2021-12-15 02:46:04 Author: blog.elcomsoft.com(查看原文) 阅读量:29 收藏

Installing the checkm8 exploit to perform forensically sound extractions with iOS Forensic Toolkit can be tricky, which is in part due to certain hardware peculiarities. If you watch our blog, you might have already read the article on checkm8, checkra1n and USB hubs. We have some good news: we managed to fix some of the issues with or without the use of a USB hub.
What’s it all about?
As mentioned in the previous article, some devices in some circumstances may be picky about the way you connect the iPhone to the computer. Since checkm8 extraction requires a native Mac, we would generally recommend using a direct connection with a single USB-A to Lightning cable. Some Macs don’t have any Type-A ports, so one could naturally think that using the original (or certified third-party) Type-C to Lightning cable would be the right thing to do. Wrong! These cables have a different ID, and the checkm8 exploit would fail to install if you used such a cable. Oddly enough, some of the cheapest no-name Type-C to Lightning cables just worked; mostly those with no PD charging. I wouldn’t rely on that, though, as the different batches of no-name cables are made by all sorts of different OEMs, so the next one may or may not work with about equal probability.
The recommended solution would be using a single-port Type-C to Type-A adapter, and connecting the Type-A to Lightning cable to the corresponding port. This solution always works on Intel-based Macs; however, it just doesn’t seem to work reliably on the Macs built with Apple Silicon. For those Apple Silicon Macs we would generally recommend using a USB hub, just like the one shown below:
All that is old news; what had changed in iOS Forensic Toolkit to warrant a new blog post? We’ve managed to catch a few bugs and optimize the code to make things more reliable with or without the hub. The current state of affairs is shown below:
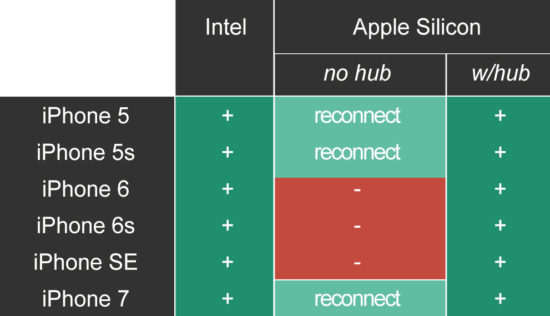
- If you are using an Intel Mac: we’ve made everything work reliably both with and without USB hubs. If you still experience problems, try the Type-A connection, but generally USB hubs are no longer an issue worth mentioning.
- If you are using an M1 (Apple Silicon) Mac: using a USB hub is still recommended as everything connected through it works reliably.
- If you are using an M1 (Apple Silicon) Mac without a USB hub, and connecting certain specific iPhone models: some iPhone models will require reconnecting during the process; iOS Forensic Toolkit will prompt for a reconnection. Some other iPhone models will not work without a USB hub at all.
The table below specifies which devices will require a reconnection, and which ones will require a USB hub on Apple Silicon Macs:
iPhone 7 support is coming soon
Our R&D just committed an update to iOS Forensic Toolkit with preliminary support for the iPhone 7. The next beta will feature a limited support for iPhone 7 devices. The beta build still has the following restrictions for iPhone 7 devices:
- iOS 10.x through 13.x: file system extraction and keychain decryption; removing screen lock passcode not required.
- iOS 14.x and 15.x: the screen lock passcode must be removed in order to perform the extraction. Note that this breaks forensically sound extractions. We are currently developing a workaround, which won’t be included in the first beta.
Stay tuned!
REFERENCES:
![]()
Elcomsoft iOS Forensic Toolkit
Extract critical evidence from Apple iOS devices in real time. Gain access to phone secrets including passwords and encryption keys, and decrypt the file system image with or without the original passcode. Physical and logical acquisition options for all 64-bit devices running all versions of iOS.
Elcomsoft iOS Forensic Toolkit official web page & downloads »
如有侵权请联系:admin#unsafe.sh