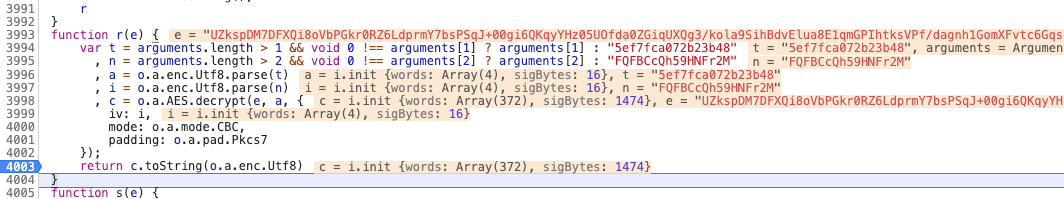
在日常测试的时候,发现系统前端打包数据给后端是加密、后端传输回来的也是加密,看来前端做了加解密,跟踪函数如下:
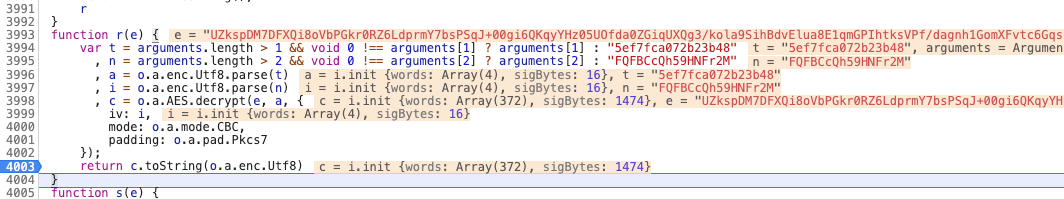
例如AES CBC加密,iv为偏移量,查看数据类型:

搜了下,没有特点的说法,CryptoJS写的,本身特定的wordArray数据类型,查看源码:
部分代码如下:
/** * Hex encoding strategy. */ var Hex = C_enc.Hex = { /** * Converts a word array to a hex string. * * @param {WordArray} wordArray The word array. * * @return {string} The hex string. * * @static * * @example * * var hexString = CryptoJS.enc.Hex.stringify(wordArray); */ stringify: function (wordArray) { // Shortcuts var words = wordArray.words; var sigBytes = wordArray.sigBytes; // Convert var hexChars = []; for (var i = 0; i < sigBytes; i++) { var bite = (words[i >>> 2] >>> (24 - (i % 4) * 8)) & 0xff; hexChars.push((bite >>> 4).toString(16)); hexChars.push((bite & 0x0f).toString(16)); } return hexChars.join(''); },
可以wordArray转到16进制,16进制转字符串
参考:
https://my.oschina.net/u/3549294/blog/1862451
https://segmentfault.com/p/1210000017534439/read
https://searchcode.com/codesearch/view/96336148/
http://tool.chacuo.net/cryptaes
https://blog.csdn.net/qq_31281245/article/details/112462715
文章来源: http://www.cnblogs.com/sevck/p/14545327.html
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh