2018-12-11 14:15:07 Author: parsiya.net(查看原文) 阅读量:55 收藏
Tiredful API is an intentionally vulnerable REST API. I am going to use it to practice a bunch of Burp tricks.
In this part, I want to show how to use Burp macros to detect invalid session and add a custom bearer token header to the requests.
I used the instructions to spin up a docker container and used it with the free Burp Community Edition 1.7.36.
Often times the session times out in the middle of testing or scanning. I only use Burp's scanner on individual requests but session can still time out. Sometimes the application log users out after sending funny payloads. Burp allows you to detect invalidated sessions and run a macro (which is a series of requests) to update the session automagically.
Usually, the session is maintained by cookies and Burp's cookie jar can be automatically updated to refresh the session. In the case of this API, we are using a Bearer token. But this method can be used for any custom header containing a token.
The login request is simple. While this example has only one request, the process for multiple-step requests is similar. The application has two registered users. We are using batman:Batman@123.
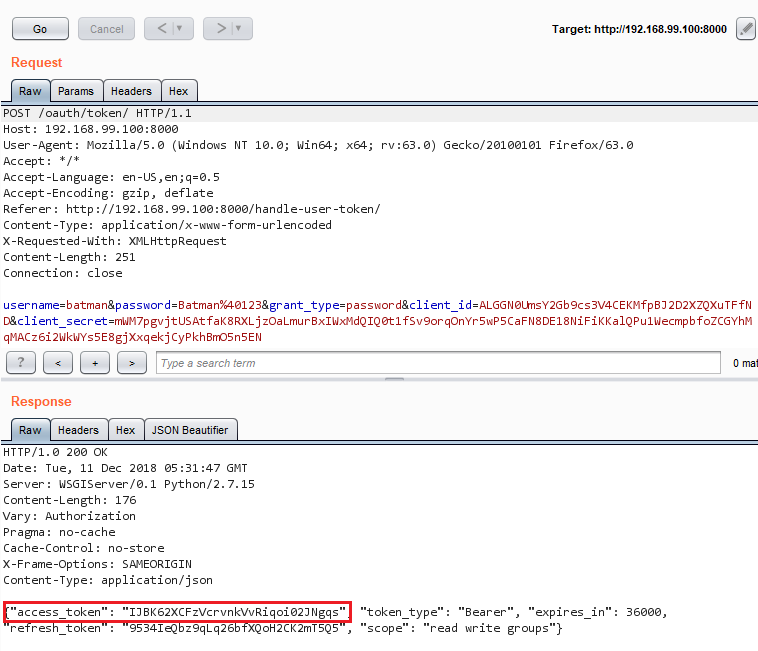 Successful login request
Successful login request
The access_token must be added to every authenticated request like Authorization : Bearer [token].
We also need to detect invalidate sessions. To do so, navigate to http://192.168.99.100:8000/api/v1/advertisements/ to see the response.
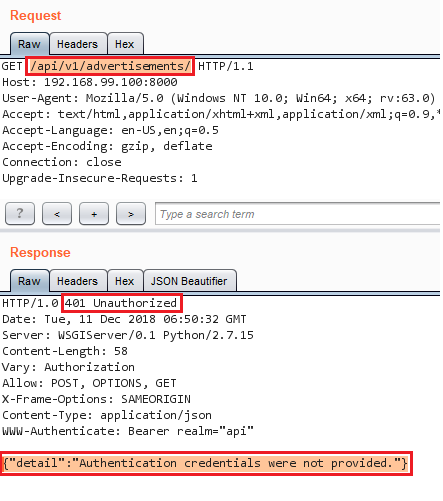 Invalid request
Invalid request
We are going to use the header 401 Unauthorized to detect invalid requests.
We should create a login macro to login as batman. This macro will be executed when Burp detects an invalid/expired session.
- Go to
Project Options > Sessionsand scroll down toMacros. - Select
Addto create a new macro. Macros are created from existing requests. - Select a successful login request (for multi-step logins, select all steps in the login flow) and press
Ok.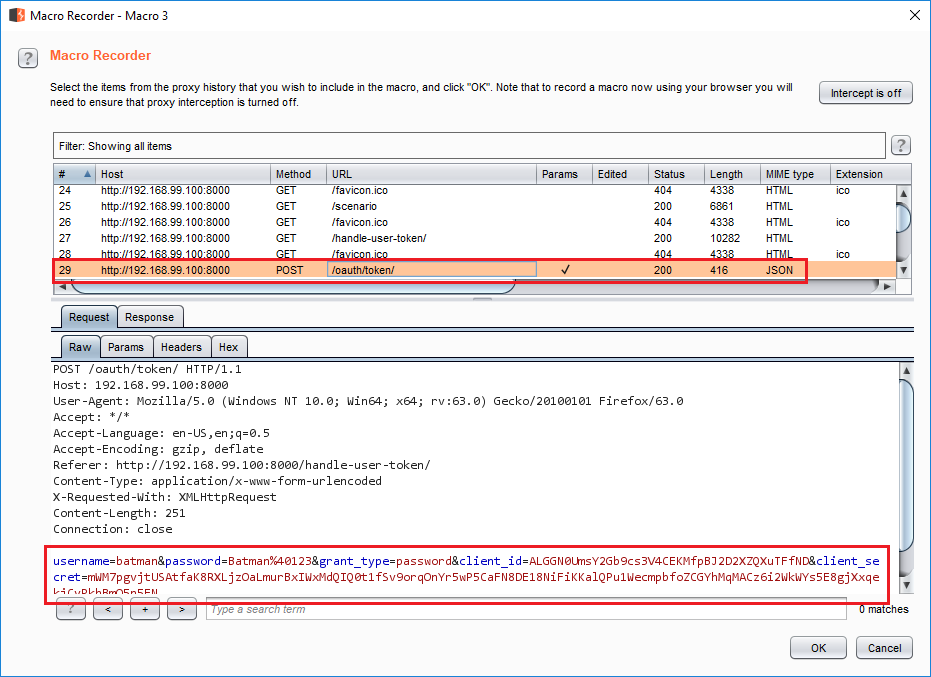 Selecting the login request in macro recorder
Selecting the login request in macro recorder - Select a name and press
OkinMacro Editorto create the macro. If the request had specific parameters (e.g. a CSRF token), we could designate it inConfigure item. This example does not need it.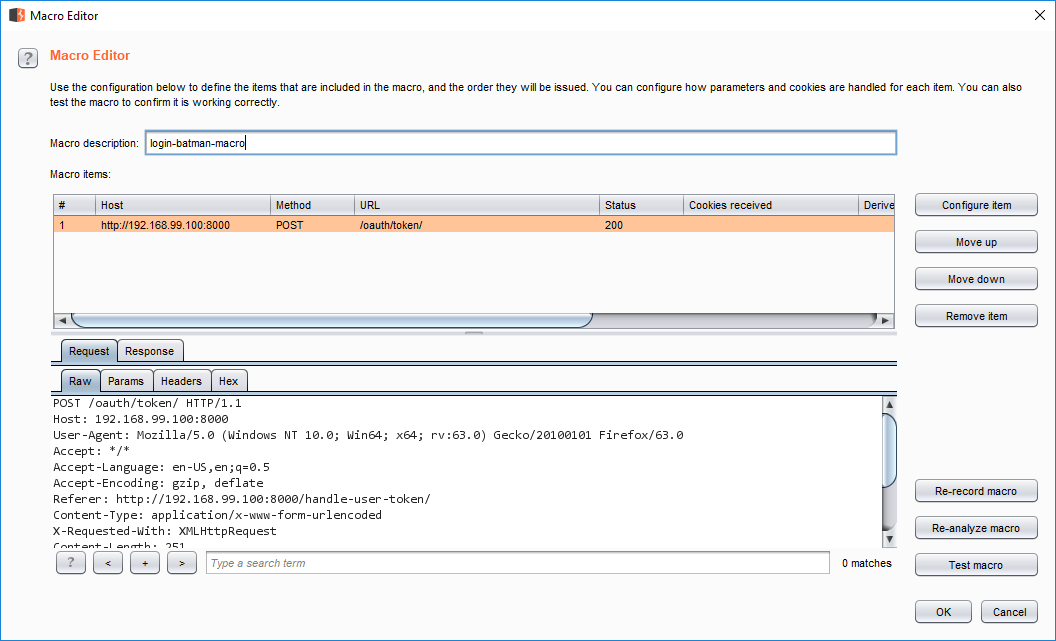 Finish macro recording
Finish macro recording
We need to make Burp perform two action:
- Create a session handling rule. Burp should run the macro whenever a session is invalid.
- Add the
access_tokenas a custom header to that request and resend it.
In order to accomplish number two, we need to use an extension. Burp vanilla does not support adding headers to requests in session validation rules. However, cookies and normal GET/POST parameters (e.g. form-urlencoded ) can be updated.
- Install the
Add Custom Headerextension at https://github.com/lorenzog/burpAddCustomHeader. It's also available in the Burp App Store. - Navigate to the
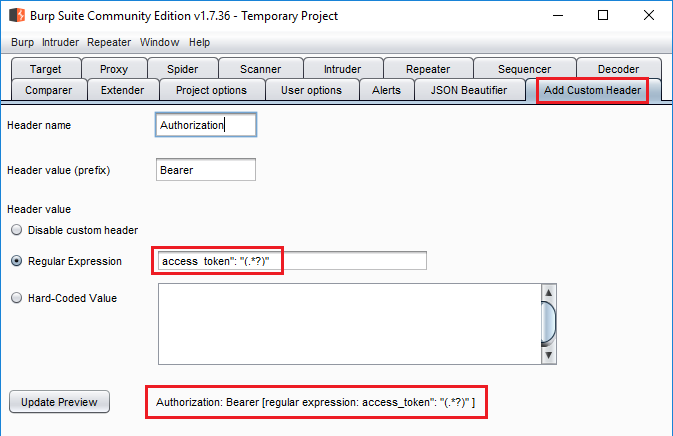
Add Custom Headertab. It's pre-populated with some sane defaults. - The original regex is
access_token":"(.*?)". The underline does not show up in the input field but you can click onUpdate Previewto see it. - We need to change the regex. Our response is a bit different. Ours has an extra space after
access_token":. Our regex will beaccess_token": "(.*?)"instead.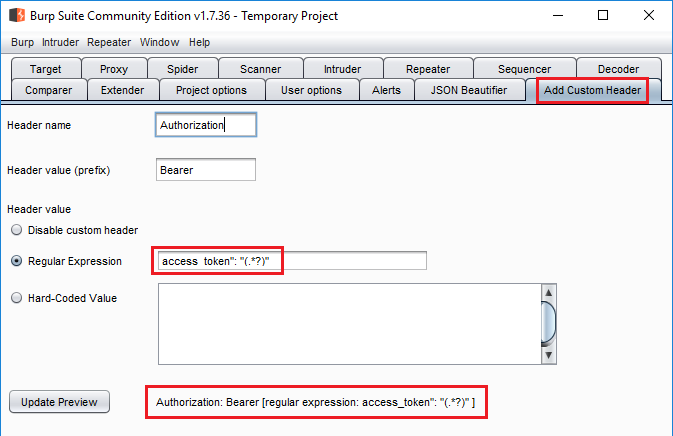 Add Custom Header setup
Add Custom Header setup
Session Handling Rule
- In the same screen (
Project Options > Sessions) clickAddunderSession Handling Rules. - Type in a rule description. E.g.,
session-validation. - Under
Rule ActionsclickAddand selectCheck session is valid.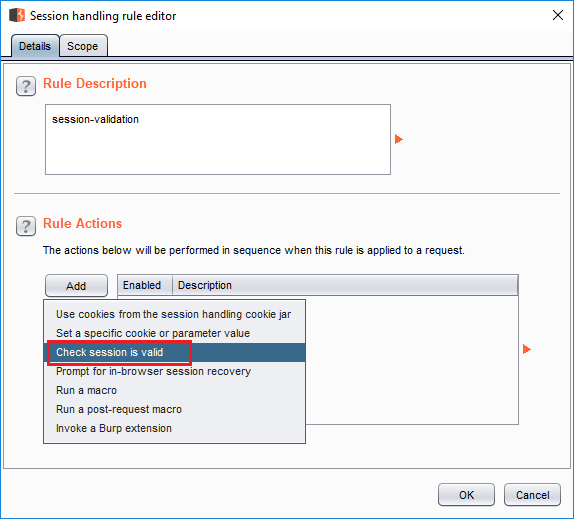 Session validation rule - 1
Session validation rule - 1 - In the next screen, select
Issue current requestunderMake request(s) to validate session. This tells Burp to modify the same request with the new header and resend it. - Under
Inspect response to determine session validity, selectHTTP headersand enter401 Unauthorizedin theLook for expressionfield. This section determines how Burp detects invalid sessions. We are telling Burp that the session is invalid if401 Unauthorizedappears in the response header. - Keep the rest of the options. We want exact match and case-insensitive.
Match indicatesmust be set toinvalid session. We are telling Burp how to detect invalid sessions after all.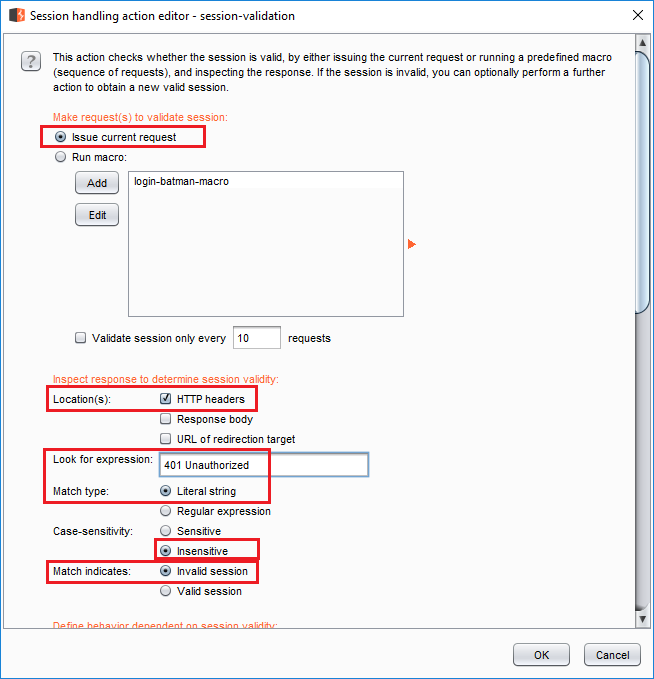 Session validation rule - 2
Session validation rule - 2- Under
Define behavior dependent on session validitycheckIf session is invalid, perform the action below, checkRun a macroand select the login macro. - Uncheck both
Update current requestboxes (doesn't matter in this example, we are not using cookies or parameters). - And finally, check
