2021-06-16 04:56:05 Author: derflounder.wordpress.com(查看原文) 阅读量:134 收藏
Home > Jamf Pro, Java, Linux, PKI > Jamf Pro deprecating the ability to issue a Tomcat certificate from the Jamf Pro built-in certificate authority
Jamf Pro deprecating the ability to issue a Tomcat certificate from the Jamf Pro built-in certificate authority
As part of the release of Jamf Pro 10.30, the following entry was added to the Deprecations section of the Jamf Pro Release Notes:
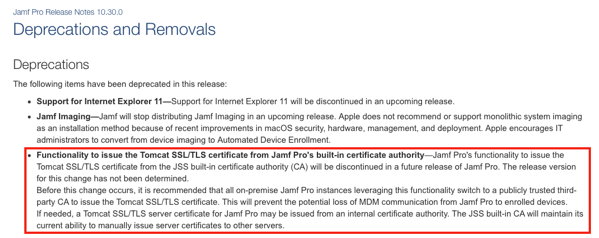
Functionality to issue the Tomcat SSL/TLS certificate from Jamf Pro’s built-in certificate authority — Jamf Pro’s functionality to issue the Tomcat SSL/TLS certificate from the JSS built-in certificate authority (CA) will be discontinued in a future release of Jamf Pro. The release version for this change has not been determined.
Before this change occurs, it is recommended that all on-premise Jamf Pro instances leveraging this functionality switch to a publicly trusted third-party CA to issue the Tomcat SSL/TLS certificate. This will prevent the potential loss of MDM communication from Jamf Pro to enrolled devices.
If needed, a Tomcat SSL/TLS server certificate for Jamf Pro may be issued from an internal certificate authority. The JSS built-in CA will maintain its current ability to manually issue server certificates to other servers.

For shops which use Jamf Pro’s built-in certificate authority to create the SSL certificate used by the Tomcat web application, this means that at some point in the near(ish) future, you will need to plan to use a certificate for your Jamf Pro server which is no longer being issued by your Jamf Pro server’s built-in certificate authority.

For more details, please see below the jump.
As part of the deprecation notes, Jamf recommends a switch to a publicly trusted certificate for Tomcat. One way to get those is to use the Let’s Encrypt certificate authority. This is a free service which will issue free publicly trusted certificates that are valid for 90 days before needing to be renewed.
While Jamf Pro does not natively include functionality for using and renewing Let’s Encrypt-issued certificates, there is at least one script available on GitHub for using Let’s Encrypt certificates with a Jamf Pro server:
https://github.com/sean-rabbitt/letsEncryptJSS

I’ve been using this script on a development Jamf Pro server myself for over a year and it works pretty well with the host OS (CentOS 7.x.) The script renews the certificate with Let’s Encrypt’s certificate authority on a scheduled basis and automatically updates the Java keystone with the new certificate for Tomcat to detect and use. Tomcat needs to be started as part of the renewal process because the certificate in the Java keystore is being changed out for the new certificate, but the script handles that as well.

I’ve also leveraged the same Let’s Encrypt-issued certificate to provide an Apache-hosted HTTPS local distribution point for this server. In this case, Apache has been configured with the filesystem path of the Let’s Encrypt’s certificate files and is able to use them without additional importing into Java or other services.

如有侵权请联系:admin#unsafe.sh