2021-02-02 15:55:13 Author: blog.elcomsoft.com(查看原文) 阅读量:243 收藏
Passcode unlock and true physical acquisition are now available for iPhone 4, 5, and 5c devices – with caveats. Learn about the benefits and limitations of passcode unlocks and true physical imaging of Apple’s legacy devices. Looking for a step by step walkthrough? Check out our imaging guide!
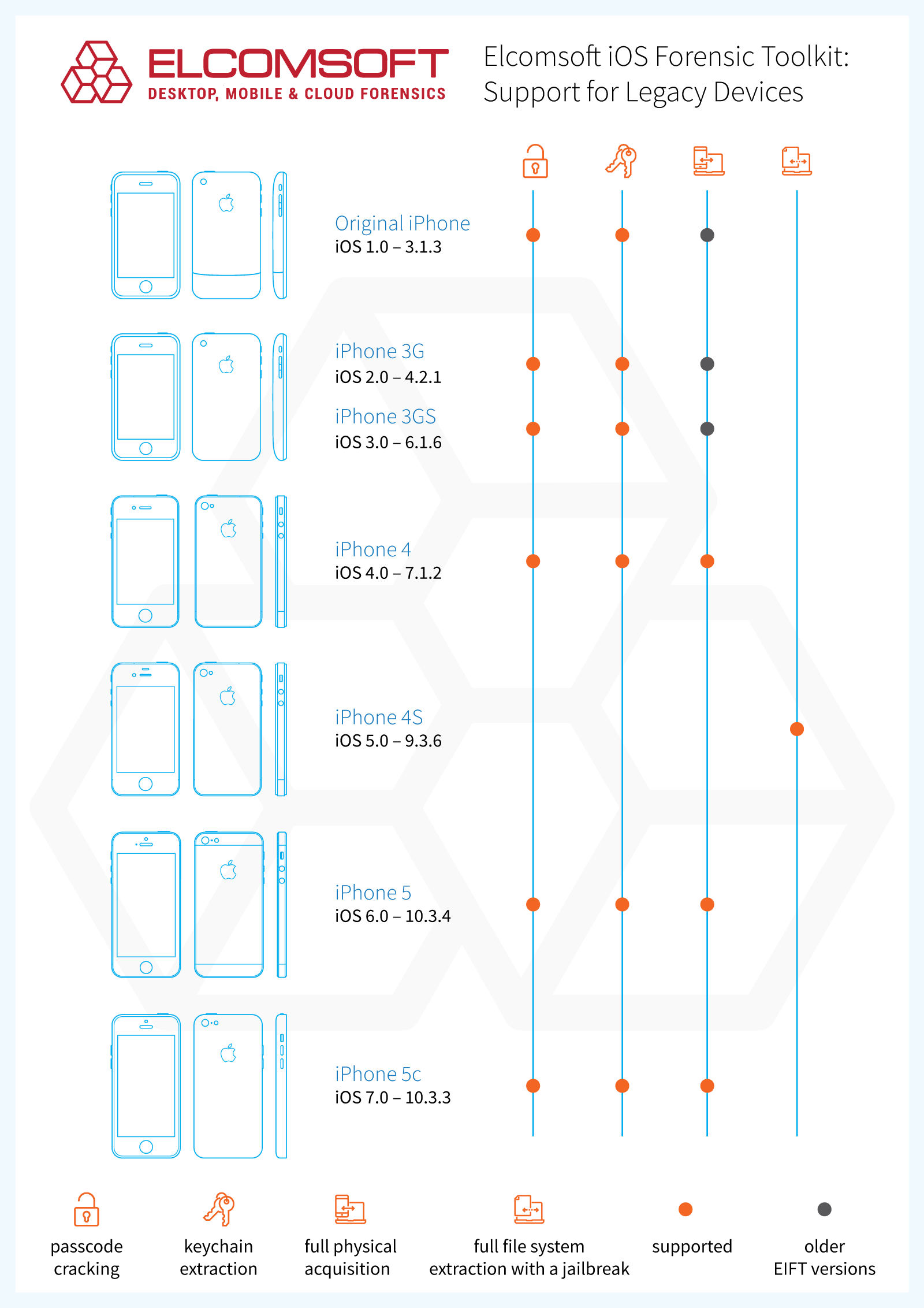
Unlocking the iPhone 4, 5 and iPhone 5c devices
Last year, we added passcode unlock for the iPhone 5 and 5c. Today, the unlocking support is extended to cover the iPhone 4. The Toolkit can try all possible 4-digit combinations in about 12 minutes (iPhone 5 and 5c), while 6-digit PIN codes take up to a day to complete. The iPhone 4 is about half the speed of the newer models, so the maximum recovery times will be double that.
We’ve developed a smart attack to target these longer passcodes, trying the list of the most common passwords first in the 5-minute preliminary attack, followed by another attack trying all 6-digit combinations matching potential dates of birth during the next 1.5 hours. Only if both these attacks fail, the tool starts the full brute-force attack, which takes up to 21 hours to complete. Once again, double the numbers for the iPhone 4. Importantly, the method works even for disabled devices (after ten manual attempts to enter the passcode had failed).
Full physical acquisition (passcode recovery, keychain extraction, user partition imaging and decryption) is available for the following device models:
- iPhone 4 (iOS 4.0 – iOS 7.1.2)
- iPhone3,1 (GSM): A1332
- iPhone3,2 (GSM Rev. A): A1332
- iPhone3,3 (CDMA): A1349
- iPhone 5 (iOS 6.0 – iOS 10.3.4)
- iPhone5,1 (GSM): A1428
- iPhone5,2 (GSM+CDMA): A1429, A1442
- iPhone 5c: (iOS 7.0 – iOS 10.3.3)
- iPhone5,3 (GSM): A1456, A1532
- iPhone5,4 (Global): A1507, A1516, A1526, A1529
Note: iPhone 4s (iPhone4,1: A1387, A1431) is not supported.
The return of true physical acquisition
True physical acquisition is back, albeit on a limited number of models. The “true” physical means imaging and decrypting the disk as opposed to imaging the file system, which is the only option for the newer, 64-bit models. In 64-bit iPhones, the encryption keys are protected with Secure Enclave, a combination of hardware and software that makes disk imaging useless due to encryption. The older models lack Secure Enclave, allowing us to extract the encryption keys and to use them when imaging the disk. This in turn enables forensically sound acquisition with zero footprint.
Currently supporting the iPhone 4, 5 and 5c (sorry, no iPhone 4s this time), the Toolkit can create and decrypt a bit-precise image of supported iPhone models. Moreover, if the iPhone is running iOS 4 through 7, the imaging works without the need to break the passcode. For newer versions of iOS you’ll have to break the passcode first, and image after. Needless to say that keychain decryption is also supported on these legacy models.
The imaging runs at ~5.8 MB/s on the iPhone 4, while the newer iPhone 5/5c is imaged faster at approximately ~15.6 MB/s.
You will get a DMG image of the data partition as a result of the extraction (no system partition included). If you are a Mac user, you can simply mount the DMG and analyze the file system. Windows users will need third-party software. Of course, you are free to use any forensic package you choose – DMG is a standard format supported by most forensic tools.
If the iPhone you are investigating runs a really old version of iOS (in the iOS 4 through iOS 7 range), you can extract most information from the iPhone even without breaking the passcode. Notable exceptions are many keychain records, downloaded email messages, and a few other bits and pieces. Starting with iOS 8, Apple began encrypting nearly everything in the data partition, so you will need the passcode – or use the very limited BFU extraction.
Continue reading
For a step by step walkthrough, check out the complete imaging guide for iPhone 4, iPhone 5 and iPhone 5c devices.
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh