
2021-01-04 21:05:40 Author: perception-point.io(查看原文) 阅读量:239 收藏
Email is the most common means of communication used in business today. It is also the number 1 delivery method of distribution for malware. Protecting it is an absolute necessity to continuing business operations. Despite this necessity, however, many end-users find their email protection software takes too long to scan for threats. So, why is speed so important?
Customers Expect Quick Responses
Speed is more vital than ever to the success of a business. If you’re not fast, you risk losing out to your competitors. But that’s not the only reason. Today, audiences expect it. Since more people began working from home, workers are sending more emails, per the National Bureau of Economic Research. This means your email best practices are more important than ever. Research shows a positive correlation between faster response times and higher customer satisfaction. According to Forrester Research, 77% of customers say that valuing their time is the most important thing a company can do to provide them with good online customer service.
And, more than 90% of consumers expect a one-hour email response time from companies. And they expect 15 minutes for “world-class service” according to customer service expert Jeff Toister. (Remember these figures – they are crucial for later).
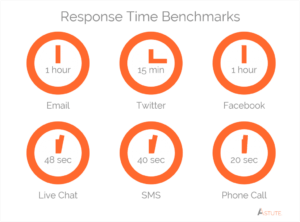
Proof: Companies are spending resources on analyzing reply rates.
The rate of response is so important, that many are investing money in improving their communication response times. One of these tools is SuperOffice.
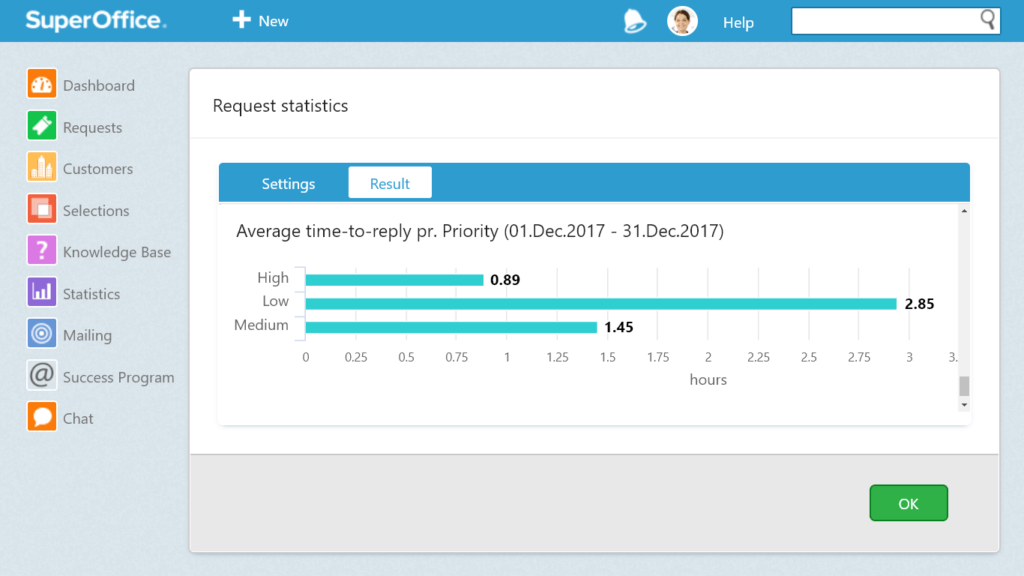
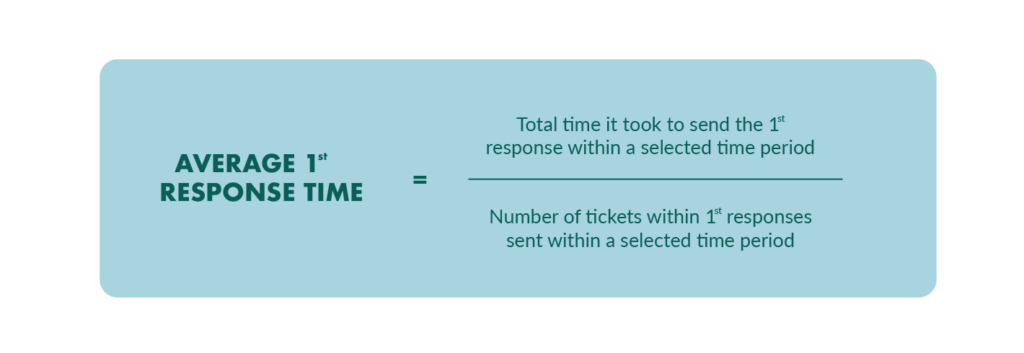
It is an entire CRM system, but one of the features they are popular for is their response time calculator. The company calculates the response rate by the following equation.
