
2021-02-07 22:23:35 Author: perception-point.io(查看原文) 阅读量:203 收藏
We are seeing a dramatic increase in the number of phishing attempts using real page builder web applications such as Weebly. These drag-and-drop, front-end editor tools make it easy to create legitimate-looking log-in pages for free.

Example
The attackers leveraged compromised, legitimate email accounts to send fake document-delivery notifications.
1. The attack starts with a hook to convince email recipients that he or she received a document. The email impersonated eFax, an internet fax service making it easy to receive faxes via email or online.
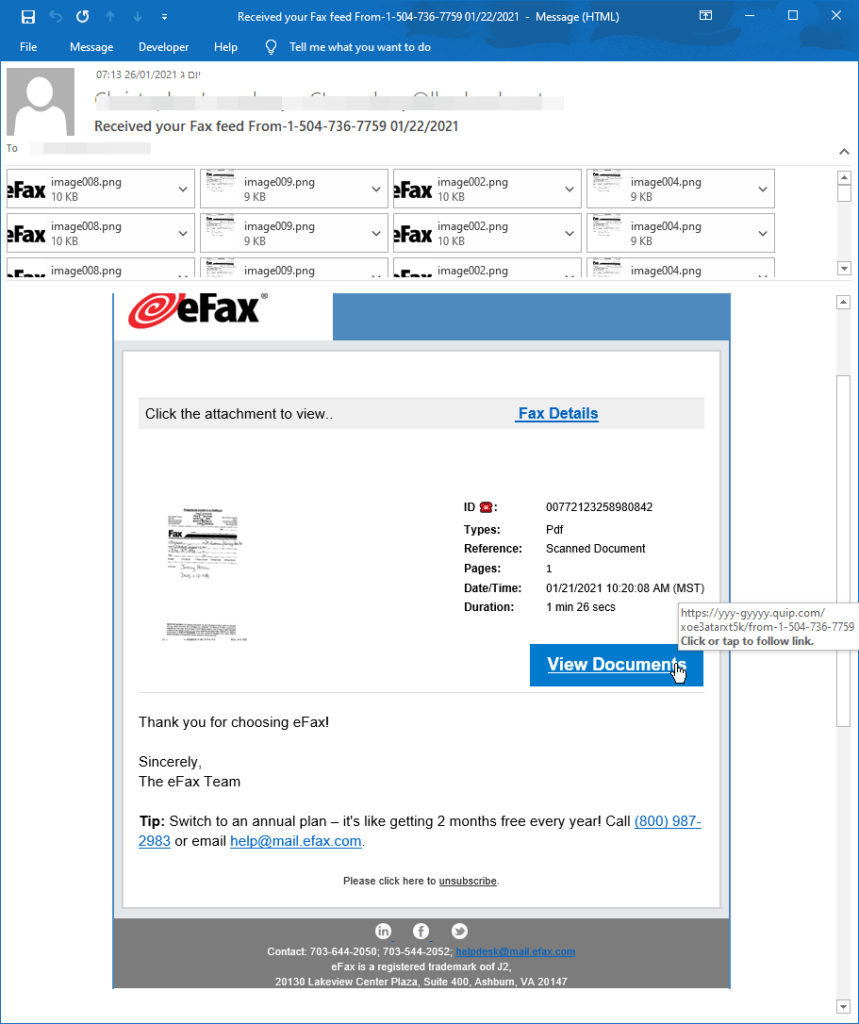
2. As you can see, the email uses the legitimate eFax branding. It includes a button with a link directing recipients to, “View Document.” And, it includes a small picture that is a sample image of a fax the recipient apparently received.
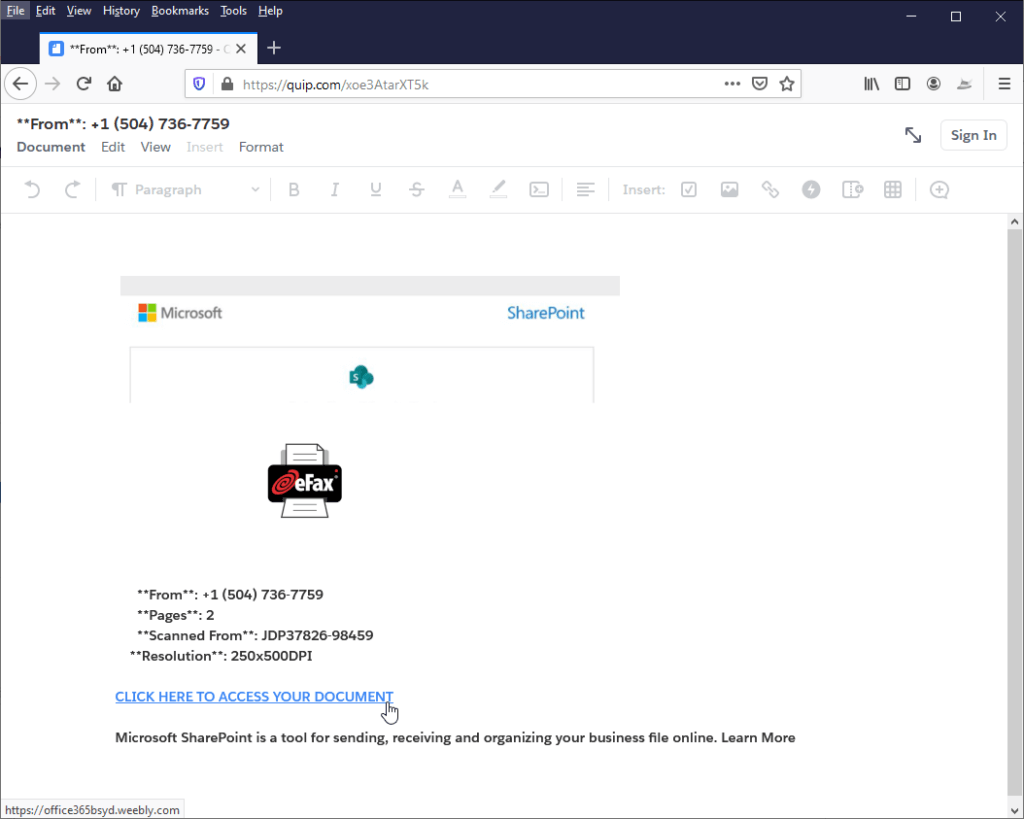
3. The embedded URL redirects the user to a fake Microsoft Office 365 log-in page. The landing page again includes a sample fax image, Caller ID and reference number, and again tells recipients to “Click Here to Access Your Account.”
4. When the person clicks the button, he or she is then taken to the final credential-stealing part of the campaign (see below).
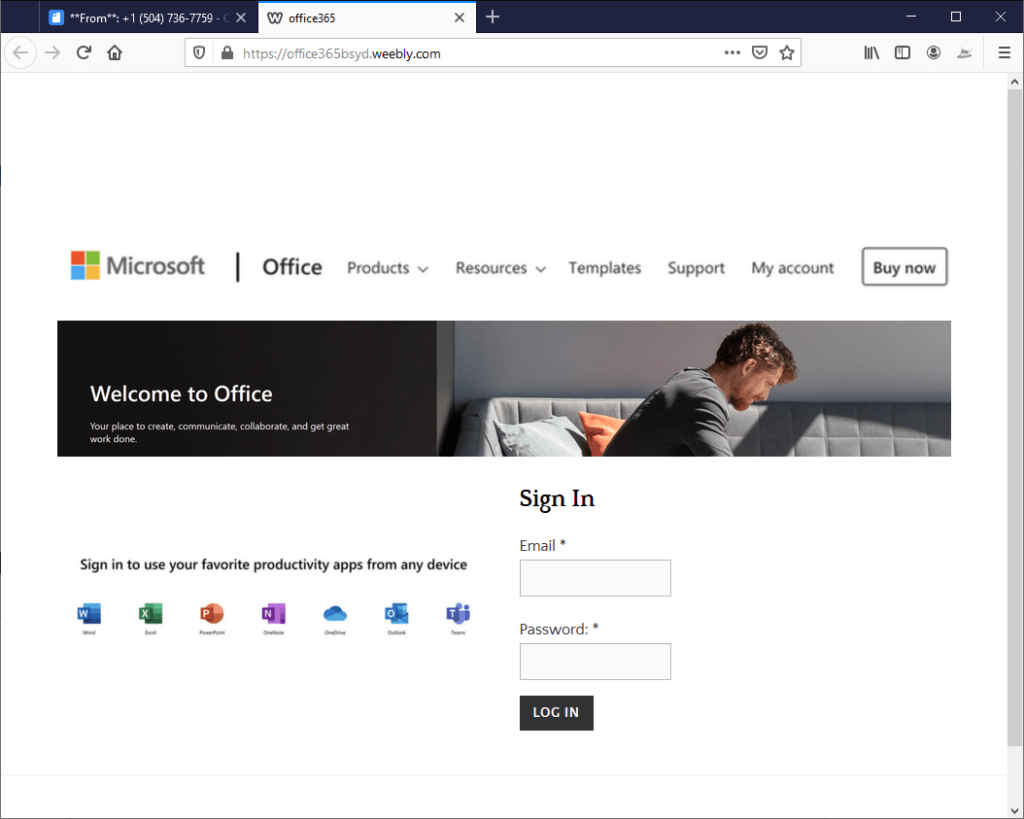
The page looks great, right? That’s because it literally can be the exact same technology used to create the original site. Free packages from some of the top page and embeddable form builders allow attackers to create single-page logins.
How They Do it for Free
The rise of SaaS tools has made it easy for anyone to create and publish anything online. This is great for many people, since it requires only little knowledge of HTML. While this is a huge benefit for most people, there are those bad actors who exploit the services, unfortunately.
Website Builders
These services offer convenience in creating professional-looking phishing pages, some of which can look like popular websites. The following are some of the most popular website building tools with a free plan:
- Wix
- Weebly
- SITE123
- Strikingly
- WordPress
- Jimdo
- SimpleSite
- Webnode
- IM Creator
- Mozello
- Ucraft
- Webstarts
- GoDaddy
- Webflow
Form Builders
The abuse of forms services like Microsoft Forms to create simple and fake phishing pages and sometimes even fake login pages. The following are some of the most popular website building tools with a free plan:
- Hubspot Free Online Form Builder
- Gravity Forms
- Typeform
- Wufoo
- Microsoft Forms
- Formstack
- Paperform
- Formsite
- Cognito forms
- Leadformly
- 123 Form Builder
- Google Forms
- Microsoft Forms
How We Detect Phishing Scams
Recursive Unpacker
We unpack everything individually. Once the email’s unpacked, we scan each file, URL text or even smaller objects within the content separately.
Then, unique algorithms run the same files and URLs in multiple versions and patterns. This makes sure the attack is not leveraging unseen evasion techniques. See more here.
Image Recognition
Our image–recognition engine scans URLs to prevent zero-day attacks and known phishing attempts. See more here.
We’ve observed and prevented attackers targeting various services. These range from generic login portals to SharePoint, Adobe Document Cloud, OneDrive, Office 365 and more. Interested in seeing them? Make sure to check out the ones here.
如有侵权请联系:admin#unsafe.sh