2021-11-10 18:17:28 Author: securelist.com(查看原文) 阅读量:26 收藏
Last year became a banner year for the online entertainment industry. Driven by the pandemic lockdown restrictions and imposed work-from-home policies, people got to spend more time at home looking for replacements for familiar sources of entertainment. While theatres and sports stadiums suffered from a lack of live events, other businesses, like online streaming services, have benefited from consumers spending more time at home. In fact, time spent streaming increased by almost 75% in 2020. In 2021, demand for video streaming has remained strong, and the global video streaming market is still growing, albeit slower than in 2020, and is expected to continue growing for the next few years.
Sources of entertainment have always been a lucrative lure for fraudsters and scammers. With millions of new users on streaming platforms, cyberattackers have recognized this heightened demand and seek to take advantage of it by distributing streaming phishing scams and spreading malware under the guise of users’ favorite shows.
This research is a continuation of our TV show and streaming threat-related reports (2020 and 2019) providing an overview of the latest trends and key events across the entertainment-related threat landscape. Traditionally, the study covers common phishing and malware threats encountered by users who seek alternative ways of watching streamed content, along with a detailed analysis of the most popular shows to become bait for careless users. Additionally, we analyzed darknet services that offer access to content at a lower price by selling streaming users’ credentials.
Methodology
In this research, we analyzed various types of threats: malware and unwanted software associated with streaming platforms and the content they offer, as well as phishing pages and fake websites mimicking the world’s biggest streaming services.
For this purpose, we analyzed streaming-related threat statistics from Kaspersky Security Network (KSN), a system for processing anonymized cyberthreat-related data shared voluntarily by Kaspersky users. In particular, we analyzed the number of (mobile or PC) users who encountered various streaming-related threats between January 2020 and June 2021.
Furthermore, we analyzed the messages published on the dark web offering access to the video streaming platforms in order to define what the “dark streaming” market looks like today: how much accounts cost, who buys them and what may happen consequently.
In this report, we analyze data related to five of the world’s major streaming platforms, namely:
- Netflix
- Hulu
- Amazon Prime Video
- Disney +
- Apple TV Plus
Malware and riskware instead of streaming
When discussing streaming-related threats, it is crucial to talk about malware and unwanted software. Looking for alternative sources to download a streaming app or an episode of a show, users often discover various types of malware, including Trojans, spyware and backdoors, as well as naughty applications, such as adware.
We searched KSN for malicious and unwanted program detections containing the names of the five streaming platforms listed above in the context of obtaining login credentials, a subscription, viewing the platform’s content for free, or downloading the streaming app.
We discovered that almost 19,000 unique users were at least once prevented from downloading malware and unwanted applications that used streaming platforms as a lure between January 1, 2020 and June 30, 2021.
Netflix does not just lead as the most popular platform in terms of subscriber numbers, but also as the most popular streaming service used as a lure by cybercriminals. In fact, 89.93% of affected users faced malware or unwanted software while searching for Netflix and related content. Amazon Prime took second place on the list with 6.26% of affected users. Notably, while previous research had shown that none of the users encountered threats while attempting to access Apple TV + content, in the last eighteen months, attackers have started targeting users of this platform.
Number of users affected by malware and unwanted applications, by platform, January 1, 2020 through June 30, 2021 (download)
Overall, Kaspersky products detected 93,095 attempts to infect 18,938 unique users with 8,650 different threats from January 1, 2020 through June 30, 2021. The peak of malicious activity was registered in the first half of 2020 with 51.62% of users encountering malware or unwanted software. Over the same period in 2021, the number of affected users dropped by more than half.
The percentage of users who encountered malware or unwanted software associated with the reviewed platforms, January 1, 2020 through June 30, 2021 (download)
This year, we have observed a rapid decrease in the indicators for all of the analyzed platforms, except for Disney+. In the first six months of 2021, the number of users encountering malware that used this platform as a lure grew four times compared to the same period of 2020.
Across all five platforms, the greatest number of affected users comes from India (11.37%). Users there most frequently faced malicious files while attempting to download streaming app downloaders. Algeria and the United States round out the TOP 3 with 8.42% and 7.41%, respectively.
The ten most affected countries, January 2020 through June 2021 are as follows:
| Country | Number of unique users* |
| India | 11.37% |
| Algeria | 8.42% |
| United States | 7.41% |
| Germany | 5.98% |
| Brazil | 4.30% |
| Spain | 2.87% |
| Mexico | 2.86% |
| Morocco | 2.77% |
| France | 2.52% |
*The number of users affected by the streaming-related malware and unwanted software in the country as a percentage of all affected users.
We also looked into the geographical distribution of threats to the users of each platform individually.
The table below shows the geographical distribution of users who encountered malware and unwanted software mimicking Amazon Prime, Apple TV, Disney+, Hulu and Netflix in relation to all affected users by platform, January 2020 through June 2021.
| Platform | Country | Share of users* |
| Amazon Prime | United States | 55.61% |
| India | 9.03% | |
| Germany | 8.78% | |
| Apple TV | Germany | 27.42% |
| Brazil | 11.83% | |
| Russia and Vietnam | 3.76% | |
| Disney+ | Italy | 9.63% |
| Germany | 9.32% | |
| India | 8.39% | |
| Hulu | United States | 9.16% |
| Algeria | 8.79% | |
| Kenya | 6.96% | |
| Netflix | India | 11.84% |
| Algeria | 9.31% | |
| Germany | 5.36% |
*The number of unique users who encountered platform-specific malware and unwanted software in the country as a percentage of all unique users who encountered platform-specific malware and unwanted software.
The largest number of users who encountered malware and unwanted software associated with Amazon Prime belonged to the United States (55.61%). That might be related to the fact that most Amazon Prime viewers are located in that country.
The greatest number of users who encountered various types of malware and unwanted software associated with Apple TV comes from Germany (27.42%).
As for Disney+, the three most affected countries are Italy (9.63%), Germany (9.32%) and India (8.39%) with relatively similar shares of users affected by malicious and unwanted programs associated with this streaming service.
When it comes to malware and unwanted software that uses Hulu as a lure, cybercriminals tend to target users from the United States (9.16%), Algeria (8.79%) and Kenya (6.96%).
As for Netflix, a platform most often targeted by cybercriminals, users from India (11.84%), Algeria (9.31%) and Germany (5.36%) encountered malicious activity exploiting the Netflix name most frequently.
Threats behind fake streaming platforms
To get a clear picture of how cybercriminals are exploiting popular streaming services, we extracted and analyzed samples distributed using Netflix, Disney+, Hulu, Apple TV and Amazon Prime as a lure to define the main types of distributed threats.
The distribution of specific threats encountered by our users is as follows:
TOP 10 types of threats most frequently encountered by Kaspersky users and disguised under the name of Netflix, Disney+, Apple TV, Hulu and Amazon Prime, January 1, 2020 through June 30, 2021 (download)
We discovered that more than a third (33.12%) of the threats encountered by our users were Trojans. The attackers also actively used specific types of Trojans, such as Trojan-Spies (5.41%), Trojan-Bankers (4.68%), Trojan-Downloaders (2.92%) and PSWs (2.25%). Often, they are designed to electronically spy on the user’s activities one way or another: PSWs are designed to steal logins and passwords for various services and detect when those services are being used, bankers target banking websites and applications and spy on the user’s banking activity. Trojan-Downloaders do not spy or steal, but they are capable of installing other malicious programs. The second most common threat encountered were unwanted files detected with a “not-a-virus” verdict, including non-malicious downloaders (20.58%), RiskTools (5.78%) and adware (19.12%) that bombard users with unwanted ads and notifications.
Popular shows as a lure
Further analysis of the streaming threat landscape showed that cybercriminals are actively using certain shows and series as bait. We dived into deeper analysis to specify which content pieces were used by scammers the most frequently.
To make sure our research is unbiased, there are bound to be some restrictions to the scope of the research. We used public ratings of the most popular TV shows according to the world’s most authoritative movie sources: IMDB and Rotten Tomatoes. Having analyzed lists of the most popular series of 2020 and 2021 (so far), we created a list of thirty TV shows available for streaming from the most popular services.
The series analyzed within this research:
| Better Call Saul |
| Bridgerton |
| Dark |
| Dota: Dragon’s Blood |
| Elite |
| Emily in Paris |
| Euphoria |
| It’s a Sin |
| Loki |
| Mare of Easttown |
| Money Heist |
| Never Have I Ever |
| Ozark |
| Peaky Blinders |
| Raised by Wolves |
| Resident Alien |
| Rick and Morty |
| Sex Education |
| Shadow and Bone |
| Superman and Lois |
| Sweet Tooth |
| The Boys |
| The Crown |
| The Mandalorian |
| The Queen’s Gambit |
| The Umbrella Academy |
| The Witcher |
| Unorthodox |
| WandaVision |
| Westworld |
Kaspersky products detected 27,860 attempts to infect 7,051 users with 6,157 different threats that used Netflix, Hulu, Disney+, Apple TV, Amazon Prime and HBO Max content as a lure.
The table below shows ten most popular series used as bait to spread threats by number of detections, January 1, 2020 through June 30, 2021.
| Name | Number of infection attempts* |
| The Mandalorian | 28.72% |
| Money Heist | 28.41% |
| Rick and Morty | 9.69% |
| Peaky Blinders | 9.25% |
| Westworld | 7.17% |
| Sex Education | 2.82% |
| Better Call Saul | 2.47% |
| Ozark | 2.01% |
| The Boys | 1.64% |
| Euphoria | 1.58% |
*Number of infection attempts associated with the certain show as a percentage from all infection attempts associated with popular shows.
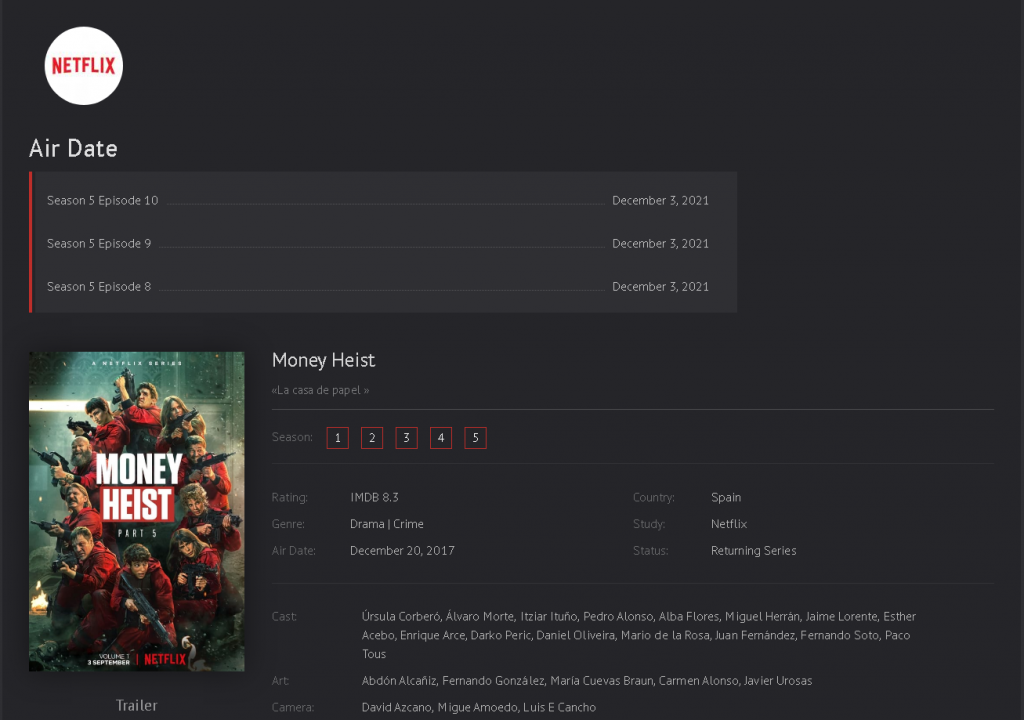
We discovered that almost 60% of infection attempts used just two shows as a lure. The Mandalorian (28.72%) and Money Heist (28.41%), the world’s biggest hits for the past few years, are being actively exploited by cybercriminals for spreading their malicious activity. As a matter of fact, these series are also the main baits used by phishers.
An example of a phishing page offering to stream Money Heist
Phishing
Phishing attacks are one of the most widespread ways of stealing account credentials. As most films are released online, fraudsters have delved into the sphere of streaming services. Wanting to be the first viewers of a new episode of their favorite show, users become careless about websites they visit, and this is exactly what scammers benefit from when creating phishing websites.
We found examples of phishing pages for each analyzed platform: Netflix, Amazon Prime, Disney+, Apple TV and Hulu. In most cases, they look almost identical to the original designs: the colors, fonts and layouts might not even betray a fake.
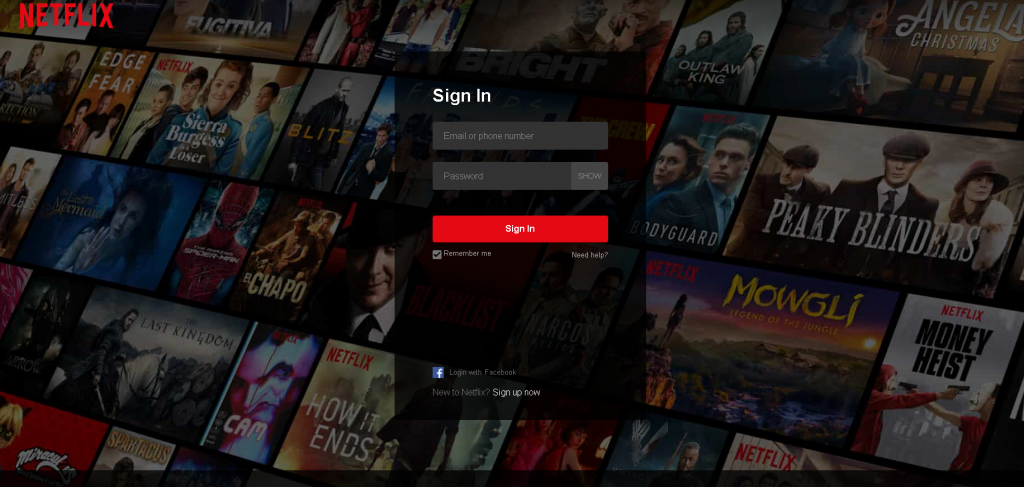
An example of a phishing page mimicking the Netflix login page
The primary target for scammers is user credentials. We discovered phishing scams mimicking the reviewed platforms’ login pages as a way to harvest credentials. Just like any sign-in page, most of these ask to enter an email and password for the viewer account. As a result, users’ credentials end up in untrustworthy hands. After that, scammers may start using that data for malicious purposes, e.g., launching spam attacks, and gaining access to users’ email or other accounts on various websites: many users reuse passwords for shopping platforms, social media, online banking, etc. And often, stolen data is put up for sale on the dark web.
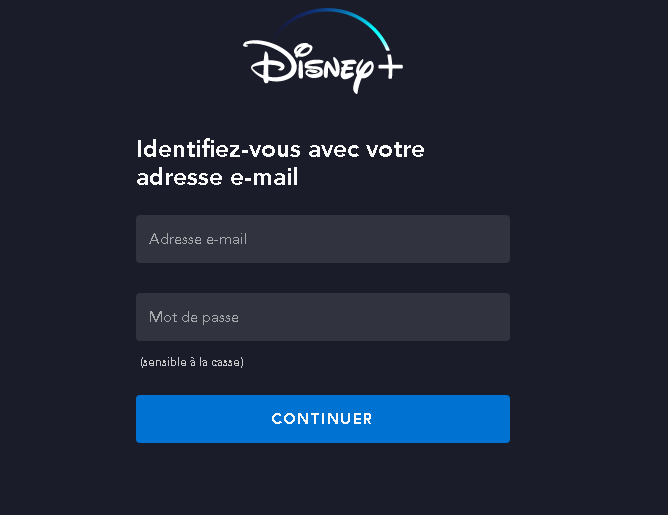
An example of a phishing page mimicking the Disney+ login page
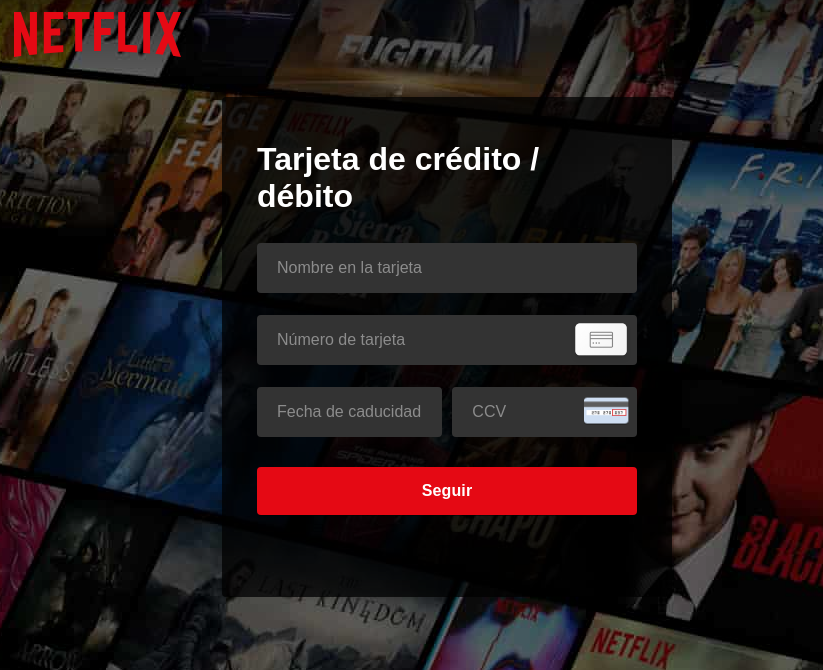
Other types of phishing pages we found were financially motivated. These pages typically asked users to confirm their payment details in order to subscribe to the streaming service. Visiting a fake subscription page and assuming that they are buying access to all of their favorite shows, the user ends up sending money to fraudsters. The scheme is pretty simple, yet effective and, therefore, widespread. In addition, these pages harvest both identifying information and banking credentials.
An example of a Netflix phishing page asking for banking credentials
Another widespread way to steal money from impatient viewers is creating phishing pages offering to stream certain shows. Scammers usually intensify their malicious activity around the long-awaited premieres or new seasons of popular shows. In the hope of watching the long-awaited season’s premiere, users could end up on a website showing the first few minutes of the show (typically extracted from official trailers) before being asked to pay a small subscription fee to continue watching. Needless to say, after the “subscription fee” is paid, the episode will not continue streaming, while the users will lose their money to cybercriminals.
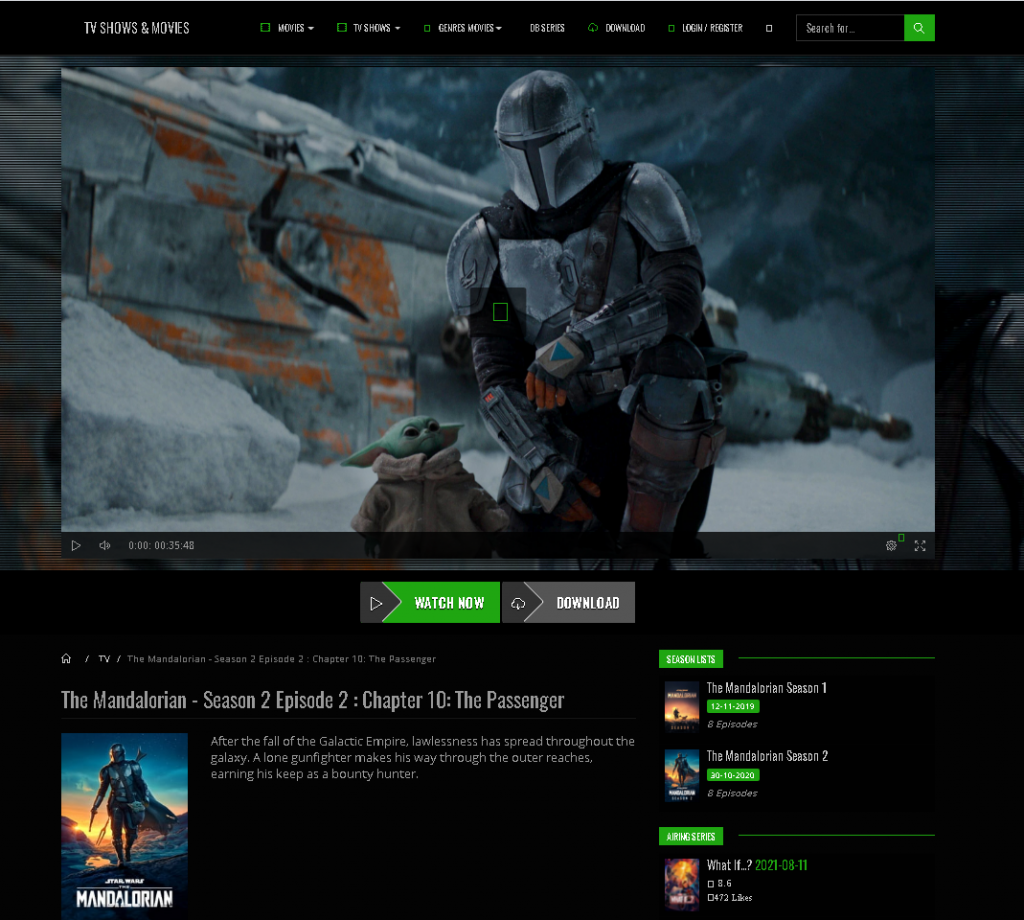
An example of a phishing page offering to stream an episode of “The Mandalorian”
It is not always users that discover untrustworthy webpages while looking for a streaming source: sometimes, users themselves are sought out by fraudsters. In that scenario, cybercriminals send out spam to lure streaming service users to a phishing page. The main fraud scheme is always similar: to avoid losing the account, the user must update or confirm their bank account information, credit card details or account credentials. If the user falls for that scheme, they usually end up exposing the account credentials or banking details to cybercriminals.
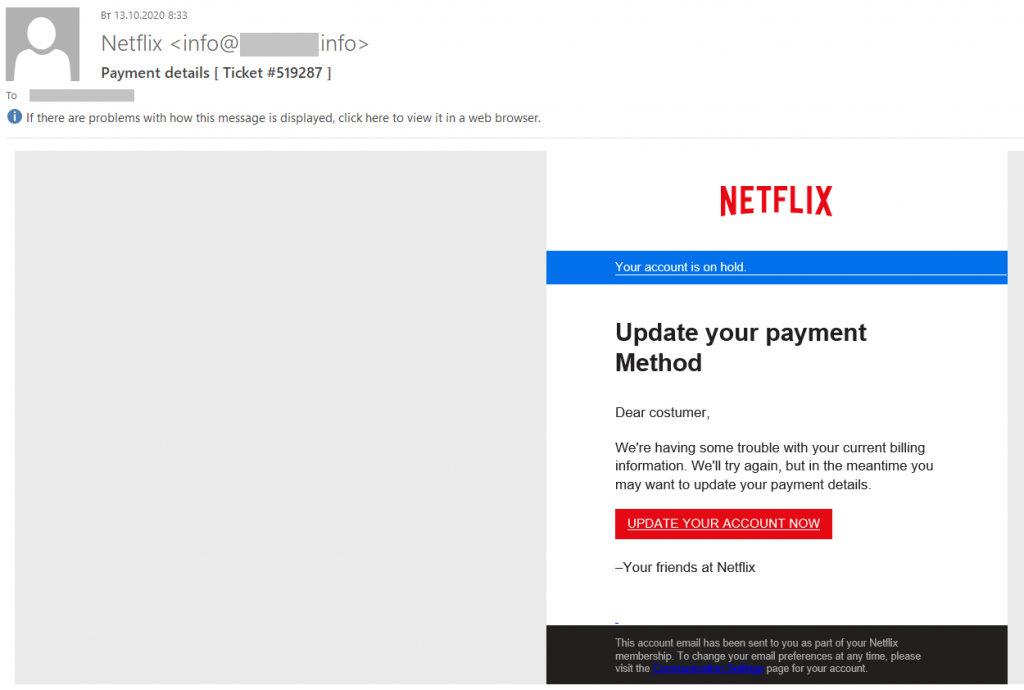
A phishing email asking the recipient to provide a valid payment method for a Netflix account
Streaming services have not been unaffected by classic phishing schemes, such as fake giveaways and raffles. We discovered an example of a phishing page promising users a generous reward on behalf of Disney+ for sharing a link with twenty friends. In such cases, cybercriminals use victims themselves as a tool for spreading scams as a part of a raffle. A link sent by people you know sees more trust than one received from a stranger. If the user follows the link and tries to get their prize, they usually find they have to pay a commission or fee first. After the money is paid, cybercriminals disappear without rewarding the unfortunate user.
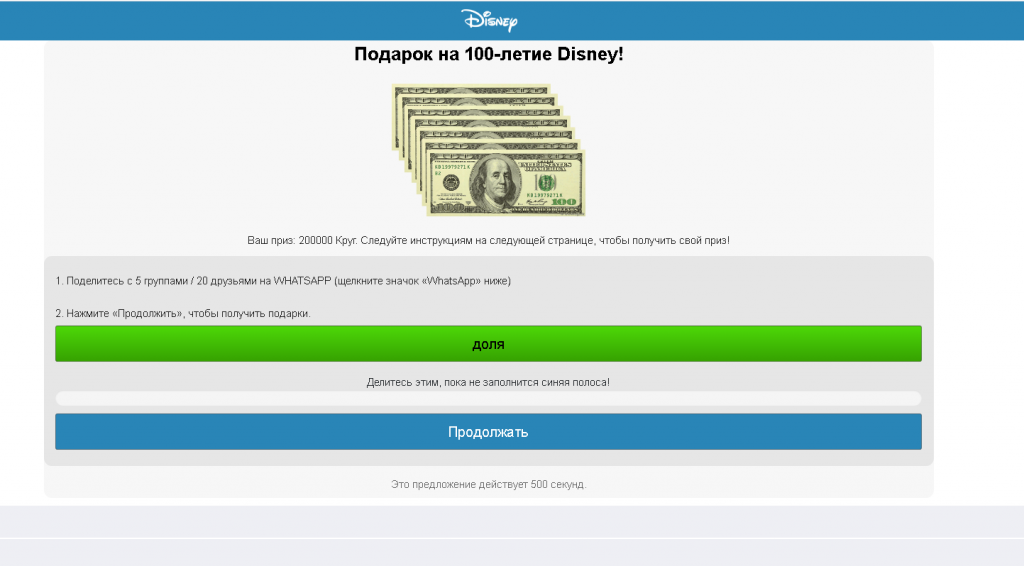
A fake raffle is asking to distribute phishing links among friends to get a gift from Disney
“Dark streaming” and the real price of cheap deals
A quick search for streaming accounts online, in forums and marketplaces, as well as on the dark web, reveals numerous “unofficial” services offering access to on-demand content at a much lower price. For many users, these options are too good to ignore.
A typical scenario would see a user buying access to a password-sharing account. With most streaming services offering the option to share subscriptions with other users, families and friends, fraudsters are taking advantage of this. In response, providers including Netflix are looking to make changes to tighten up password sharing; an example of this is a recent two-factor authentication test by Netflix to crack down on fraud. However, there are still offers out there for password-sharing accounts, and with prices averaging at around $2.50 per monthly subscription, they are very attractive.
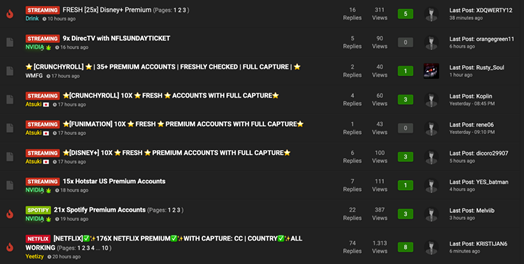
An example of streaming account offers on the dark web
Another option available on the dark web is to purchase access details to stolen accounts in bulk. The price in this case varies from 50 cents to $8.
On some forums, users even offer streaming accounts for “free” in order to promote themselves as account sellers or to boost their reputation on the forum. Accounts thus purchased typically come with some form of temporary service guarantee, or without any guarantee. In practice, though, these “guarantees” are often worth nothing, as we will find out next.
An example of a streaming account sale for reputational purposes
There are typically two scenarios possible after one buys such an account: it suddenly becomes inaccessible due to being banned by the provider, or the credentials change, meaning the user cannot access the content any longer. The seller typically promises to replace the account with another, but this does not always happen. The old adage, “you get what you pay for”, certainly rings true here.
In almost all scenarios, the euphoria of having cheap access to the latest content will be short-lived. If a deal seems too good to be true, then it probably is. Taking this route is ultimately fraudulent and an act of piracy. There is also no guarantee that after payment, the buyer will receive the goods, or if they do, they will not be banned quickly.
All in all, most of the accounts sold on the dark web are real users’ accounts. The credentials are obtained illegally through social engineering tactics and phishing pages where the real account owners are duped into giving their private and confidential account details to cybercriminals.
Conclusion and recommendations
On-demand content and streaming services have seen rapid growth in the past year and a half, driven largely by the increased use of mobile technology and availability of high-bandwidth networks, which have been further accelerated by the pandemic. Consumers today expect to be able to watch their favorite shows and features as soon as they are released, to keep up with the buzz on social media.
But, instead of going through “official” channels to do this, many people today are bypassing the legitimate routes to streaming services in favor of cheaper alternatives or early access. Looking for alternative sources, users often end up with data theft, money loss, or malware on their devices.
We observed how the malicious activity reached its peak in the first six months of 2020. This is not surprising, as this is the time of the year when the first restrictions and lockdown measures were introduced. People started to stay home more and got a chance to spend their free time watching their favorite shows. During the next year, we observed how the number of users encountering malware gradually decreased.
Of the reviewed platforms, Netflix is the most widespread lure used by cybercriminals and fraudsters. We detected 80,302 attempts to infect 17,031 users with 7,199 files associated with the name of that platform. Nevertheless, these numbers also dropped between H1 2020 and H2 2021.
As for the other platforms, this year, Disney+ became a much more appealing target for cybercriminals. During the first six months, the number of affected users of this service was already higher than for the whole of 2020, growing nearly four times year on year.
Phishing remains a serious challenge for streaming service users. We have discovered phishing pages in various languages for each analyzed platform, aiming to steal users’ identifying information, banking credentials or money. As a result, the data sent by the victims end up on the dark web, and accounts for streaming platforms are sold as password-sharing accounts.
To avoid falling prey to malicious programs and scams while using streaming services, Kaspersky recommends that users:
- Check the authenticity of websites before entering personal data and only use official, trusted webpages to watch or download movies; double-check URL formats and company name spellings.
- Pay attention to the extensions of files they are downloading. A video file will never have an .exe or .msi extension.
- Use a reliable security solution, such as Kaspersky Security Cloud, that identifies malicious attachments and blocks phishing sites.
- Avoid links promising early viewings of content. If you have any doubts about the authenticity of the content, check with your entertainment provider.
- Do not open attachments or click on links in emails from streaming services, particularly if the sender insists on it. It is better to go to the official website directly and log in to your account from there.
- Be wary of any deals that seem too good to be true, such as a “one-year free subscription”.
- Whenever possible, only access streaming platforms via your own, paid subscription on the official website or an app from an official marketplace.
- Do not download any unofficial versions or modifications of these platforms’ applications.
如有侵权请联系:admin#unsafe.sh