Typically, There was no significant impact (in general the severity is low) for a Broken Cryptography flaw in the android application. Unless, if there is a strong dependency between the application workflow and cryptography functions.
In the recent private bugbounty program, I faced a challenge. In which the application request body was encrypted with some kind of cryptography mechanism. So I should have to find the encryption mechanism to further assess the application.
To understand the encryption logic, I have de-compiled the APK using Android reverse Engineering tools set and then I have analyzed the code for the encryption mechanism and sensitive key information. But I haven’t found any hard-coded secret in the reversed source code.
It’s time to Inspect the application heap memory
Heap Memory
The Heap is used for dynamic memory allocation. To provide a smooth user experience, Android sets a hard limit on the heap size for each running application. The heap size limit varies among devices and is based on how much RAM a device has. Heap memory is used to allocate objects. Whenever you create an object, it’s always created in the heap.
Why we need to analyze
Due to the short time of development, The developers only focus on the building feature, functionalities and UI components. But they may forget to Inspect app memory usage with Memory Profiler. Therefore we may get a chance to obtain these cryptography secrets keys on the memory Leakage.
How to analyze the android application memory leaks
Step: 1
First we have to recompile the target application with android:debuggable="true”. To rebuild the target application with debug flag I use the apk-mitm.
Uninstall the original app and Install the re-compiled version of the target app and navigate to all feature of the application and use as a normal application for a few minutes.
Step: 2
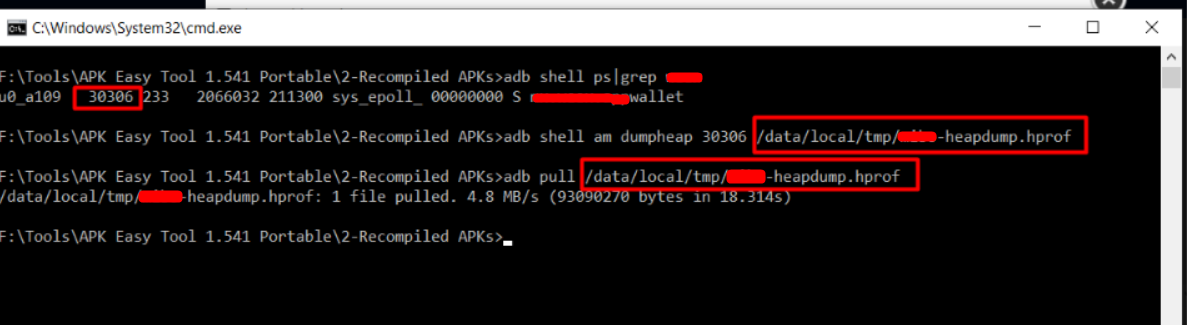
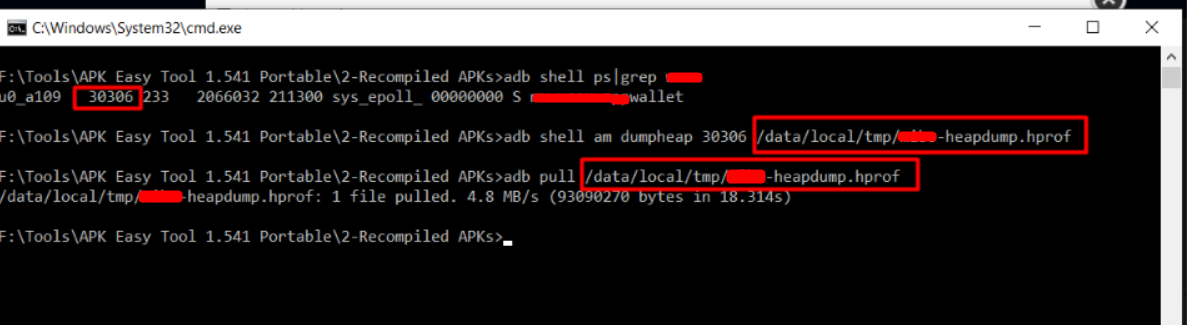
Now get the application memory profile using the adb. To do this use the below commands.
adb shell am dumpheap <PID of target app> /path/to/store/heap-dump.hprof#get the heapdump file to PC
adb pull /path/to/the/hprof .
Step: 3
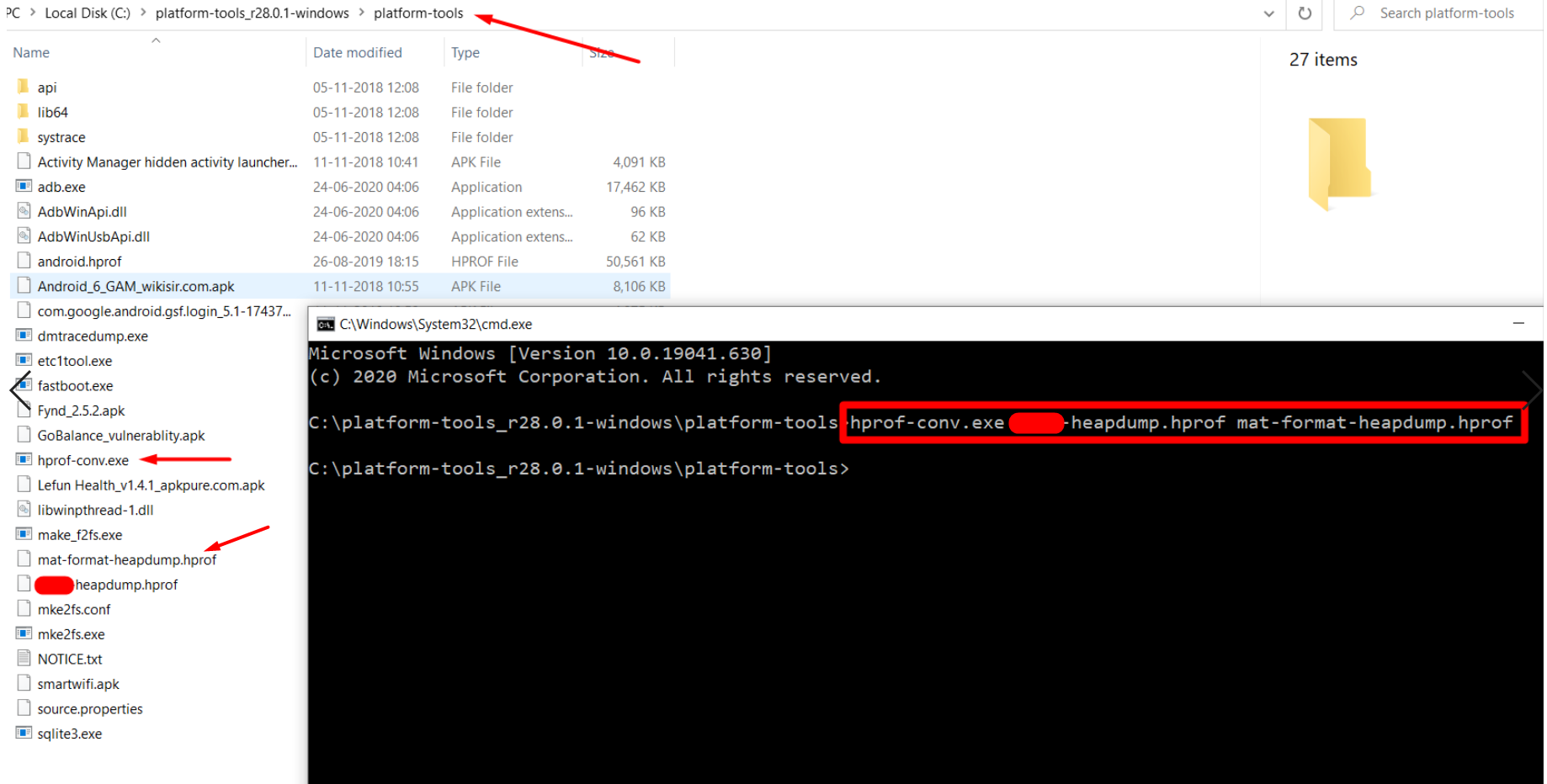
To analyse the hprof file in MAT Analyzer tool convert the hprof file in MAT support format. For that need to use the hprof-conv tool that’s located in [Android-SDK]\platform-tools.
cd "C:\android-sdk\platform-tools"hprof-conv.exe "heapdump.hprof" "MAT-format-heapdump.hprof"
Step: 4
Now we have MAT support hprof file of the target application. Let’s analyze the file for the sensitive strings.
Download the Eclipse MAT using this link
Open the converted hprof file using MAT analyzer. From de-compiled source code, I have observed that the AES secret is starting with “TbTS”. Which was got to know by analyzing the bytes array function. So I have searched this string pattern with OQL (Object Query Language) Feature in the Eclipse MAT.
SELECT s.count, toString(s) FROM java.lang.String s WHERE (toString(s) LIKE "TbTS.*")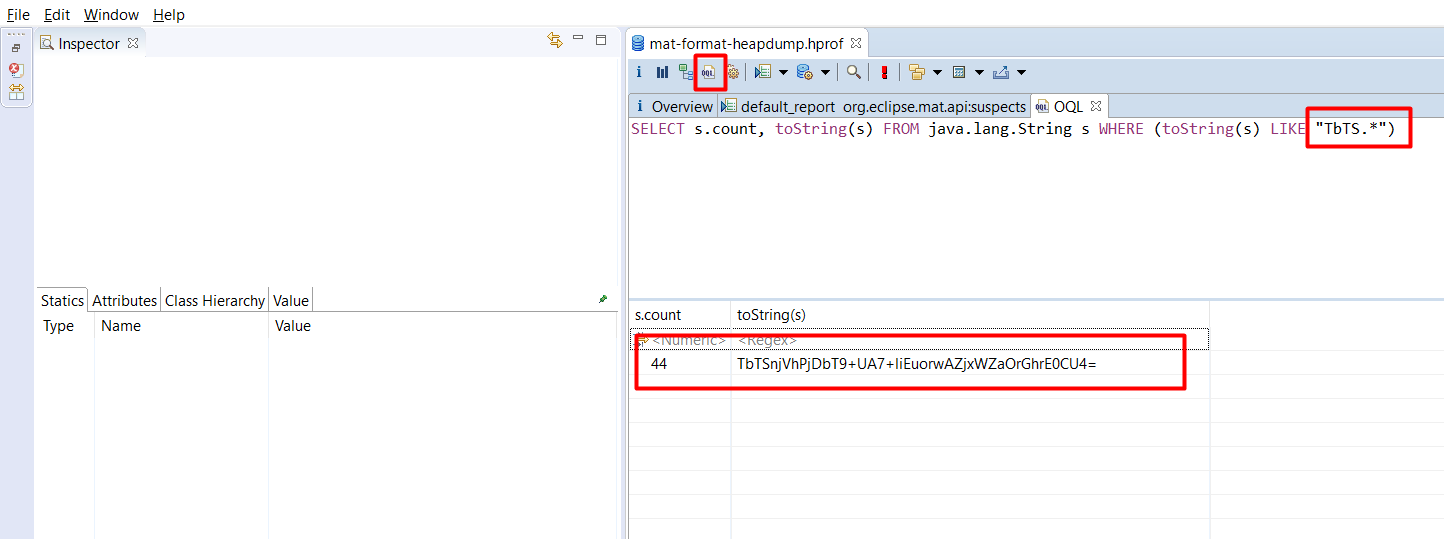
Finally, I got the AES secret key, but I need IV random key to decrypt or encrypt the data.