After running the macro, invoke a Burp extension action handler:and selectAdd Custom Header. Response of the last request in the macro is passed toAdd Custom Header. The extension extract sthe token using the regex (remember the match group) and adds it as a header to the request.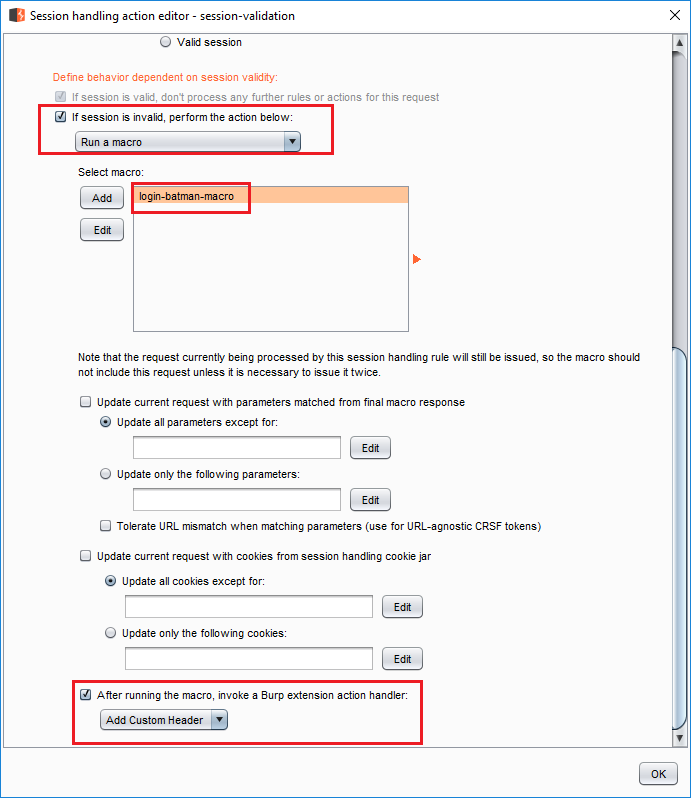 Session validation rule - 3
Session validation rule - 3 - Press
Okand we're back at the first screen. Now we need to select the scope. - Click the
scopetab and select any tool that needs this rule underTools Scope. We will go with the default. - Under
URL ScopeselectUse suite scope. We will set it later.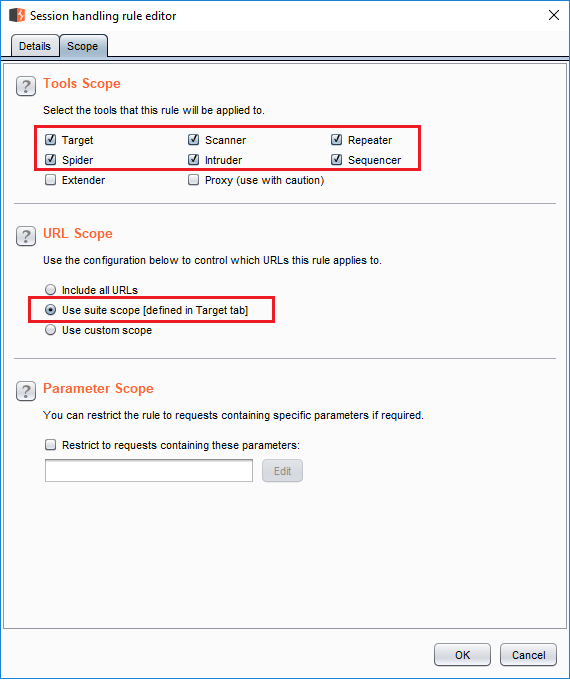 Setting scope
Setting scope
Alternate Session Handling Rule
Instead of detecting the session, we can use an easier rule and run the macro and add the header to every request. I went with the more complicated process because I wanted to practice setting it up.
- The alternate rule is the same in every aspect, except the
Rule Actionswhich isAdd (button) > Run a Macro. - Select the macro.
- Uncheck both update checkboxes.
