According to the 2020 Data Breaches report by Verizon, 25% of all breaches involved the use of stolen credentials. And for small businesses, that number hit 30%. Brute force attacks have a similar share, accounting for 18% of all breaches, and 34% of those for small businesses.
Why are password attacks like brute forcing so effective? And how exactly do they work?
Let’s take a look at three kinds of password attacks that present a real threat to sites and businesses of all sizes.
Brute Force Attacks
Brute forcing in its essence is trying many passwords to gain access to an account.
Brute Force Real-Life Analogy
Let’s say that a burglar wants to get the door to your house open, but he can’t find an entry point or another place to break in. So he goes to the alarm keypad and starts tapping in random codes, hoping one will work eventually.
On a website, attackers can usually try some of the default usernames like admin, administrator, webmaster, etc., and on those usernames they can try a huge number of passwords.
How do attackers get password combinations to use for the attack?
There’s several ways they can go. Attackers can use a pre-made dictionary that contains commonly used passwords. Some even combine commonly used passwords with generated strings. Or they can generate their own dictionary – or even just generate the password on-the-fly right as they’re about to use it.
How do attackers generate a brute force password list?
Attackers have several ways to achieve this, but one of the most common tools is Crunch.
Crunch allows them to select the minimum and maximum number of characters they want each word to have. They can even select which characters they want to limit the words to.
Now, let’s say that a website uses simple passwords with a limit of 5 characters. Using Crunch, they can generate a list from one character to five characters (this is just for letters):
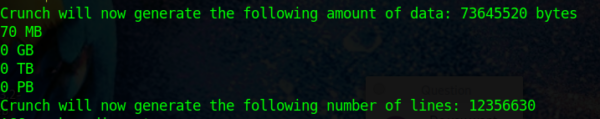
So, this is a list with just 12,356,630 lines (1 word per line) and will only take 70MB in space to store. That’s quite small.
What if that same site were to require special characters and digits?
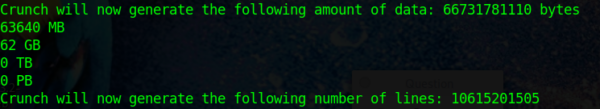
A simple addition to the list was generated, but the increase in variations bumps the size of the list from 70 MB to 62 GB. Good so far?
The stronger the password restrictions for a site are, the larger and larger the list of potential passwords will have to be. Let’s say a site requires a password to be longer than 8 characters.
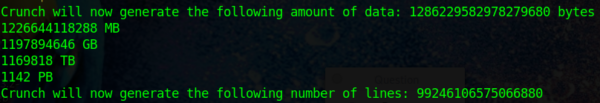
Even just generating passwords between 8 to 12 characters, this list has 99,246,106,575,066,880 lines (that’s about 8 billion times the number of lines from the previous list). In terms of space required to save this list it would take 1,169,818 TB. That’s 1,142 PB (petabytes).
Let’s once again throw digits and special characters into the mix.
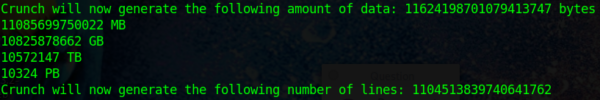
The list size went up by about 10 times. This goes to show how the simple inclusion of complex characters makes it much more difficult for attackers to brute-force a site.
You may now be thinking, “Wow, how do attackers have so much space to store all that?”
Well, they don’t really need to. The same tool allows them to directly pass the words it generates to another piece of software or script to be used, avoiding the need to save the lists at all.
But more importantly, think about it this way, “If my password is just slightly bigger and has special characters and numbers, it takes the attackers a lot more effort.”
Brute Force Key Takeaways
Even though the attack is pretty simple to get underway, it’s also easily defeated. Strong password enforcement rules, captchas, flood limits and fail2ban are pretty effective at stopping a brute-force attack, especially when used together.
The bigger the effort behind a brute force attack, the easier it is to detect and block with the right tools in place.
