2021-07-28 23:52:43 Author: blog.elcomsoft.com(查看原文) 阅读量:69 收藏
Protecting one’s online privacy is becoming increasingly more important. With ISPs selling their customers’ usage data left and right, and various apps, mail and Web trackers contributing to the pool of “anonymized” data, de-anonimyzation becomes possible with big data analysis. This was clearly demonstrated with the recent event highlighted in Catholic priest quits after “anonymized” data revealed alleged use of Grindr.
“While this might be the first case of a public figure’s online activities being revealed through aggregate data, “it unfortunately happens very often” to the general public, Andrés Arrieta, director of consumer privacy engineering at the Electronic Frontier Foundation, told Ars. “There are companies who capitalize on finding the real person behind the advertising identifiers.” Furthermore, de-anonymizing data in the way The Pillar did is trivially easy. All you need to do to buy the data, Arrieta said, is pretend to be a company. There are no special technical skills required to sift through the data, he added.”
Apple did an attempt protecting their users’ location by introducing approximate locations in iOS 14. That change alone makes analyzing aggregate data from iPhone users more difficult but not impossible. In this publication, we compare the tools to protect one’s privacy online while using Apple iOS devices and desktop computers by making one’s browsing activities inaccessible to the middleman.
Encrypted DNS / DNS over HTTPS
Why would anyone want to encrypt their DNS requests? The reason is very much the same as encrypting HTTPS traffic. “When people access the web within your app, their privacy is paramount”, reads Apple’s 2020 WWDC Keynote. “When your app accesses a website, the system asks a question, a DNS query, to turn that name into a set of addresses. Generally, the question is sent to a DNS server configured by your local network. So where does privacy come into the picture? One concern is that DNS questions and answers are usually sent over an unencrypted transport, UDP. That means that other devices on the network can not only see what names you’re looking up, but they can even interfere with the answers. The other privacy concern is that you may not trust the DNS resolver on your local network. If you’ve joined a public Wi-Fi network, your internet usage could be tracked or blocked.”
“So how does encrypted DNS improve this situation? Encrypted DNS, simply put, is using encryption to protect your DNS questions and answers. And if you don’t trust the network you’re on, it can also involve sending your questions to a DNS server that you do trust.” (WWDC 2020 Transcript)
In Windows, using a secure DNS server is easy if you are using Microsoft Edge. For iOS, you’ll have to install an app or make a profile to use encrypted DNS; more on that later.
Which secure DNS service to choose?
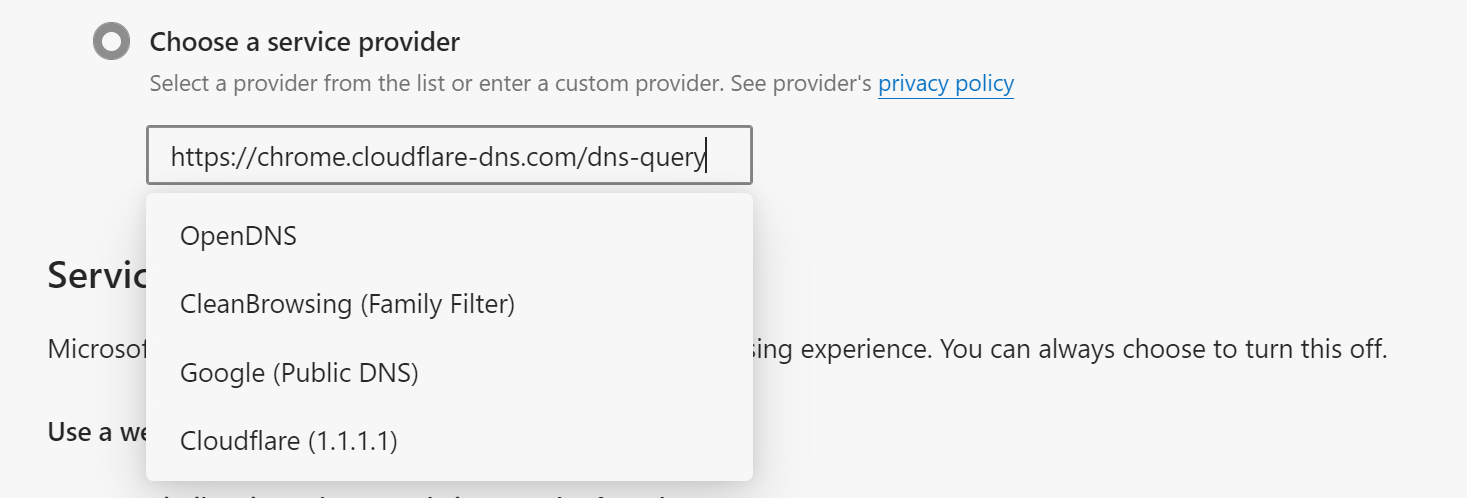
There are multiple secure DNS services around. The most commonly used ones are Cloudflare, Google, OpenDNS, NextDNS, and AdGuard.
