2021-07-24 01:11:39 Author: derflounder.wordpress.com(查看原文) 阅读量:90 收藏
To help maintain the security of the Apple Silicon Macs in your environment, it’s helpful to be able to monitor what the Startup Security settings are for those Macs.

For this task, the reporting functions of the bputil tool are available. Normally, Apple wants you to avoid the bputil tool like you would a swarm of bees. As part of that, the following warning is displayed by bputil:
| username@computername ~ % bputil -d | |
| This utility is not meant for normal users or even sysadmins. | |
| It provides unabstracted access to capabilities which are normally handled for the user automatically when changing the security policy through GUIs such as the Startup Security Utility in macOS Recovery. | |
| It is possible to make your system security much weaker and therefore easier to compromise using this tool. | |
| This tool is not to be used in production environments. | |
| It is possible to render your system unbootable with this tool. | |
| It should only be used to understand how the security of Apple Silicon Macs works. | |
| Use at your own risk! | |
| The tool requires running as root | |
| username@computername ~ % |
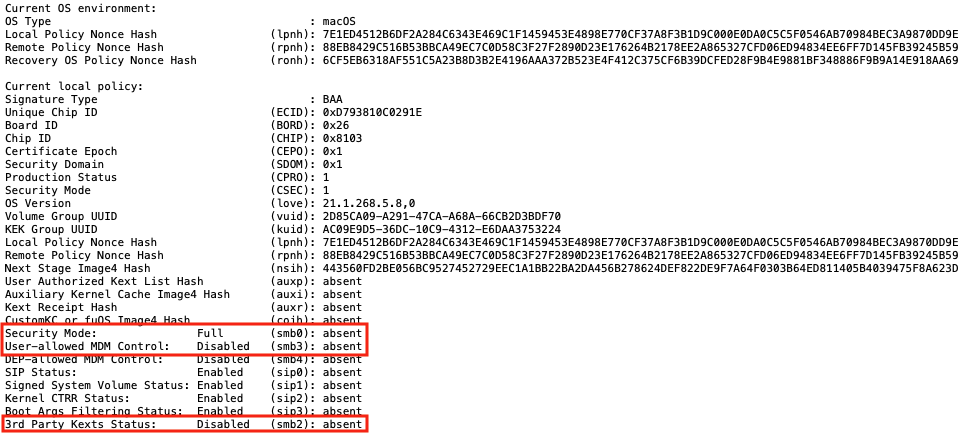
However, the bputil -d command is safe to use as it displays the contents of the current security policy’s settings. When the default Full Security security mode is enabled, running the bputil -d command with root privileges should display content similar to what’s shown below:
| username@computername ~ % sudo bputil -d | |
| Password: | |
| This utility is not meant for normal users or even sysadmins. | |
| It provides unabstracted access to capabilities which are normally handled for the user automatically when changing the security policy through GUIs such as the Startup Security Utility in macOS Recovery. | |
| It is possible to make your system security much weaker and therefore easier to compromise using this tool. | |
| This tool is not to be used in production environments. | |
| It is possible to render your system unbootable with this tool. | |
| It should only be used to understand how the security of Apple Silicon Macs works. | |
| Use at your own risk! | |
| Current OS environment: | |
| OS Type : macOS | |
| Local Policy Nonce Hash (lpnh): 7E1ED4512B6DF2A284C6343E469C1F1459453E4898E770CF37A8F3B1D9C000E0DA0C5C5F0546AB70984BEC3A9870DD9E | |
| Remote Policy Nonce Hash (rpnh): 88EB8429C516B53BBCA49EC7C0D58C3F27F2890D23E176264B2178EE2A865327CFD06ED94834EE6FF7D145FB39245B59 | |
| Recovery OS Policy Nonce Hash (ronh): 6CF5EB6318AF551C5A23B8D3B2E4196AAA372B523E4F412C375CF6B39DCFED28F9B4E9881BF348886F9B9A14E918AA69 | |
| Current local policy: | |
| Signature Type : BAA | |
| Unique Chip ID (ECID): 0xD793810C0291E | |
| Board ID (BORD): 0x26 | |
| Chip ID (CHIP): 0x8103 | |
| Certificate Epoch (CEPO): 0x1 | |
| Security Domain (SDOM): 0x1 | |
| Production Status (CPRO): 1 | |
| Security Mode (CSEC): 1 | |
| OS Version (love): 21.1.268.5.8,0 | |
| Volume Group UUID (vuid): 2D85CA09-A291-47CA-A68A-66CB2D3BDF70 | |
| KEK Group UUID (kuid): AC09E9D5-36DC-10C9-4312-E6DAA3753224 | |
| Local Policy Nonce Hash (lpnh): 7E1ED4512B6DF2A284C6343E469C1F1459453E4898E770CF37A8F3B1D9C000E0DA0C5C5F0546AB70984BEC3A9870DD9E | |
| Remote Policy Nonce Hash (rpnh): 88EB8429C516B53BBCA49EC7C0D58C3F27F2890D23E176264B2178EE2A865327CFD06ED94834EE6FF7D145FB39245B59 | |
| Next Stage Image4 Hash (nsih): 443560FD2BE056BC9527452729EEC1A1BB22BA2DA456B278624DEF822DE9F7A64F0303B64ED811405B4039475F8A623D | |
| User Authorized Kext List Hash (auxp): absent | |
| Auxiliary Kernel Cache Image4 Hash (auxi): absent | |
| Kext Receipt Hash (auxr): absent | |
| CustomKC or fuOS Image4 Hash (coih): absent | |
| Security Mode: Full (smb0): absent | |
| User-allowed MDM Control: Disabled (smb3): absent | |
| DEP-allowed MDM Control: Disabled (smb4): absent | |
| SIP Status: Enabled (sip0): absent | |
| Signed System Volume Status: Enabled (sip1): absent | |
| Kernel CTRR Status: Enabled (sip2): absent | |
| Boot Args Filtering Status: Enabled (sip3): absent | |
| 3rd Party Kexts Status: Disabled (smb2): absent | |
| username@computername ~ % |
Here’s what bputil -d will return if the Startup Security settings are configured as follows:
- Reduced Security: Enabled
- Allow user management or kernel extensions from identified developers: Enabled
- Allow remote management of kernel extensions from identified developers: Enabled

