2021-01-07 16:09:43 Author: blog.elcomsoft.com(查看原文) 阅读量:251 收藏
Shame on us, we somehow missed the whole issue about Apple dropping plan for encrypting backups after FBI complained, even mentioned in The Cybersecurity Stories We Were Jealous of in 2020 (and many reprints). In the meantime, the article is full of rumors, guesses, and unverified and technically dubious information. “Fake news”, so to say. Is there truth to the rumors, and what does Apple do and does not do when it comes to encrypting your personal information?
iCloud Security
We know a lot about iCloud encryption, as we were the first third party who independently reverse engineered it over 8 years ago. I personally made several dozen presentations on iCloud security in various conferences all over the world. iCloud is a very complex ‘ecosystem’, and let me outline the main points on how it handles and protects the data.
The data stored in iCloud includes:
- Device backups (iOS, iPadOS)
- Data synced across devices (such as contacts, notes, etc.)
- iCloud Drive (both the regular storage and third-party app data)
- Some extras (such as logs, purchase history, etc.)
Some information on the encryption is provided in iCloud security overview in Apple Knowledge Base, and we have a deeper explanation in our own article iCloud Backups, Synced Data and End-to-End Encryption. In a nutshell:
- All data is stored on servers that are hosted by other companies (but not by Apple)
- All data is encrypted
- The encryption keys are stored at Apple’ own servers
- Some data is so-called “end-to-end” encrypted
As we explained before, there is no real end-to-end encryption in iCloud (apart from some data that is being synced directly between devices, such as certain location data and Screen Time stats). What Apple says (“Your data is protected with a key derived from information unique to your device, combined with your device passcode, which only you know. No one else can access or read this data”) is not the whole truth. Having only the iCloud credentials (incl. the second factor) and the passcode of one of the trusted devices (just the passcode, not the device itself and definitely not anything “unique to your device“), a third party can access this data – using Elcomsoft Phone Breaker.
iCloud Backups
In Apple ecosystem, the backups do not have any kind of additional protection or encryption with the user’s password. While still protected with storage encryption (with encryption keys kept on Apple servers), there is nothing that could check as “end-to-end encrypted”. Despite that, iCloud backups are very difficult to obtain if you are not restoring a genuine Apple device running a compatible version of iOS. There are generally two ways for accessing iCloud backups:
- Legal request: obtained directly from Apple, through the company’s Law Enforcement Support Program
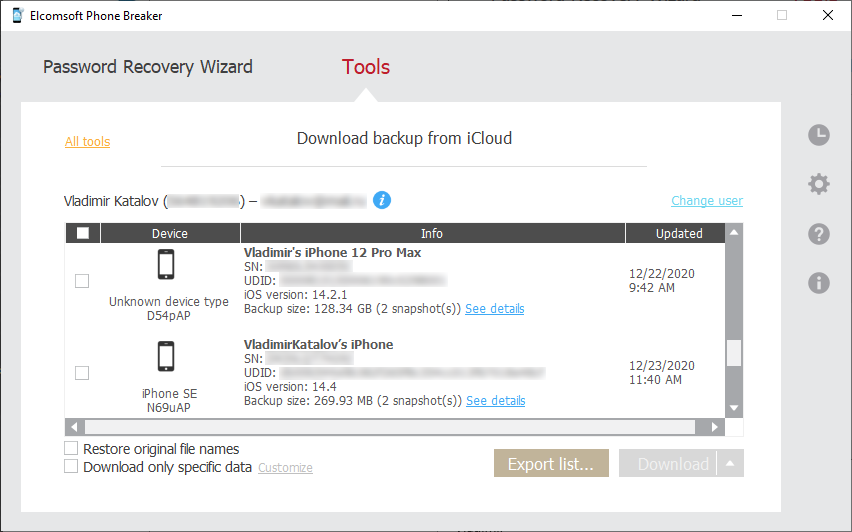
- Download with our software
Government requests are served according to Apple’s legal process guidelines. We covered this topic before:
In fact, Apple returns encrypted data (from third-party servers) accompanied with the encryption keys from their own servers. This data is very “raw”; it is not structured as standard iTunes-style backups (unlike with our software; which, by the way, delivers more iCloud-synced data than Apple returns when serving LEA requests). If you’re using our software to download backups, you will need the following:
- Apple ID
- Password to that Apple ID
- Second authentication factor (trusted device or SIM card)
There are two major problems with iCloud backups (whatever method is used). First, with every major iOS version, Apple reduces the amount of data that goes into iCloud backups as opposed to being synchronized across devices via a different mechanism. As of iOS 14 (14.4 beta at the time of this writing), the following data is (or may be) missing in cloud backups:
- Health records
- Call logs
- Safari browsing history
- Media files (pictures and videos), if synced
- Messages (iMessage and SMS), if synced
- Keychain
The keychain is something very special. It is included in iCloud backups, but with an extra protection layer. The records are encrypted with a hardware-specific key, so that the keychain can only be restored onto the same physical device it was backed up from. If you restore an iCloud backup to any other device, everything but keychain data is restored. You can use iCloud keychain, but this is a different story.
