Introduction
Nmap Scripting Engine (NSE) has been one of the most efficient features of Nmap which lets users prepare and share their scripts to automate the numerous tasks that are involved in networking. As we know about the Nmap’s speed and. competence, it allows executing these scripts side-by-side. According to the needs of the users, they can pick from the range of available scripts or can create their scripts as per the requirements.
Table of Contents
- Introduction
- .nse Scripts
- ms17-010 Vulnerability
- Vsftpd backdoor
- SSL-Poodle Vulnerability
- Rmi classloader vulnerability
- HTTP Slowloris vulnerability
- Nmap-Vulners
- Conclusion
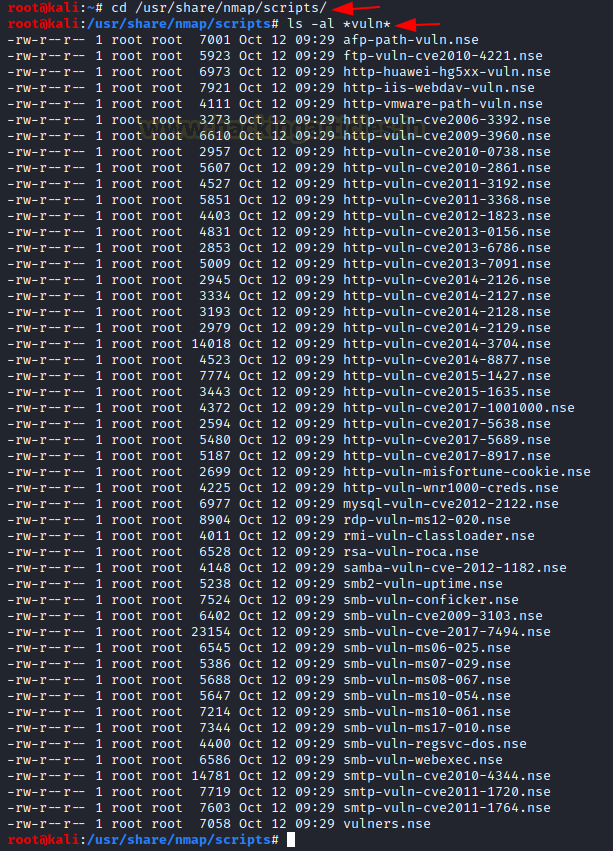
So, let’s get started with listing all the scripts that are available for discovering the vulnerability. Here we see that a list of scripts are available to detect the vulnerabilities. One by one we will run these scripts and check for vulnerabilities.
cd /usr/share/nmap/scripts/ ls -al *vulns* |

ms17-010 Vulnerability
This script detects whether an SMBv1 server in Microsoft systems is vulnerable to the remote code execution which is commonly known as the EternalBlue vulnerability. This vulnerability had been vastly exploited by ransomware like WannaCry. This works on Windows XP, 2003, 7, 8, 8.1, 10, and server 2008, 2012 and 2016.
You see that on executing this script, you see that the system is susceptible to a vulnerability that is at high risk in nature.
nmap --script smb-vuln-ms17-010.nse 192.168.1.16 |

Vsftpd backdoor
This script checks for the presence of vsFTPd 2.3.4 backdoor vulnerability by attempting to exploit the backdoor using a harmful command.
nmap --script ftp-vsftpd-backdoor -p 21 |

SSL-Poodle Vulnerability
The SSL Poodle is a Man-in the middle exploit whose purpose is to take advantage of the security software running on SSL. On running this script, you see that the system is vulnerable.
nmap –script ssl-poodle 192.168.1.12 |

Rmi classloader Vulnerability
This script checks whether Java rmiregistry allows class loads or not. The rmiregistry has default configuration which allows the class to load from remote URLs which may lead to remote code execution.
nmap --script=rmi-vuln-classloader -p 1099 192.168.1.12 |

HTTP Slowloris Vulnerability
It checks for the vulnerability in the web server Slowloris DoS attack where it does not launch an actual DoS attack. This script will open 2 separate connections to the server and then request for URL in base configuration.
nmap –script http-slowloris-check 192.168.1.12 |

SSL-CCS-Injection
This script when run checks if a server is vulnerable to the SSL/TLS “CCS Injection” vulnerability. To exploit this vulnerability using MITM (Man in the Middle Attack), the attacker will then wait for a new TLS connection which will be followed by Client-Sever ‘Hello’ handshake messages.
Nmap –script ssl-ccs-injection -p 5432 192.168.1.12 |

Nmap-Vulners
Nmap – Vulners is a NSE script using some well-known service to provide info on vulnerabilities. This script completely depends on having information on software versions therefore works with -sV flag.
You can install it using git hub code. Then update the scripts in the NSE database.
git clone https://github.com/vulnersCom/nmap-vulners use/share/nmap/scripts/vulners nmap --scripts-updatedb |

Let us load the scripts and check the service versions available on the target machine using nmap vulners. Here we see that all the scripts are loaded which can be used for vulnerability detection based on a particular service version.
nmap -sV -Pn 192.168.1.12 --script=vulners/vulners.nse |


Conclusion
Hence, we see that it using the nmap scripts we can detect the vulnerabilities present on the system which can be a benefit for the Pen Testers.
Author: Jeenali Kothari is a Digital Forensics enthusiast and enjoys technical content writing. You can reach her on Here