Digital steganography is one of the data hiding techniques, which is to embed another data in one data (hereinafter referred to simply as steganography). we will use Steghide to hide text file inside image file, In steganography, the original file used for hiding is called a cover file, and the created data is called a stego file.

For example, by embedding a text file in a certain image file, the existence of the text can be concealed. At this time, the stego file has changed compared to the previous image, but it is difficult for humans to detect the change. The actual stego file, cover file, and hidden image file are shown below.
In digital steganography, electronic communication can include steganographic encoding within the transport layer, such as a document file, image file, program, or protocol.
Media files are ideal for steganographic transfer due to their large size.
For example, a sender might start with a harmless image file and adjust the color of every 100th pixel to match a letter in the alphabet that’s so subtle that someone not looking for it is unlikely to notice it.
The advantage of steganography over cryptography is that the alleged secret message does not draw attention to itself as an object of control.
Highly visible encrypted messages – no matter how cryptographically strong – are of interest and may in themselves be incriminating in countries where encryption is illegal.
Thus, while cryptography is the practice of protecting the content of a message alone, steganography is about hiding the fact that a secret message is being sent and also hiding the content of the message.
What is steganography technique?
Confidential data must be kept out of sight. To do this, encrypt such data so that no secrets are revealed. However, encrypted data is rather noticeable, revealing that “there is a secret.” Therefore, it cannot be said that confidential data is perfect if it is encrypted.
Different “steganography technology” is the following technology.
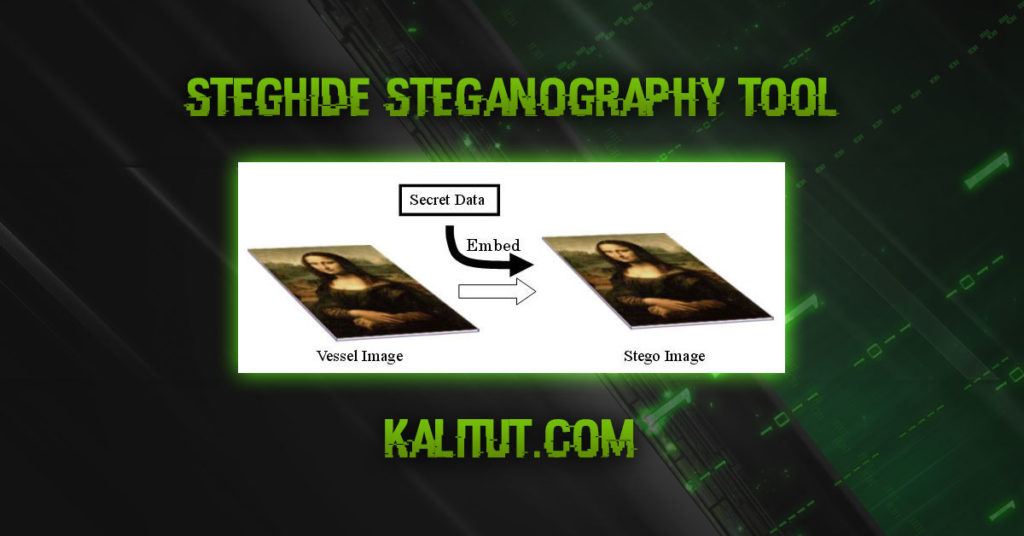
First, steganography involves two types of data. One is the important secret data itself, and the other is the media data (images, sounds, etc.) that serves as a container for “embedding and concealing” the important data. This is also known as vessel, carrier, dummy data, etc. Container data that already has secret data embedded in it is called “stego data”.
Special programs and key data are required to embed secret data and retrieve data once embedded.
A common container data is a 24-bit “full-color image” consisting of red, green, and blue color components. The figure below shows the general concept and mechanism of steganography. This example shows the situation where important secret data is embedded in a “common image” called Mona Lisa.

In this way, steganography technology is a technology that hides the whereabouts of secrets by embedding (actually replacing ) important secret information in inconspicuous media data , and the embedded information is very large. It’s safe. There are various specific embedding methods, but there is no way to determine which method was embedded by looking at the stego data. Steganography can also be said to be “a technology that can cooperate with cryptography” because it can also “embed encrypted data”.
The most important point in steganography is that it leaves no “evidence of embedding” in the stego data. In other words, the stego data must be infinitely similar to the pre-embedded data. In addition, steganography users should immediately discard the pre-embedding container data after the embedding process is complete. That is, you should eliminate the possibility that someone can compare the data before and after embedding.
Any stego data in each scheme must be reusable as “vessel data” in another implant. If not, the initial embedding would have essentially altered the original container data, and such embedding cannot be called “steganography”. That is, all vessel data must be “reusable” in any steganography, and only the “last embedded secret data” is extracted.
In addition, large embedding capacity is also a requirement for steganography. We are convinced that the BPCS method is still the best method for embedding in image data.
Steganography in Kali Linux Steghide
What is steghide? Steghide is a steganography program that allows you to hide data in various types of images and audio files.
How to use steghide Video tutorial
Color-sensitive sampling rates do not change, making the embedding robust against first-order statistical tests.
Features:
- inline data compression
- encryption of embedded data
- embedding a checksum to verify the integrity of the extradited data
- Supports JPEG, BMP, WAV and AU files
Installing Steghide
Installation on Kali Linux is easy as steghide is already available in the Kali Linux repository.
Run the following command and you’re done:

How to use steghide
Hide text file in image
I created a steguide folder in the root home folder and placed the image.jpg and secret.txt files there too.
image.jpg is the file where I am going to hide the secret.txt file.
I’m going to show the teams here for all this mess.
To hide a text file in a picture in Kali Linux using steghide, use the following command:
steghide embed -cf image.jpg -ef secret.txt
This command will insert the secret.txt file into the picture.jpg file.

Now you can send, share or do anything with this new image.jpg file without having to worry about someone exposing your data.
Extract text file from image
After you fill in your secret as shown above, you can send the picture.jpg file to the person who should receive the secret message.
The receiver should use steghide as follows:
steghide extract -sf image.jpg

If the supplied passphrase is correct, the contents of the original secret.txt file will be extracted from the image.jpg file and saved in the current directory.
After displaying some general information about the file (format, capacity), you will be asked if steghide should try to get information about the embedded data.
If you answer yes, you must provide a passphrase.

Steghide will then try to fetch the embedded data using this phrase and – if it succeeds – will display some information about it.
Steganalysis and detection
When computed, a steganographically encoded image with data packet detection is called steganalysis.
However, the easiest way to find modified files is to compare them with known originals.
For example, in order to detect information moving through graphics on a website, an analyst may maintain known clean copies of those materials and compare them to the current content of the website.
Differences assuming the carrier is the same constitute a payload.
In general, using extremely high compression rates makes steganography difficult, but possible.
Compression errors provide data hiding, but high compression reduces the amount of data available to store the payload, increasing encoding density, making it easier to detect (in extreme cases, even by casual observation).