| username@computername ~ % sudo bputil -d | |
| Password: | |
| This utility is not meant for normal users or even sysadmins. | |
| It provides unabstracted access to capabilities which are normally handled for the user automatically when changing the security policy through GUIs such as the Startup Security Utility in macOS Recovery. | |
| It is possible to make your system security much weaker and therefore easier to compromise using this tool. | |
| This tool is not to be used in production environments. | |
| It is possible to render your system unbootable with this tool. | |
| It should only be used to understand how the security of Apple Silicon Macs works. | |
| Use at your own risk! | |
| Current OS environment: | |
| OS Type : macOS | |
| Local Policy Nonce Hash (lpnh): 987619CF88732BB0FB0CCC476302DFE84EB1C1F7B92E8CBEC4B124D9F76B3DBACD8787E5DEBB8A3F70576639CE74F727 | |
| Remote Policy Nonce Hash (rpnh): 88EB8429C516B53BBCA49EC7C0D58C3F27F2890D23E176264B2178EE2A865327CFD06ED94834EE6FF7D145FB39245B59 | |
| Recovery OS Policy Nonce Hash (ronh): 6CF5EB6318AF551C5A23B8D3B2E4196AAA372B523E4F412C375CF6B39DCFED28F9B4E9881BF348886F9B9A14E918AA69 | |
| Current local policy: | |
| Signature Type : BAA | |
| Unique Chip ID (ECID): 0xD793810C0291E | |
| Board ID (BORD): 0x26 | |
| Chip ID (CHIP): 0x8103 | |
| Certificate Epoch (CEPO): 0x1 | |
| Security Domain (SDOM): 0x1 | |
| Production Status (CPRO): 1 | |
| Security Mode (CSEC): 1 | |
| OS Version (love): 21.1.284.5.5,0 | |
| Volume Group UUID (vuid): 2D85CA09-A291-47CA-A68A-66CB2D3BDF70 | |
| KEK Group UUID (kuid): AC09E9D5-36DC-10C9-4312-E6DAA3753224 | |
| Local Policy Nonce Hash (lpnh): 987619CF88732BB0FB0CCC476302DFE84EB1C1F7B92E8CBEC4B124D9F76B3DBACD8787E5DEBB8A3F70576639CE74F727 | |
| Remote Policy Nonce Hash (rpnh): 88EB8429C516B53BBCA49EC7C0D58C3F27F2890D23E176264B2178EE2A865327CFD06ED94834EE6FF7D145FB39245B59 | |
| Next Stage Image4 Hash (nsih): 1FAC4F6723D591DD6FAEC1DDB7D84C0AB28782096F8F2570EDA1F3CC41DECBE883A59BC4C3C962484E283F4E11549CB6 | |
| User Authorized Kext List Hash (auxp): absent | |
| Auxiliary Kernel Cache Image4 Hash (auxi): absent | |
| Kext Receipt Hash (auxr): absent | |
| CustomKC or fuOS Image4 Hash (coih): absent | |
| Security Mode: Reduced (smb0): 1 | |
| User-allowed MDM Control: Enabled (smb3): 1 | |
| DEP-allowed MDM Control: Disabled (smb4): absent | |
| SIP Status: Enabled (sip0): absent | |
| Signed System Volume Status: Enabled (sip1): absent | |
| Kernel CTRR Status: Enabled (sip2): absent | |
| Boot Args Filtering Status: Enabled (sip3): absent | |
| 3rd Party Kexts Status: Enabled (smb2): 1 | |
| username@computername ~ % |
Note: This reporting function does not require macOS Recovery and works while booted from regular macOS.
To check the Startup Security settings, the following status codes should be checked:
- smb0
- smb2
- smb3