Perception Point Hack
If you don’t want to pay for this service, you can do it yourself. For example, imagine you send 3 customer service emails per day. The first email takes 2 hours, the second takes 4 hours, and the third takes 3 hours. Collectively, it takes you 9 hours to respond to all 3 emails. Now, divide 9 hours by the 3 emails you sent and you end up with an average response time of 3 hours.
Cybersecurity’s Role in Response Times
Unfortunately, many people today find their cybersecurity email scanning tool to take too long. The delay in communications is an average of up to 20 minutes. So, by the time the user receives an email, they’ve only got 40 minutes left to prepare, proof and send a response to make it under the recommended one hour. And if you’re aspiring to be a world-class responder – well, that’s a shame. There’s no way you could respond within this time frame at all For many people, this delay is directly affecting their bottom line. Just take a look at some of the comments on Microsoft’s help forum to understand the frustration from some end users.
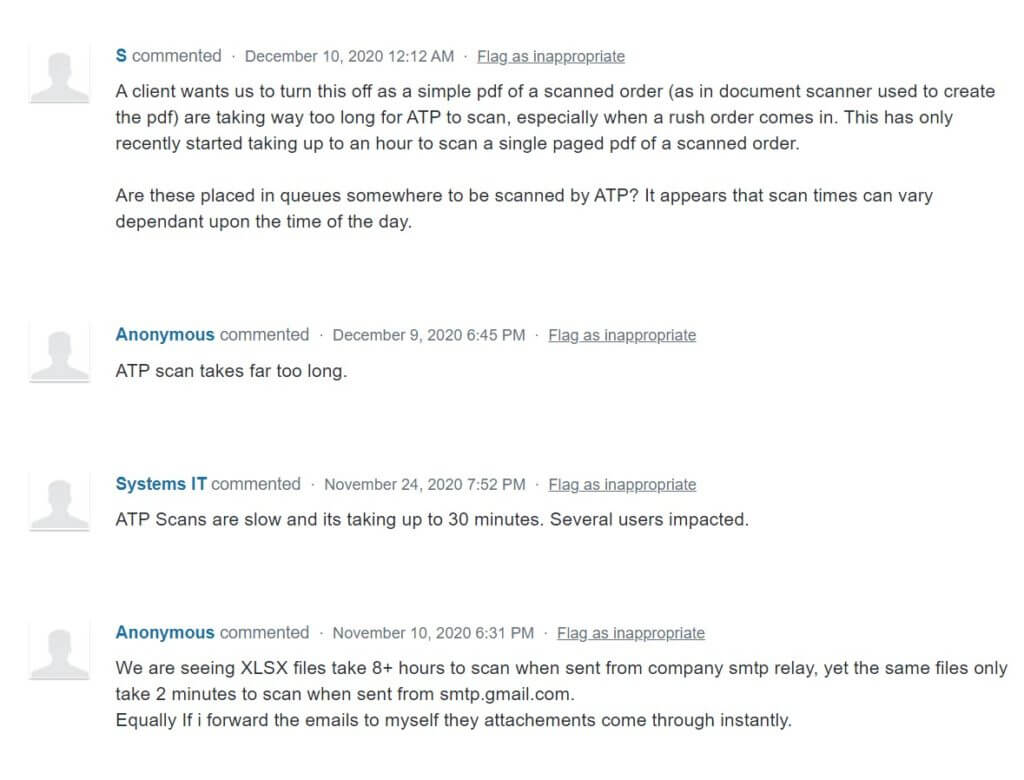
Because of the importance of quick content flow as outlined above, many CISOs are moving their security solutions to detection mode, which is the releasing and scanning of the data happening in parallel. Unfortunately, many are finding they made the wrong decision after realizing how susceptible they have been to threats without content sharing security prevention measures. This puts companies in an awkward position—with many thinking they need to sacrifice safety for speed.
Balancing Safety with Speed
Some CISOs compromise between user experience and safety by scanning only a portion of the emails coming in. This may sound pretty good till one unscanned email makes it into your system. The cost of that one missed compromised email is extremely high.
Canadian lender Desjardins Group recently revealed it had spent C$70 million ($53 million) in the wake of a breach earlier in the year that exposed personal information of 2.9 million members. Manufacturer Norsk Hydro said the final bill for its crippling cyberattack could be as high as $75 million. British Airways and Marriott have had to add $100 million each onto the final cost of their incidents after falling foul of GDPR.
Use Case
Although there are many examples of problems associated with slow emails, we’ve decided to highlight the one that most people have experienced.
You’re on the phone with an important client who has requested a certain document that you need to email. Now you need to wait a good 20 minutes in the meeting before getting to that one document. It’s easy to see why this is unproductive.
How to Stay Secure While Also Being Fast
Remember, not all prevention tools are equal. Our technology combines static, dynamic and anti-evasion techniques to deliver ultra-fast prevention. This means a delay of up to only 30 seconds to the end user. Now it’s a seconds game. Not a minutes one, and this means a world of difference. Take a look at the stats below. The median scan time with us is only 7 seconds with an average of 14.2 seconds. This means that 75 percent of all emails get delivered within 15 seconds. With us, there’s no need to sacrifice user experience for safety.
How We Do It: Protection vs. Detection
Rather than just detecting malware, our system works at the exploit stage. If a vulnerability is unknown, it simply doesn’t matter—exploitation is a deterministic act; if there is an exploit there is an attack. By targeting attacks at this stage, it’s impossible for zero-days to make it past the HAP. (Learn more about the HAP below).
Multi-Layered Approach
Our multi-layered platform provides unprecedented detection and prevention of APTs, phishing, malware, spam, BEC attacks, and more, delivered with the speed, scale, and flexibility of the cloud. One simple solution that scans all content within 30 seconds.
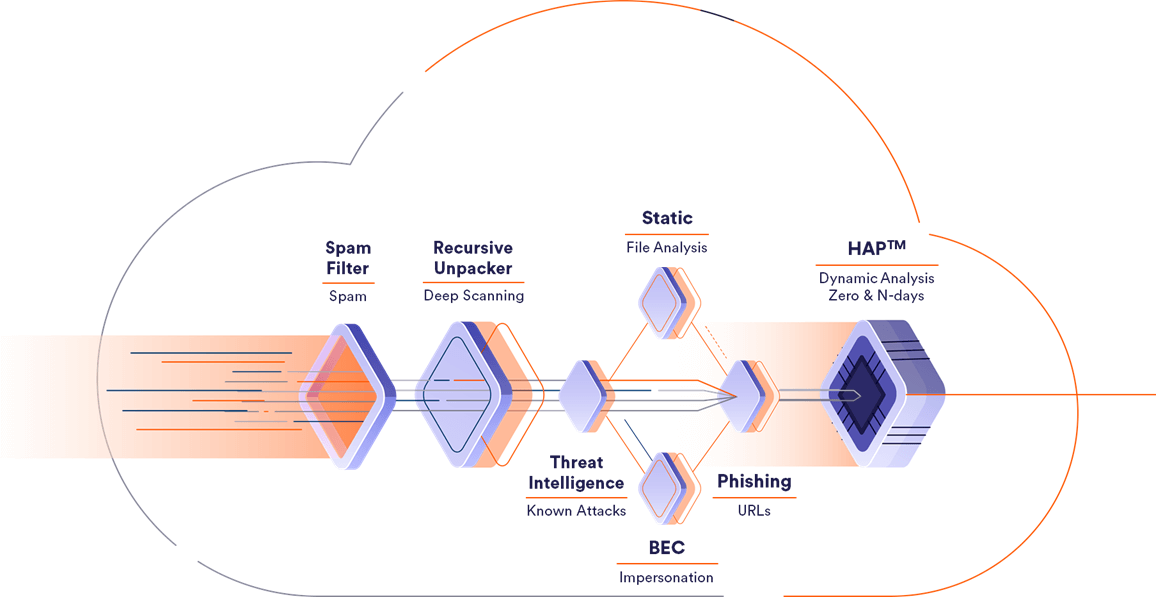
1. Anti-Spam
Receives the email and applies reputation and anti-spam filters to quickly flag an email as malicious.
2. Recursive Unpacker
Unpacks the content into smaller units (files and URLs) in a recursive manner to identify hidden malicious attacks. All of the extracted hidden components go separately through to the next security layers.
3. Threat Intelligence
Combines multiple threat intelligence sources with a unique internally developed engine that scans URLs and files in the wild to warn about potential or current attacks.
4. Static Signatures
Combines best-in-class signature based anti-virus engines to identify malicious attacks. In addition, we’ve developed a tool that acts to identify highly complicated signatures.
5. BEC
Prevention of payload-less attacks including spoofing, look-alike domain, and display name deception.
6. Phishing Engines
Best-in-class URL reputation engines coupled with Perception Point’s in-house built image-recognition analysis engine identify impersonation techniques and phishing attacks.
7. Hardware-Assisted Platform (HAP™)
Unique CPU-level technology acts earlier in the kill chain than any other solution. Blocking attacks at the exploit phase – pre-malware release – for true APT prevention.
如有侵权请联系:admin#unsafe.sh