One key point of a brute-force attack is that attackers rarely actually use Crunch unless it’s a very targeted attack. Crunch requires significant time to be successful, and a list with the most commonly used passwords usually has a good degree of success.
Attackers may also utilize a list of discovered/leaked passwords. Whenever a big site is compromised and its user accounts are dumped, all those specific passwords – no matter how uncommon and secure – become available for these kinds of lists. This is why it’s strongly advised to never re-use the same passwords across different websites.
Brute Force Curiosity
In 2007, a computer would be able to make about 7 million password attempts per second. Now in 2021, one can make more than 100 million attempts per second.
Even with the massive increase, the list of passwords using 8 to 12 plain characters with 99,246,106,575,066,880 words still takes about 99 million seconds (1.6 million minutes, 27 thousand hours, or 1148 days). And this is without taking into account any security measures that may be in place or even network delays.
This just goes to show that if you want to protect yourself as much as possible from this, a good strong password with multiple upper and lower-case characters, symbols and numbers is a good strategy.
Password Spraying
Now let’s take a look at password spraying. This term is not as well known as brute-forcing, but it’s actually quite similar.
Brute-forcing can take many forms, but the essence of it is this: Attempt the largest number of passwords on the smallest number of accounts (maybe even a single account).
Password spraying is almost the opposite: It attempts the smallest number of passwords on the largest number of accounts possible.
Attackers get a list of the most commonly used passwords across the web – or even from past intelligence gathered on the target. Then they attempt usernames at random, or they can buy a list of usernames from the dark web or from leak lists.
An important part of password spraying is staying under the radar. This usually implies that there was previous reconnaissance done on the target.
For example, an attacker might have learned that an account gets locked after five wrong password entries. So, they’ll try just four passwords on an account before moving to the next one. It would raise suspicion if all of a sudden all accounts started to be disabled and would hinder the attack’s effectiveness. That could alert the target and crash the entire attack’s efforts.
Attackers can employ other methods to make detection harder, like utilizing several VPNs or using different compromised machines to carry out attacks. They could even try just waiting some time before attempting another password. Although these methods slow down the total duration of the attack, it makes them harder to detect.
Password Spraying Example
Let’s consider an example: An attacker plans to carry out a password spraying attack.
First, they need to obtain the list of usernames to compromise on the target. They can investigate the target by looking for leaks or checking the dark web for anything related to the target.
If nothing is found through these means, attackers can then run a more active search on the target. A way to achieve this is, for example, to use a tool called Maltego. Maltego aggregates data found across the web, with a basic focus on analyzing real-world relationships between data. Maltego’s intent and primary use is for legitimate investigative purposes. But it also provides valuable information to attackers – a common scenario in the security world.
Here’s an example of how it looks:
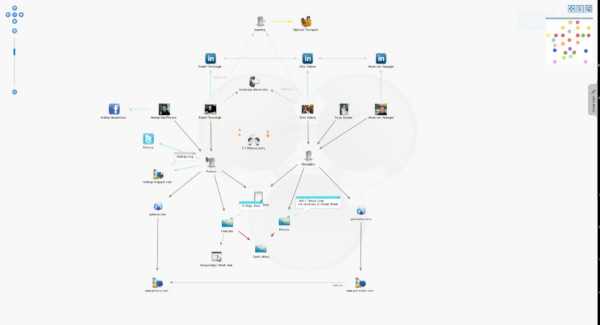
An attacker can tell Maltego what the target is, and the tool will seek information about anything related to the target. This includes employees, related servers or services, and anything from social media, etc.
But for this objective the attacker just wants people, more importantly employees. Attackers may be able to find their email addresses, and if not, try to extrapolate it from known ones or even their actual username for the target. The attacker can remove the other information from their scope, at least for now.
Say they just look for email addresses from the target’s personnel.
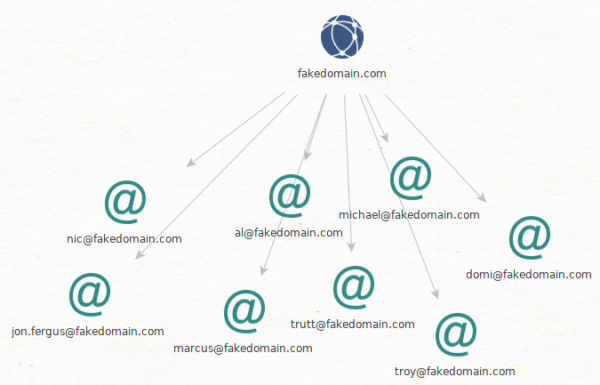
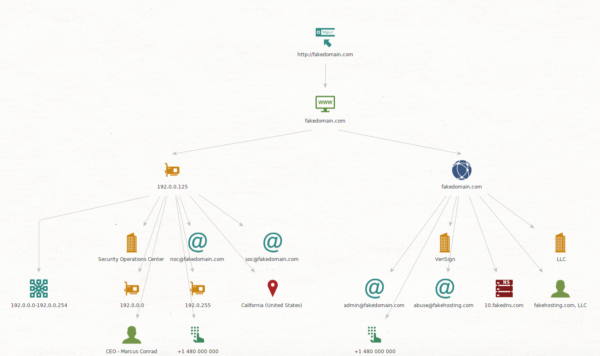
(On top of this attackers could get Twitter accounts, Facebook profiles, tweets sent, etc. All of this is valuable information, either for the current plan or for other attacks.)
Side note: In the image with the wider scope, we can see that the CEO is named Marcus Conrad. So, in the narrower view immediately above, an attacker might look for an email connected to “Marcus” or “Conrad”. Those emails could very well be the CEO’s, especially one as simple as “marcus@”. This is particularly valuable target information if someone wanted to attempt to specifically compromise his account(s) or conduct follow up targeted attacks.
Regardless, the attacker has accumulated a number of accounts through this process, which increases the likelihood that password spraying will work.
Credential Stuffing
To summarize credential stuffing as quickly as possible: It’s using stolen or leaked credentials to gain access to other services.
Credential stuffing is also referred to as a credential reuse attack.
Either way, it’s really quite simple.
Credential Stuffing Example
Say an email address and password leaked on the web. Attackers try that email and password on several services like Amazon, eBay, etc. They’ll also take the first part of the email and try it on other email providers like Yahoo, Gmail, etc.
So if the leaked account was [email protected], the attackers would also try the same password at [email protected], [email protected]. They’ll also try the same email and password but on services like Netflix, Amazon, and so on.
This attack is all based on the principle that a normal user will most likely reuse the same password across different accounts and services.
And this is the reason it’s very important to use different passwords for every account and service. If one of them gets compromised and leaked, the risk to any other account is minimized.
Conclusion
Now that you are more familiar with the many threats in the wild, hopefully you understand why security professionals insist on everyone following password security best practices
So based on what we’ve learned, what’s the best way to protect your accounts, sites, and servers?
- Keep your passwords as complex and as long as you can
- Keep them unique for each account and service that you use
- Keep an eye on public leak monitoring lists like https://haveibeenpwned.com/
- Add two factor authentication to as many services as possible
- Consider using a password manager to be able to consistently use complex passwords
An average user has to keep track of around 20 to 40 passwords. So it’s understandably tempting to start writing them down somewhere random. But don’t fall into that temptation! Use a password manager to ensure your security precautions aren’t undercut by one careless document.
Looking Forward
Because of all this, many tech companies are making a push towards password-less logins by making use of, for example, bio-metrics or a physical object like a u2f key. This likely not only reduces the risk of passwords but also the prevalence of phishing attacks.
Moving from something that the user knows to something that the user has presents the potential to mitigate most of the risks associated with passwords.
If you want to remain up to date with the latest website security trends, sign up for our blog email feed.