- Enable
After running the macroand selectAdd Custom Header.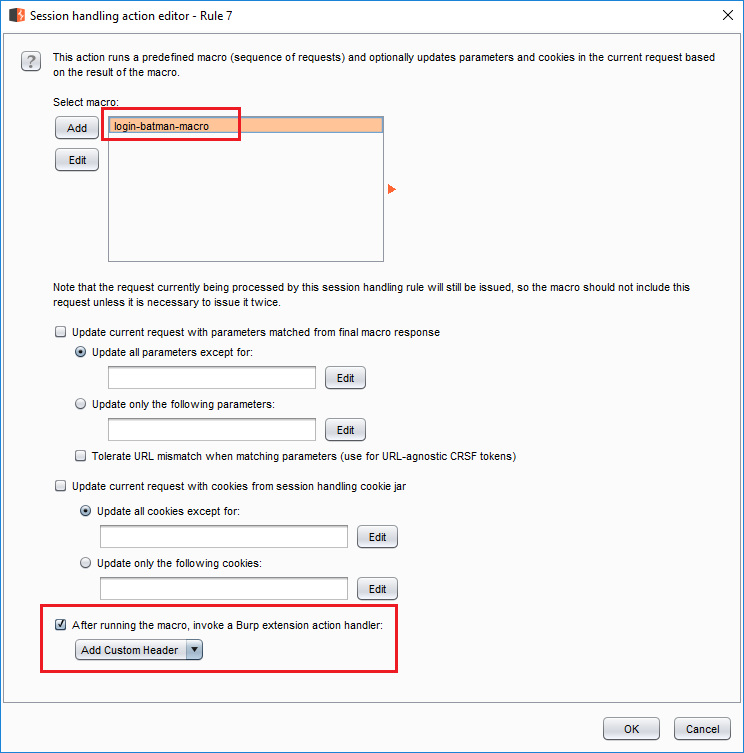 Alternate rule
Alternate rule
Setting the Scope
In this example, we do not have to set the scope. But usually, we want to only operate in a specific scope. In my VM, the address is http://192.168.99.100:8000 so I added it in Target > Scope tab. I also excluded the login and logout API endpoints.
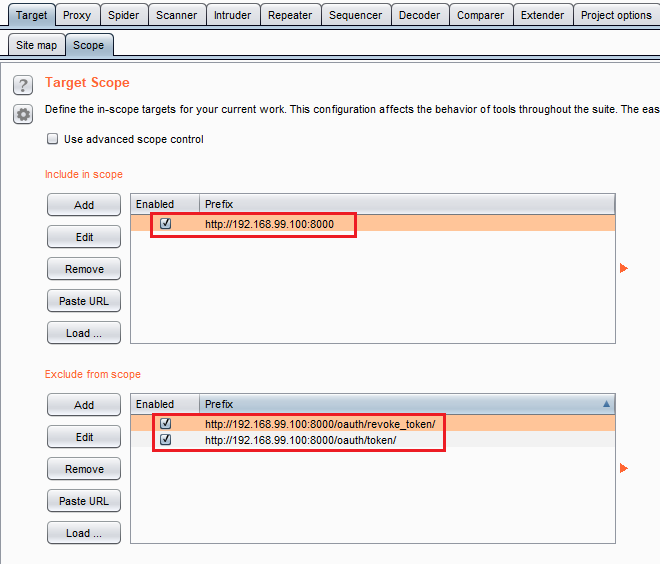 Scope
Scope
Now it's time to see the fruit of our labor. Right click the request to http://192.168.99.100:8000/api/v1/advertisements/ in Burp history and send it to Repeater. Click Send and see the header added to the request and get a valid response. It's empty but it's valid.
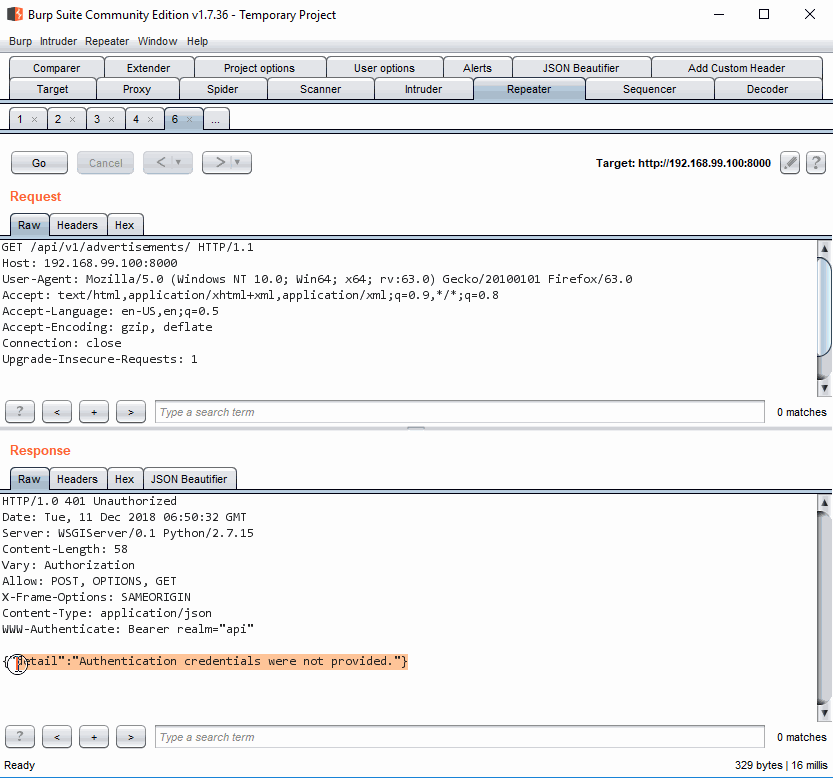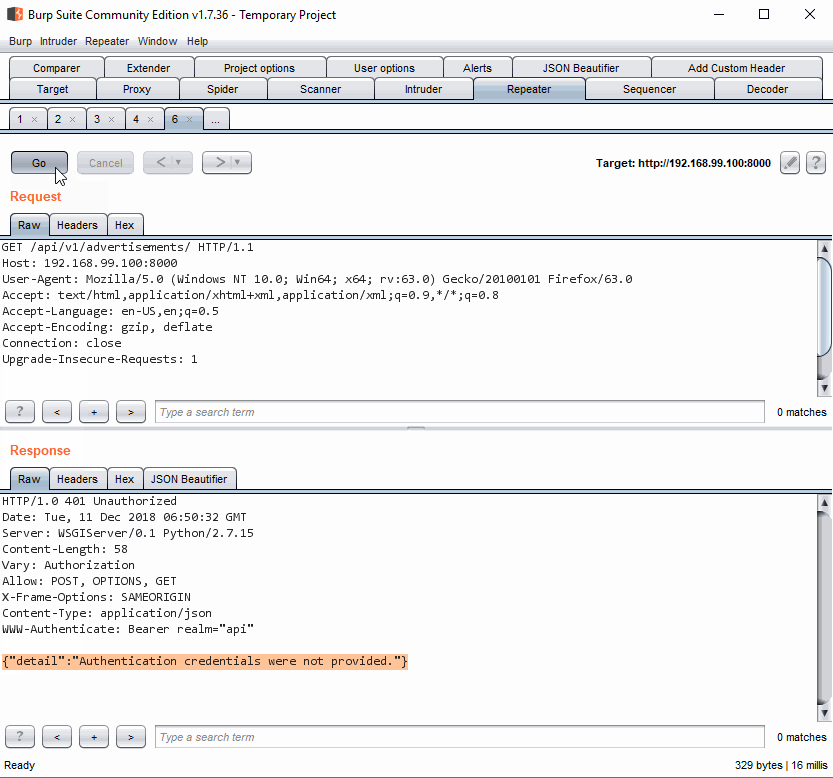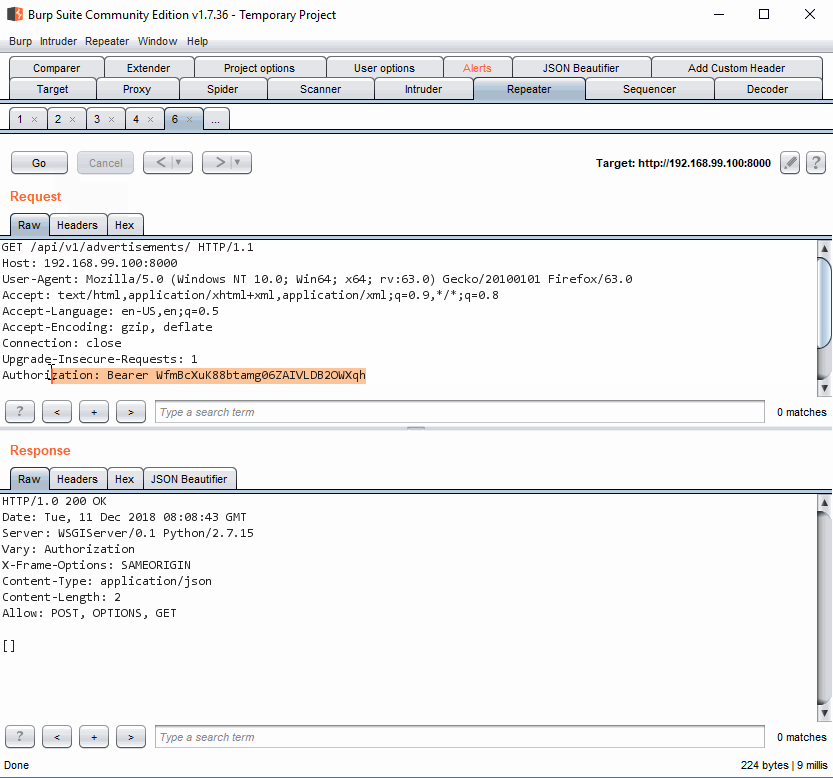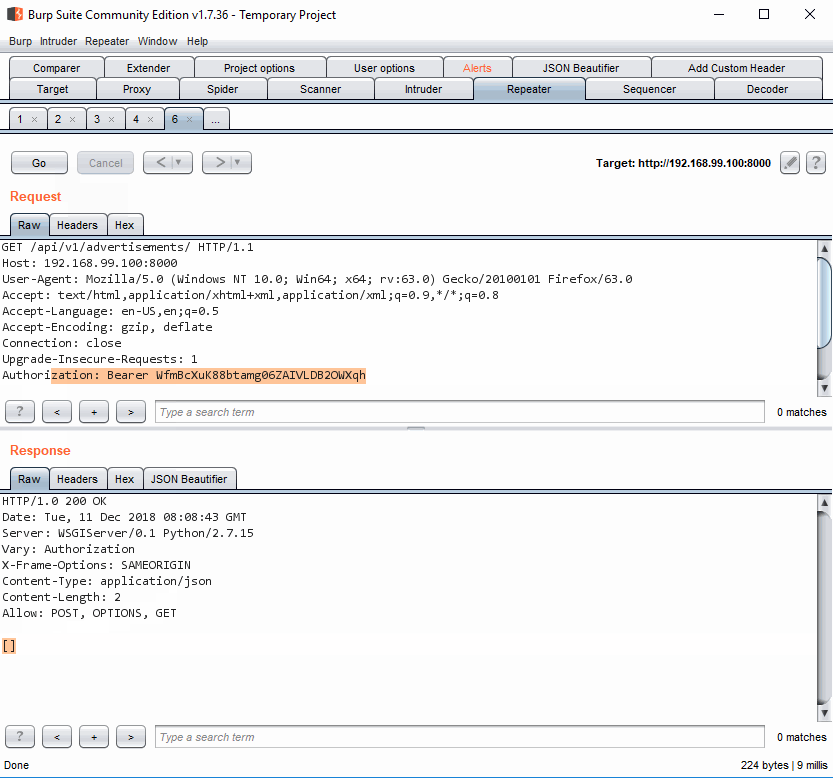 Burp in Action
Burp in Action
Tune in for the next section, where I talk about using Burp's sitemap comparison.
如有侵权请联系:admin#unsafe.sh