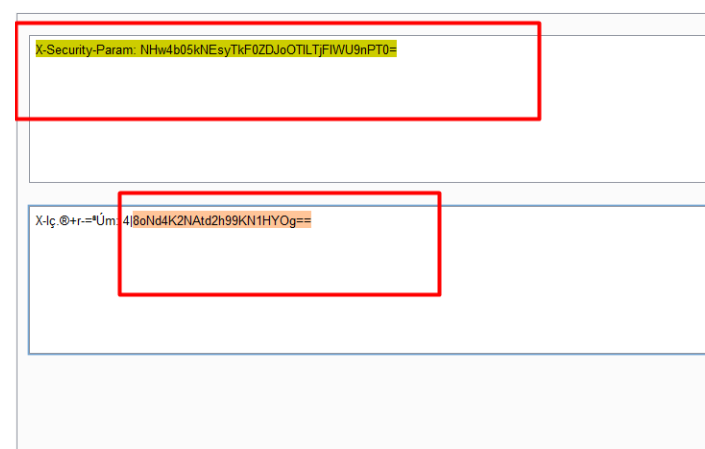
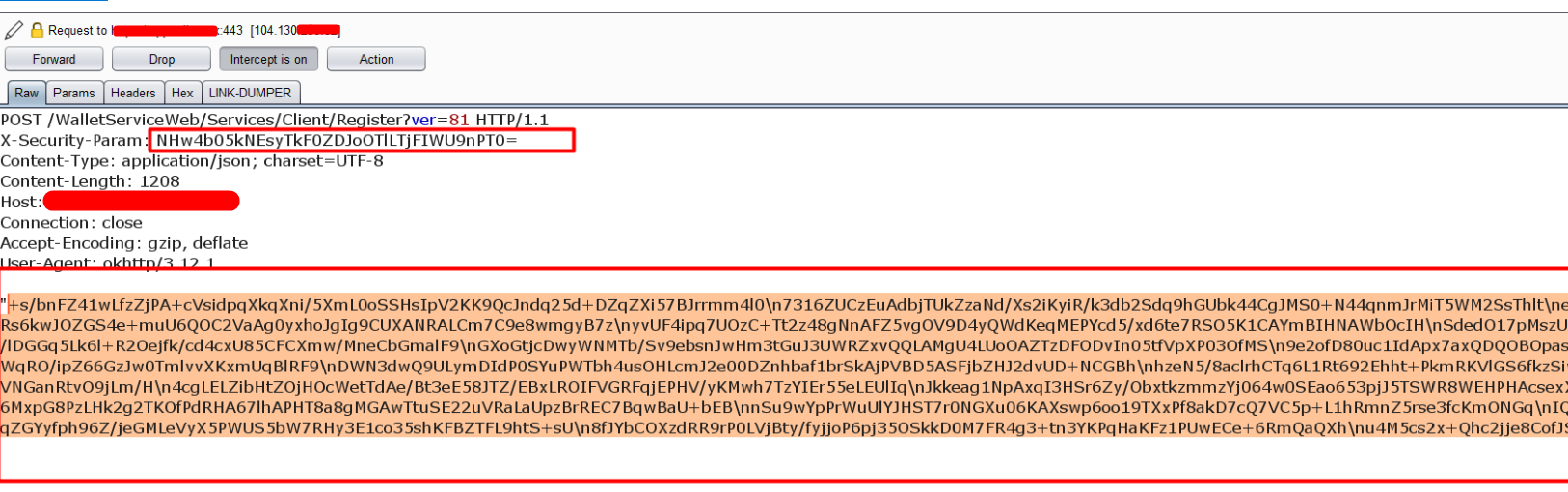
After some analysis, my eyes are focus on the ‘X-Security-Param’ header. When I decode this header value I got a value and I strongly believed this is IV key of the digest.
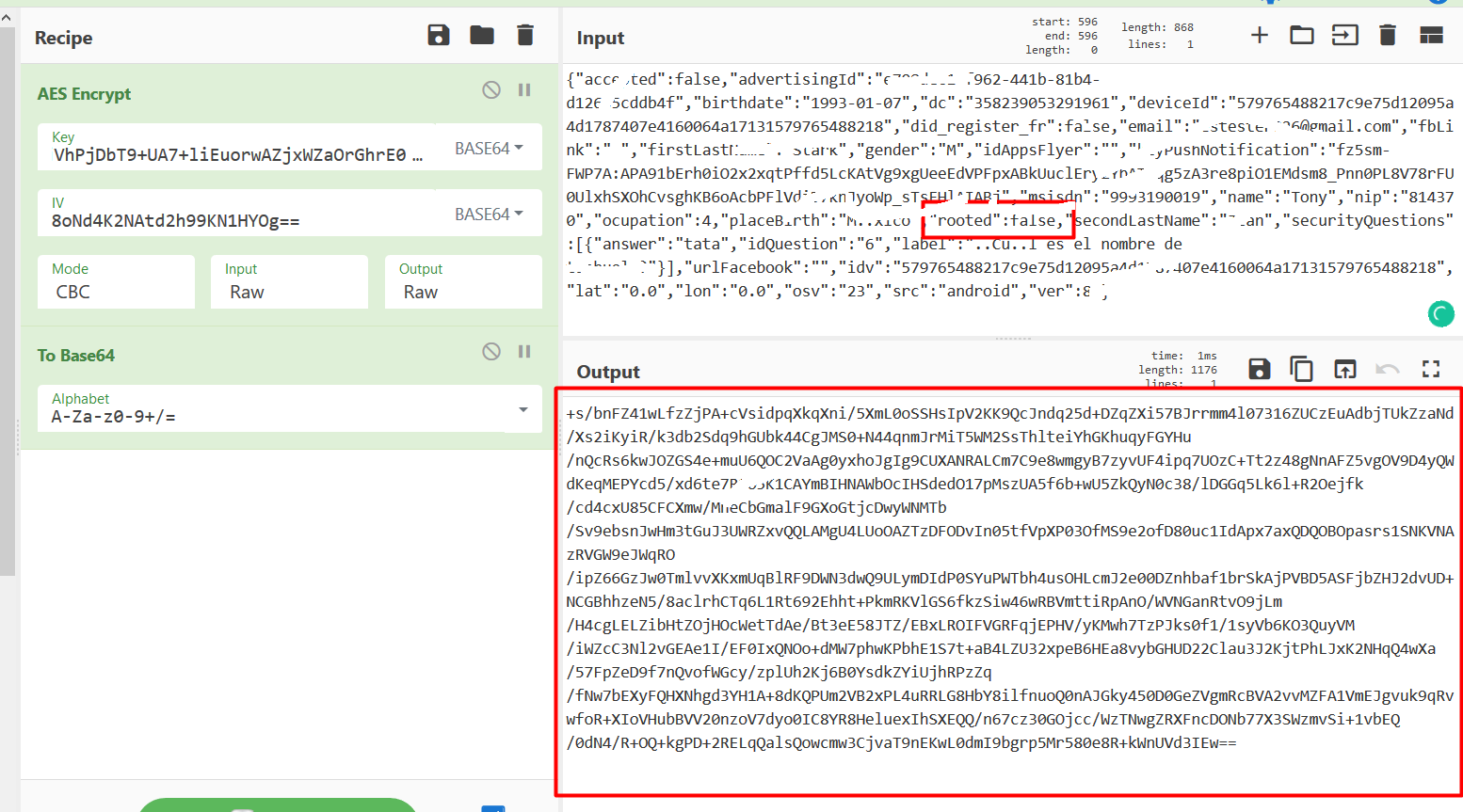
Using the Identified values Finally, I decrypted and modified the encrypted request body.
Thanks for spending your time to read this blog. If you want to learn the android hacking please do follow me and stay tune for interesting hacking techniques and view my profile to read interesting BugBounty write-ups.