2021-06-01 17:48:36 Author: blog.elcomsoft.com(查看原文) 阅读量:191 收藏
How to break ‘strong’ passwords? Is there a methodology, a step by step approach? What shall you start from if your time is limited but you desperately need to decrypt critical evidence? We want to share some tips with you, this time about the passwords saved in the Web browsers on most popular platforms.
Breaking passwords becomes harder every day. Vendors are making their apps increasingly tough to break by hardening password protection. They are doing their best to slow down the attacks, often going as far as implementing special tricks targeting GPU attacks specifically, making password attacks run at terribly low speeds. What are your options then? Stored passwords and passwords re-use are often the key. Get the low-handing fruits first by collecting the user’s passwords that are saved in their Web browser.
Windows
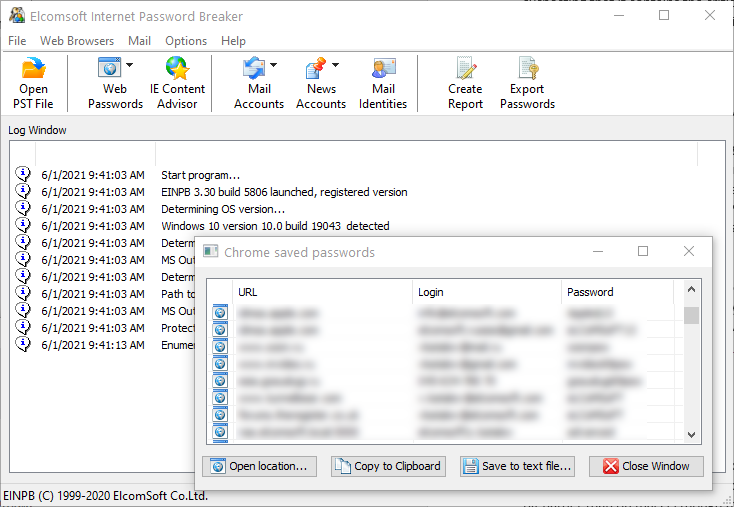
Google Chrome? We’ve got you covered. Microsoft Edge (or old-school Internet Explorer)? No problem as well. Mozilla Firefox and Opera? We support them too, as well as several popular Chinese browsers (Tencent QQ Browser, UCWeb UC Browser, Qihoo 360 Safe Browser) and even Tor. All these browsers have the ability to save passwords once they are entered on a Web sites, and we know how to extract and decrypt them. You’ll need an authenticated session to extract most of these passwords from the user’s Windows account. Elcomsoft Internet Password Breaker can also collect POP3/IMAP/SMTP/NNTP passwords, as well as the passwords saved in Microsoft Outlook, Outlook Express, Windows Mail and Windows Live Mail, and Thunderbird.
macOS
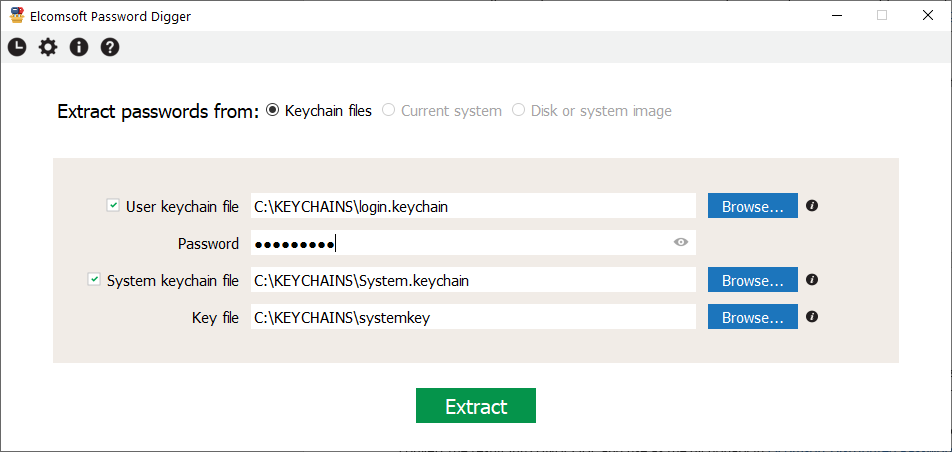
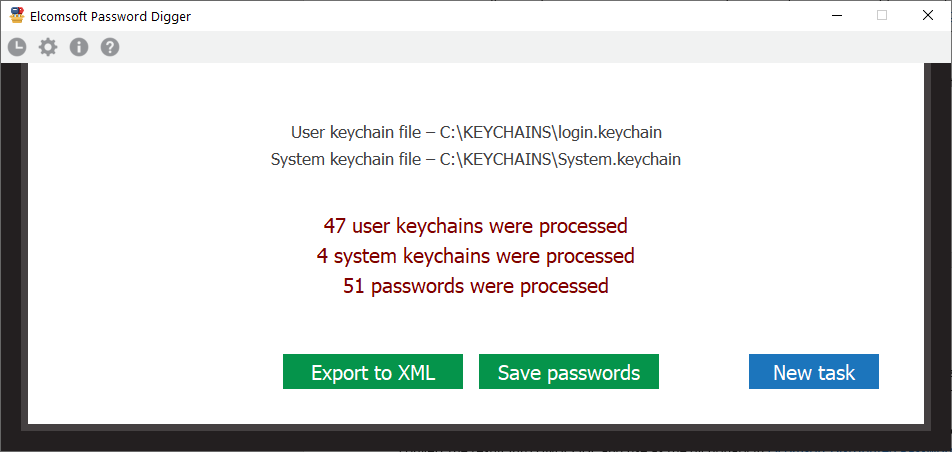
In macOS, the passwords are stored in the user’s keychain. To extract them, you will need the keychain database itself (and so physical access to the computer with root privileges), as well as the user’s password. That’s it, the passwords will be extracted and decrypted in seconds, just use Elcomsoft Password Digger (and read Digging Mac OS Keychains to get some insides).
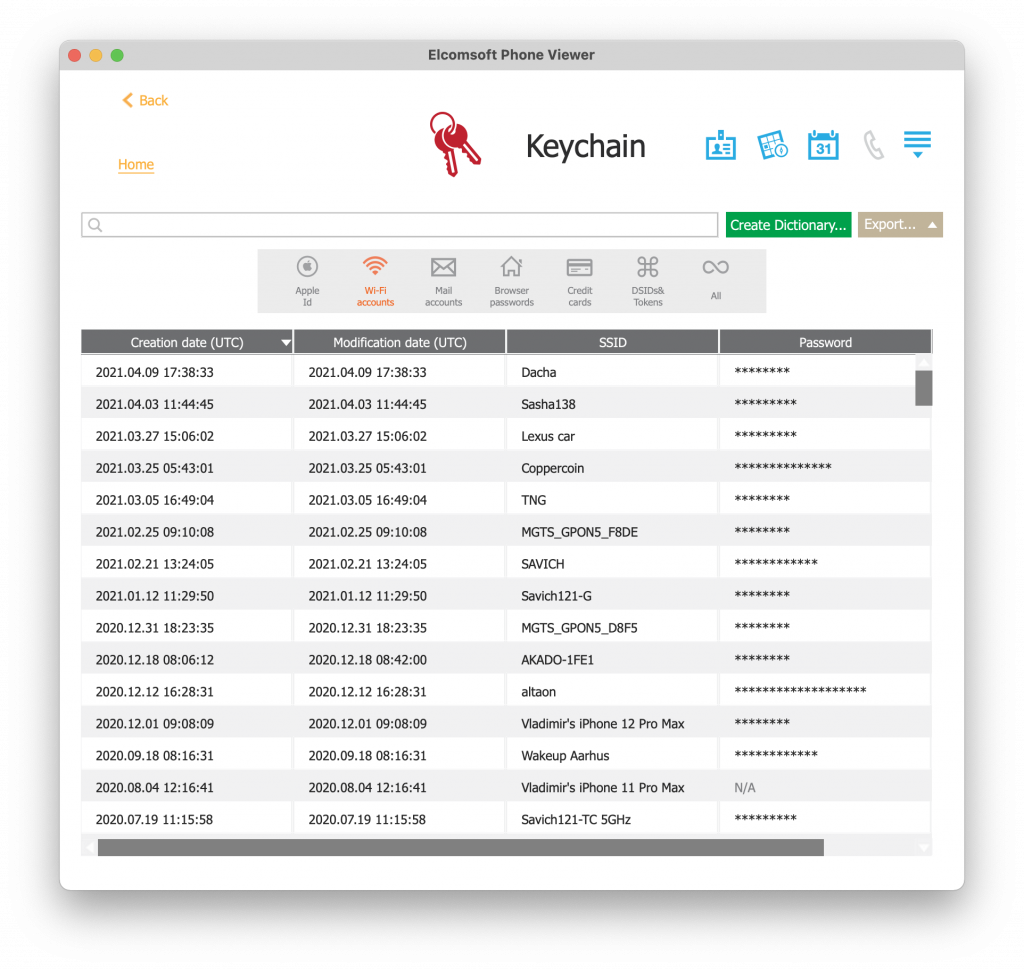
iOS/iPadOS
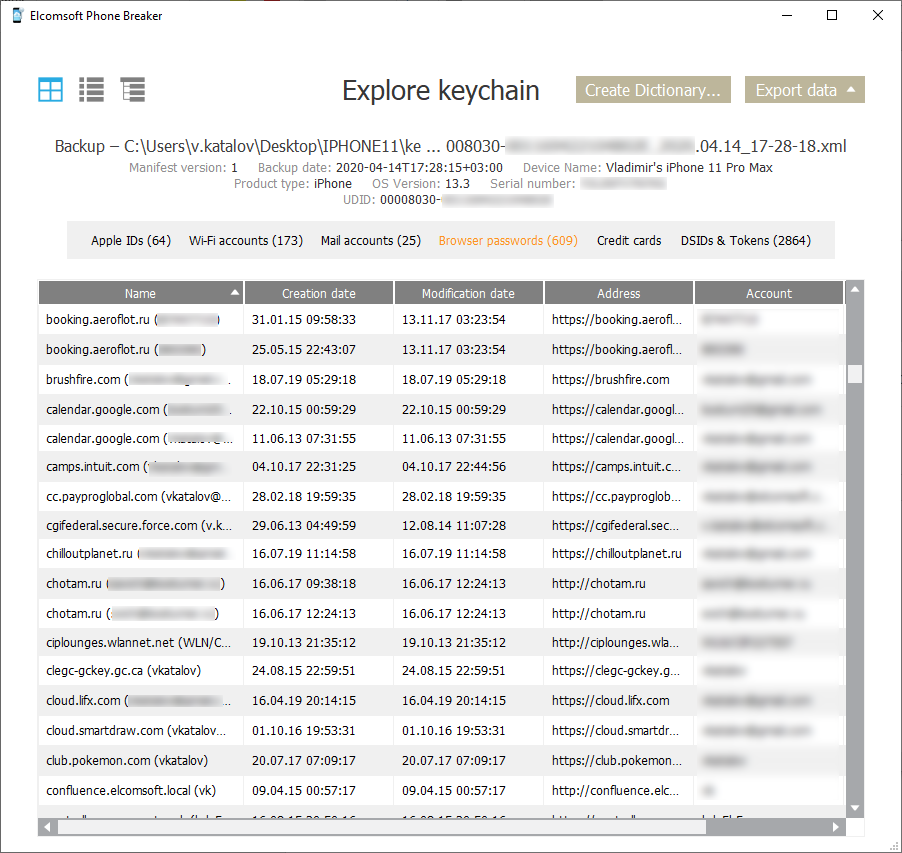
On Apple mobile devices, the passwords along with other sensitive data such as credit card numbers, encryption keys, certificates etc. are saved in the keychain, pretty similar to macOS. The extraction may be more difficult compared to macOS. The easiest way to access stored passwords is to create a password-protected device backup with iTunes (Windows), Finder (Mac), or any forensic software that supports logical acquisition, then using Elcomsoft Phone Breaker or Elcomsoft Phone Viewer to decrypt the keychain and view the passwords (either tool will work).
Clouds
Cloud accounts are another excellent source of passwords. Four years ago, we discovered a way to extract cloud keychain from Apple iCloud (see Acquiring Apple’s iCloud Keychain). While this method has some limitations (you need authentication credentials and the user’s screen lock passcode), it is really worth it: iCloud saves tons of passwords, and most of Apple users (especially those with more than one Apple device) have it enabled. Use Elcomsoft Phone Breaker to download iCloud keychain as well as many other “end-to-end encrypted” data categories.
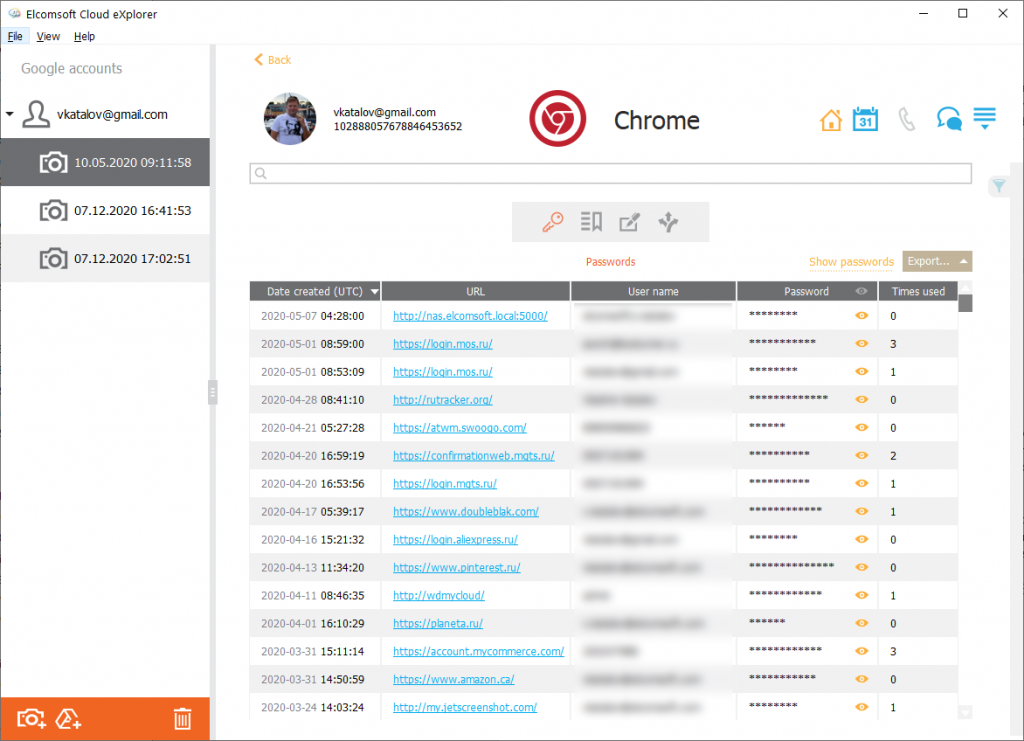
Google Chrome, the most popular browser in Windows and Android devices, also saves passwords in the cloud, specifically into the user’s Google Account. The passwords don’t have any special protection and can be easily extracted with Elcomsoft Cloud eXplorer (of course, you’ll authentication credentials to sign in to the user’s Google Account).
What’s next?
All of the tools mentioned above not only allow decrypting the passwords stored in Web browsers but export them into ‘wordlists’ (or ‘dictionaries’). You will have to do some homework: frequency sorting, deduplication etc., and remove passwords that are obviously incorrect (sometimes ‘false matches’ are returned such as base64-wrapped binary data). Then convert the result into Unicode and use as the dictionary in Elcomsoft Distributed Password Recovery.
REFERENCES:
![]()
Elcomsoft Cloud eXplorer
Learn what Google knows about you! Download information directly from the Google Account with or without a password. Elcomsoft Cloud Explorer enables over-the-air acquisition for a wide range of Google services including Contacts, Hangouts Messages, Google Keep, Chrome browsing history, search history and page transitions, Calendars, images, location and a lot more.
![]()
Elcomsoft Distributed Password Recovery
Build high-performance clusters for breaking passwords faster. Elcomsoft Distributed Password Recovery offers zero-overhead scalability and supports GPU acceleration for faster recovery. Serving forensic experts and government agencies, data recovery services and corporations, Elcomsoft Distributed Password Recovery is here to break the most complex passwords and strong encryption keys within realistic timeframes.
Elcomsoft Distributed Password Recovery official web page & downloads »
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
![]()
Elcomsoft Phone Breaker
Gain full access to information stored in FileVault 2 containers, iOS, Apple iCloud, Windows Phone and BlackBerry 10 devices! Download device backups from Apple iCloud, Microsoft OneDrive and BlackBerry 10 servers. Use Apple ID and password or extract binary authentication tokens from computers, hard drives and forensic disk images to download iCloud data without a password. Decrypt iOS backups with GPU-accelerated password recovery.
![]()
Elcomsoft Password Digger
Elcomsoft Password Digger is a Windows tool to decrypt information stored in Mac OS X keychain. The tool dumps the content of an encrypted keychain into a plain XML file for easy viewing and analysis. One-click dictionary building dumps all passwords from the keychain into a plain text file, producing a custom dictionary for password recovery tools. The custom dictionary helps breaking passwords to encrypted documents or backups faster.
![]()
Elcomsoft Phone Viewer
Elcomsoft Phone Viewer is a fast, lightweight forensic viewer for quickly accessing information extracted from mobile backups. Supporting a variety of platforms and data formats, the tool can display information extracted from local and cloud iOS backups and Microsoft Accounts. Password-protected iTunes backups can be automatically decrypted and analyzed without using third-party tools.
如有侵权请联系:admin#unsafe.sh