2021-05-31 19:00:35 Author: securelist.com(查看原文) 阅读量:187 收藏
The statistics presented here draw on detection verdicts returned by Kaspersky products as provided by users who consented to share statistical data.
Quarterly figures
According to Kaspersky Security Network, in the first quarter we saw:
- 1,451,660 detected mobile installation packages, of which
- 25,314 packages were related to mobile banking Trojans,
- 3,596 packages were mobile ransomware Trojans.
- The majority (61.43%) of the discovered threats belonged to the adware category.
Quarterly highlights
While it is a year since the world entered a lockdown amid the coronavirus pandemic, our statistics suggest that the topic has only slightly decreased in relevance, if at all. There are still threats in the wild which names use the word “corona” in various combinations. For instance, adware that belongs to the AdWare.AndroidOS.Notifyer family was distributed in the first quarter under the guise of a file named ir.corona.viruss.apk, and Backdoor.AndroidOS.Ahmyth.f open-source backdoors bore the name com.coronavirus.info. Other notable names were tousanticovid.apk (actually the Hqwar dropper), and covid_19_radar.apk (AdWare.AndroidOS.Ewind.kp).
However, Q1 2021 was not only memorable for the exploitation of the pandemic theme. The emergence of the first-ever Trojan-Gamethief-category mobile Trojan might have been the most interesting event of the quarter. This type of Trojan is specific to the PC, a popular platform for game services and in-app purchases, which, unlike consoles, makes it is relatively easy to install malware. Therefore, a black market for game accounts and Trojans that work to satisfy the demand have been around for a long time. Real-money purchases are no less popular in mobile games, but we had never seen an attempt at hijacking an account in any game. However, eleven years after the first Android-specific Trojan appeared, we discovered a malicious file designated as HEUR:Trojan-Spy.AndroidOS.Agent.xy, which targets PlayerUnknown’s Battlegrounds (PUBG) accounts.
The Trojan checks for a com.tencent.ig package on the device, i.e. the mobile version of PUBG.
If successful, the Trojan locates configuration files that contain account credentials and extracts the contents of these files.
Then, the Trojan uses superuser privileges to search for credentials in the game files and the OS protected storage.
The targets are not limited to PUBG: the Trojan is after Facebook and Twitter accounts and even attempts to find out the linked Gmail credentials.
Mobile threat statistics
Kaspersky detected 1,451,660 malware installers in Q1 2021, a decrease of 655,020 from Q4 2020 but an increase of 298,998 year on year.
Number of detected malicious installation packages, Q1 2020 — Q1 2021 (download)
Distribution of detected mobile apps by type
Distribution of newly detected mobile applications across types, Q1 2021 and Q4 2020 (download)
Adware accounted for the overwhelming majority (61.43%) of all threats discovered in Q1 2021, a decrease of 12 percentage points from Q4 2020. The malicious objects we most frequently encountered came from the AdWare.AndroidOS.Ewind family (65.17% of all detected threats in the category), AdWare.AndroidOS.HiddenAd (17.82%) and AdWare.AndroidOS.FakeAdBlocker (11.07%).
These were followed by RiskTool potentially unwanted applications (PUAs), up by 2 percentage points to 15.43%. Nine out of ten apps of the type that were discovered belonged to the SMSreg family.
Non-specific Trojans came third with 8.27%, their share increasing by 5 percentage points. The largest contributors were the Agent family with 45.30%, Boogr with 29.88% and Plangton with 8.11%.
Twenty most common mobile malware programs
Note that the malware rankings below exclude riskware or PUAs, such as RiskTool or adware.
| Verdict | %* | |
| 1 | DangerousObject.Multi.Generic | 32.10 |
| 2 | Trojan.AndroidOS.Boogr.gsh | 12.24 |
| 3 | Trojan-SMS.AndroidOS.Agent.ado | 6.43 |
| 4 | DangerousObject.AndroidOS.GenericML | 4.98 |
| 5 | Trojan-Dropper.AndroidOS.Hqwar.cf | 4.13 |
| 6 | Trojan.AndroidOS.Agent.vz | 3.50 |
| 7 | Trojan-Downloader.AndroidOS.Necro.d | 3.48 |
| 8 | Trojan.AndroidOS.Triada.el | 2.91 |
| 9 | Trojan-Downloader.AndroidOS.Helper.a | 2.79 |
| 10 | Trojan.AndroidOS.Whatreg.b | 2.32 |
| 11 | Trojan-Downloader.AndroidOS.Gapac.c | 2.27 |
| 12 | Trojan.AndroidOS.Triada.ef | 2.26 |
| 13 | Trojan.AndroidOS.MobOk.ad | 2.24 |
| 14 | Trojan.AndroidOS.LockScreen.ar | 2.17 |
| 15 | Trojan-Downloader.AndroidOS.Agent.ic | 2.17 |
| 16 | Trojan-SMS.AndroidOS.Agent.acv | 2.16 |
| 17 | Trojan-Banker.AndroidOS.Agent.eq | 1.98 |
| 18 | Trojan.AndroidOS.Hiddad.fw | 1.91 |
| 19 | Exploit.AndroidOS.Lotoor.be | 1.68 |
| 20 | Trojan-Dropper.AndroidOS.Hqwar.di | 1.65 |
* Unique users attacked by this malware as a percentage of all users of Kaspersky mobile solutions that were attacked.
First place in the rankings for Q1 as usual went to DangerousObject.Multi.Generic (32.10%), the verdict we use for malware detected with cloud technology. Cloud technology is triggered whenever the antivirus databases lack data for detecting a piece of malware, but the company’s cloud already contains information about the object. This is essentially how the latest malware types are detected.
Second and fourth places went to Trojan.AndroidOS.Boogr.gsh (12.24%) and DangerousObject.AndroidOS.GenericML (4.98%). These verdicts are assigned to files recognized as malicious by our machine-learning systems.
Members of the SMS Trojan family Agent, Agent.ado (6.43%) and Agent.acv (2.16%), occupied third and sixteenth places. In the overwhelming majority (90%) of the cases, these varieties were discovered with Russian users. These malicious programs are dangerous in that they both subscribe to paid services unbeknownst to the victim and enable cybercriminals to control the victim’s bank account via an SMS banking service.
Fifth and twentieth places were taken by members of the Trojan-Banker.AndroidOS.Hqwar family: Hqwar.cf (4.13%) and Hqwar.di (1.65%). These droppers remain steadily popular, with some 100,000 unique users attacked per quarter. As with SMS Trojans, this type of malware was most frequently (65%) detected with Russian mobile users.
Sixth place went to Trojan.AndroidOS.Agent.vz (3.5%), which downloads a payload while serving as payload for another type of malware. Cybercriminals create this type of chains to make sure that the malware remains on the device: even if the victim removes one of the links in the chain, another will ensure repeat infection.
Seventh and ninth places went to Trojan-Downloader.AndroidOS.Necro.d (3.48%) and Trojan-Downloader.AndroidOS.Helper.a (2.79%). These Trojans are part of the kind of chain described above, which will result in persistent infection and obtrusive ads being shown on the screen of the device. Other members of the same infection sequence are Trojan.AndroidOS.Triada.el (2.91%) and Trojan.AndroidOS.Triada.ef (2.26%), which occupied eighth and twelfth places, respectively. They are designed for downloading suitable exploits, which the Necro and Helper Trojans can use for gaining a foothold on the device.
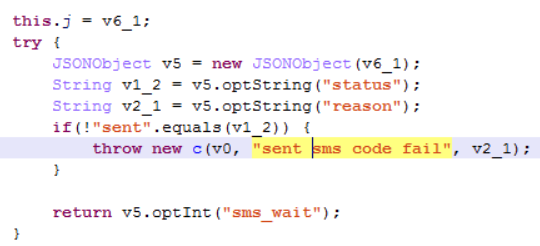
Tenth place went to the quarter’s novelty, Trojan.AndroidOS.Whatreg.b (2.32%), which deserves a story of its own. The creators of that malware program did their best to reverse-engineer the WhatsApp registration protocol and the process of data exchange with the server to implement registration of new accounts on command.
Trojan code with WhatsApp server lines
The cybercriminals can use accounts thus obtained in any way they wish, e.g., for sending spam, or sell these on the black market. The latter presents a particular danger to the victim, as WhatsApp registration uses a cell number, so any illegal activity involving the account, such as distribution of prohibited content, will highlight the unsuspecting user to law enforcement. Notably, 85% of the users who had the Trojan were located in Russia.
The second score of verdicts begins with Trojan-Downloader.AndroidOS.Gapac.c (2.27%). This Trojan, like some of those mentioned above, is part of an infection chain, downloading other modules. It is more primitively designed though, with a C2 center encrypted with a basic algorithm that converts the digit equivalents of ASCII characters.
Trojan.AndroidOS.MobOk.ad (2.24%), a family capable of subscribing the user to paid services, came thirteenth. MobOk malware programs attempted to attack mobile users in Russia more frequently than in any other country.
Trojan.AndroidOS.LockScreen.ar (2.17%), in fourteenth place, has been part of the twenty most common mobile malware types for several quarters. This primitive virus locks the device screen to prevent normal use.
Trojan-Downloader.AndroidOS.Agent.ic (2.17%), another malware tool that downloads other applications when commanded by cybercriminals, occupied fifteenth place.
Seventeenth place went to the Trojan-Banker.AndroidOS.Agent.eq verdict (1.98%). It is assigned to various financial threat families, in particular, Wroba, Asacub and many other bankers.
Trojan.AndroidOS.Hiddad.fw (1.91%) was eighteenth. This type of malware is designed for taking root on the device and displaying mobile banners.
Exploit.AndroidOS.Lotoor.be (1.68%), a local exploit used for elevating privileges on the device to superuser, came nineteenth. Widespread families, such as Necro, Helper and Triada, use its services to establish themselves on the device and get access to the file system, which pushed Lotoor.be onto the list of twenty.
Geography of mobile threats
Map of infection attempts by mobile malware, Q1 2021 (download)
Ten countries with the largest shares of users attacked by mobile malware
| Country* | %** | |
| 1 | Iran | 25.80 |
| 2 | China | 16.39 |
| 3 | Saudi Arabia | 13.99 |
| 4 | Algeria | 13.22 |
| 5 | Morocco | 10.62 |
| 6 | Turkey | 10.43 |
| 7 | Yemen | 10.05 |
| 8 | Nigeria | 9.82 |
| 9 | India | 8.08 |
| 10 | Kenya | 8.02 |
* Excluded from the rankings are countries with relatively few users of Kaspersky mobile security solutions (under 10,000).
** Share of unique users attacked as a percentage of all users of Kaspersky mobile security solutions in the country.
Iran led in terms of the share of attacked users in Q1 2021 with 25.80%. The most frequently encountered of all threats relevant to Iranians were the pestilent adware modules belonging to the AdWare.AndroidOS.Notifyer and AdWare.AndroidOS.Fyben families.
China came second with 16.39%, with Chinese users most frequently encountering RiskTool.AndroidOS.SmsPay and RiskTool.AndroidOS.Wapron PUA families. Both threat families target victim’s cell carrier accounts. The former can send short messages to make purchases inside games that use a questionable text message monetization scheme, and the latter sends text messages purportedly as payment for porn viewings.
In Saudi Arabia, which came third with 13.99%, users most commonly encountered AdWare.AndroidOS.HiddenAd and AdWare.AndroidOS.FakeAdBlocker adware.
Mobile banking Trojans
We found 25,314 mobile banking Trojan installers during the reporting period, a decrease of 8,528 from the previous quarter and a decrease of 16,801 year on year.
The largest contributors to these figures were the Trojan-Banker.AndroidOS.Agent (57.51% of all installation packages detected), Trojan-Banker.AndroidOS.Wroba (7.98%), and Trojan-Banker.AndroidOS.Gustuff (7.64%) families. Interestingly enough, the capabilities of Trojan-Banker.AndroidOS.Gustuff make it virtually the most dangerous financial Trojan, but it is not frequently seen in the wild.
Number of mobile banking Trojan installers detected by Kaspersky, Q1 2020 — Q1 2021 (download)
Ten most common mobile bankers
| Verdict | %* | |
| 1 | Trojan-Banker.AndroidOS.Agent.eq | 22.06 |
| 2 | Trojan-Banker.AndroidOS.Anubis.t | 11.01 |
| 3 | Trojan-Banker.AndroidOS.Svpeng.q | 9.67 |
| 4 | Trojan-Banker.AndroidOS.Asacub.ce | 5.62 |
| 5 | Trojan-Banker.AndroidOS.Asacub.snt | 5.03 |
| 6 | Trojan-Banker.AndroidOS.Anubis.n | 4.66 |
| 7 | Trojan-Banker.AndroidOS.Asacub.bv | 3.66 |
| 8 | Trojan-Banker.AndroidOS.Agent.ep | 3.56 |
| 9 | Trojan-Banker.AndroidOS.Hqwar.t | 3.43 |
| 10 | Trojan-Banker.AndroidOS.Agent.cf | 2.52 |
* Unique users attacked by this malware as a percentage of all Kaspersky mobile security solution users who encountered banking threats.
Members of the Asacub family occupied three positions out of ten among mobile bankers in Q1 2021, with the Asacub-like Trojan-Banker.AndroidOS.Agent.eq taking the lead with 22.06%.
Trojan-Banker.AndroidOS.Anubis family members, Anubis.t (11.01%) and Anubis.n (4.66%) were second and sixth, respectively. The family consists of classic mobile financial threats with a well-established set of features: access to Accessibility Services, phishing window display, two-factor authentication hacking and screenshotting. The family’s source code leaking into the public domain ensured its high popularity.
The long-familiar Trojan-Banker.AndroidOS.Svpeng.q came third with 9.67%.
Geography of mobile banking threats, Q1 2021 (download)
Ten countries with the largest shares of users attacked by mobile banking Trojans
| Country* | %** | |
| 1 | Japan | 1.59 |
| 2 | Turkey | 0.67 |
| 3 | Germany | 0.40 |
| 4 | Spain | 0.31 |
| 5 | France | 0.31 |
| 6 | Australia | 0.28 |
| 7 | Norway | 0.22 |
| 8 | South Korea | 0.19 |
| 9 | Italy | 0.16 |
| 10 | Finland | 0.12 |
* Excluded from the rankings are countries with relatively few users of Kaspersky mobile security solutions (under 10,000).
** Unique users attacked by mobile banking Trojans as a percentage of all Kaspersky mobile security solution users in the country.
Japan has the largest share of unique users attacked by mobile financial threats in Q1 2021, 1.59%. In 97% of cases, users in that country encountered Trojan-Banker.AndroidOS.Agent.ep.
Turkey followed by a wide margin with 0.67%. The most commonly encountered malware types in that country were again Agent.ep (17.85%), as well as Trojan-Banker.AndroidOS.Agent.ia (15.62%) and Trojan-Banker.AndroidOS.Cebruser.pac (15.05%).
Third came Germany (0.40%), where Trojan-Banker.AndroidOS.Agent.eq was the most widespread financial threat with 93%.
Mobile ransomware Trojans
We detected 3,596 mobile Trojan ransomware installers in Q1 2021, a decrease of 1,000 from Q4 2020 and a decrease of 743 year on year.
Number of mobile ransomware installers detected by Kaspersky, Q1 2020 — Q1 2021 (download)
Ten most common mobile ransomware varieties
| Verdict | %* | |
| 1 | Trojan-Ransom.AndroidOS.Pigetrl.a | 50.67 |
| 2 | Trojan-Ransom.AndroidOS.Small.as | 6.67 |
| 3 | Trojan-Ransom.AndroidOS.Rkor.an | 6.29 |
| 4 | Trojan-Ransom.AndroidOS.Congur.am | 6.21 |
| 5 | Trojan-Ransom.AndroidOS.Small.o | 2.74 |
| 6 | Trojan-Ransom.AndroidOS.Small.ce | 2.04 |
| 7 | Trojan-Ransom.AndroidOS.Rkor.snt | 1.83 |
| 8 | Trojan-Ransom.AndroidOS.Fusob.h | 1.52 |
| 9 | Trojan-Ransom.AndroidOS.Soobek.a | 1.41 |
| 10 | Trojan-Ransom.AndroidOS.Agent.bg | 1.23 |
* Unique users attacked by the malware as a percentage of all Kaspersky mobile security solution users attacked by ransomware Trojans.
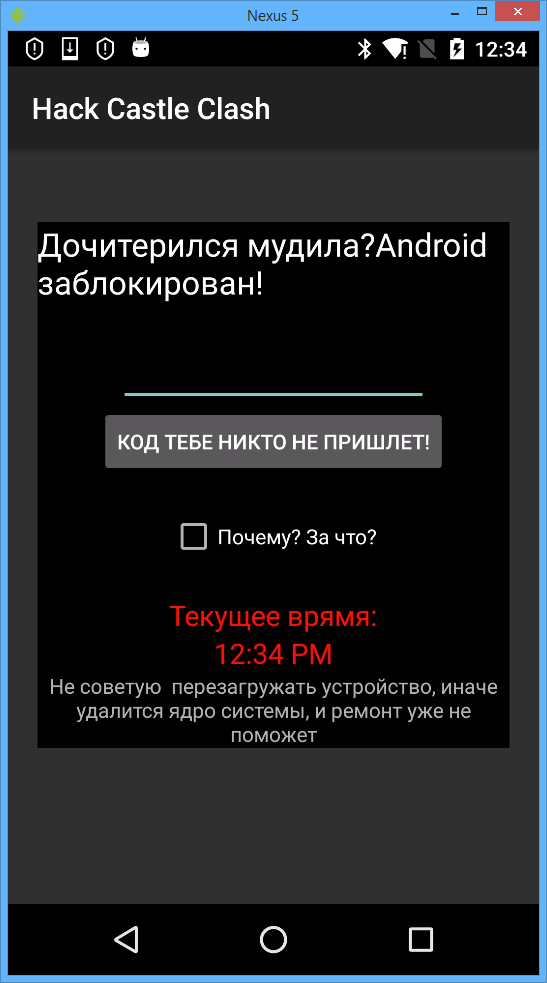
Trojan-Ransom.AndroidOS.Pigetrl.a led in the first quarter after attacking 50.67% of all users who faced the type of threat in question.
Pigetrl.a more closely resembles a nasty trick than a criminal money-making tool. Once a victim’s device is locked, the malware requests a code without providing a means of obtaining one. “No one is sending you a code!” being displayed on the screen suggests that this is as designed. In reality, the code is part of the Trojan body. In the screenshot above, it is “775”. A Pigetrl.a window will remain on the home screen after the device is unlocked, making removal difficult. This Trojan was first reported in 2018 and has not significantly changed since that time, still a toy in its creator’s hands.
The remaining places in the rankings were occupied by well-known ransomware types that are far more dangerous than Pigetrl.a. It should be mentioned, however, that both in terms of the number of attacked users and in terms of detected threats, mobile ransomware Trojans have been slowly losing ground.
Geography of mobile ransomware Trojans, Q1 2021 (download)
The ten countries with the largest shares of users attacked by mobile ransomware Trojans
| Country* | %** | |
| 1 | Kazakhstan | 0.25 |
| 2 | Kyrgyzstan | 0.17 |
| 3 | Colombia | 0.16 |
| 4 | China | 0.07 |
| 5 | Sweden | 0.06 |
| 6 | Saudi Arabia | 0.04 |
| 7 | Estonia | 0.04 |
| 8 | Moldova | 0.03 |
| 9 | Israel | 0.03 |
| 10 | Latvia | 0.03 |
* Excluded from the rating are countries with relatively few users of Kaspersky mobile security solutions (under 10,000).
** Unique users attacked by ransomware Trojans as a percentage of all Kaspersky mobile security solution users in the country.
In Kazakhstan, the country with the largest (0.25%) share of users attacked by ransomware, potential victims mostly encountered members of the Trojan-Ransom.AndroidOS.Rkor family.
In Kyrgyzstan, which followed with 0.17%, users were most frequently attacked by Trojan-Ransom.AndroidOS.Rkor and Trojan-Ransom.AndroidOS.Pigetrl.a.
如有侵权请联系:admin#unsafe.sh