
2021-09-08 22:08:06 Author: www.sentinelone.com(查看原文) 阅读量:45 收藏
By Juan Andres Guerrero-Saade & Igor Tsemakhovich
Executive Summary
- EGoManiac is responsible for the previously reported ‘Octopus Brain’ campaign, where the operators interdicted the machines of OdaTV journalists to place malware and incriminating documents, effectively framing them before arrest.
- Our research connects Octopus Brain to a toolkit called Rad, in development as early as 2010 and used until 2015.
- Rad samples use hardcoded email addresses for exfiltration.
- One of those email addresses is cited in connection to the prosecution of rogue members of the Turkish National Police along with executives of a company called ‘Datalink Analiz’. They refer to Rad as ‘HORTUM’.
- Following the trail of ‘Datalink Analiz’, we suspect that EGoManiac activity includes the use of Hacking Team’s Remote Control System (RCS) contracted under this same front company with a series of irregularities as early as 2011.
- In 2013, a report emerged on the use of RCS against a Turkish victim in the United States. The victim voiced an unverified suspicion that its use represented the unsanctioned interests of rogue Gullenist elements within the Turkish government.
In this post, we provide an abridged version of our in-depth investigation into the activities of this unscrupulous threat actor. The full report provides detailed technical breakdowns of malware samples, full IoCs and hunting rules along with further attribution details.
The Hunt for Ahtapot
In the world of cyberespionage research, the human-interest element is often lost amidst a barrage of technical indicators. The absence of a human dimension can make our research seem overly technical and dry, something we write for defenders to block and other researchers to enjoy. When we can see the impact that some of these campaigns have on civil society and the weakening of public institutions, it invokes a certain doggedness that won’t let sleeping dogs lie. EGoManiac is one that’s been in the back of our heads for the past five years. The research involved multiple dead ends, false starts, and layers of conspiratorial mystery.
What we refer to as EGoManiac is a cluster of two notable campaigns starting as early as 2010. The first campaign came to be known in research circles as ‘Octopus Brain’, based on the Turkish strings Ahtapot and Bejin left in the malware. This original campaign used a combination of publicly available RATs (including Turkojan and Bandook) as well as the closed-source Ahtapot, with delivery methods ranging from malicious documents to personal visits by the attackers.
Our initial awareness of this case came from Turkish court documents surrounding arrests of journalists at OdaTV. Much greater detail came to light thanks to the excellent work of the folks at Arsenal Consulting. Their forensic investigation not only proved the presence of the malware and the physical interdiction of the victim systems, but also established the attacker’s access as the definitive source of the incriminating documents on those systems that were then used to justify arrests by the Turkish National Police. The journalists were ultimately acquitted by a court in 2017—six years after the attacks.
This scenario is one of the often-ignored dirty edge cases of ‘lawful intercept’ malware, stated plainly: what’s the expectation of evidential integrity when it comes to an infected device? This question is currently playing out further in the Bhima Koregaon case in India, where it appears malware was used to upload incriminating letters onto the victim’s machine.
While these particular operators resorted to physically tampering with the devices they were monitoring, there’s little keeping malware operators from placing incriminating or damaging files on systems infected with malware that has file download capabilities, as most rudimentary malware does.
In the face of such an unscrupulous actor, we are left to wonder if this activity is part of a cluster we already track, and if not, what else has this actor been up to in the shadows? Octopus Brain provided few answers. Despite finding a handful of Ahtapot modules, there were no newer samples nor connections to other toolkits. The trail went cold…until now.
Experiments in Innovative Pivoting
As threat hunting technology continued to improve, there were different attempts to once again pick up the scent of the attackers behind the Octopus Brain campaign. Code similarity analysis is one of the favorite tools in our research arsenal. However, initial attempts to cluster new samples based on shared unique code snippets were not fruitful.
We decided to take a different approach. Rather than focusing on unique code snippets, we can instead focus on a bulk of shared common code as a way of profiling the development environment that produced the samples and attempt to find other samples produced in the same way: same compiler, same optimizations, relying on the same statically-linked libraries, etc. Limited testing of this method has yielded positive results under specific circumstances—like allowing us to cluster a set of samples based off of the analysis of a single original sample and without needing to spend cycles conducting extensive goodware testing.
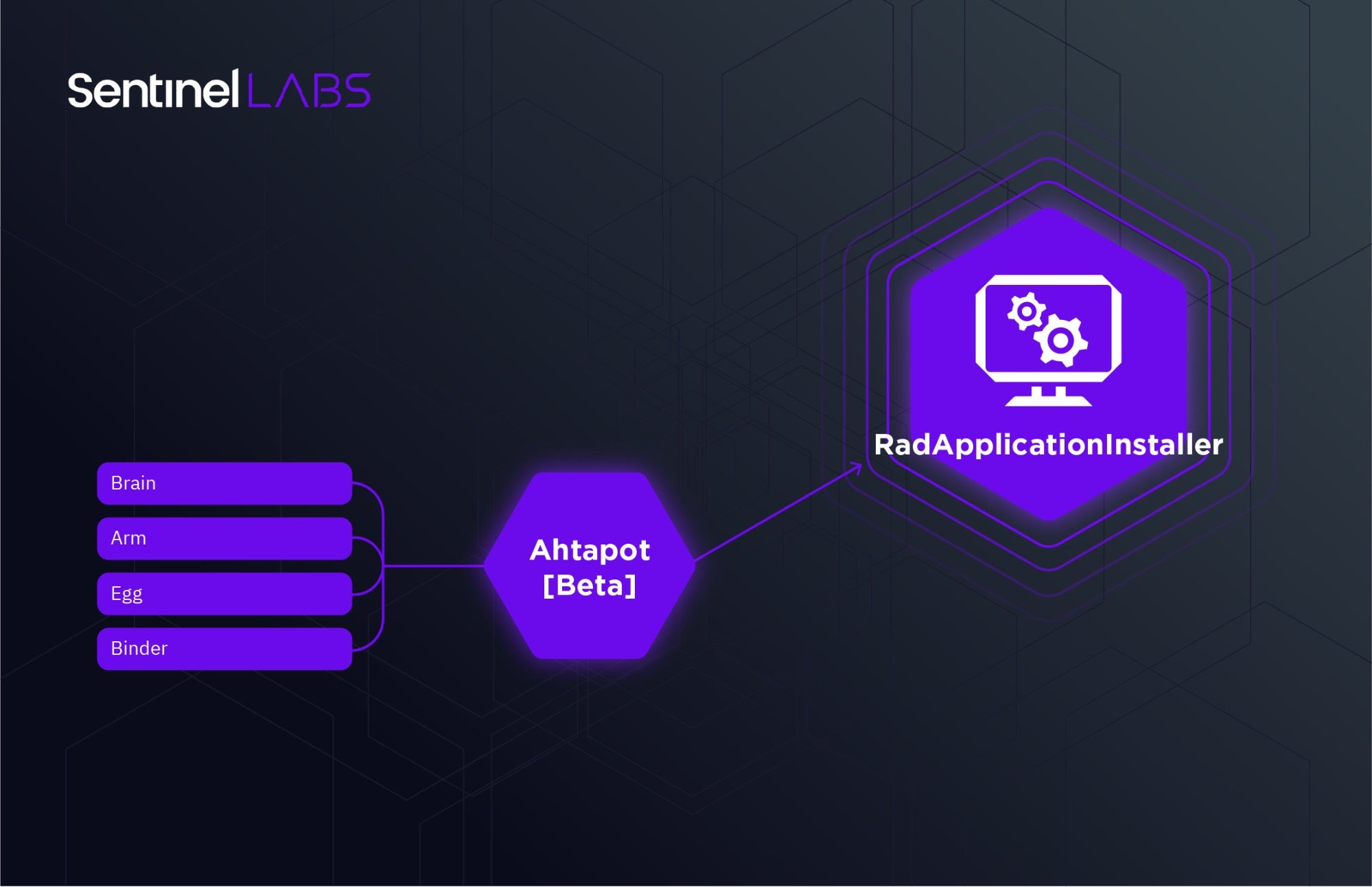
To our surprise, applying this experimental approach to Octopus Brain yielded results. By generating a rule based off of the bulk of common code of Ahtapot components, we stumbled upon a set of samples we’ll call ‘Rad’, based on a persistent typo in symbol paths left within the binaries.
Expanding on this initial finding, we found a cluster of more than 50 samples and subcomponents for a modular espionage toolkit almost entirely undetected at the time of discovery.
EGoManiac’s ‘Rad’ Toolkit
Rad is a modular espionage malware toolkit built around the POCO C++ cross-platform development libraries. The design entails a form of organized development but not a particularly savvy or sophisticated one at that. POCO is doing most of the heavy lifting. Functionality is split into modules contained within a ‘RadApplicationInstaller’ and orchestrated by a ‘RadStarter’ module that takes its cues from an encrypted configuration XML file. All of the Rad samples we’ve found rely on email exfiltration with a hardcoded address belonging to either Gmail, Yandex, or Woxmail (defunct at the time of writing).
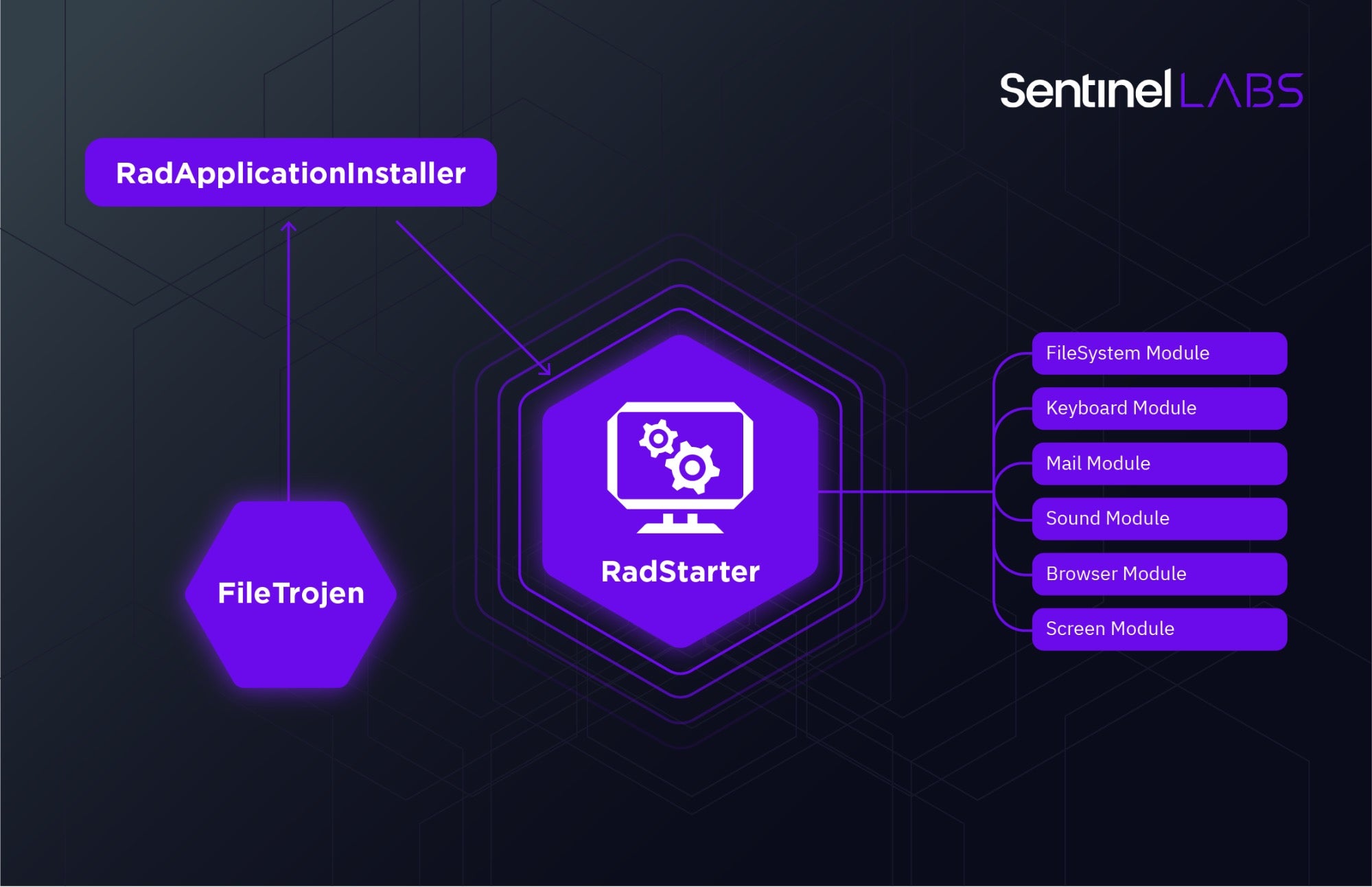
The execution flow of the Rad toolkit is straightforward. wsms.exe (RadStarter) is the main module that runs from a registry key set by the installer. It, in turn, runs the other modules as separate processes. Each process represents different functionality, including a keylogger, hot mic recorder, browser information extractor, screen capture module, file search, and a communication module for exfiltration. More details are provided in the full report.
Who is EGoManiac?
Attribution based solely on technical indicators is complicated and inexact. Most technical indicators are subject to modification and require interpretation based on limited visibility. Lacking a greater understanding of local context and closed-source intelligence, it’s difficult to extend attribution beyond abstract entities (like an APT group name) to specific people or organizations.
On the surface, EGoManiac activity revolves around a Turkish nexus. The malware is riddled with Turkish language, lures are written in Turkish, victims are Turkish and relevant to local politics. The connection to Ahtapot and the OdaTV incident entails the actor’s ability to physically interdict systems within Turkey. Additionally, most PDB paths for Rad components have a root folder of ‘EGM’, from which we derived the name ‘EGoManiac’.
EGoManiac’s Rad toolkit relies on hardcoded email addresses for communication. Obfuscated logs and other exfiltrated materials are sent to the following emails across multiple service providers:
[email protected] [email protected] [email protected] [email protected] [email protected] [email protected] [email protected]
While email comms might usually lead to another research dead-end, the address [email protected] raised an interesting connection.
In 2016, Turkish websites reported sparse details of an ongoing attempt to prosecute members of the Turkish national police and executives of an IT company called ‘Datalink’ suspected of leaking information on active police operations. The leaks were reportedly used by FETO/Gulenist movement social media accounts to fuel conspiratorial elements in an ongoing power struggle within the country.
Reports cite the use of spyware called ‘HORTUM’ (roughly translated as ‘garden hose’) to siphon data from infected machines within public institutions in Turkey including the Intelligence department of the General Directorate of Security (EGM). Some of the reporting mistakenly conflates HORTUM with Hacking Team’s RCS. The siphoned data was sent to [email protected], and from there allegedly redistributed by Datalink. The capabilities of HORTUM and its communication methods match those of EGoManiac’s Rad, including the hardcoded Woxmail address.
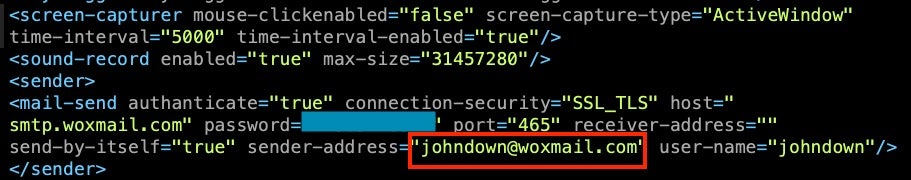
[email protected] for exfiltrationWe cannot independently verify the veracity of the initial reporting. An independent investigation to that effect was conducted by Kim Zetter, who obtained extensive details including a report by the prosecutor handling the case. Taking the information we have at face value, we uncover another possible facet of the EGoManiac story.
The Hacking Team Connection
As early as 2012, victims of Hacking Team’s Remote Control System (RCS) ‘Da Vinci’ began to show up in Turkey. In 2013, Wired reported that a woman in the United States was targeted with RCS. The victim suspected that she was targeted by Gulenist elements that had infiltrated the Turkish government. However, Hacking Team continued to assert that it only sells its tools to governments and did not confirm Turkey’s status as a customer. Now, in the aftermath of Phineas Fisher’s devastating hack-and-leak operation against Hacking Team, we can independently confirm that Turkey was in fact a customer of Hacking Team at the time, but who exactly was their customer in Turkey?
The leaked Hacking Team treasure trove contains communications with officials claiming to be a part of the Turkish National Police as early as 2011. Citing problems with their mail server, they proceed to use three Gmail accounts to plan their purchase of RCS. A Gmail account is also used for communication with the Hacking Team support portal.
Hacking Team officials note further irregularities as the first deal goes through. Though the purchase is intended under the umbrella of a UAE-based shell company (‘Foresys Information Technology-FZE’), Hacking Team receives payment from a company registered in Istanbul: ‘Datalink Analiz LTD’.
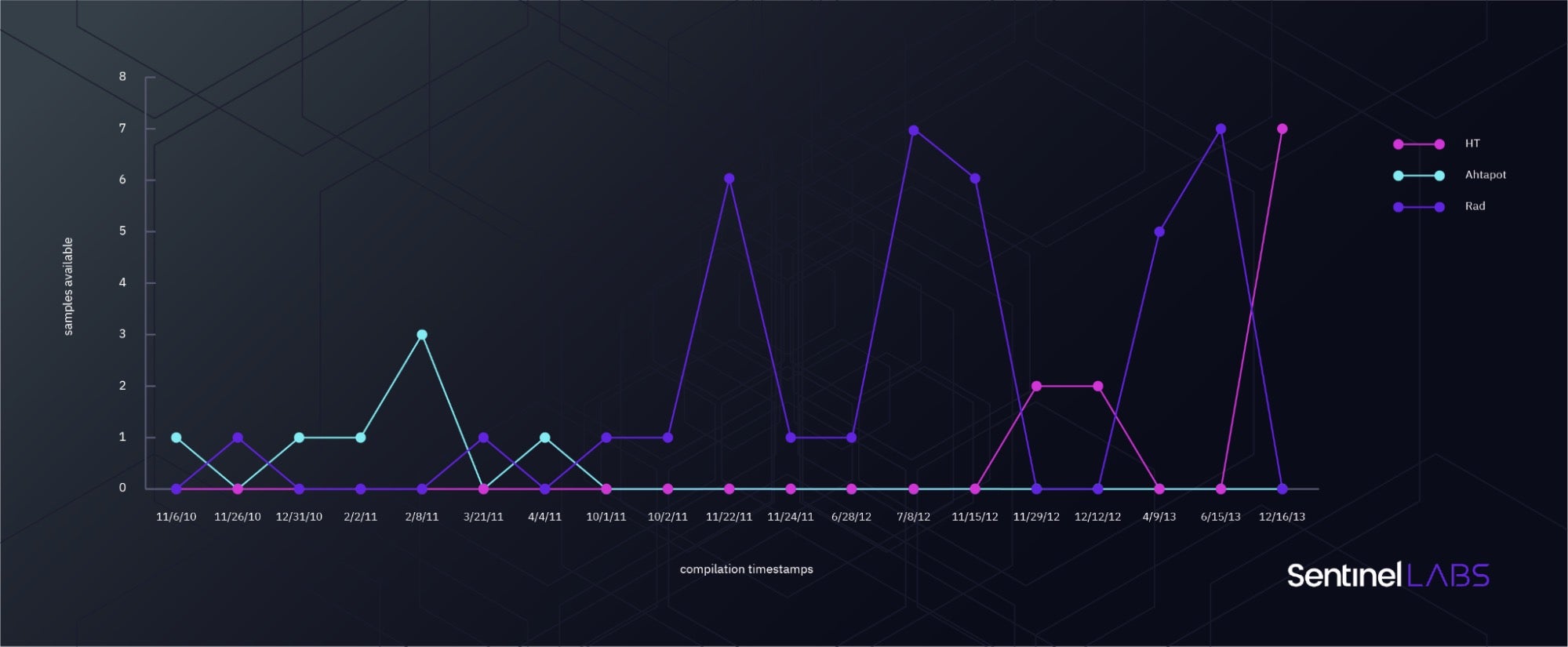
To be thorough, we chart the use of Hacking Team RCS by the Turkish National Police (see Appendix C in the full report) based on the company’s internal watermarking scheme used to track the origin of leaked samples among their customer base. The graphic above notes the coincidental cadence of the use of the different malware families related to the EGoManiac cluster. However, we can’t go as far as to equate the two clusters without resolving the murky allegiances of the operators involved.
The connection between the EGoManiac umbrella and this specific sub-cluster of Hacking Team RCS is built on the admittedly thin strand of the ‘Datalink Analiz’ shell company. That thread merited an investigation beyond the purely technical to straighten out an abundance of conspiratorial claims, alleged foreign money laundering, and ambiguous finger pointing.
Conclusion
The case of EGoManiac is far from straightforward. It involves difficult investigative connections that test the boundaries of our visibility, the efficacy of our research tools, and the limits of purely technical attribution. Beyond the technical exercise, it’s a profile of a threat actor willing to spy on both friend and foe and to use that access to malign and entrap journalists without compunction. While this particular intrusion set is outdated, the questions it raises speak to the friction between the unsupervised governmental use of malware and the integrity of public institutions, rule of law, and evidentiary standards. They are more relevant now than ever before.
如有侵权请联系:admin#unsafe.sh