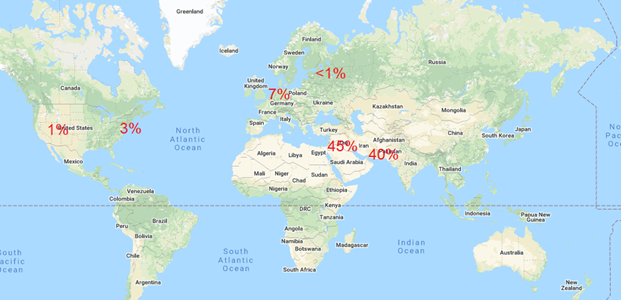
Distribution of vulnerable IP addresses by percentage
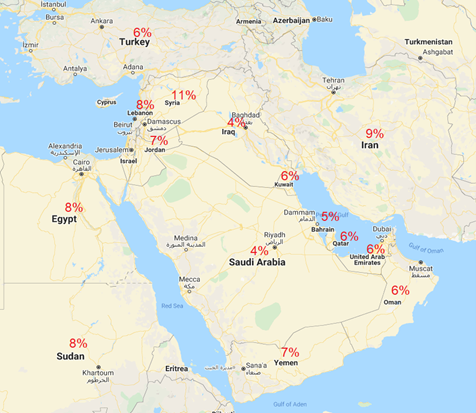
Share of vulnerabilities by country in the Middle East region
Statistics of detected vulnerabilities on services (download)
What’s behind the statistics
| Vulnerable networks | Data leaks | Dark web |
| Lack of security updates
Bad network service configuration Management interfaces available publicly |
Corporate accounts in databases of leaked passwords | Leaked financial data
Access to compromised infrastructure for sale |
Methodological materials
Depending on the complexity of the exploitation and the damage cause, the detected vulnerabilities are divided into five levels:
- Critical – Vulnerabilities that, if exploited, can compromise an infrastructure resource in one step;
- High – Vulnerabilities that, if exploited, will give access to infrastructure in two or more steps. Additional data (e.g. credentials) to penetrate the infrastructure may be required;
- Medium – Vulnerabilities that allow an attacker to obtain useful information about a resource that can be used to obtain restricted access: e.g. management interfaces of various services, directory listing, protocols used to unencrypt data transfer, etc.;
- Low – Vulnerabilities that allow an attacker to collect information about a resource, such as logins used in the system, access as anonymous user to various services, etc.;
- Information – Vulnerabilities related to security flaws, such as default and start pages of web services, printer services and various software that can be used to perform DDoS attacks, routing protocols, etc.
Importance of vulnerability based on industry vertical
The governmental sector leads the way in critical-level vulnerabilities, whereas the standard cybercriminal target – the financial industry – has mostly low-level vulnerabilities.
Industrial companies fall in the middle of this spectrum, though their share of medium-level vulnerabilities still deserves attention. Most of these vulnerabilities lead to the disclosure of information about a resource that can be used to obtain restricted access.
Share of vulnerabilities across various verticals (download)
Share of vulnerable companies across various verticals (download)
Which companies have critical vulnerabilities?
- 30% of industrial companies have critical-level vulnerabilities;
- Every third industrial company is prone to critical-level vulnerabilities;
- Every second industrial and government organization has high-level vulnerabilities;
- 7% of all banking organizations in the Middle East have critical vulnerabilities.
Vulnerabilities that can be exploited by adversaries
Security issues in various verticals:
- 2% of governmental organizations in the scope of the research have Microsoft Windows 2000 in their environments;
- Large share of misconfigured services in industrial companies indicates a low level of information security maturity;
- Among the resources in the industrial sector, both old vulnerabilities (e.g. HEARTBLEED) and the latest vulnerabilities (e.g. vulnerabilities in Citrix network equipment) were found.
Vulnerabilities by categories (download)
Vulnerable services by type (download)
Which services are vulnerable?
- 3% of vulnerable web servers are related to banking organizations;
- DBMS and FTP servers are most vulnerable in industrial companies;
- 3% of all exposed remote management interfaces belong to government bodies, placing them first worldwide.
Statistics on obsolete software in companies of the Middle East region
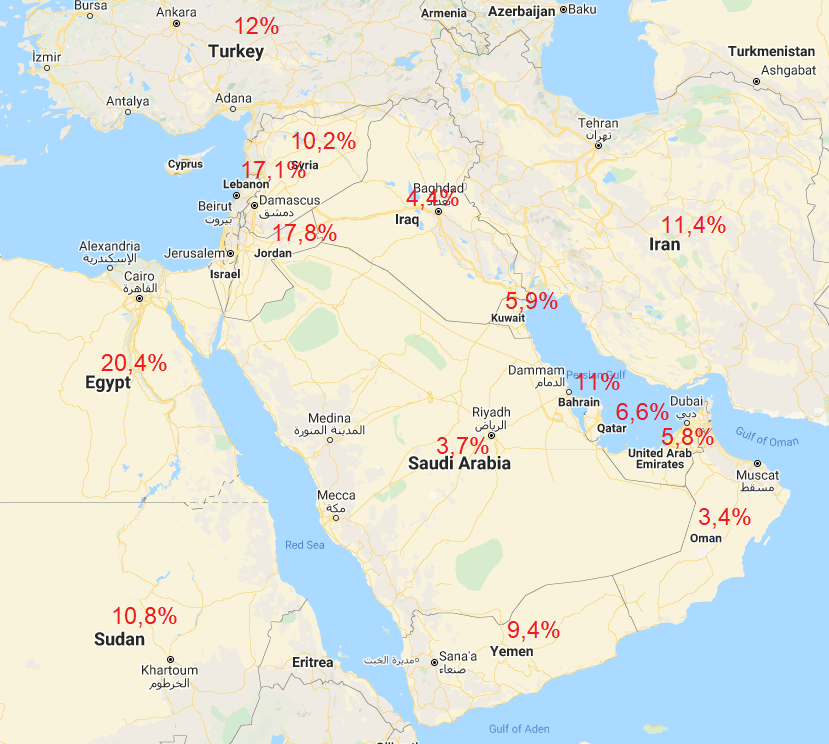
Obsolete software in the region
Data leaks
Corporate accounts of employees from 253 organizations (from a total of 402) were found in public dumps of compromised third-party services. This indicates that employees use their corporate emails to register on external services, for example, social media networks.
Corporate accounts leakage in the region (download)
The highest numbers
- More than 50% of those accounts are linked to banking organizations in Turkey;
- About 48% of such accounts linked to industrial companies are in Saudi Arabia.
If employees use compromised passwords for external services as well as for corporate resources, that information can be used to gain unauthorized access to those resources.
The scope of the Digital Footprint Intelligence Service is not restricted to public sources only – it also tracks the activity of cybercriminals on resources with limited access such as darknet forums and stores. The analyzed data includes demand and offers for credit cards and online banking accounts, insider hiring activities, the sale of compromised corporate accounts and client and employee databases, ongoing bounties for top managers, etc.
Statistics on activity in darknet forums and stores (download)
The majority of the topics and adverts discovered on darknet forums are related to bank card sales. We observed a fall in demand for bank cards in February 2020 after the festive season. The decrease was also caused by global lockdowns related to the COVID-19 pandemic.
Customer traffic in e-commerce has rocketed due to the coronavirus and it has naturally led to an increase in fraudulent activities such as phishing. Offers of online banking accounts and credit cards increased on darknet forums in May.
The dark web and the financial industry
Analysis of shadow activities related to the Middle East financial sector revealed that bank cards of four out of 15 countries were found on sale in darknet stores.
Bank card dumps and numbers (with/without CVV) are in high demand among criminals. Information of this kind can be used both for stealing money, for example, by making purchases in online shops and for money laundering.
Share of bank cards in darknet stores by country (download)
By Q3 2020, more than 78,000 credit card numbers and corresponding CVV/CVV2s of Middle East banks were found in darknet stores.
Distribution of cards by type (download)
Sales of payment cards with CVVs increased in July and August due to the opening of national borders after COVID-19 lockdowns were eased.
Distribution of banking cards sold by month (download)
如有侵权请联系:admin#unsafe.sh