The Article
Let’s go back to the article; I want to quote and comment a few lines.
…six sources familiar with the matter told Reuters
As many as six sources, really? Good luck getting any information on Apple internal plans at all, even from a single source. Most Apple employees and LEA officials are under strict NDA. But anyway, let’s take a note of this number: 6.
The tech giant’s reversal, about two years ago, has not previously been reported. It shows how much Apple has been willing to help U.S. law enforcement and intelligence agencies.
I will not comment on the “has not been previously reported” (assuming that all six sources decided to share confidential information with a Reuters reporter at the same time), but do you understand the second part? I do not. “Apple has been willing”, but then changed its mind (and now does not), or what? Apple does help Law Enforcement, and it does comply with the laws. And not just in the U.S. but worldwide.
U.S. President Donald Trump piled on, accusing Apple on Twitter of refusing to unlock phones used by “killers, drug dealers and other violent criminal elements.”
So what? No relationship to iCloud [backups].
More than two years ago, Apple told the FBI that it planned to offer users end-to-end encryption when storing their phone data on iCloud, according to one current and three former FBI officials and one current and one former Apple employee.
Now we have not six but five “insiders”: four from the FBI (three of them are ex), and one from Apple (also an ex). Not only the numbers do not much, but the entire statement is hard to believe.
Under that plan, primarily designed to thwart hackers, Apple would no longer have a key to unlock the encrypted data, meaning it would not be able to turn material over to authorities in a readable form even under court order.
First, nobody knows the actual reason behind this plan, if it ever existed. Second, Apple never provided iCloud backups “in a readable form” (it is really troublesome to decrypt and analyze iCloud backup data returned by Apple).
Reuters could not determine why exactly Apple dropped the plan.
So Reuters know (told by 5 or 6 sources, or just guessing?) that the plan was to “thwart hackers”, but have no idea why it was dropped? Let’s keep reading.
Two of the former FBI officials, who were not present in talks with Apple, told Reuters it appeared that the FBI’s arguments that the backups provided vital evidence in thousands of cases had prevailed.
New numbers: two of the (former) three. And if they never talked to Apple, how do they know?
However, a former Apple employee said it was possible the encryption project was dropped for other reasons, such as concern that more customers would find themselves locked out of their data more often.
I think this is the actual reason. But I like the “it was possible”, so the former Apple employee was not sure either.
Once the decision was made, the 10 or so experts on the Apple encryption project – variously code-named Plesio and KeyDrop – were told to stop working on the effort, three people familiar with the matter told Reuters.
Okay, now we have ten more experts, and three more “people familiar with the matter”. I am totally confused with the numbers now.
But I am even more confused with Plesio and KeyDrop “projects”. What the hell is the “project” in terms of backup encryption? Was it to implement the same scheme as in the local, iTunes-style backups (that is indeed very strong)? And why two?
Apple’s decision not to proceed with end-to-end encryption of iCloud backups made the FBI’s job easier.
Instead of protecting all of iCloud with end-to-end encryption, Apple has shifted to focus on protecting some of the most sensitive user information, such as saved passwords and health data.
Passwords were always encrypted, from the very first version where iCloud backups were implemented (iOS 5 if I remember correctly). As for the Health data, it was not “end-to-end encrypted” in iOS 11, but only since iOS 12. To be honest, Health records rarely contain critical evidence; there are several significantly more critical categories. Also, if Apple still decided to protect some sensitive information, how does it make the FBI job easier?
But backed-up contact information and texts from iMessage, WhatsApp and other encrypted services remain available to Apple employees and authorities.
Not exactly. iMessage and text messages are not always included in iCloud backups. WhatsApp chats can be opted-out easily (by the user). And most other “encrypted services” (like Telegram and Signal) never store the chats in backups (even local ones), see Forensic guide to iMessage, WhatsApp, Telegram, Signal and Skype data acquisition.
Conclusion
Never blindly trust media reports. Do your own fact check, and exercise due diligence. If you want to read a serious report, I recommend Data Security on Mobile Devices: Current State of the Art, Open Problems, and Proposed Solutions – an excellent piece of work covering both physical devices and iCloud security; or Mass Extraction: The Widespread Power of U.S. Law Enforcement to Search Mobile Phones for less technical info. And you have saved the address of our blog, right?
REFERENCES:
![]()
Elcomsoft Phone Breaker
Gain full access to information stored in FileVault 2 containers, iOS, Apple iCloud, Windows Phone and BlackBerry 10 devices! Download device backups from Apple iCloud, Microsoft OneDrive and BlackBerry 10 servers. Use Apple ID and password or extract binary authentication tokens from computers, hard drives and forensic disk images to download iCloud data without a password. Decrypt iOS backups with GPU-accelerated password recovery.
如有侵权请联系:admin#unsafe.sh