2021-12-08 18:02:11 Author: fuzzinglabs.com(查看原文) 阅读量:22 收藏
Today I will like to discuss the Mozilla NSS BigSig vulnerability found recently by @taviso from Google Project Zero. Inside its blogpost, Tavis Ormandy detailed the vulnerability and mentioned some really good points about why this bug was not found using fuzzing by OSS-fuzz. It’s a really interesting case to analyze if you’re writing fuzzers because there is a lot of interesting lessons to learn from it.
Vulnerability (old school Buffer overflow)
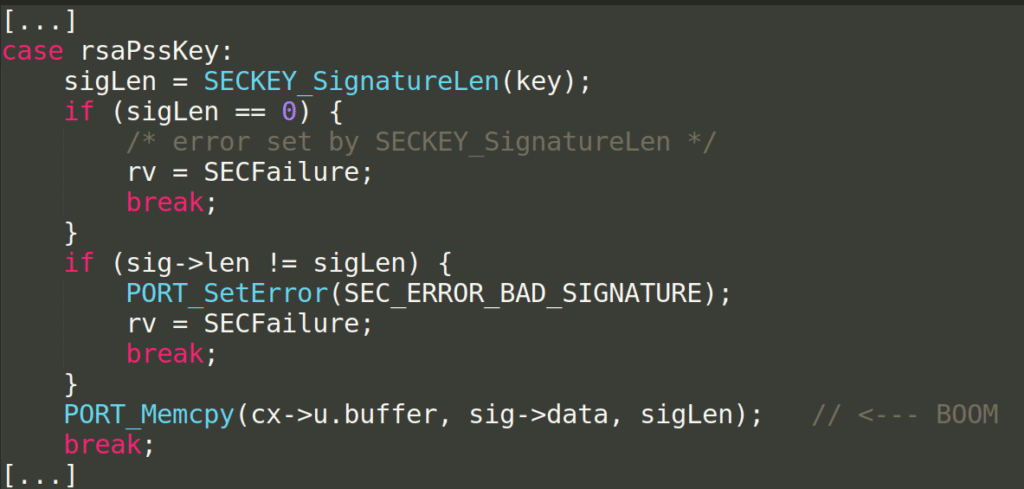
Bug fixed:
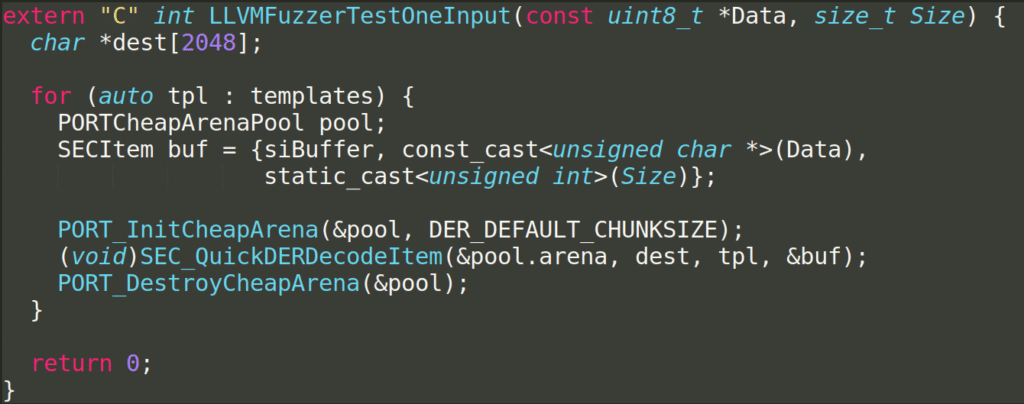
Lessons Learned by @taviso
- Missing end-to-end testing (Only focussed on decoding using `SEC_QuickDERDecodeItem`)
- Arbitrary size limits. (fuzzer limitation)
- Misleading metrics. (coverage of all fuzzers combined)
No fuzzer are reproducing the behavior of `vfychain` program.
–> You should always convert your programs/unittests into fuzzing harnesses.
Fuzzers are between 3 and 5 years old.
–> You should review, improve and extend your fuzzer every year (or after every major change)
No fuzzers was calling public verifying APIs with arbitrary data
–> When you’re writing/fuzzing a library, you should fuzz ALL the public APIs of the library (even if your main program are not using them, just think that someone else library might be or even yours in the future)
Limitation by OSS-FUZZ config restraint the fuzzers:
–> You should use multiple fuzzers and multiple fuzzer configs (some of them might not be configured the same way by default) – That’s why I’m always advising to fuzz with multiple fuzzers
Enter your email and we'll send you a bundle of awesome resources. 100% free - 100% awesome.
Any questions about our services and trainings ?
Get in touch today with any questions that you might have.
如有侵权请联系:admin#unsafe.sh