2021-07-15 15:55:24 Author: blog.elcomsoft.com(查看原文) 阅读量:81 收藏
While we are still working on the new version of Elcomsoft iOS Forensic Toolkit featuring forensically sound and nearly 100% compatible checkm8 extraction, an intermediate update is available with two minor yet important improvements. The update makes it easier to install the tool on macOS computers, and introduces a new agent extraction option.
macOS installation
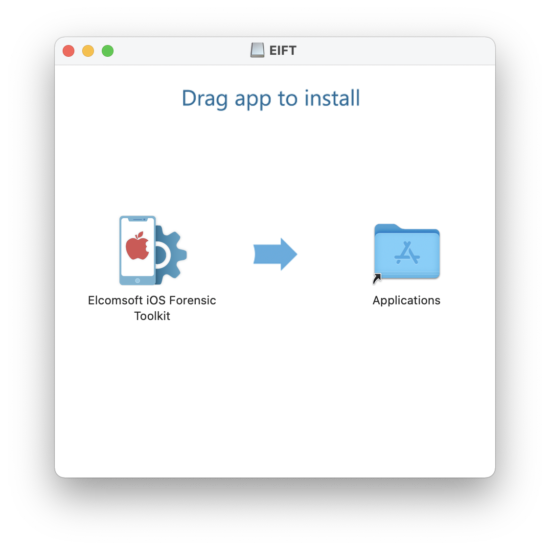
Elcomsoft iOS Forensic Toolkit is a console tool, similar to many non-commercial forensic software products such as APOLLO, iLEAPP, etc. That does not make it any more complex to use compared to many GUI-based tools as we tried to make the menu-driven, console-based UI very simple and straightforward to use, without the need to set complex command-line parameters. But many of our customers reported problems with… installation. We recently made a Windows installation package to make it easier, taking care of raising privileges and setting up the proper default folders for extracted data. On macOS, however, one still had to do a few things manually: clean the quarantine flag (on Catalina and Big Sur), and tell the OS it was OK to run software from an “unidentified developer” in Security & Privacy settings. While that is not rocket science and most macOS users are familiar with this kind of things, we decided to pack the program (that consist of the script, several auxiliary command-line utilities and some additional data from patched firmware) into a single app bundle. With this, and all you have to do is drag and drop the package into the Applications folder, and run it from there like all other programs.
When you start the program at the first time, the following warning is still shown (as the program is not from Mac App Store); this is normal, just press Open.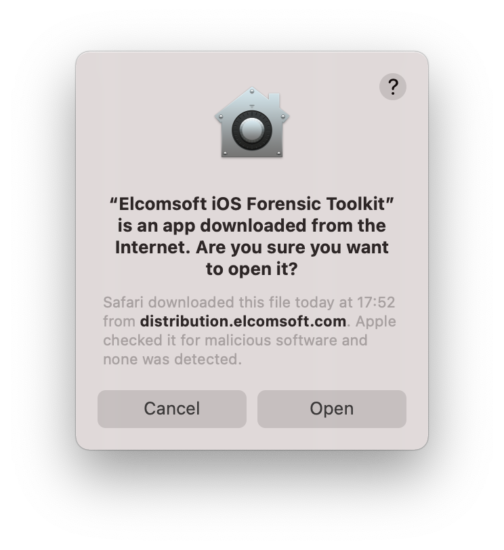
Still, GUI is on the way!
New agent acquisition option
This option fixes the extraction of iOS devices with corrupted file systems. If the corruption occurs, the extraction may freeze when attempting to read a corrupted file. Moreover, even logical extraction would fail if the corruption is present.
We’ve added a new option related to agent acquisition. The new option allows you to set the maximum size of the files being copied. If the file system of the device being extracted is partially corrupted, the size reported for a particular file may be really huge (in the exabytes range). We do not know the reason that may be causing that, yet it is a real-life situation we’ve encountered it more than once. When it happens, the agent would simply freeze on copying the file, and the whole process would never complete, although everything is fine with the rest of the files.
Here is what we did: added an option for the maximum file size (you can also use it to skip “normal” yet very large files to speed-up the extraction process); larger files will be just skipped. The default setting is 512 GB, which is more than enough for normal operations, but you can set any size you like. To do that, locate the AcquisitionClient calls with the –image parameter, and add –max_file_size followed by the size and measurement value: k/M/G for kilobytes, megabytes and gigabytes respectively. The resulting string may look like this (an example from macOS, limiting the file size to 8 gigabytes):
"$AGENTDIR"/AcquisitionClient --image --max_file_size=8G -p "$outdir"
Editing the script
Changing some program settings require manual editing of the main script. In Windows, the script is located at the following path (Administrator privileges are required):
C:\Program Files (x86)\Elcomsoft Password Recovery\Elcomsoft iOS Forensic Toolkit\Toolkit.cmd
In macOS (and with the new installer and software packaging), right-click on the Elcomsoft iOS Forensic Toolkit in Applications folder, select Browse Contents from the pop-up menu, then navigate to:
Contents/Resources/macosx/Toolkit.sh
Please edit the script with care, and only do so if you know exactly what you are doing. The options you may need to edit are:
- IPORT: 22 by default, but 44 for BFU acquisition with checkra1n
- AGENT_ID, AGENT_PASSWORD, AGENT_TEAMID: for easier agent installation
- max_file_size: see above
Anything else?
Yes, a few other bits and pieces. First, we fixed a minor problem with the Windows installer: we have realized that one of the runtime libraries was linked dynamically was missing on some legacy Windows 7 systems with no updates, so you had to install the runtime package manually. We’ve fixed that.
Second, we have added a quick reminder to the log extraction process (which is a part of our extended logical acquisition) to install a sysdiagnose profile in advance; that will allow you to get more data. The profiles are available here (for iOS, tvOS and watchOS):
https://developer.apple.com/bug-reporting/profiles-and-logs/
Finally, although there is no official support for M1-based Macs, we have tested the new build and found no problems so far after adding the digital signatures and notarizing all of the toolkit components. All you need to do install Rosetta 2. Even support for legacy devices (based on limera1n and checkm8 exploits) works, though you still need to take care of connections (USB-A cable, no hubs and all that). The upcoming major release with forensically sound checkm8 extraction for newer models will feature native M1 code.
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh