For more than ten years, we’ve been exploring iPhone backups, both local and iCloud, and we know a lot about them. Let’s reveal some secrets about the different types of backups and how they compare to each other.
Full file system acquisition is probably the best method delivering the most complete data set, but there’s a catch. iPhone backups (both local and iCloud) may contain some data that is not available from the iPhone anymore, and there is no way to recover from the device. Also, there could be several devices connected to the same iCloud account and the data is collected from all of them (if synchronization is enabled, of course). Finally, some records (notes and media files in particular) remain available in iCloud for quite some time (typically one to three weeks) even after they disappear from the Recently deleted folder.
Apart from the device itself, there can be several other sources of data:
- Local (iTunes) backups without a password
- Local (iTunes) backups protected with a password
- iCloud backups
- iCloud synced data (regular)
- iCloud synced data (“end to end” encrypted)
Note that we put encrypted and non-encrypted iTunes backups into different categories, and there is a reason for that. Encrypted backups contain significantly more data than unencrypted ones; in particular, they have Safari browsing history, Health data and keychain. Well, the keychain is always there, but it cannot be obtained from backups that have no password set.
What about iCloud backups? The closest match are non-encrypted local backups. Neither of those contain the following data:
- Safari browsing history
- Maps data
- Call log
- Health data
Anything else? You may also miss Messages (both SMS and iMessage) and media files (pictures and videos).
The reason? Depending on iCloud settings on your device, this data may be synced directly with iCloud, see Use Messages in iCloud and Set up and use iCloud Photos. In that case the synced data is not included in iCloud backups. What does iCloud back up? explains it further:
When you use Messages in iCloud or turn on iCloud Photos, your content is automatically stored in iCloud. That means that they’re not included in your iCloud Backup.
But wait, there is more:
Your iPhone, iPad, and iPod touch backups only include information and settings stored on your device. They do not include information already stored in iCloud such as Contacts, Calendars, Bookmarks, Notes, Reminders, Voice Memos, Messages in iCloud, iCloud Photos, and shared photos. Some information is not included in an iCloud backup but can be added to iCloud and shared across multiple devices like Mail, Health data, call history, and files you store in iCloud Drive.
In fact, this information is only partially correct. Regardless of the settings, Contacts, Calendars, Bookmarks, Notes, Reminders and Voice Memos are still stored in iCloud backups.
There is something special about the call history. If you follow our news, you might remember that we covered it almost five years ago:
- iPhone User? Your Calls Go to iCloud
- iOS Call Syncing: How It Works
- “We take privacy very seriously” – Apple, we do not buy it, sorry
So this is the story: the call history is synced to the cloud, but there was never a setting to control that behavior. There is no such setting even now in iOS 14.6. We learned how to download these call logs in Elcomsoft Phone Breaker, but with the release of iOS 13, they just stopped syncing. Or at least it looked like it. Some people including some of my colleagues reported they get the sync working, while the others (including myself) cannot get it to work. I have a dozen devices connected to my iCloud account, and none of them sync the call logs at the moment. Maybe the reason is that they all run different versions of iOS, ranging from iOS 10 to 14.7 beta. There is also a chance that call logs are synced directly between devices (so true end-to-end encryption, like Screen Time statistics) when they are physically close to each other and maybe connected to the same wireless network (if they aren’t using Wi-Fi Direct), but it never worked for me during the last year or so. And the setting is still missing on the iPhone (although we can see Apple Watch here, which is quite interesting; as far as we know, Apple Watch data only syncs with the phone it is paired with, but not directly to the cloud).
iCloud security overview gives some further explanation on “end-to-end” encryption:
End-to-end encryption provides the highest level of data security. Your data is protected with a key derived from information unique to your device, combined with your device passcode, which only you know. No one else can access or read this data.
These features and their data are transmitted and stored in iCloud using end-to-end encryption:
- Apple Card transactions (requires iOS 12.4 or later)
- Home data
- Health data (requires iOS 12 or later)
- iCloud Keychain (includes all of your saved accounts and passwords)
- Maps Favorites, Collections and search history (requires iOS 13 or later)
- Memoji (requires iOS 12.1 or later)
- Payment information
- QuickType Keyboard learned vocabulary (requires iOS 11 or later)
- Safari History and iCloud Tabs (requires iOS 13 or later)
- Screen Time
- Siri information
- Wi-Fi passwords
- W1 and H1 Bluetooth keys (requires iOS 13 or later)
To access your data on a new device, you might have to enter the passcode for an existing or former device.
Messages in iCloud also uses end-to-end encryption. If you have iCloud Backup turned on, your backup includes a copy of the key protecting your Messages. This ensures you can recover your Messages if you lose access to iCloud Keychain and your trusted devices. When you turn off iCloud Backup, a new key is generated on your device to protect future messages and isn’t stored by Apple.
The last paragraph is intriguing. Looks like the key is stored in the keychain (and not synced to iCloud keychain), and so can be decrypted only by the very same device. It’s hard to verify, unfortunately.
What’s the deal about “end-to-end encryption” in iCloud? If you ever parsed Apple warrant returns, you know that such data is not there, which means that Apple has no decryption keys for it. Is it still possible to access this data from iCloud? Yes, with our software.
As usual, the devil is in the details. To access end-to-end encrypted data, not only will you have to supply the login credentials and pass 2FA, but also provide the passcode of one of the trusted devices.
Note that this is the only way to access (download and decrypt) Apple Maps data, Health, keychain, messages, Safari browsing history and some ScreenTime data.
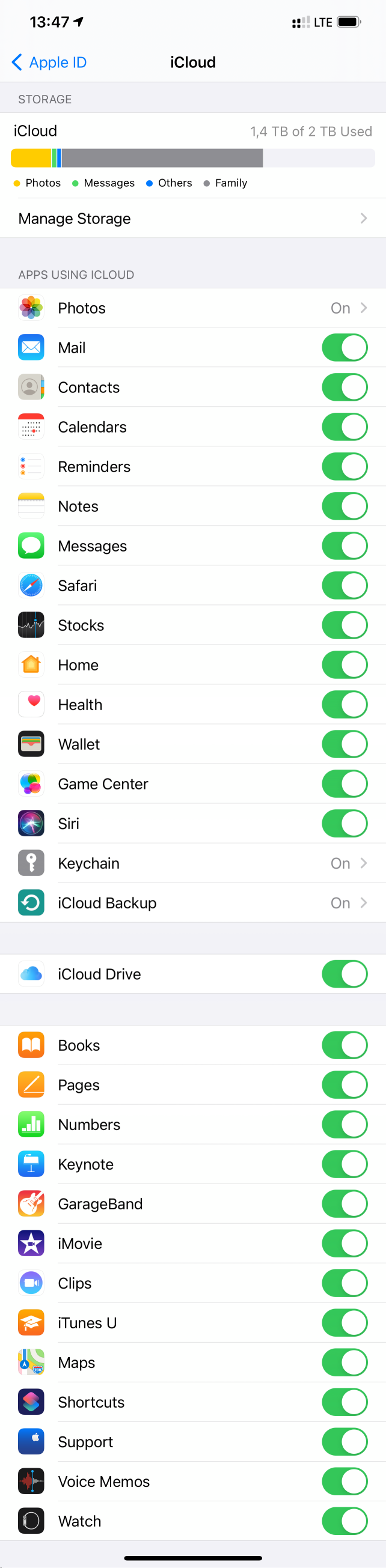
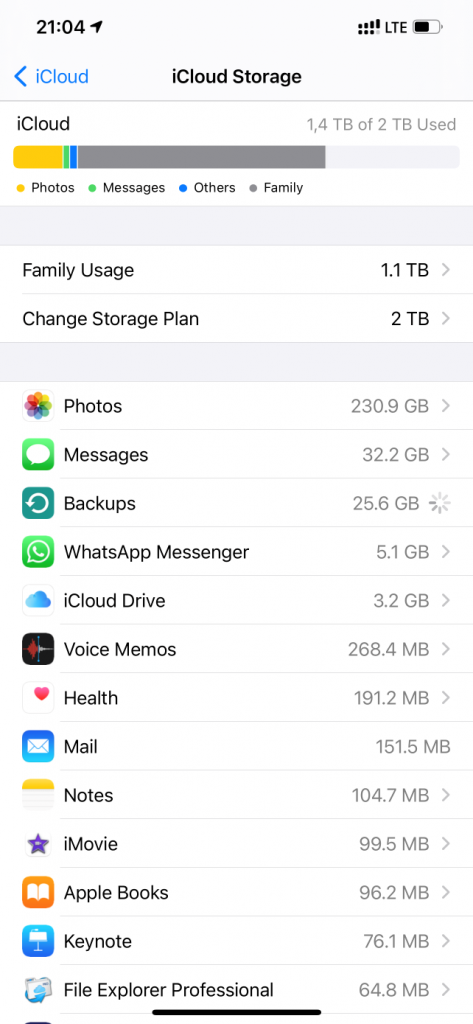
Last but not least, you have a certain degree of control on what data is included in iCloud backups via Settings | {Apple ID} | iCloud | Manage Storage. Here you can see the types of data stored in your iCloud account in backups, synced data and files in iCloud drive.
If you go further to Backups | {Device}, you can specify apps that are allowed to back up their data as part of iCloud backups.
I played with these options a bit and was able to cut the size of my iCloud backup from about 140 GB to 16 GB on the first attempt, and then to just 5 GB. A smaller backup will be much easier and faster to restore if something goes wrong. Still, I have 230GB worth of photos and videos and 32GB of messages (that’s including attachments) stored in iCloud. He is the comparison; a fresh local (iTunes) backup goes first; 280 GB:
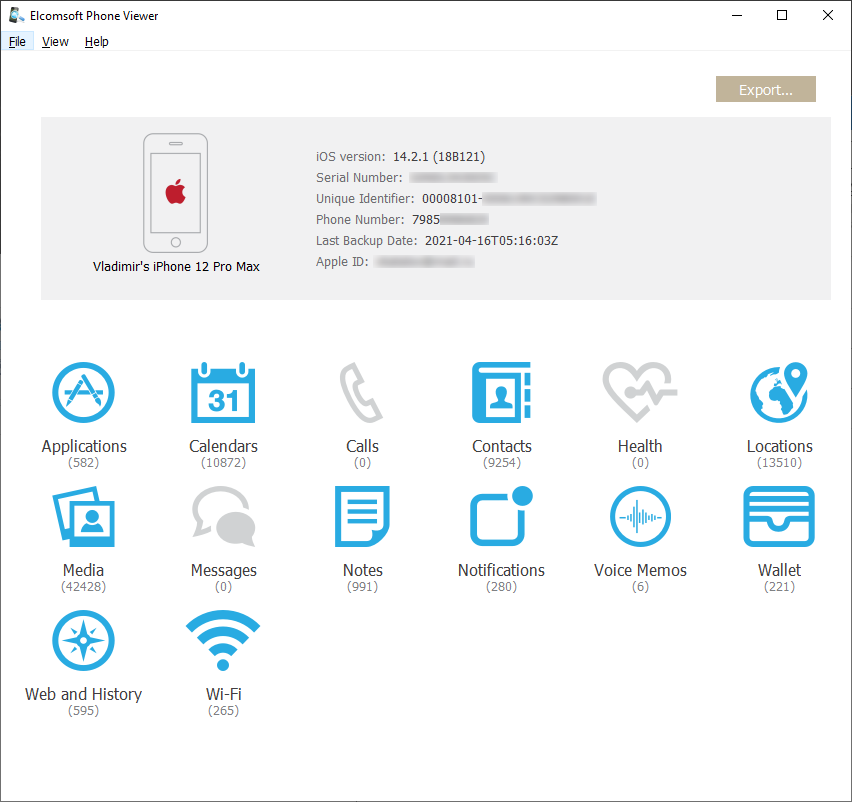
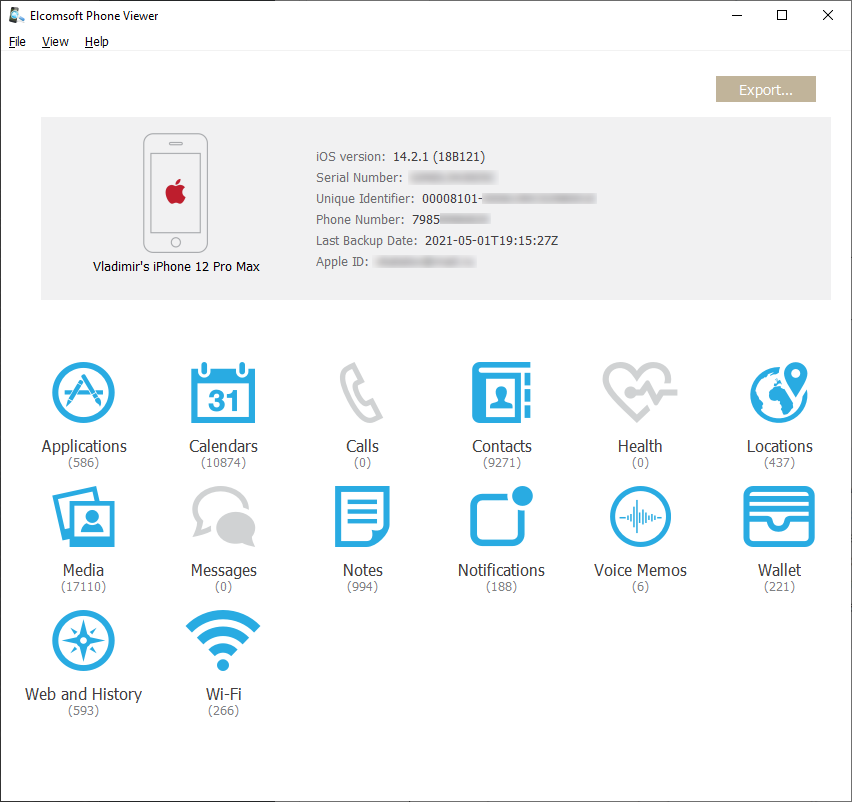
An iCloud backup made over a month ago, 140 GB:
The next one, two weeks later (note the reduced number of media files, and so the locations; 15 GB):
And the latest one, created yesterday (5 GB only):
As you can see, none of the iCloud backups contain Health data, messages or calls, yet you can still download them from synced data storage.
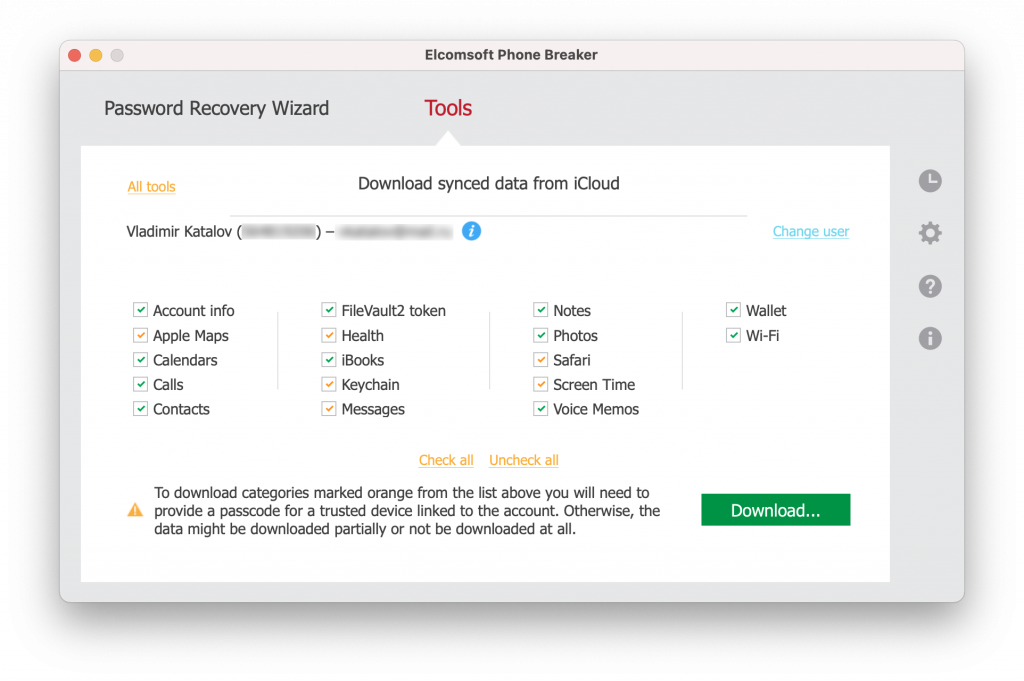
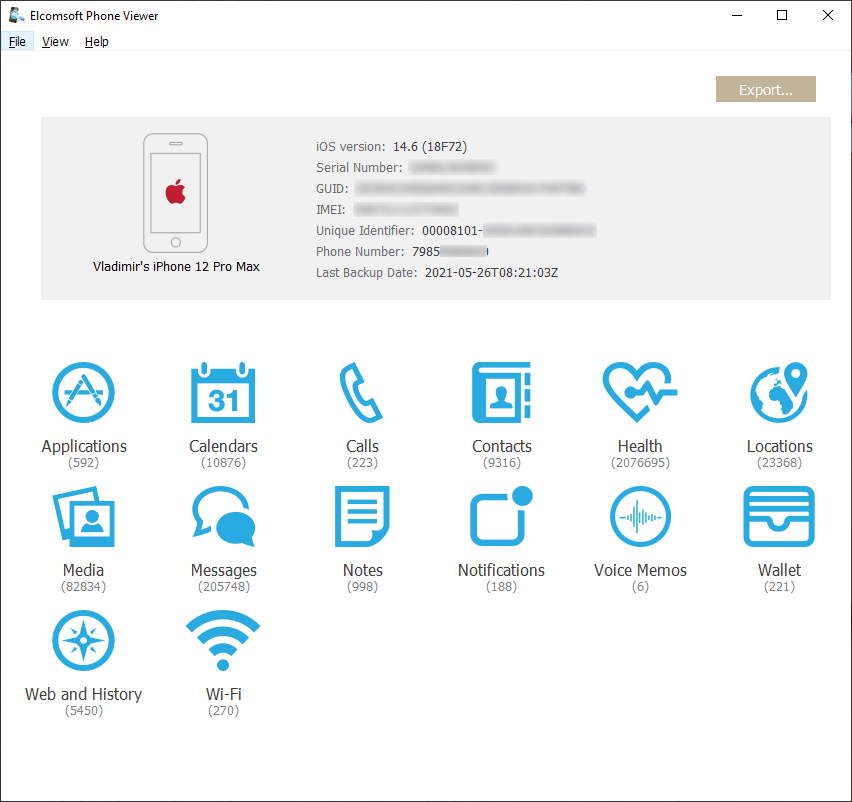
To conclude: make sure to collect everything you can access including all the backups mentioned above, plus the full file system if possible, plus any data from other sources such as laptops and desktops, as well as Apple Watch devices. And then carefully analyze everything you have got to extract the most critical evidence. Below are some screen shots of the data opened in Elcomsoft Phone Viewer extracted from an iCloud backup and from iCloud synced storage. They are two weeks apart, so the data itself should be very similar, yet the content of cloud backups and synced data is quite different with many overlaps and some unique data in either source. Both are extracted with the same tool: Elcomsoft Phone Breaker.
REFERENCES:
![]()
Elcomsoft Phone Breaker
Gain full access to information stored in FileVault 2 containers, iOS, Apple iCloud, Windows Phone and BlackBerry 10 devices! Download device backups from Apple iCloud, Microsoft OneDrive and BlackBerry 10 servers. Use Apple ID and password or extract binary authentication tokens from computers, hard drives and forensic disk images to download iCloud data without a password. Decrypt iOS backups with GPU-accelerated password recovery.
![]()
Elcomsoft Phone Viewer
Elcomsoft Phone Viewer is a fast, lightweight forensic viewer for quickly accessing information extracted from mobile backups. Supporting a variety of platforms and data formats, the tool can display information extracted from local and cloud iOS backups and Microsoft Accounts. Password-protected iTunes backups can be automatically decrypted and analyzed without using third-party tools.
如有侵权请联系:admin#unsafe.sh