In the Startup Security Utility app in macOS Recovery, the following settings correspond to the status codes listed above:
- smb0: Full Security / Reduced Security
- smb2: Allow user management of kernel extensions from identified developers
- smb3: Allow remote management of kernel extensions from identified developers
For more details, please see below the jump.
If you want to check to see if an Apple Silicon Mac is set for Full Security or Reduced Security, run the command shown below with root privileges:
| bputil -d | awk '/smb0/ {print $5}' |
If Full Security is set, you should see the following result:
absent

If Reduced Security is set, you should see the following result:
1

If you want to check to see if an Apple Silicon Mac is set for Allow user management or kernel extensions from identified developers, run the command shown below with root privileges:
| bputil -d | awk '/smb2/ {print $7}' |
If Allow user management or kernel extensions from identified developers is not set, you should see the following result:
absent

If Allow user management or kernel extensions from identified developers is set, you should see the following result:
1

Note: If this setting is returning a value of 1, this means that Reduced Security is enabled, so the smb0 status code will also return 1.

If you want to check to see if an Apple Silicon Mac is set for Allow remote management of kernel extensions from identified developers, run the command shown below with root privileges:
| bputil -d | awk '/smb3/ {print $6}' |
If Allow remote management of kernel extensions from identified developers is not set, you should see the following result:
absent
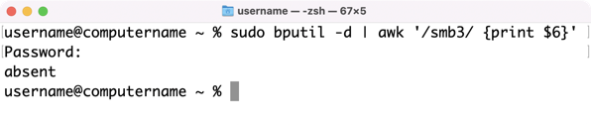
If Allow remote management of kernel extensions from identified developers is set, you should see the following result:
1
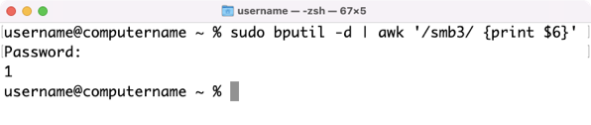
Note: If this setting is returning a value of 1, this means that Reduced Security is enabled, so the smb0 status code will also return 1.

如有侵权请联系:admin#unsafe.sh