
I have written a lot about thick clients. However, I have not done more than a few practical examples that I can show my co-workers or anyone else asking questions. Recently, I came across the Damn Vulnerable Thick Client Application by SecVulture at https://github.com/secvulture/dvta.
I am not going to use the original version of the application. Someone has created a fork and added more protections. We will use this fork instead:
Neither fork's setup instructions worked for me. As a result, the first part is actually setting up the application and the necessary back-end in only one VM. But don't worry, we will do a bit of reverse engineering with dnSpy to fix an issue.
Thanks to SecVulture for creating the app and maintainers of the second repository for adding protections.
There are no instructions in the original repository at:
But author's has some post on Infosec Institute with setup and solutions at1:
The fork has a Word document file with pictures and setup instructions. I still could not make it work.
I know setup is boring and you want to "hack." But this is necessary to have fun later.
0. Ingredients and Price
Hint: Everything is free.
- Windows 7 (or 10) VM. I used a 32-bit Windows 7 VM from https://modern.ie: Free.
- Microsoft SQL Server 2008 Express: Free.
- Microsoft SQL Server 2008 Management Studio Express: Free.
- FileZilla FTP Server: Free.
- Microsoft Sysinternals Suite: Free.
- dnSpy: Free.
1. Get the Code and Binary
Download the whole repository as a zip file (because you don't want to install git on a disposable VM like me) from:
Extract it to a location of your choice. I named mine dvta-master.
2. Install Microsoft SQL Server 2008 Express
3. Install Microsoft SQL Server 2008 Management Studio Express
We need management studio to set up our database and tables.
4. Create the DVTA Database
Now we can use the management studio to create the database and populate it.
- Start
SQL Server Management Studioand connect to theSQLExpressinstance. - Right-click on
Databasesto the left and selectNew Database. - Enter
DVTAin the database name and pressOK. Don't change anything else.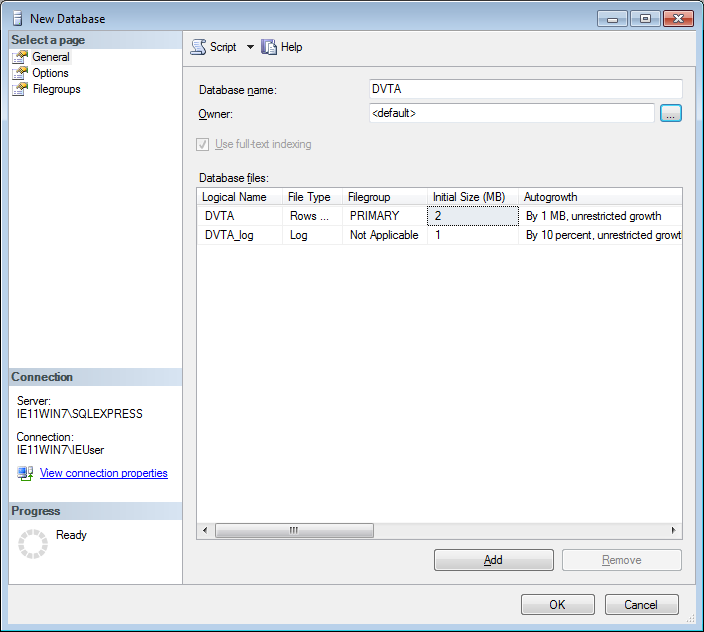 Only change the database name
Only change the database name - Right-click on
DVTAunderDatabasesand selectNew Query. - To create the
userstable, enter this query and selectExecute(note this is different from the original instructions, we are setting theidcolumn to auto-increment by1starting from0). Without auto-increment, registration will not work:Creating the users table 1 2 3 4 5 6 7 8CREATE TABLE "users" ( "id" INT IDENTITY(0,1) NOT NULL, "username" VARCHAR(100) NOT NULL, "password" VARCHAR(100) NOT NULL, "email" VARCHAR(100) NULL DEFAULT NULL, "isadmin" INT NULL DEFAULT '0', PRIMARY KEY ("id") )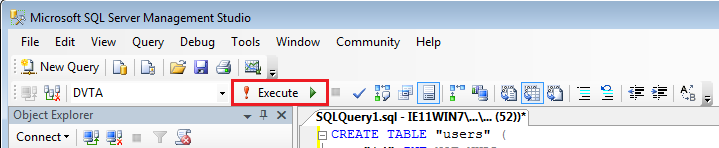 Execute button is a bit hard to find
Execute button is a bit hard to find - Next create the
expensestable (I have set theidcolumn to auto-increment):Creating the expenses table 1 2 3 4 5 6 7 8 9CREATE TABLE "expenses" ( "id" INT IDENTITY(0,1) NOT NULL, "email" VARCHAR(100) NOT NULL, "item" VARCHAR(100) NOT NULL, "price" VARCHAR(100) NOT NULL, "date" VARCHAR(100) NOT NULL, "time" VARCHAR(100) NULL DEFAULT NULL, PRIMARY KEY ("id") ) - Populate the users table with some test data. The non-admin users can be added through the application later but admin needs to be setup manually.
Adding test users 1 2 3 4 5INSERT INTO dbo.users (username, password, email, isadmin) VALUES ('admin','admin123','[email protected]',1), ('rebecca','rebecca','[email protected]',0), ('raymond','raymond','[email protected]',0);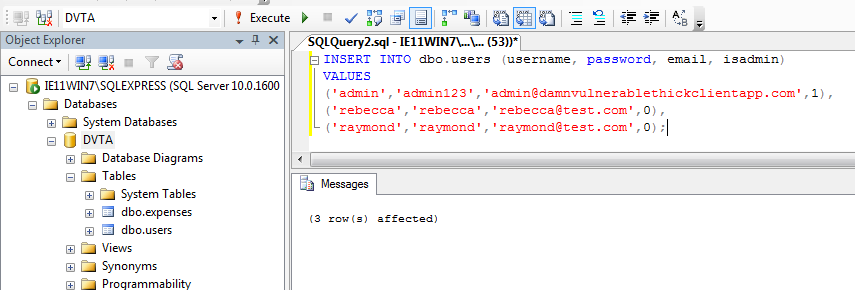 Three test users added
Three test users added - Now we can right click on
dbo.usersand selectSelect Top 1000 Rowsto see the test data.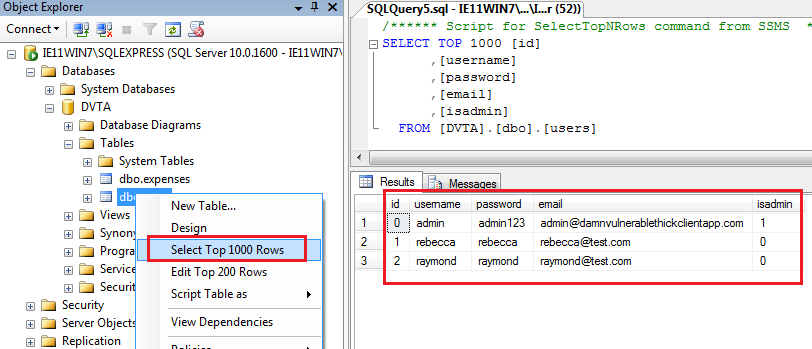 Test users in the database
Test users in the database - Open
SQL Server Configuration Managerand click onSQL Server Network Configuration > Protocols for SQLEXPRESS
5. Setup the FTP Server
There's no need to install XAMPP. Manually install and use FileZilla FTP server.
- Create a directory (this will be the FTP root directory), I named it
dvta-ftpand put in on desktop. - Download and install the Filezilla FTP server (or any other server of your choice).
- Use
Edit (menu) > Users
Now our FTP server is ready and runs as a Windows service.
6. Modify DVTA to Connect to Our Local SQL Server
The binary is configured to look for the SQL and FTP servers at a hardcoded IP address. The SQL Server address is in the .NET config file (which is just an XML file).
- Open
dvta-master\DVTA\DVTA\bin\Debug\DVTA.exe.config(by default extensions are hidden on Windows so the extension might not be visible).- Under
appSettingschange value ofDBSERVERto127.0.0.1\SQLEXPRESS.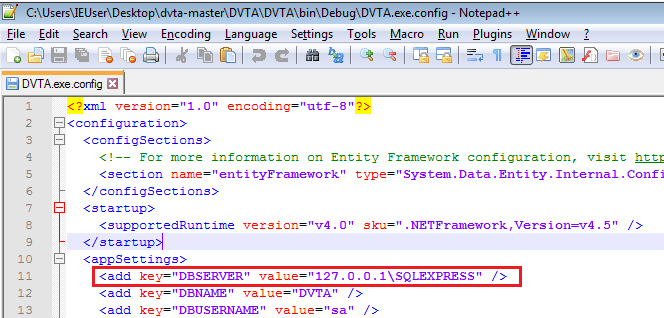 Modified config file
Modified config file - Note: The
Releaseversion in this fork has extra protections (the login button is disabled by default). We will use theDebugversion for testing the connection to our SQL Server. Be sure to do the same for theReleasebuild later.
- Under
- Now we can login with any of the test users and also register new users.
- Notes:
- The
Fetch Timebutton will return an error regardless. I think it is the cert pinning protection that we need to bypass later.
- The
7. Fix the FTP Connectivity
Admin can backup server files to an FTP server. But the FTP's address is hardcoded. It's 192.168.56.110. We can see this in the source code at \dvta-master\DVTA\DVTA\Admin.cs (search for Upload("ftp://192.168.56.110", "dvta", "p@ssw0rd", @pathtodownload+"admin.csv");). We want to change it to localhost.
- We can fix it in different ways:
- Modify the source code and recompile the app. That involves installing Visual Studio and I don't wanna do that.
- Modify the binary with dnSpy.
- This is not the case here but if the application used a hostname, we could redirect using the
hostsfile. This is a common approach with real world software.
7.1 Use dnSpy to Modify the Hardcoded FTP Address
Let's assume we do not know the FTP address. That means we need to:
- Discover the address.
- Change the address in binary.
Discover the FTP Address
Use whatever method you are comfortable with. I used Procmon.
- Start Procmon.
- Run the application, login as admin and try to use the backup functionality.
- Wait until you get the error message.
- Set this filter in Procmon
Process Name is DVTA.exe. - Remove all activities other than network by clicking on the buttons in the picture. Only keep the middle button enabled to display network activity.
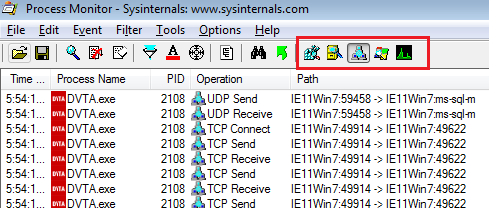 Hover over each button to see what it does
Hover over each button to see what it does - ???
Profit2.
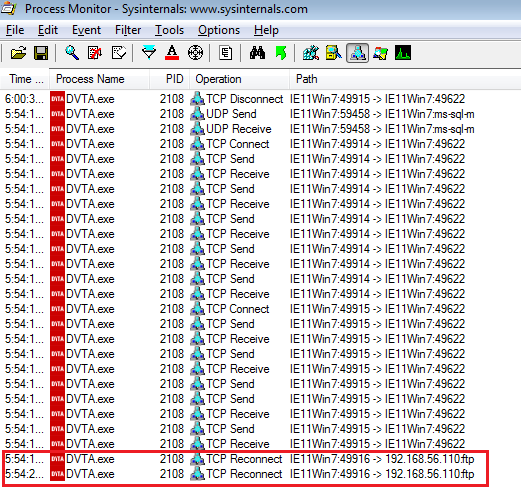 FTP address discovered
FTP address discovered
Modify the Address in Binary
Now we can use dnSpy to modify this address in the application.
We setup DVTA in a VM and patched it to connect to our local FTP server. Now things are ready to go and we can start hacking the application. In the next post I will start working on the application.
如有侵权请联系:admin#unsafe.sh