Cloudflare has opened its DNS servers to the public in 2018. The company claims its unique WARP technology offers a higher degree of protection compared to other DNS service providers. No logging policy, and the company claims it won’t share the data with advertisers. Link to Privacy Policy (scroll down to Public DNS Resolver Users).
Google Public DNS offers DNS resolution over TLS-encrypted TCP connections. Google is known to go after its customers’ data, and runs one of the largest advertisement networks. The data is collected according to the company’s Privacy Policy. Whether to trust Google your DNS queries is your decision.
OpenDNS is a public DNS service. In 2015 it was acquired by Cisco. OpenDNS has a controversial privacy policy allowing the company to keep logs of DNS queries for 2 business days if the user has no account with the company. Users with accounts can optionally select a different retention setting or opt out of the logging. Note that the name “OpenDNS” refers to the DNS concept that queries are accepted from any source. It is not related to open source software.
NextDNS advertises a zero logging policy, which is active by default for all users. Users can create an optional account, in which case NextDNS keeps 3 months worth of logs with an option to turn off the logging entirely.
AdGuard is a relative newcomer advertising strict zero-logging policy for its DNS services. In addition to resolving Internet addresses, AdGuard DNS service can automatically filter out ads, malicious websites, tracking, and phishing.
LibreDNS
This is a public encrypted DNS service run by LibreOps, an organization that contributes to other free, open source technologies, that people can use to maintain secrecy of their DNS traffic, but also circumvent censorship. The company keeps no logs, detailing that logs are disabled for their DNS daemon. In addition, the company claims to use a local resolver for the DNS requests, and OpenNIC as their Tier 1.
Using encrypted DNS in iOS 14 and newer
Starting with iOS 14, Apple natively supports encrypted DNS. However, if you try searching through the Settings app, you will find no mention of it anywhere. The support for encrypted DNS is there, but the setting is not. In order to actually use a different (secure) DNS server, you will have to download a third-party app, or install a third-party configuration profile.
There are several apps in the App Store offering encrypted DNS services such as Cloudflare, AdGuard and NextDNS. If you’d rather install a configuration profile for a particular encrypted DNS service without using an app, you can create a custom NextDNS profile for your device, or download a ready-made, pre-signed one by paulmillr/encrypted-dns:
Paul Miller’s article on iOS 14, Big Sur & DNS over HTTPS / TLS is also worth reading.
Using encrypted DNS in Windows 10
As of today, windows 10 does not have a system-wide setting allowing to use encrypted DNS services. However, you can enable encrypted DNS in Microsoft Edge by choosing the corresponding service or entering a custom one under Privacy, search & services > Security (or by simply entering “DNS” in the Settings search box):
A matter of trust
How much protection does a public secure DNS service add compared to using your ISP’s default DNS servers? “If your ISP is no longer resolving DNS addresses, someone else must be doing it? Today, it’s probably cloudflare with its 1.1.1.1 public DNS, or google (8.8.8.8). So, instead of letting your ISP monitoring your DNS traffic, Cloudflare or Google will do it. Of course, they can sell collected data, or use it to create a dossier on someone.”, says Paul Miller. Indeed, while your ISP will be unable to clearly see which Web sites you visit, the public DNS service of your choice will. The choice of such service then becomes purely a matter of trust.
Key points:
- Your ISP or any other intermediary will not know which Web sites (domain names) you visit
- The IP addresses, however, will be still accessible
- The DNS service provider will see your requests; read their privacy policy and choose wisely
- Web site owners and trackers will see your real IP (and may be able to determine your location via reverse lookup)
- DNS requests are encrypted; the actual traffic is not (unless HTTPS)
- In iOS, DNS requests originating from Safari and all other apps are encrypted
- In Windows, only Microsoft Edge DNS requests are encrypted (other apps require separate settings; non-encrypted third-party DNS may be configured via network settings)
iOS 15 Hide IP Address
Hiding one’s IP address in Safari is a part of Apple’s Intelligent Tracking Prevention.
Starting with iOS 15, users will be able to hide their IP addresses from trackers and Web sites with a new privacy-centric Safari feature. This feature is not to be confused with Apple’s another new privacy feature called Private Relay. The Hide IP Address feature will be available for all users with iOS 15, while Private Relay is part of the pair iCloud+ subscription.
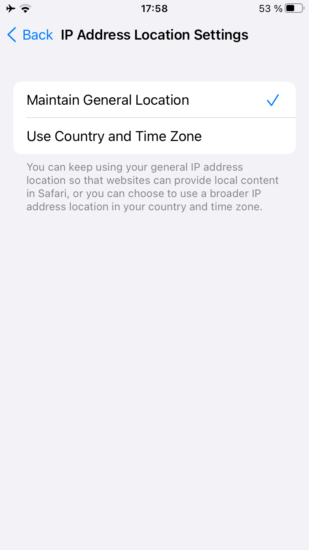
The new feature adds an option in Safari settings named “Hide IP Address” with the choice of “Trackers only” and “Trackers and Websites”, effectively allowing to hide your real IP address from online trackers that load alongside websites. The point of this feature is restricting access to your real location data, which can be traced via an IP geolocation database.
With iOS 15 still in beta, little is known about this feature.
Key points:
- Free service available to all Safari users in iOS 15
- Traffic encryption: unknown
- DNS encryption: unknown (but unlikely)
- Generally, the feature offers limited privacy protection in Safari only
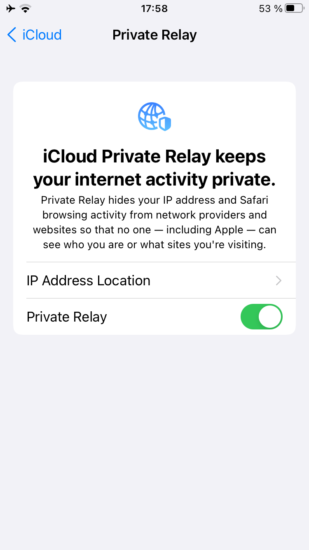
iOS 15 Private Relay
According to Apple, “Private Relay is a new internet privacy service that’s built right into iCloud, allowing users to connect to and browse the web in a more secure and private way. When browsing with Safari, Private Relay ensures all traffic leaving a user’s device is encrypted, so no one between the user and the website they are visiting can access and read it, not even Apple or the user’s network provider. All the user’s requests are then sent through two separate internet relays. The first assigns the user an anonymous IP address that maps to their region but not their actual location. The second decrypts the web address they want to visit and forwards them to their destination. This separation of information protects the user’s privacy because no single entity can identify both who a user is and which sites they visit.”
What is Apple Private Relay exactly, and how does it compare to a VPN service? This is what we know at this point What is Apple Private Relay and is it worse than a VPN? | TechRadar (updated with comments from various VPN providers). According to this, Apple Private Relay looks a lot closer to Tor rather than a VPN. “Tor also uses a system where your connections are routed through multiple relays. But while Apple stops at two, Tor defaults to three, and there can be many more. These are all run by volunteers, too, greatly reducing the chance that any one person can track what you’re doing, and we’ve seen arguments that this makes Tor safer than Private Relay”, says TechRadar’s Mike Williams.
Key points:
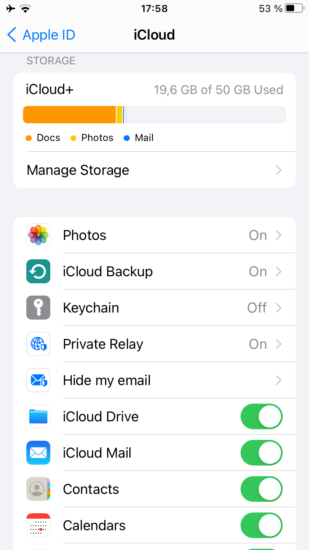
- Apple Private Relay is available as part of paid iCloud subscription
- Limited to 50GB of monthly traffic with basic subscription
- Protects activities in Safari and apps with insecure connections (HTTP rather than HTTPS) by passing encrypted traffic through two hoops
- No device-wide traffic encryption
- IP address in geographical proximity used by default; users can select a wider region
- Encrypts both DNS queries and traffic
- Apple hasn’t released any details about who runs the Private Relay network (early hints point to Cloudflare, Fastly and Akami)
- Whoever those providers are, they won’t see who is visiting what (two hops, full anonymization)
- The feature will not work where it’s needed the most: Apple has confirmed that the feature will not work in China, Belarus, Colombia, Egypt, Kazakhstan, Saudi Arabia, South Africa, Turkmenistan, Uganda and the Philippines.
More information: No, Apple’s Private Relay is not a VPN – CNET, iCloud+ Private Relay explained: Don’t call it a VPN | Macworld.
Using Private Relay
Once iOS 15 is released, paid iCloud subscribers will be able to activate the new service by enabling Private Relay in iCloud settings.
Tor browser
Tor ensures fully encrypted and completely private Web browsing experience – if you opt to use a particular Web browser app. The Onion protocol routes encrypted traffic through three independent hops, making it (theoretically) impossible to intercept traffic even if one of the nodes is compromised. In real life, Tor protection is not as impenetrable as the theory claims, yet it’s much more than enough for the simple purpose of preventing someone from running a big data analysis attack against you.
For most platforms other than iOS, the Tor browser uses a modified version of Firefox. The browser runs in the incognito/private mode by default, which means no history is left and no cookies are kept on the device once you close the browser.
Things are different in the iOS land. In Can I run Tor Browser on an iOS device?, the developers recommend an iOS app called Onion Browser, which is open source, uses Tor routing, and is developed by someone who works closely with the Tor Project. However, according to the developers, Apple requires browsers on iOS to use something called Webkit, which prevents Onion Browser from having the same privacy protections as Tor Browser.
Should you use the Tor browser? On the one hand, it’s a complete overkill for the simple purpose of preventing tracking. On the other, you’ll be tied to a particular Web browsing app with missing cloud synchronization and deprived of the many convenience features one comes to expect from a modern Web browser. It’s probably okay on occasions, but using Tor all the time for the sole purpose of preventing tracking would be a massive overkill and a major inconvenience.
Key points:
- Protection only within a certain browsing app (Tor browser on desktops, Onion Browser in iOS)
- Your ISP or any other intermediary will not know which Web sites you visit, including their IP addresses
- Web site owners and trackers won’t see your real IP
- Both DNS requests and traffic are encrypted (even plain HTTP)
- Less protection (but still major inconvenience) in iOS due to Webkit
Proxies
The idea behind using a proxy is relaying traffic through an intermediary (proxy) server. This will hide your real IP address (and the location associated with that IP address) from Web sites and trackers. However, most proxy servers do not encrypt traffic, leaving your communications vulnerable to deep packet inspection. Note that, depending on the type, proxy servers may not be completely transparent, and may require additional configuration in some apps.
Key points:
- Protection within supported apps
- Your ISP or any other intermediary will not easily know which Web sites you visit, including their IP addresses
- …unless deep packet inspection is used
- Web site owners and trackers won’t see your real IP
- The traffic is tunneled but not encrypted
- Less protection compared to VPN but similar inconvenience factor
VPN
A VPN service creates a secure, encrypted tunnel to route all your traffic from your device to the end point. Nobody can see what is flowing through the tunnel; not even your ISP. A VPN service encrypts everything: your DNS requests, the sites you visit and their IP addresses, the actual traffic (even plain HTTP) regardless of the protocol. Your ISP will see a single encrypted connection between your device and one remote server; it won’t be able to see any of your requests other than measure the amount of data flown through the tunnel. VPN services are frequently used to protect personal information, secure access to work locations or local networks in your home, encrypt your internet connection, and keep your browsing activities private.
Sounds too good to be true? A VPN is a double-edged sword. While a VPN service protects your data flow against the prying eye, in return, the VPN service provider itself gains full access to your online activities (naturally, except HTTPS and other encrypted traffic). For this reason, selecting a trustworthy VPN service is utterly important if you want to protect your privacy and not just gift someone your full browsing history.
It is not our intention to review or recommend any VPN service in particular. Do your research, and choose wisely. Several big-name VPN providers are ExpressVPN, NordVPN, PureVPN, Surfshark, CyberGhost, Private Internet Access, Tunnelbear; there are dozens of other VPN service providers of varying quality. If you prefer the big names, you can start by checking out a few articles:
- The best VPN service in 2021 | Tom’s Guide (tomsguide.com)
- The best VPN service 2021 | TechRadar
- Best VPN Service of 2021 | The Top Virtual Private Networks (security.org)
- 10 Best no log VPNs 2021 | Find proven zero log VPNs (proprivacy.com)
If you are after a lesser known one (but be aware of the caveats!) check out this:
- 5 Best VPNs You’ve Never Heard Of for 2021 (Hidden Gems!) (vpnmentor.com)
Also note that some well-known apps from reputable companies (such as AdGuard VPN or Speedtest by Ookla) provide limited VPN services for free while offering paid subscriptions through iTunes.
Technically, public VPN services in iOS are generally provided through dedicated apps made by their respective providers. If you know what you are doing, you can use OpenVPN Connect on the App Store to set up connection to an OpenVPN server, install a VPN profile through iOS settings or manually configure your VPN service through the Settings app.
Key points:
- Device-wide traffic encryption: encrypts and relays all traffic through a secure tunnel
- Impenetrable from the outside
- No full anonymization: the VPN service provider can see your online activities (but won’t have access to HTTPS and other encrypted types of traffic)
- Due diligence required when choosing VPN provider
- Most VPN providers require subscriptions
- Limited free offers are available; few of them originate from reputable sources
- Subject to limitations (number of devices and monthly traffic)
- VPN services may offer services in a wider range of regions
- Both DNS queries and traffic encrypted
- VPNs may or may not work in certain countries (e.g. China)
Choosing the right VPN service provider is probably the most important.
Do:
- Do your due diligence.
- Read the reviews.
- Read the actual policies.
- Approach services offering affiliate programs with skepticism and scrutiny.
Avoid:
- Using “free VPN” apps from the App Store from unknown developers. If they cannot make money by selling subscription, they’ll profit by selling your data.
- Buying a “lifetime” subscription from any service. Many were sold in the early days; few are still around today.
- Signing up for anything without reading the relevant policies.
Conclusion
Which method or combination of methods should you use pick to protect yourself from ISP eavesdropping your traffic on your iOS device? If you are using a trusted VPN service, keep using it: a VPN is enough to protect against all known tracking methods. If not VPN, Apple Private Relay seems like a good option, and is cheaper in the basic level than most VPNs of comparable quality. If you are not using either service, consider configuring encrypted DNS from a trusted provider with a privacy policy that you approve. Enabling “Hide IP address” protection for “Trackers only” in iOS 15 won’t hurt, but I’d be wary using that for “Trackers and Websites” due to connection speed concerns.
Using a proxy server this day and age is a dubious choice due to the same inconvenience factor as a VPN, which offers a significantly higher level of protection. Tor is better used on occasions and not as a main Web browser due to major inconveniences and the lack of cloud sync.
Be aware: if you opt to use a proxy, encrypted DNS or VPN service, you’re trusting your data to a third party. Technically, a VPN service provider can learn your browsing habits; a third-party DNS service will know which domains you resolve. Apple Private Relay and Tor are exceptions due to multiple independent hops used to anonymize your activities.
如有侵权请联系:admin#unsafe.sh