Today we’re going to solve another boot2root challenge called “Conceal“. It’s available at HackTheBox for penetration testing practice. This laboratory is of a difficult level, but with adequate basic knowledge to break the laboratories and if we pay attention to all the details we find during the examination it will not be complicated. The credit for making this lab goes to bashlogic. Let’s get started and learn how to break it down successfully.
Level: Hard
Since these labs are available on the HackTheBox website.
Penetration Testing Methodology
Reconnaissance
- Nmap
Enumeration
- Snmpwalk
- Ike-scan
- Strongswan
- Dirsearch
Exploiting
- Abuse of write permission in FTP service
Privilege Escalation
- Abuse of permission in SeImpersonatePrivilege in the system
- Capture the flag
Walkthrough
Reconnaissance
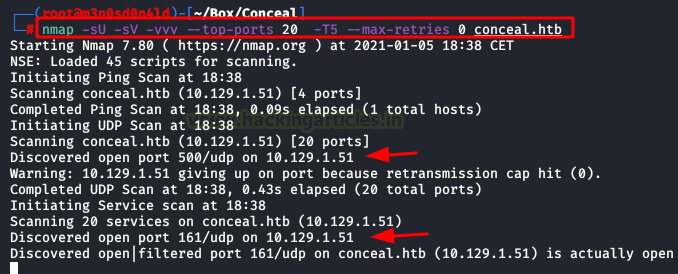
This time, the recognition be hard with nmap tool. We will use the next command to obtain the result of the UDP ports.
nmap -sU -sV -vvv --top-ports 20 -T5 --max-retries 0 conceal.htb |

Enumeration
We will enumerate the UPD ports 161 and 500. We will use the snmpwalk tool with the public channel. We found a hashed password for IKE VPN, this is nice, we have open port 500 UPD.

We will use the next command for enumerating users.

We will use this command for enumerating open ports in the localhost.

We will use the ike-scan tool to obtaining information on the configuration software IKE VPN.

We will back with password hashed and we use the website hashes.com for cracking.

Now, we install strongswan software and we edit the “/etc/ipsec.conf” with this configuration:

Also, we configure the file “/etc/ipsec.secrets” with our IP Address and password.

Now, we run strongswan with our configuration.

We use nmap tool and now yes enumerate ports. (yes, see view how status “filtered“)

I have a script for portscan in bash scripting, I use for testing open ports.

We also enumerate Microsoft IIS on the server.

Exploiting
We ignore SMB service and we use the FTP service, we can connect with user “anonymous” and we have the permission of write.
We upload the file “cmd.aspx“, this is a webshell for executing commands.

Now have problem… Where is this file? xD We use dirsearch tool for enumerating directories and we a directory with the name “upload“.

Wow! We found file!

WTF?? It doesn’t work! We tested with other files also but doesn’t work.

We searching others webshell in ASP language and we found this webshell.

Okey! Now we execute a reverse shell in Powershell of Nishang, we will put a python server with we reverse shell, A netcat in listen and we execute this command for webshell.

Yeah! We are in!

We read the file proof.txt

Privilege Escalation (Administrator)
We execute the command “whoami /all” and we found permission with privilege “SeImpersonatePrivilege“.
This privilege is possible exploiting with “Juicy Potato“.

We execute command “systeminfo” and we enumerate Windows version for use CLSID correct. (Here the list CLSID)

We found a problem, It does not work correctly with nishang reverse shell. We use netcat in another terminal.

We use the binary “JuicyPotato.exe” executed with other cmd.exe in the port 5555.

We have a netcat in listen and we received reverse shell as administrator (nt authority\sytem). We can read the root flag.

Author: David Utón is Penetration Tester and security auditor for Web applications, perimeter networks, internal and industrial corporate infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.