2021-02-10 11:31:56 Author: medium.com(查看原文) 阅读量:226 收藏
This writeup describes a bug/security issue on Facebook where an Admin of Facebook page creates an event on his page but the Admin(Host of the event) unable to remove a malicious user who have privilege to perform all co-host actions edit/delete on that event. However, it was resolved and being published under responsible disclosure policy.
Hi All,
I am Kunjan Nayak from Nepal and I am new in the Bug Bounty field. Today I am going to describe my 14th i.e. 2nd valid report, which was a logical bug as a beginner we must try for logical flaws. I was just performing some basic testing on FB events and accidently identified a unusual behavior, when I noticed that I am not listed in co-host list but still I have all co-host permission. This report showed positive response from FB and leads to a bounty decision.
when an admin of Facebook Page creates an event on the page he will become primary host of that event. A host can add multiple co-host(i.e. pages and profiles) for that event. when the host adds a page as a co-host( page automatically become admin of that event after accepting invite) which was intended.
But the issue was, a malicious co-host page can create a scenario, where he was able to become unremovable co-host and gains persistence on that event permanently because Facebook was not removing admins of co-host page from event when co-host page is deleted and still assume admins of deleted page as co-host internally on FB4A and mobile version of Facebook.
This bug allowed admin of deleted co-host page to edit the event without a co-host role and prevent owner/admin from removing them.
why it was considered as security issue?
An admin who creates an event he have permission to modify edit/delete and remove any user including co-host, if co-host become unremovable he can perform malicious activities without getting removed by admin because the co-host becomes hidden by exploiting that bug, which lead to a security issue.
Setup
userOne admin of pageOne (victim)
userTwo admin of PageTwo (attacker use FB4A app to perform attack)
Repro Steps
- userOne (admin) creates an event on his pageOne and adds pageTwo as co-host on that eventOne.
- login as userTwo, a invitation for co-host role is received as “PageOne is invited to PageTwo for the eventOne” open the notification.
- userTwo will Save the eventOne ,then accept the invitation. Now In order to become hidden co-host, userTwo delete his whole pageTwo to become permanently unremovable .
(It was a test page so we can easily delete the page but in practical, attacker co-host will not delete his whole page because it make the attack very limited, attacker have co-host role he can simply create a Fake page and add that Fake page as a co-host to become hidden which was more practical.)
4. As pageTwo is no longer co-host but userTwo while navigating the eventOne from FB4A, which was saved in step-3 still can see event “Edit” button and he can delete any discussion posts including eventOne.
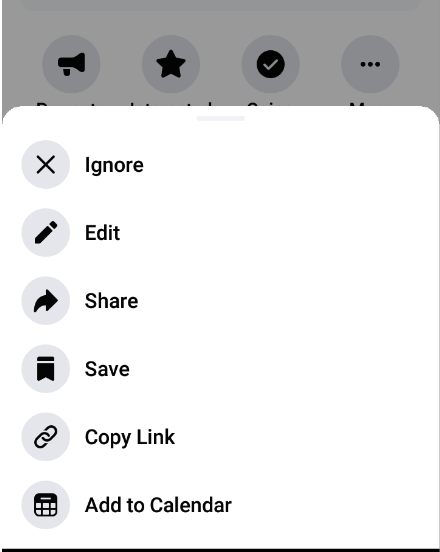
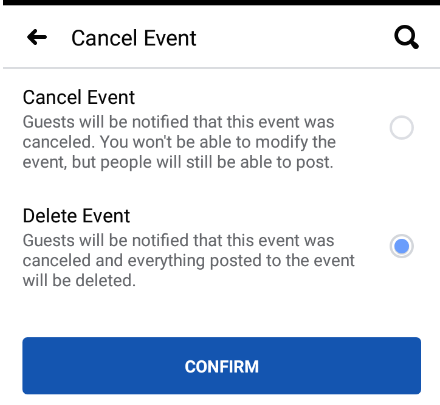
Practically it was impossible to remove deleted co-host page from the event and FB4A still assumes admins of deleted page as co-host internally due to which userTwo was immortal and can still moderate the eventOne.
September 2, 2020: Report sent
September 15, 2020: pre-Triaged after further explanations.
October 2, 2020: Triaged
October 15, 2020: Closed as informative by giving invalid reason.
October 15, 2020: Objected on decision, saying not a valid reason to close the report.
November 13, 2020: Again Triaged on showing further impacts.
January 8, 2020: Fixed by Facebook.
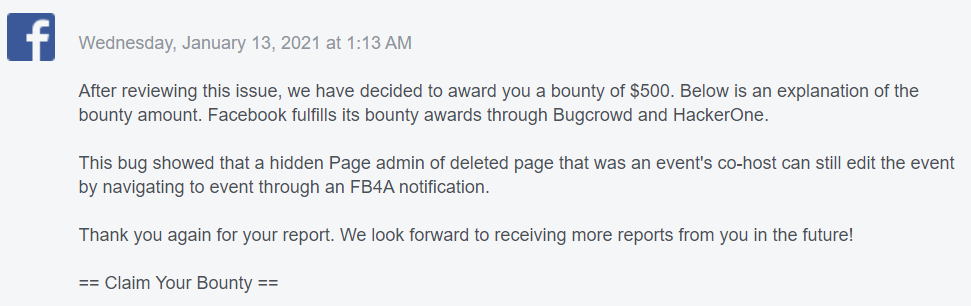
January 13, 2021: Bounty rewarded .
This issue required so long time around 4 months for the complete process, nearly 35 emails exchanged during the process. Even after the report is closed multiple times, I still managed to make it valid issue and FB rewarded with $xxx bounty :) However, it requires co-host role to reproduce the issue hence, the issue showed a limited impact.
This was my First Bug Bounty Writeup, sorry for the grammatical errors. And Thanks for giving Time to read the article about a basic vulnerability on FB.
See you soon ;) with Next writeup, my first Valid bug on Facebook “Story of my 1st valid bug on Facebook | leads to $xxx+$xxx+$xxxx” three bounty within same report.
You can reach out to me on Facebook , just started with twitter for sharing updates regarding related stuff.
如有侵权请联系:admin#unsafe.sh