Quarterly highlights
Banking phishing: new version of an old scheme
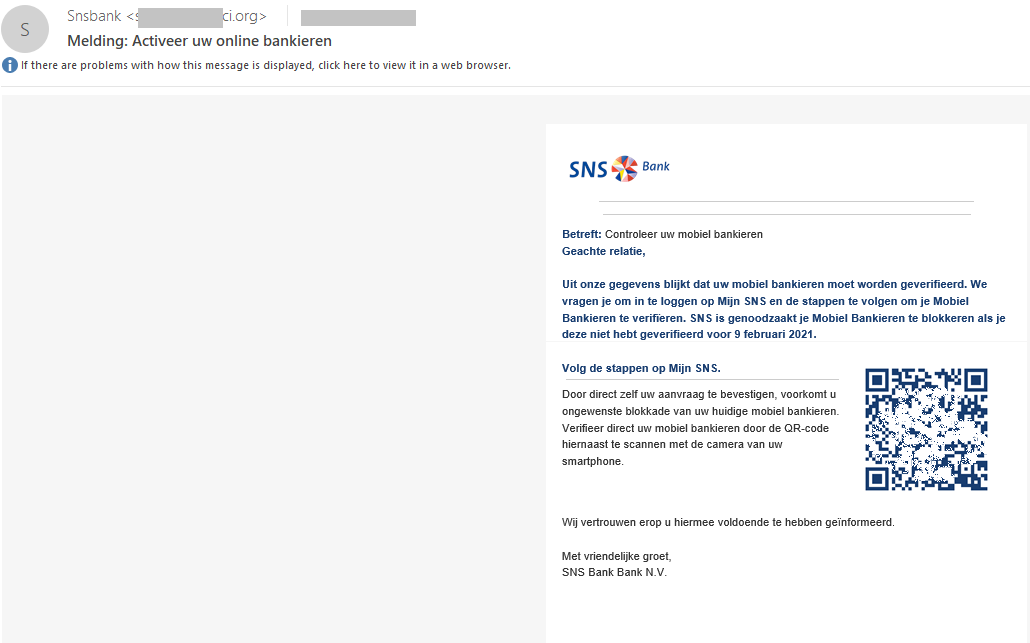
In Q1 2021, new banking scams appeared alongside ones that are more traditional. Clients of several Dutch banks faced a phishing attack using QR codes. The fraudsters invited the victim to scan a QR code in an email, ostensibly to unblock mobile banking. In actual fact, scanning the code resulted in a data leak, money theft or device infection, if it contained a link to a web page with malware.
To lure users to their sites, phishers exploited the COVID-19 topic. In particular, in a newsletter purporting to be from the MKB bank, recipients were asked to catch up on the latest news about the pandemic and measures taken by the bank. The link pointed to a fake Outlook authorization page.
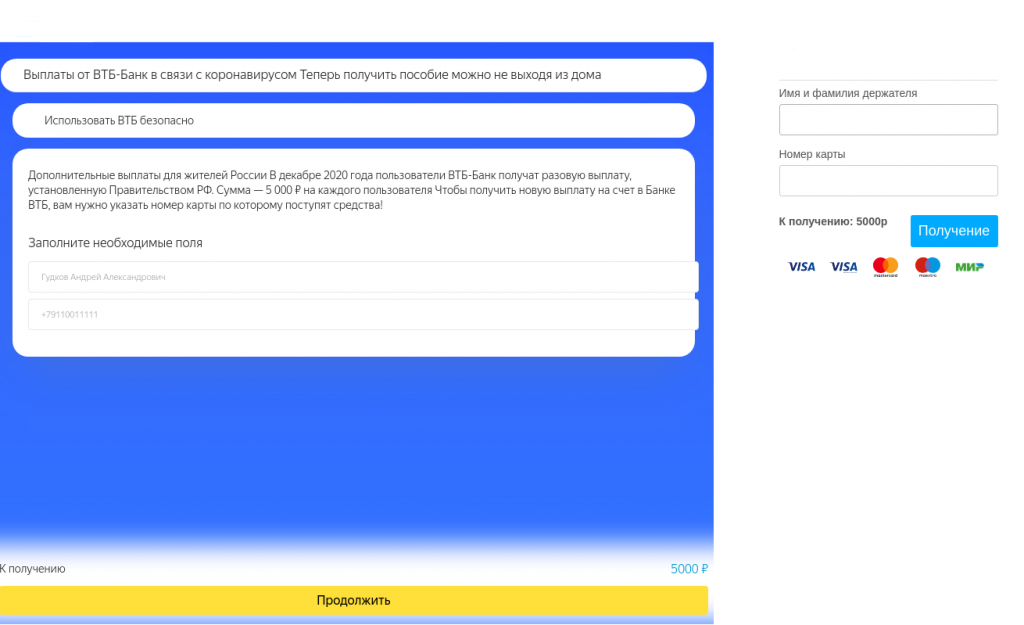
This past year, cybercriminals have actively exploited the topic of government payouts, most often in relation to damage caused by the pandemic. In Q1 2021, scammers imitating bank emails began to focus on compensation. The links in their messages took the victim to a well-designed phishing pages with official emblems, business language and references to relevant laws. The attacks were mostly aimed at stealing any card details and personal data.
However, users of specific banks were also targeted. In this case, the focus was on copying the external attributes of the bank’s website to create a near-indistinguishable phishing version.
Vaccine with cyberthreat
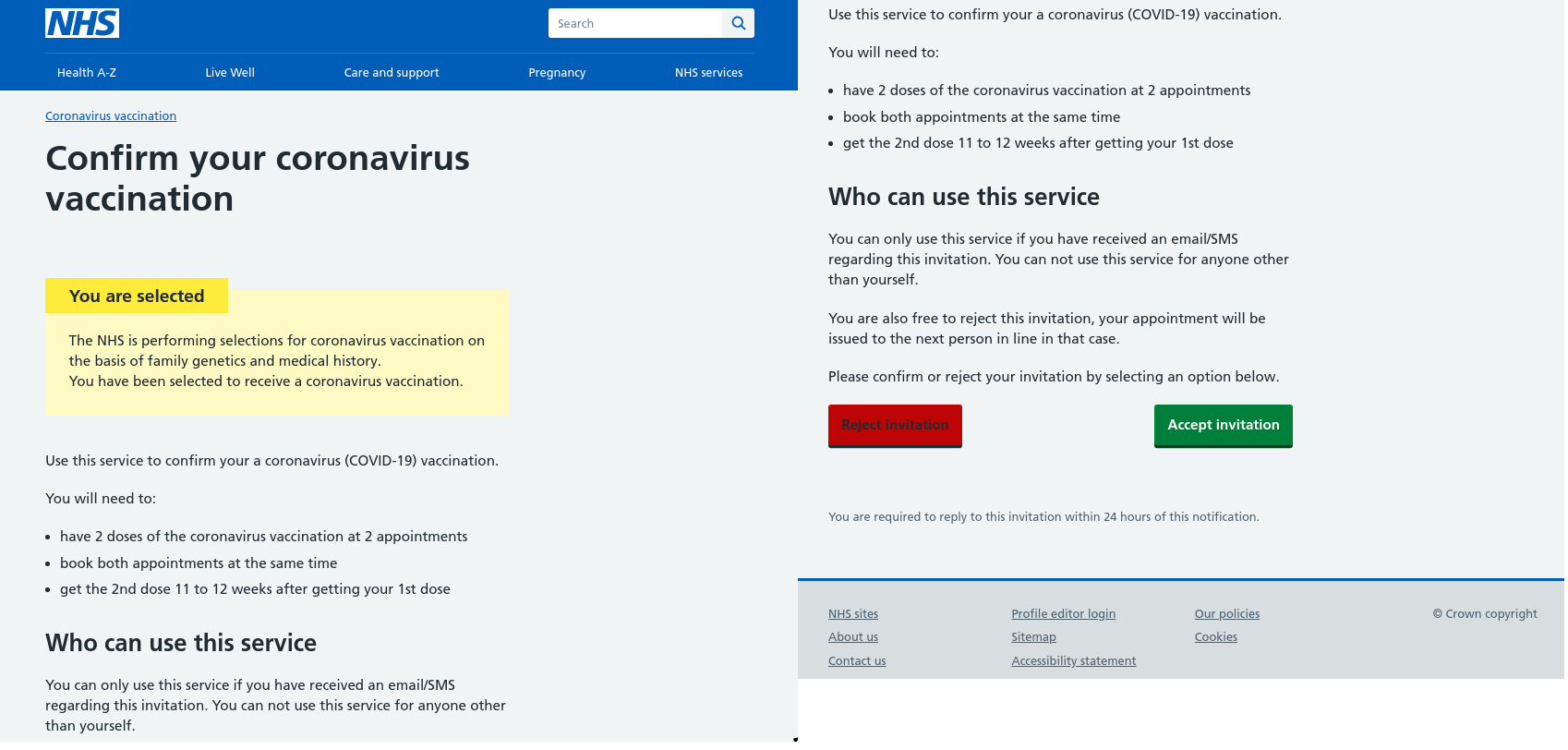
COVID-19 vaccination was one of the hottest global topics, and hence highly attractive to scammers. Cybercriminals took advantage of people’s desire to get vaccinated as quickly as possible. For instance, some UK residents received an email that appeared to come from the country’s National Health Service. In it, the recipient was invited to be vaccinated, having first confirmed their participation in the program by clicking on the link.
In another mailing, the attackers focused on age — people over 65 were asked to contact a clinic to receive a vaccine.
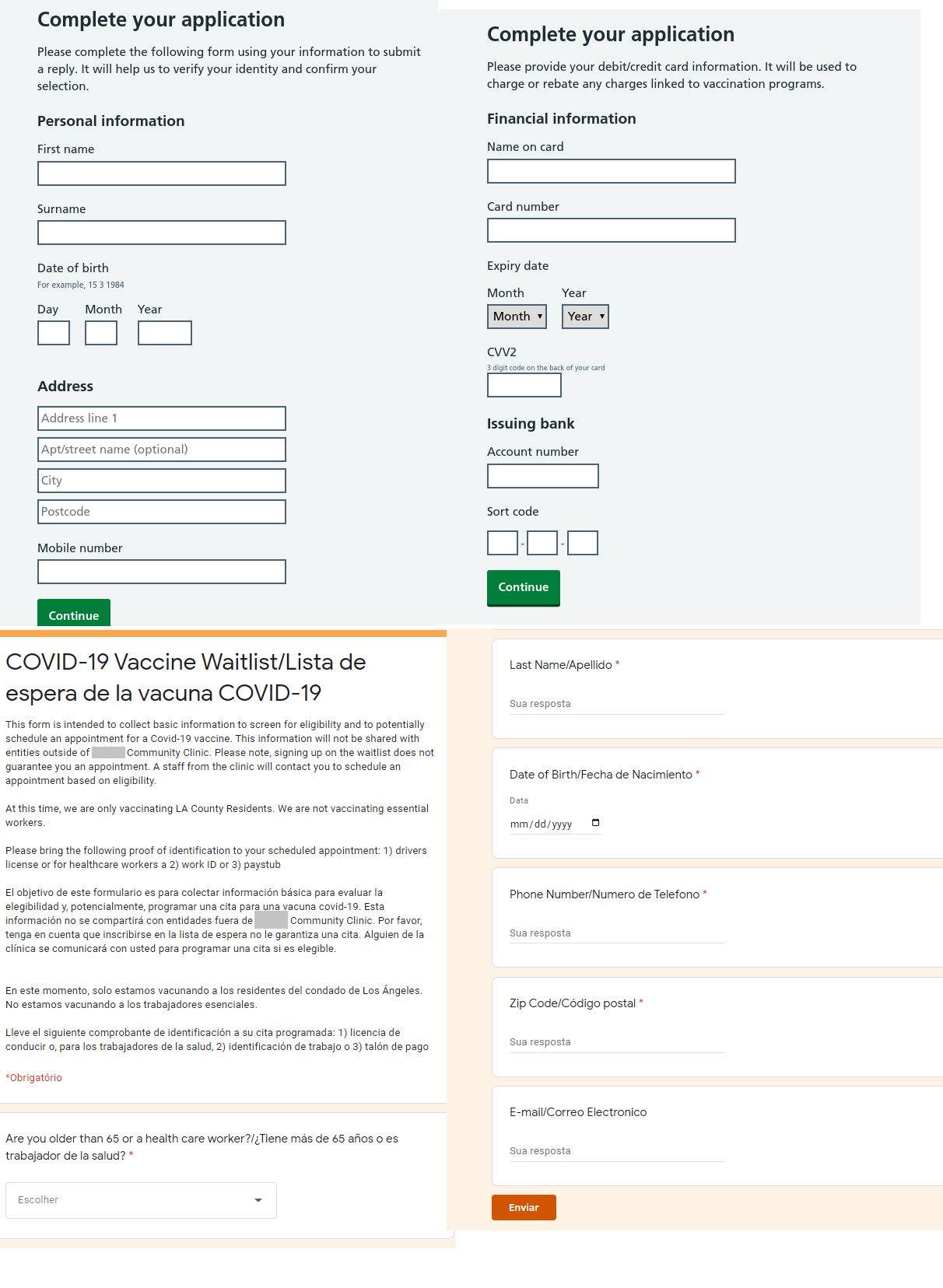
In both cases, to make a vaccination appointment, a form had to be filled out with personal data; and in the first case, the phishers also wanted bank card details. If the victim followed all the instructions on the fake website, they handed their money and personal data to the attackers.
Another way to gain access to users’ personal data and purse strings was through fake vaccination surveys. Scammers sent out emails in the name of large pharmaceutical companies producing COVID-19 vaccines, or of certain individuals. The message invited the recipient to take part in a short survey.
Participants were promised a gift or cash reward for their help. After answering the questions, the victim was redirected to a page with the “gift.”
Having consented to receive the prize, the user was asked to fill out a detailed form with personal information. In some cases, the attackers also asked for payment of a token amount for delivery. However, if the victim went ahead and entered their bank card details, the amount charged was several times higher. Needless to say, no gift materialized.
The vaccination topic could hardly be ignored by spammers offering services on behalf of Chinese manufacturers. The emails mentioned lots of products related to diagnosis and treatment of the virus, but the emphasis was on the sale of vaccination syringes.
Such offers may look very favorable, but the likelihood of a successful deal is zero. Most if not all of the time, the “business partners” simply vanish into thin air after receiving the agreed prepayment.
Corporate segment: on-the-job fraud
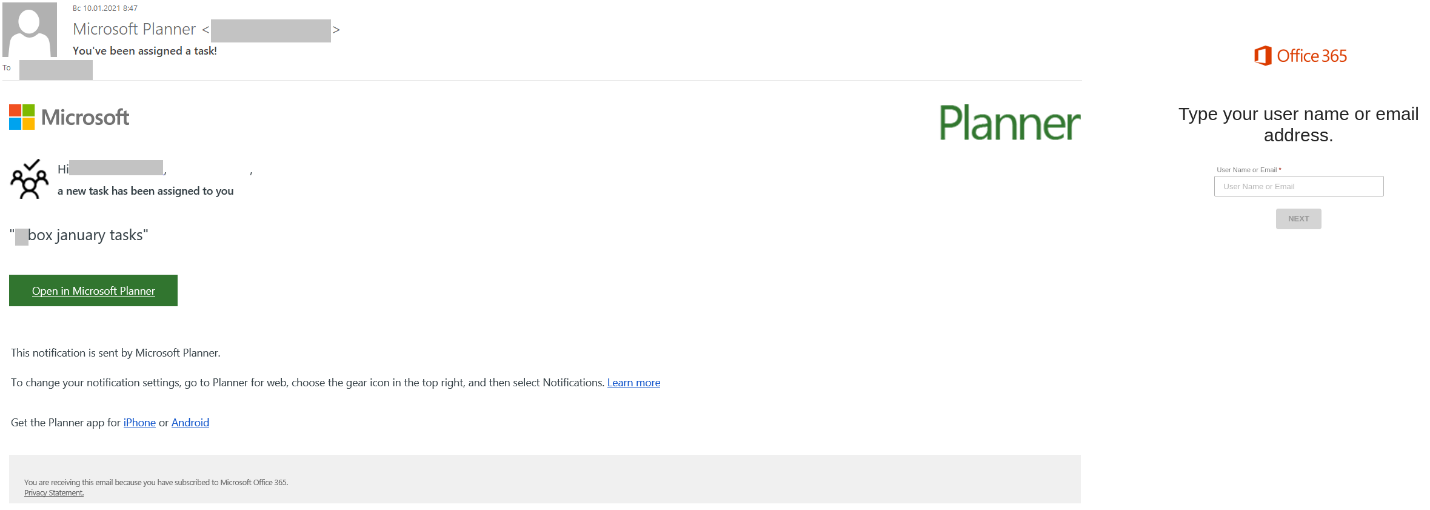
Corporate usernames and passwords remain a coveted prize for scammers. To counter people’s increasingly wary attitude to emails from outside, attackers try to give their mailings a respectable look, disguising them as messages from business tools and services. By blending into the workflow, the scammers calculate that the user will be persuaded to follow the link and enter data on a fake page. For example, a “notification” from Microsoft Planner invited the user to review their tasks for the coming month. The link redirected them to a phishing page requesting their Microsoft account credentials.
In the Runet (Russian internet), we found an email seemingly from the support department of an analytics portal. The messages talked about recent updates and suggested checking the availability of the resource. The link also required entering corporate account credentials.
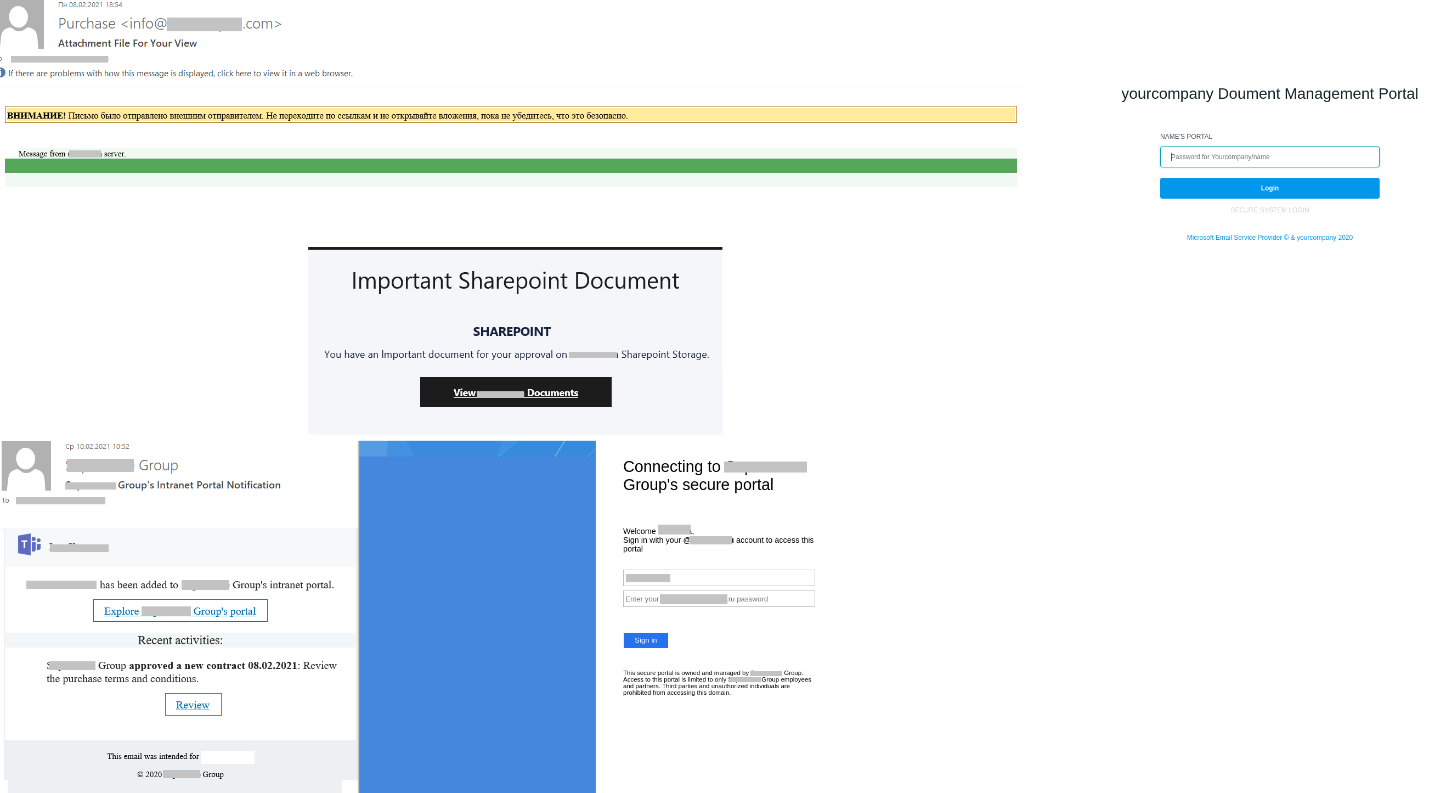
Old techniques, such as creating a unique fake page using JavaScript, were combined in Q1 with overtly business-themed phishing emails. If previously scammers used common, but not always business-oriented services as bait, the new batch of emails cited an urgent document awaiting approval or contract in need of review.
Every little bit helps
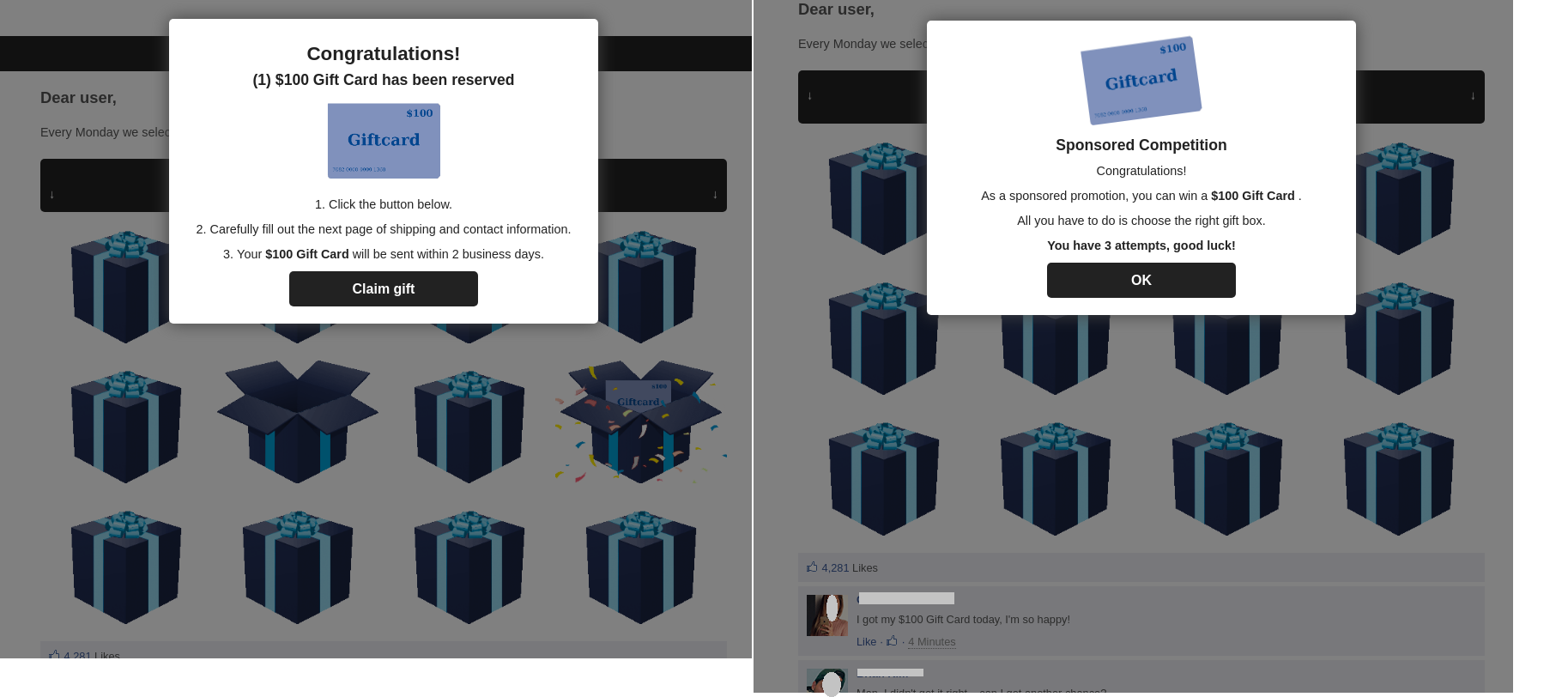
Since the end of last year, we have observed fraudulent emails and fake pages urging users to pay a small sum for certain services. The payment indicated in the fake email was often so tiny that the potential victim could ignore the risks. For example, in one of the emails below, the cybercriminals ask for just 1.99 rubles (US$0.027). The calculation was simple: users would be less averse to paying a small amount than a larger one, which means more potential victims willing to enter card details on the bogus site. To make the emails more convincing, they imitated commonly used services. For example, delivery services — messages from which are often faked — led the field. The potential victim was asked to pay for customs clearance or package delivery. However, the scammers did not fake the courier service emails very well: they were readily given away by the address in the From field or by the invalid tracking number indicated in the email.
Besides delivery, scammers found other reasons for mailing out “invoices.” In particular, fake notifications about payment for domain usage or even an expired WhatsApp subscription did the rounds. In the latter case, the very mention of a paid subscription should sound an alarm, since even the business version of WhatsApp is free.
Although the scammers asked for a token payment in the email, in reality, if successful, they siphoned off far more than that from the victims’ account, and swiped their bank card details. This danger is ever-present when entering data on dubious websites.
Intrigue: emails from strangers
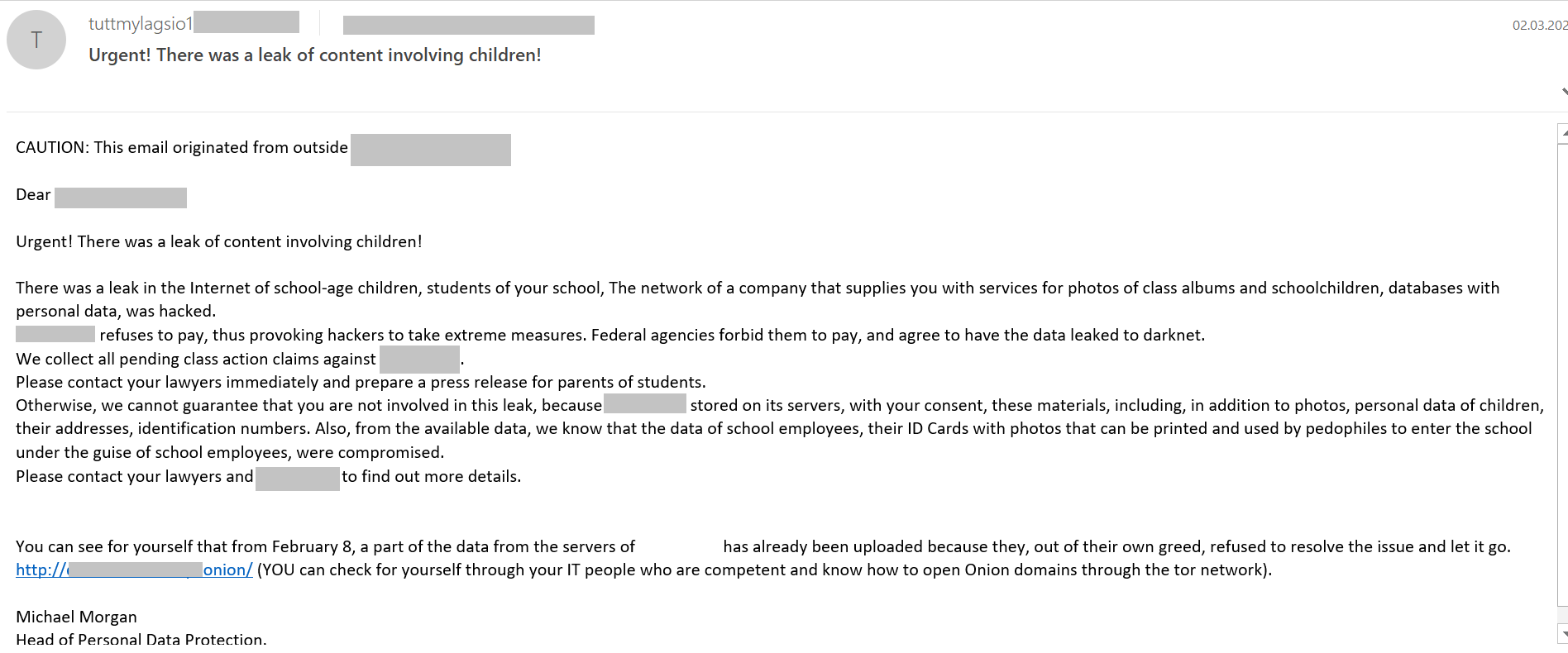
In March, we identified a targeted mailing to the addresses of an educational institution. The email reported a hack of the database of the school’s partner company, which resulted in the intruders getting their hands on the personal data of students and employees. The company refused to pay the ransom, so now the school administration must prepare for the worst: the data might find its way onto darknet, and from there to even worse criminals, who could use it to enter the school building under the guise of an employee. To convince the school leaders of the reality of the looming threat, the email authors advised clicking the provided link and viewing a portion of the stolen database. The link led to a site in the .onion domain, which can only be opened using the Tor browser. Behind the link was a C&C server that was accessed by malware (various ransomware, including Trojan-Banker.Win32.Danabot). A link to this resource was also contained in ransom messages from the attackers, and in some cases malware was downloaded from it. If a curious employee visited this resource, they risked launching the ransomware in the school’s network or facing a demand to pay the ransom on behalf of the partner company.
Cybercriminals adopted an interesting tactic to attack Facebook users. The potential victim received an email saying that their account had violated the social network’s terms of use. To avoid the account being deleted, the scammers advised the recipient to follow the link and lodge an appeal. At the same time, the window for doing so was very short so as to hurry the victim into acting quickly without scrutinizing the message. The email would have been no different from any other aimed at stealing Facebook credentials, but for one nuance: the link in the message pointed to an actual Facebook page.
Resembling an official notice, the page stated that an erroneous decision to block an account could be disputed by following the link provided. In reality, it was a note in a Facebook user’s profile, which the sharp-eyed user could have discerned from the word “notes” in the address. Clicking the link in the note took the victim straight to a phishing site. The attackers’ calculation was simple: first lull the victim’s vigilance with a legitimate link, then get them to enter their credentials on a fake page.
Statistics: spam
Proportion of spam in mail traffic
In Q1 2021, the share of spam in global mail traffic continued to decline and averaged 45.67%, down 2.11 p.p. against Q4 2020 (47.78%).
Proportion of spam in global email traffic, Q4 2020 and Q1 2021 (download)
The highest percentage of junk mail was recorded in January (46.12%). This is 0.71 p.p. less than the lowest figure in 2020 (46.83%). The calmest month was March, in which spam accounted for only 45.10% of all emails.
In the Runet, the average share of spam was also lower than in Q4 48.56% versus 50.25%. As was generally the case worldwide, the most turbulent month of the reporting period was January (49.76%), and the quietest was March (47.17%). In contrast to the global picture, January’s share of spam in the Runet was 1.30 p.p. higher than December’s (49.76% versus 48.46%).
Proportion of spam in Runet mail traffic, Q4 2020 and Q1 2021 (download)
Sources of spam by country
In 2020, Russia and Germany led the pack by volume of outgoing spam. In Q1 2021, they remained out in front: Russia accounted for 22.47% of spam, and Germany’s share was 14.89%. Third place went to the US (12.98%), and fourth to China (7.38%).
Sources of spam by country, Q1 2021 (download)
The Netherlands (4.18%) ranked fifth, followed by France (3.69%) and Spain (3.39%). Poland (2.39%), Brazil (2.37%) and Japan (2.23%) round out the Top 10.
Malicious mail attachments
In Q1 2021, Kaspersky solutions detected 38,195,315 malicious mail attachments. This is almost 3 million fewer than in the last three months of 2020. That said, the number of attachments blocked by Mail Anti-Virus grew during the quarter.
Number of Mail Anti-Virus triggerings, Q4 2020 and Q1 2021 (download)
Malware families
The most common Trojans detected by our solutions in mail attachments came from the Agensla family (8.91%). These malicious programs specialize in stealing credentials from browsers, as well as from mail and FTP clients. In second place came exploits for the CVE-2017-11882 vulnerability in the Microsoft Equation Editor component, which were detected in 6.38% of cases. Third position this time was taken by Trojans from the Badun family (5.79%). Malicious programs disguised as e-documents are detected with this verdict. Malware from the Badun family most often spreads through archives.
Top 10 malware families in mail traffic, Q1 2021 (download)
Fourth place went to SAgent (4.98%) — documents containing a VBA script that runs PowerShell to covertly download other malware. The fifth- and sixth-placed families are Taskun (3.79%) — programs that create malicious tasks in Windows Task Scheduler, and ISO (3.69%) — malicious disk images distributed by email. In seventh place is the Noon spyware (2.41%), which steals passwords from browsers and reads keystrokes. In eighth is the Crypt family (2.16%), which consists of highly obfuscated or encrypted software. The Top 10 is rounded out by Androm backdoors (2.05%) and worms coded in Visual Basic (1.66%).
Top 10 malicious attachments, Q1 2021 (download)
The Top 10 most common malicious attachments in Q4 corresponds exactly to the ranking of families. This suggests that each of the above-described families was widespread largely due to one member.
Countries targeted by malicious mailings
Our solutions registered the largest number of attempts to open malicious attachments in Spain (8.74%). This country was the top malicious mailing target throughout 2020, and held on to first place in this reporting quarter. Italy (7.59%) moved up to second place, and third place went to Germany (5.84%).
Countries targeted by malicious mailings, Q1 2021 (download)
In fourth position in Q1 was the UAE (5.25%), with Russia (4.88%) closing out the Top 5.
Statistics: phishing
In Q1 2021, our Anti-Phishing system prevented 79,608,185 attempted redirects to fraudulent websites. 5.87% of Kaspersky users encountered phishing, and 695,167 new masks were added to the anti-phishing databases.
Geography of phishing attacks
This quarter, phishing attacks affected a relatively small proportion of our users, both overall and in specific countries. The leader was France, where 9.89% of all users of Kaspersky solutions tried to follow a fraudulent link at least once during the reporting period.
Distribution of phishing attacks by country, Q1 2021 (download)
Israel placed second and Hungary third, where 8.45% and 8.27% of users, respectively, encountered phishing pages. Meanwhile, Brazil (7.94%), which topped the rating in 2020, only managed ninth position in Q1.
Top-level domains
As usual, the largest share of phishing sites that users attempted to visit in the period January–March 2021 were located in the .com domain zone (32.80%). The second most popular domain among scammers this time around was .xyz (11.38%). Bronze goes to the .tk domain zone (3.24%), belonging to the Tokelau Islands, a dependent territory of New Zealand, in the Pacific Ocean. Tokelau domains are cheap to rent, and so popular with phishers.
Top-level domain zones most commonly used for phishing, Q1 2021 (download)
Also prevalent this quarter were phishing sites that were not assigned domain names (2.78%). Such resources were the fourth most popular. In fifth spot, just 0.01 p.p. behind, was the Russian domain .ru (2.77%).
Organizations under attack
The rating of organizations targeted by phishers is based on the triggering of the deterministic component in the Anti-Phishing system on user computers. The component detects all pages with phishing content that the user has tried to open by following a link in an email message or on the web, as long as links to these pages are present in the Kaspersky database.
The Top 10 organizations used by phishers as bait remained practically unchanged in Q1 relative to 2020. Online stores (15.77%) still lead the way, followed by global internet portals (15.50%) and banks (10.04%). Fraudsters’ continued targeting of users of electronic trading platforms is explained by the pandemic-related restrictions that remained in force in many countries this quarter.
Distribution of organizations targeted by phishers, by category in Q1 2021 (download)
Conclusion
In Q1 2021, we largely saw a continuation of the 2020 trends. Cybercriminals are still actively using the COVID-19 theme to entice potential victims. And as coronavirus vaccination programs have been rolled out, spammers have adopted it as bait. Corporate account hunters continue to hone their techniques to make their emails as convincing as possible. Meanwhile, phishers who prey on personal accounts are still actively spoofing the websites of online stores, which have risen in popularity due to the pandemic.
Attackers will likely carry on exploiting the COVID-19 vaccination topic in Q2. Moreover, we can expect new fraudulent schemes to emerge. Scams related to compensation for damages caused to individuals and companies worldwide will not go away any time soon, too. Moreover, Q2 may see an associated rise in the number of fraudulent schemes offering payments from governments or other structures. And as the summer season approaches, an increase in the number of emails related to tourism is possible; however, due to the pandemic, it is likely to be small. On the other hand, cybercriminals will almost certainly continue to actively hunt corporate account credentials, exploiting the fact that many companies are still in remote working mode and communication among employees is predominantly online.
如有侵权请联系:admin#unsafe.sh